This document discusses binary vulnerabilities and methods for identifying and exploiting them. It covers topics like stack overflows, heap overflows, integer overflows, and pointer vulnerabilities. It also discusses vulnerability metrics, identifiers, and tools that can be used for analysis like fuzzers, symbolic execution, and decompilers. Exploitation techniques like bypassing protections and transferring control are also mentioned.




![Logic vulnerabilities
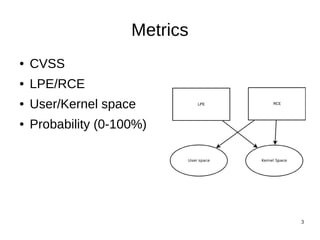
● Int rand(){return 4;}
● Client decide if authorization successful or not
● [Ch-ch-ch-ch-ching!!! $60,000] [117226] [117230] Critical CVE-2011-3046:
UXSS and bad history navigation. Credit to Sergey Glazunov.
● GNU C library dynamic linker $ORIGIN expansion Vulnerability
Tavis Ormandy.
6](https://image.slidesharecdn.com/3-120804021425-phpapp01/85/3-6-320.jpg)




![Example stack overflow
#include <string.h>
void foo (char *bar)
{
char c[12];
strcpy(c, bar); // no bounds checking...
}
int main (int argc, char **argv)
{
foo(argv[1]);
}
13](https://image.slidesharecdn.com/3-120804021425-phpapp01/85/3-13-320.jpg)


![Example Heap overflow
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include <string.h>
#define BUFSIZE 16
#define OVERSIZE 8 /* overflow buf2 by OVERSIZE bytes */
int main(){
u_long diff;
char *buf1 = (char *) malloc(BUFSIZE), *buf2 = (char *) malloc(BUFSIZE);
diff = (u_long) buf2 -(u_long) buf1;
printf("buf 1 = %p, buf2 = %p, diff = 0x% x bytesn", buf1, buf2, diff);
memset(buf2, 'A ', BUFSIZE - 1), buf2[BUFSIZE - 1] = '0';
printf("before overflow: buf2 = %sn", buf2);
memset(buf1, 'B(u_int) (diff + OVERSIZE));
printf("after overflow: buf2 = %sn", buf2);
return 0;
}
16](https://image.slidesharecdn.com/3-120804021425-phpapp01/85/3-16-320.jpg)



![Example integer overflow
int main(int argc, char **argv) {
char chLogin[100];
char chPassword[100];
int intPasswordLength;
strcpy(chLogin, argv[1]);
strcpy(chPassword, argv[2]);
intPasswordLength=atoi(argv[3]);
int admin=0;
char chOriginalPassword[100]="administrator";
if(intPasswordLength<1) intPasswordLength=0;
intPasswordLength++;
if(chLogin="admin"){
admin=1;
for(i=0;i<=intPasswordLength;i++)
if((chPassword[i])!=chOriginalPassword[i])
admin=0;
}
setUserStastusAdmin(admin);
}
21](https://image.slidesharecdn.com/3-120804021425-phpapp01/85/3-21-320.jpg)

![Pointer vulnerability
● Heap/Jit Spray
● NPD in user space: 1) Rewrite SEH -handler 2) [eax+bit_value]
.
23](https://image.slidesharecdn.com/3-120804021425-phpapp01/85/3-23-320.jpg)
![Example NPD
Registers:
eax=00000000 ebx=0000003b ecx=0be0f1c0 edx=00000000 esi=0be0f1c0 edi=0bfa3058
eip=6a606e58 esp=02333000 ebp=0233300c iopl=0 no up ei pl nz na po nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010202
Code disassembly:
6A606E48 | 80cc04 | or ah, 0x4
6A606E4B | 0000 | add [eax], al
6A606E4D | 8d4dff | lea ecx, [ebp-0x1]
6A606E50 | 51 | push ecx
6A606E51 | 52 | push edx
6A606E52 | 8bce | mov ecx, esi
6A606E54 | c645ff00 | mov byte [ebp-0x1], 0x0
6A606E58 | ffd0 | call eax
6A606E5A | 807dff00 | cmp byte [ebp-0x1], 0x0
6A606E5E | 750c | jnz mshtml!createhtmlpropertypage+0x31ec1
6A606E60 | 8b16 | mov edx, [esi]
6A606E62 | 8b82c8040000 | mov eax, [edx+0x4c8]
24](https://image.slidesharecdn.com/3-120804021425-phpapp01/85/3-24-320.jpg)
![Use after free
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=008a0000 ebx=0011ff7c ecx=00000000 edx=00000000 esi=00c12408 edi=05b71000
eip=6bdff979 esp=0011fee8 ebp=0011ff88 iopl=0 nv up ei pl zr na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246
SharedOFFICE14MSPTLS.DLL -
MSPTLS!LssbFIsSublineEmpty+0x2fdb9:
6bdff979 ff943888020000 call dword ptr <Unloaded_0.DLL>+0x287 (00000288)[eax+edi] ds:0023:06411288=????????
0:000> K
ChildEBP RetAddr
WARNING: Stack unwind information not available. Following frames may be wrong.
0011ff88 6bdce474 MSPTLS!LssbFIsSublineEmpty+0x2fdb9
0011ffb4 3179dc17 MSPTLS!LsQueryLineCpPpoint+0xb0
0011ffe0 3179dbad wwlib!GetAllocCounters+0xb6e4f
00120010 319a2cf4 wwlib!GetAllocCounters+0xb6de5
0012003c 319a2875 wwlib!DllGetLCID+0xc52fe
001200bc 31a94d48 wwlib!DllGetLCID+0xc4e7f
001204ec 31a9a05d wwlib!DllGetLCID+0x1b7352
0012052c 31a9aab5 wwlib!DllGetLCID+0x1bc667
0012064c 31785b8c wwlib!DllGetLCID+0x1bd0bf
001207a0 3176fab7 wwlib!GetAllocCounters+0x9edc4
001207c4 3176f1e5 wwlib!GetAllocCounters+0x88cef
00120808 3176b644 wwlib!GetAllocCounters+0x8841d
00120834 317691e4 wwlib!GetAllocCounters+0x8487c
00120890 31769016 wwlib!GetAllocCounters+0x8241c
001209b0 31768f9a wwlib!GetAllocCounters+0x8224e
001209d4 317642cd wwlib!GetAllocCounters+0x821d2
00120ad4 31761e22 wwlib!GetAllocCounters+0x7d505
00120afc 31761deb wwlib!GetAllocCounters+0x7b05a
00120d64 31732d59 wwlib!GetAllocCounters+0x7b023
001212b4 31926f9a wwlib!GetAllocCounters+0x4bf91
6bdff979 ff943888020000 call dword ptr <Unloaded_0.DLL>+0x287 (00000288)[eax+edi] ds:0023:06411288=????????
25](https://image.slidesharecdn.com/3-120804021425-phpapp01/85/3-25-320.jpg)
![Race Condition
int wmain(int argc, wchar_t *argv[]) DWORD WINAPI Crack(LPVOID Context)
{ {
ZwOpenKey = (_ZwOpenKey *) GetProcAddress(GetModuleHandle(L"ntdll.dll"), POBJECT_ATTRIBUTES oa = (POBJECT_ATTRIBUTES) Context;
"ZwOpenKey");
DWORD *ptr = (DWORD*)&oa->ObjectName->Buffer;
OBJECT_ATTRIBUTES oa;
wchar_t wcKeyName[] = L"REGISTRYMACHINESOFTWAREMicrosoftDrWatson";
UNICODE_STRING KeyName = { SetThreadPriority(GetCurrentThread(), THREAD_PRIORITY_HIGHEST);
sizeof wcKeyName - sizeof wcKeyName[0], SetEvent(hStartEvent);
sizeof wcKeyName,
wcKeyName
while ( true ) {
};
*ptr = 0x90909090;
if ( WaitForSingleObject(hStopEvent, 1) == WAIT_OBJECT_0 ) break;
DWORD ptr = (DWORD)KeyName.Buffer;
}
InitializeObjectAttributes(&oa, &KeyName, OBJ_CASE_INSENSITIVE, NULL, NULL);
return 0;
DWORD ThreadId;
}
HANDLE hThread = CreateThread(NULL, 0, Crack, &oa, 0, &ThreadId);
while ( !_kbhit() ) {
HANDLE hKey;
oa.ObjectName->Buffer
NTSTATUS rc = ZwOpenKey(&hKey, STANDARD_RIGHTS_READ, &oa);
if ( !NT_SUCCESS(rc) )
printf("Error: %xn", rc);
else {
CloseHandle(hKey);
}}
...
return 0;}
26](https://image.slidesharecdn.com/3-120804021425-phpapp01/85/3-26-320.jpg)









