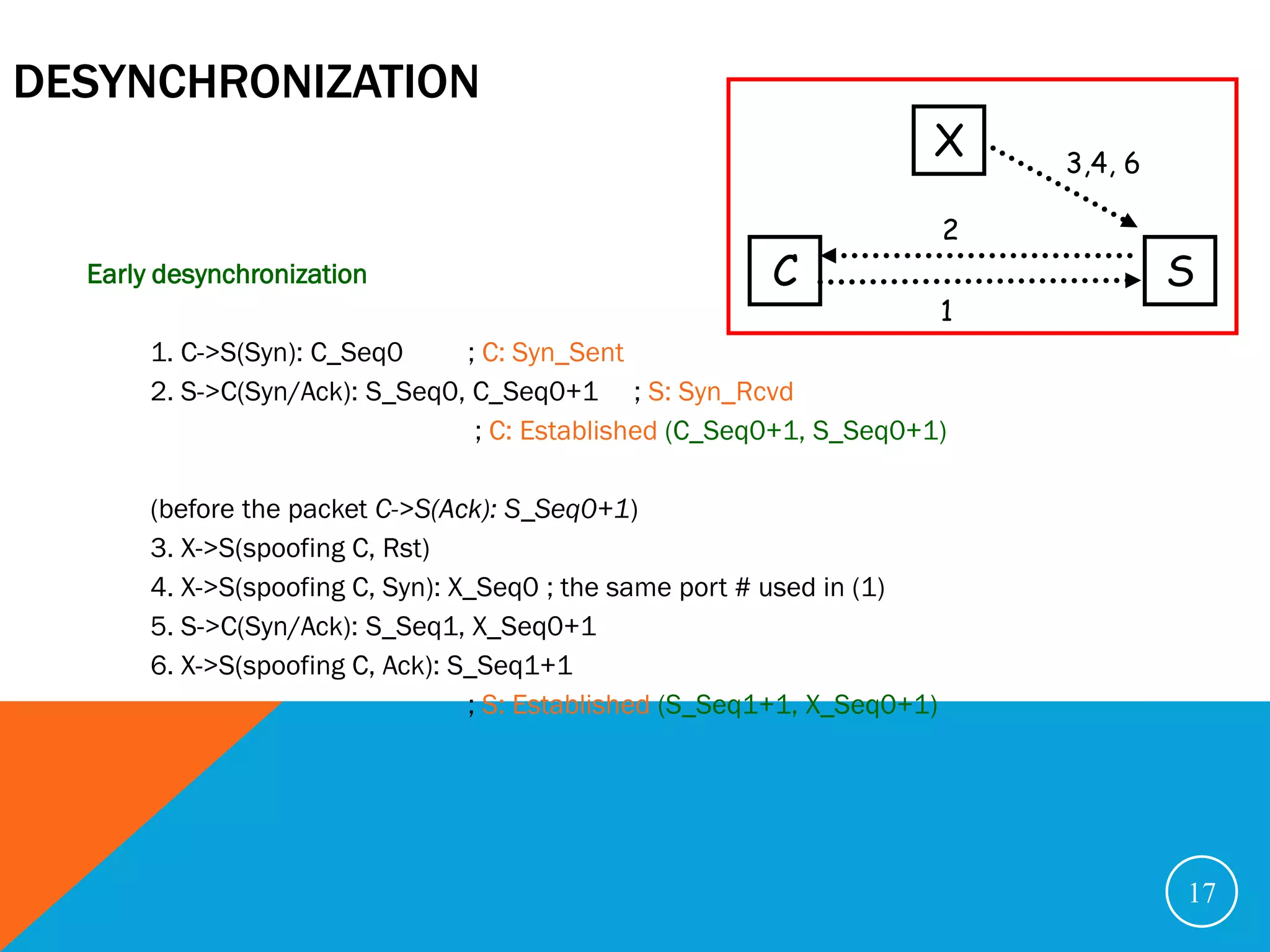
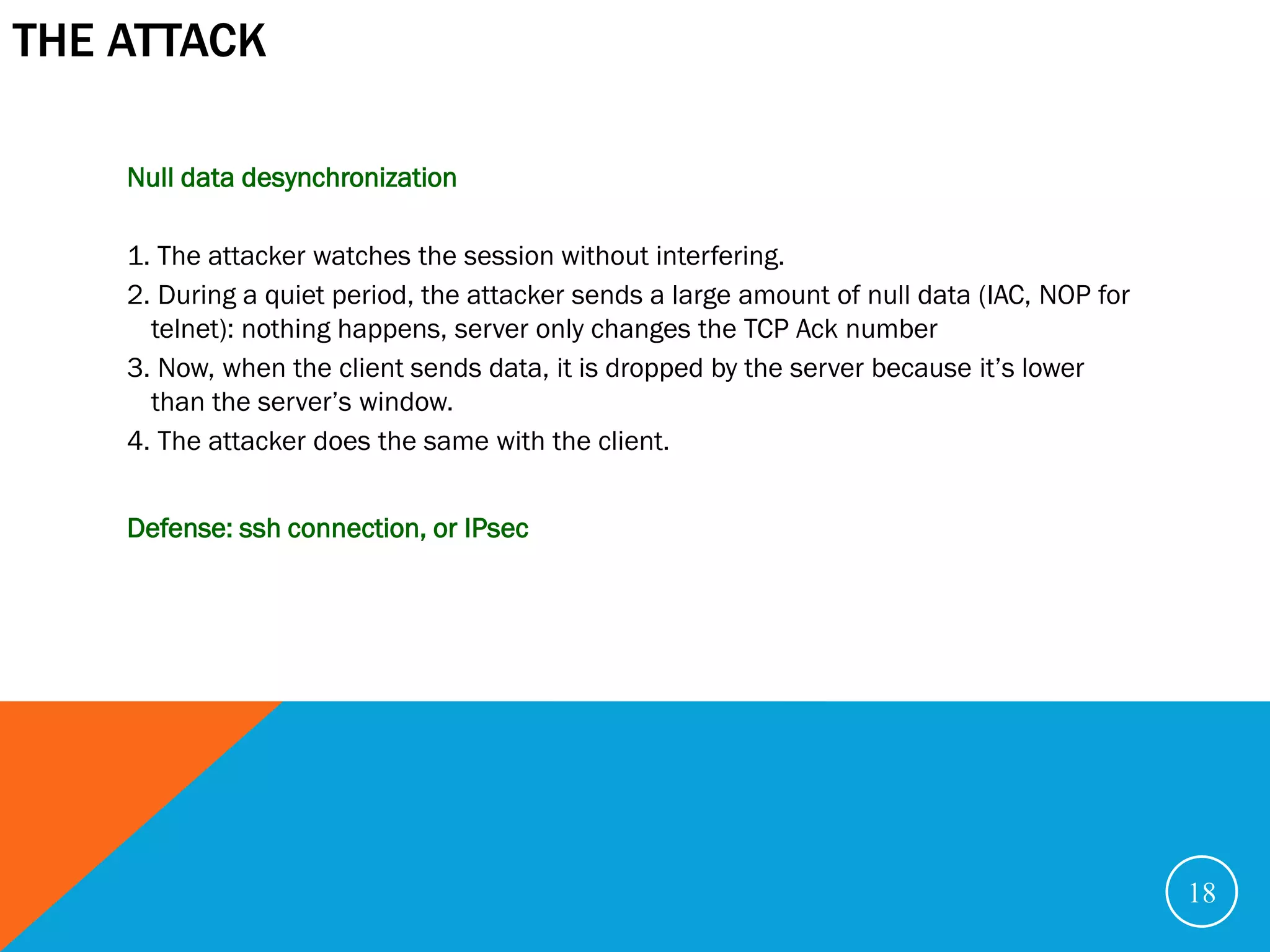
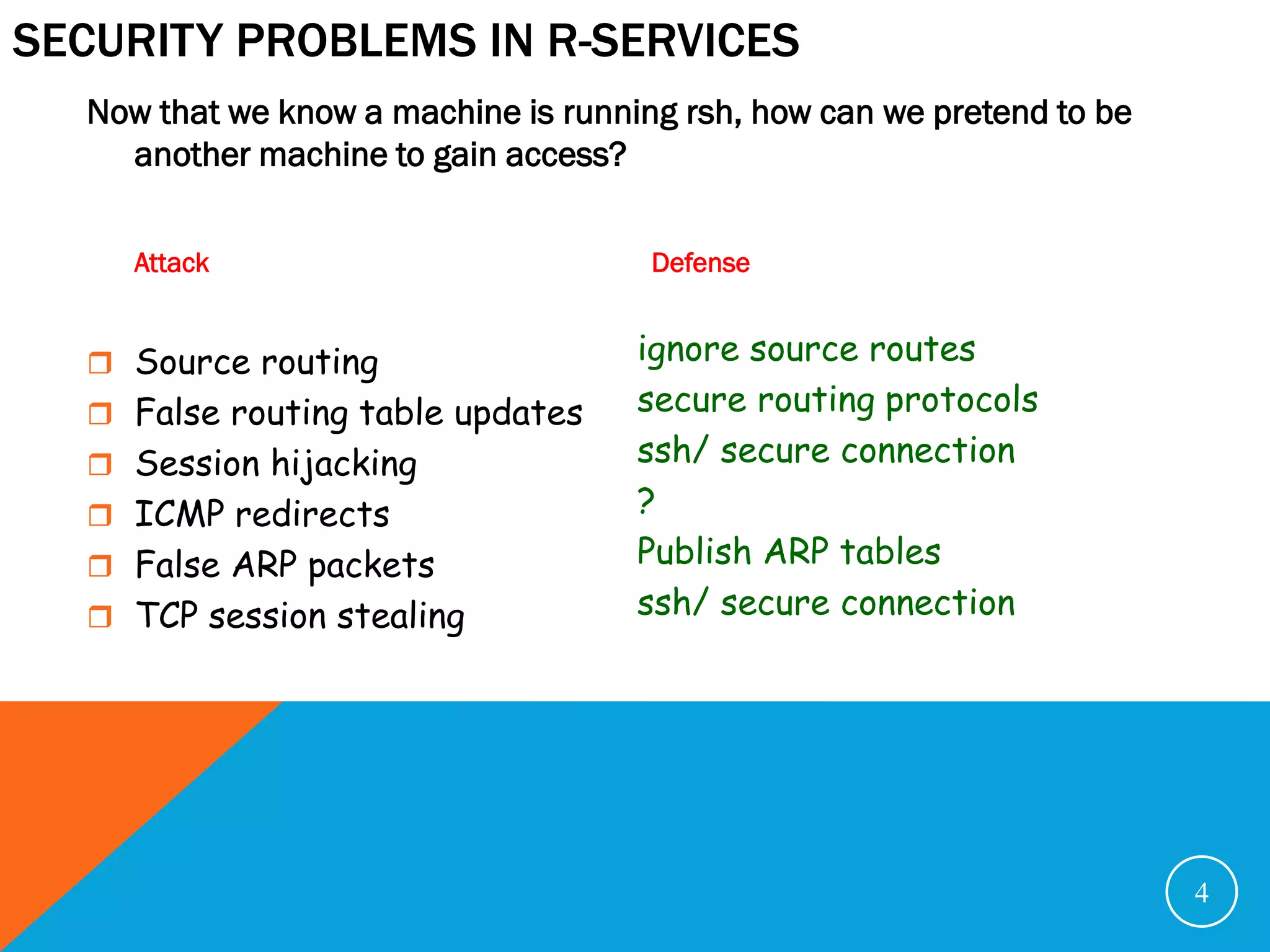
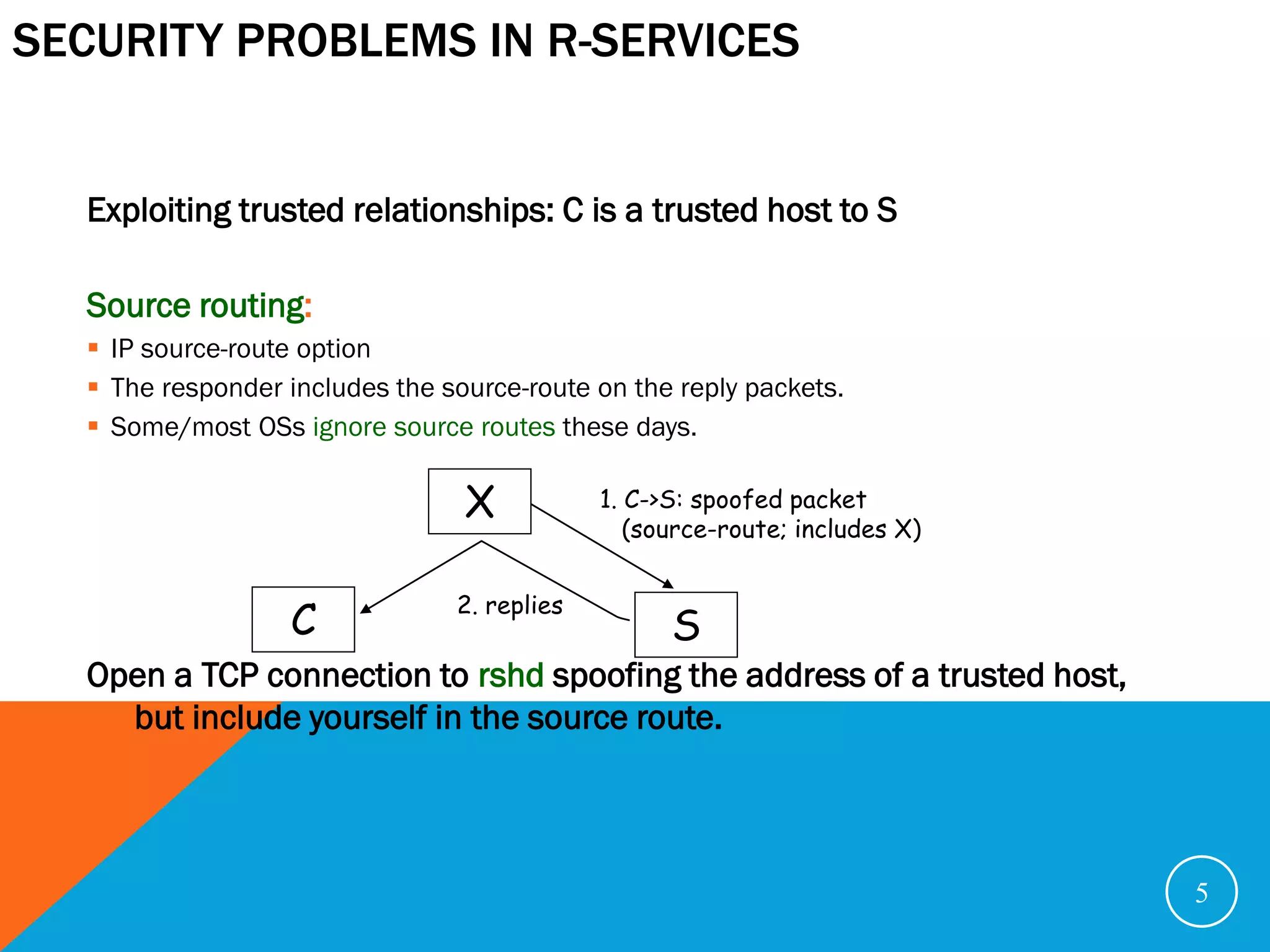
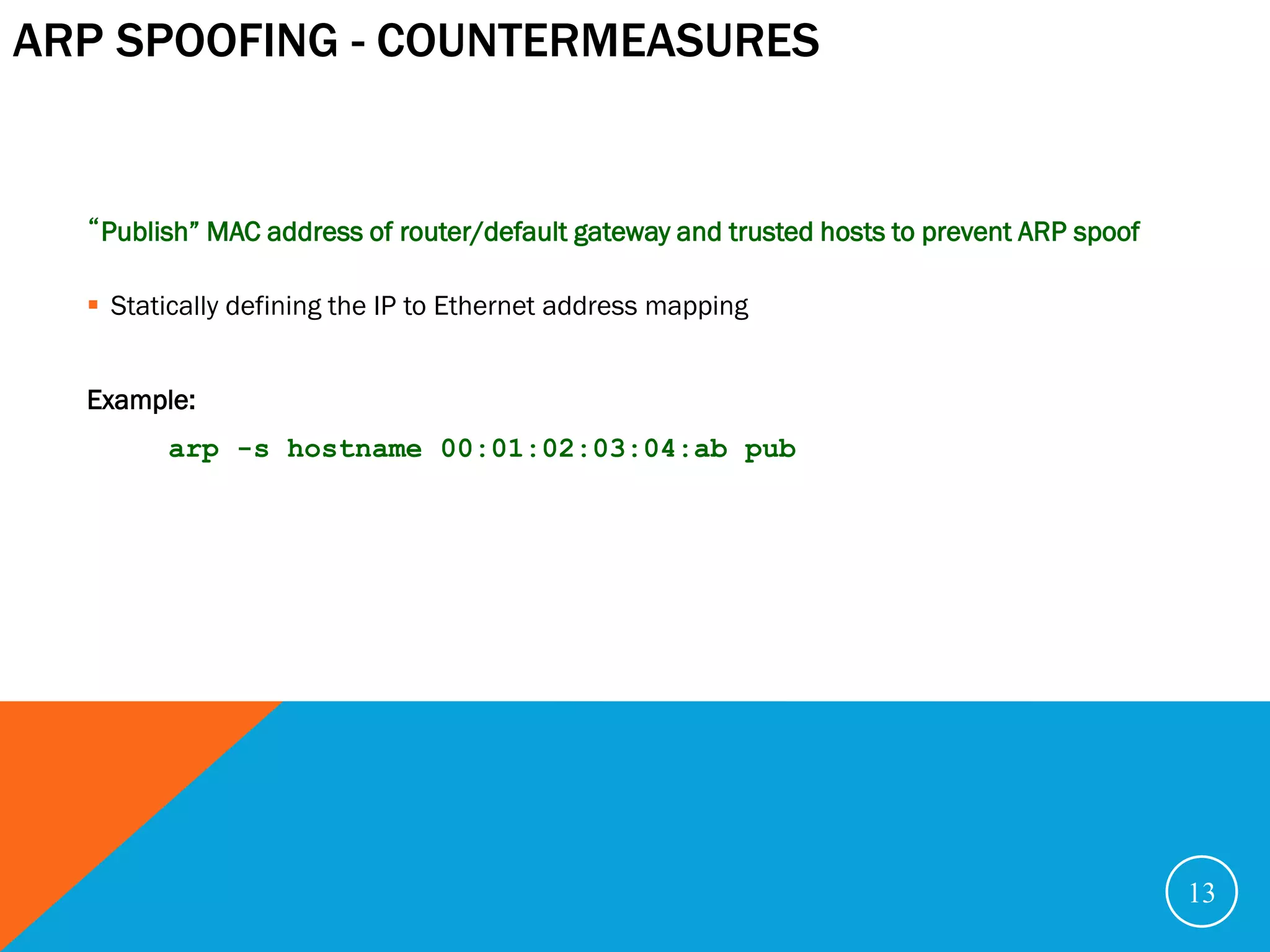
The document discusses various security problems relating to the TCP/IP protocol suite, focusing on vulnerabilities in R-services such as session hijacking, source routing, and ARP spoofing. It emphasizes methods of exploiting trusted relationships to gain unauthorized access and details defenses against these attacks, advocating for secure routing protocols and SSH connections. The document also outlines TCP session stealing, describing how desynchronization can be used to manipulate traffic between a client and a server.



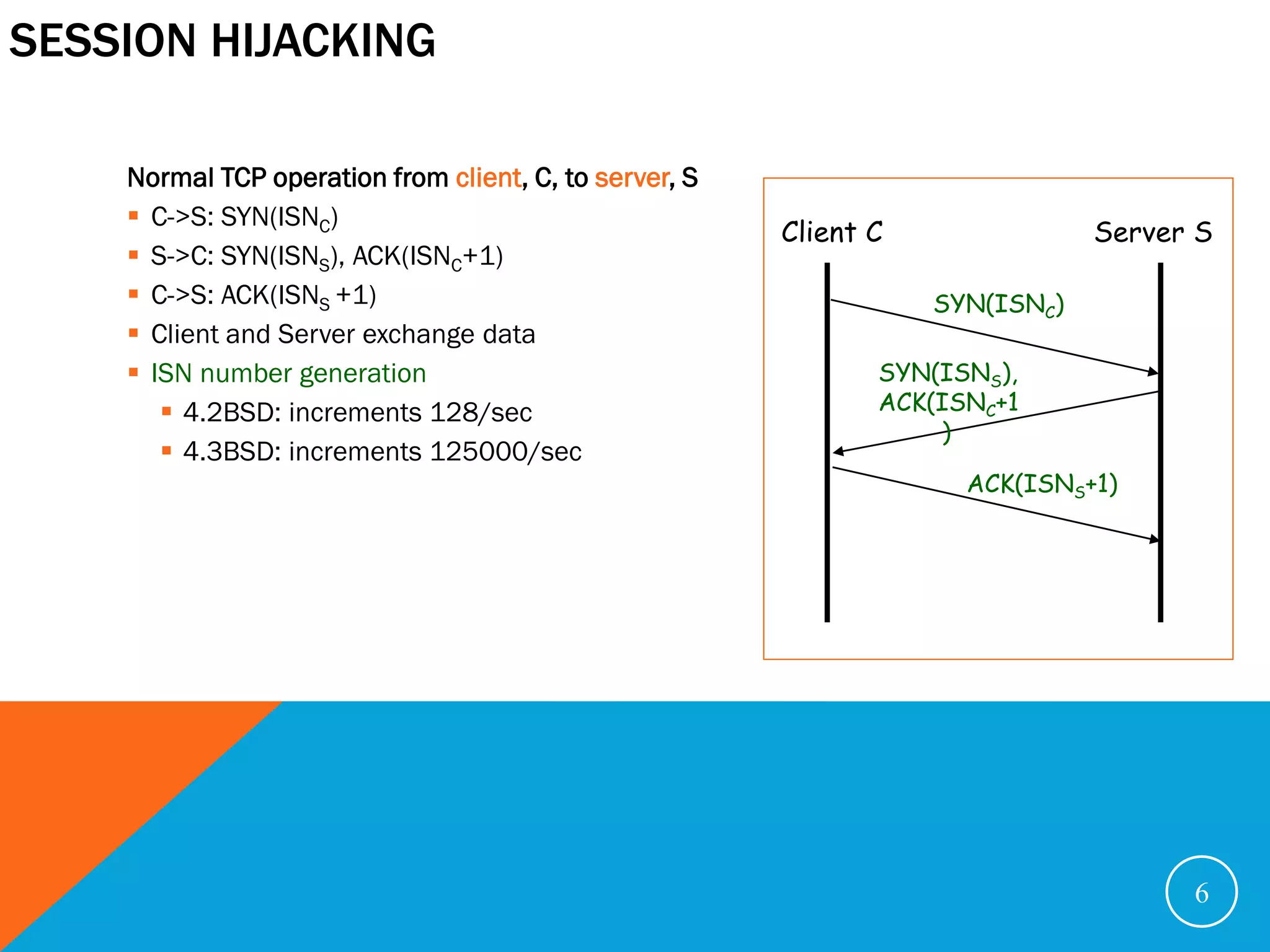
![SESSION HIJACKING
Session hijacking: Find a machine, C, that’s down, guess the ISN. Usually in regular
increments.
X->S: SYN(ISNX) [spoofs C] S: rshd server
S->C: SYN(ISNS), ACK(ISNX +1)
X->S: ACK(ISNS +1) [spoofs C; estimates ISNS]
X->S: [ echo “* *” >> ~/.rhosts] [spoofs C]
X->S: RESET [spoofs C]
X rlogins from anywhere in the world.
X 3. SYN(5000), ACK(1001)
1. ISN estimation: 1: Disables C
2. SYN(1000)
C S
Trusted relationship
7](https://image.slidesharecdn.com/securityproblemsintcp-ip-121104201622-phpapp01/75/Security-problems-in-TCP-IP-7-2048.jpg)
![SESSION HIJACKING
2. Session hijacking:
X
6: ACK(ISNS +1)
(spoofs C; estimates ISNS)
4: SYN(ISNX)
(spoofs C)
C S
5: SYN(ISNS), ACK(ISNX+1)
3. Executes remote commands:
X
7: [echo “* *” >> ~/.rhosts]
(spoofs C)
8: RESET
(spoofs C)
C S 8](https://image.slidesharecdn.com/securityproblemsintcp-ip-121104201622-phpapp01/75/Security-problems-in-TCP-IP-8-2048.jpg)


![TCP SESSION STEALING
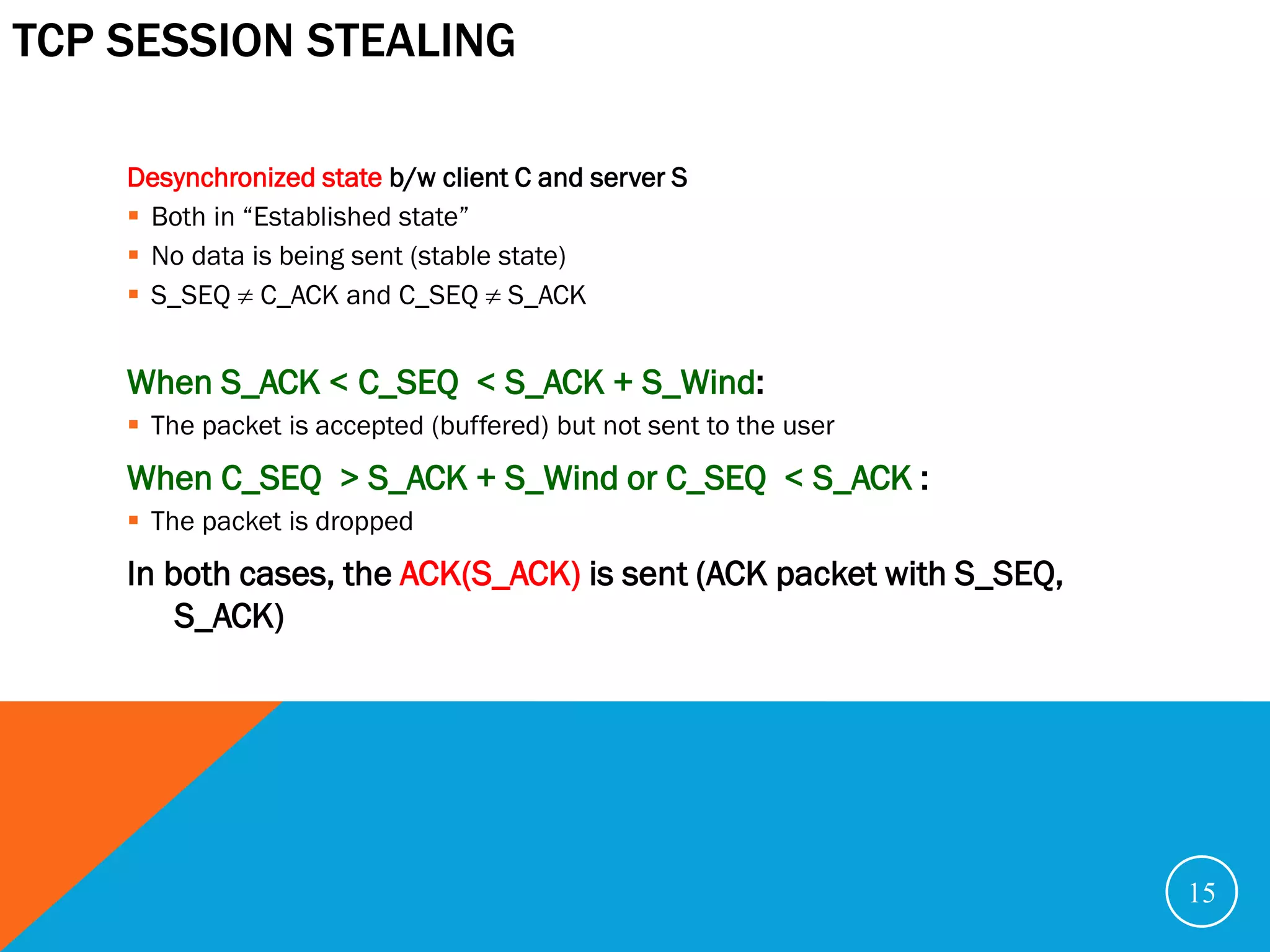
In a desynchronized state, the attacker can send any acceptable data to the server
E.g. [echo myhost >> ~/.rhost] for rlogin
X 2: X->S (spoofing C): S_ACK, S_SEQ
1: C->S: C_SEQ, C_ACK
[echo myhost >> ~/.rhost]
(accepted)
(dropped)
C S
C_SEQ, C_ACK S_SEQ, S_ACK
S_SEQ C_ACK and C_SEQ S_ACK
16](https://image.slidesharecdn.com/securityproblemsintcp-ip-121104201622-phpapp01/75/Security-problems-in-TCP-IP-16-2048.jpg)