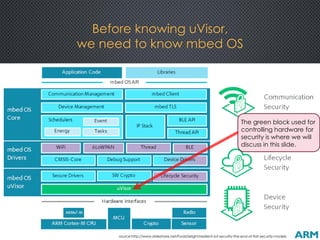
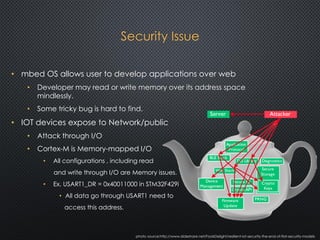
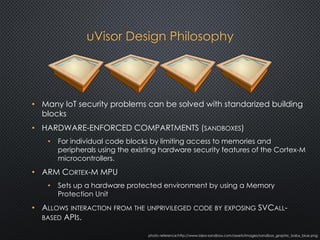
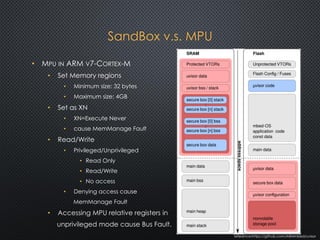
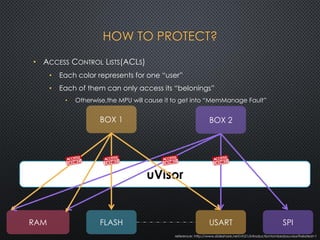
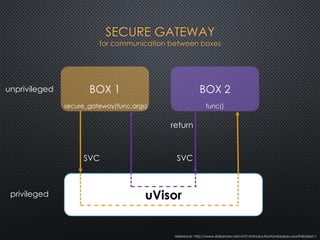
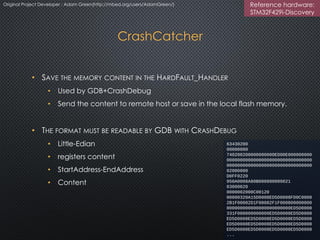
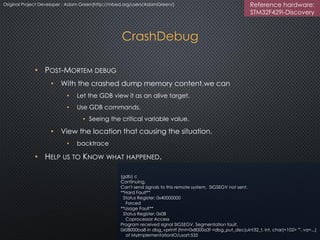
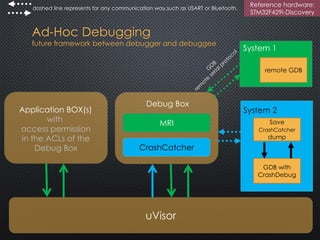
The document discusses the ARM uVisor debug refinement project presented at the 2016 Information Technology Conference in Taiwan, focusing on security issues related to IoT devices and the design philosophy of uVisor. It outlines how memory protection and access control can mitigate vulnerabilities in embedded applications through hardware-enforced compartments and describes various debugging tools and methods for Cortex-M devices, including crash debugging and remote debugging capabilities. The presentation emphasizes the importance of secure and effective debugging practices in IoT development, showcasing the uVisor as a solution to enhance security and facilitate better debugging techniques.