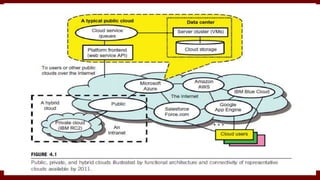
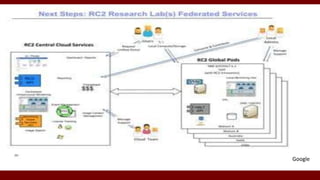
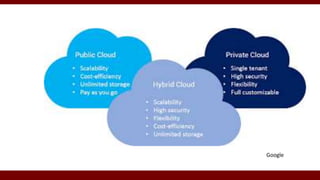
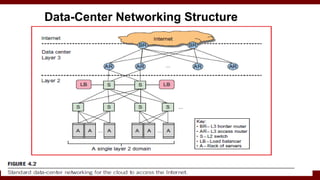
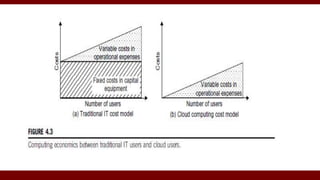
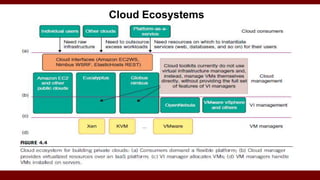
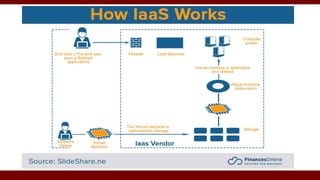
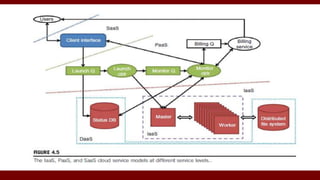
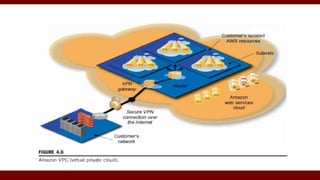
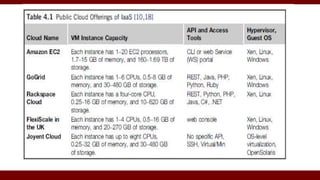
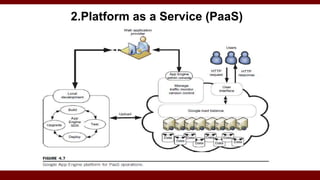
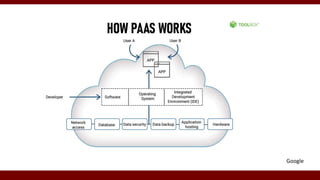
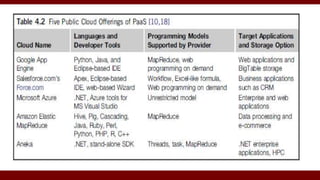
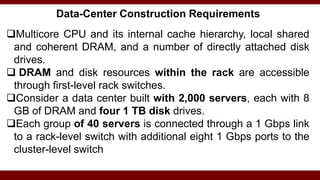
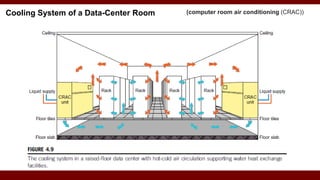
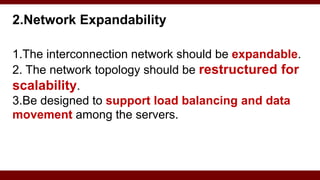
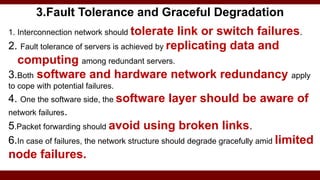
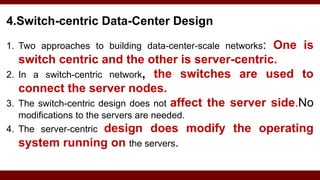
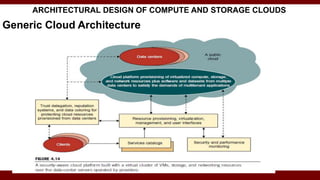
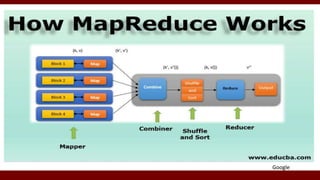
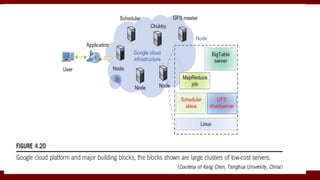
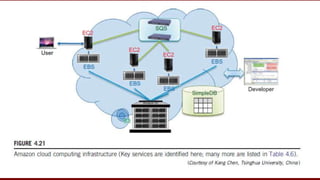
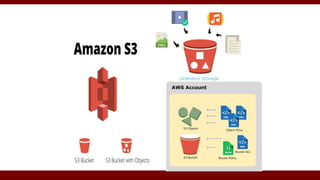
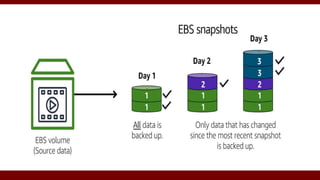
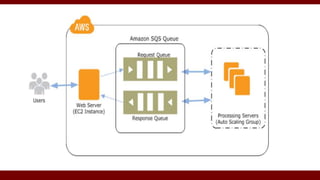
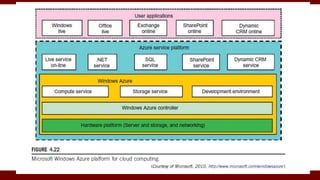
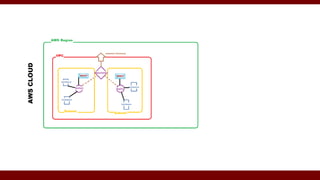
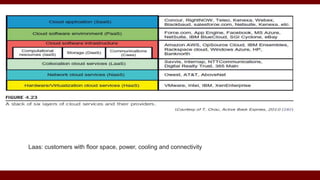
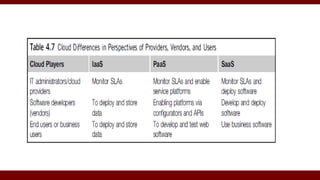
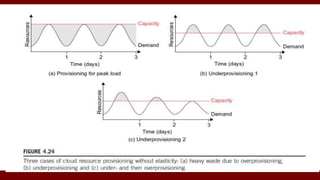
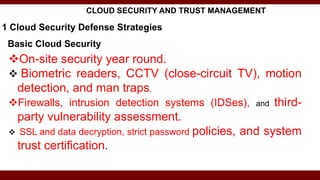
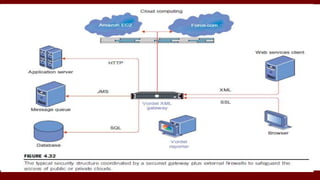
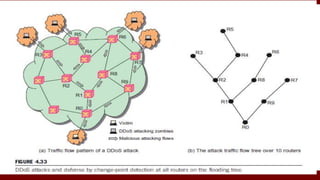
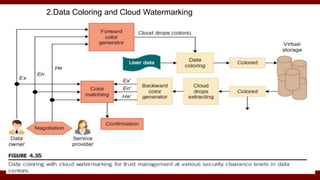
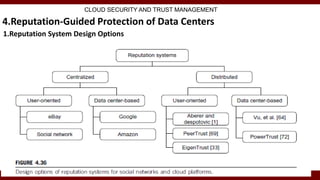
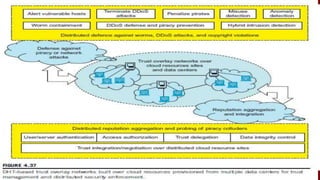
The document discusses cloud computing service models, including public, private, and hybrid clouds, and their characteristics. It provides an overview of infrastructure-as-a-service (IaaS), platform-as-a-service (PaaS), and software-as-a-service (SaaS), along with insights into data-center design, architecture challenges, and cloud security. Key cloud platforms like Google App Engine, Amazon Web Services, and Microsoft Azure are also highlighted for their roles in delivering these services.