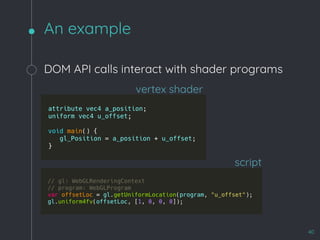
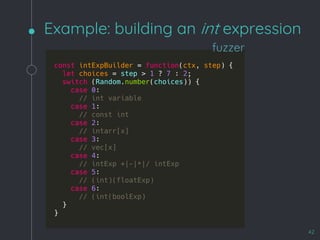
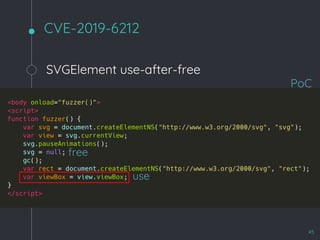
This document discusses fuzzing techniques for DOM and WebGL. It proposes an emulation-based approach to generate test cases that take into account runtime context like element states and relationships. Examples are given for fuzzing SVG and WebGL. Case studies of past DOM bugs involving use-after-free and out-of-bounds writes are also presented. The document concludes by thanking contributors to the field of DOM fuzzing.


![Domato – Google Project Zero [2017]
8
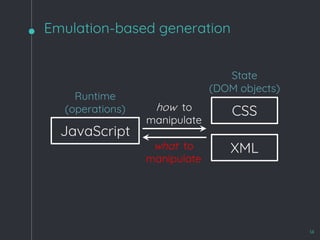
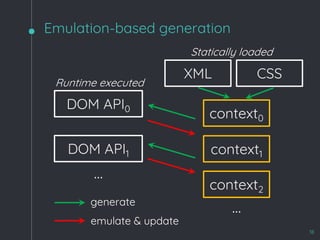
A generation-based approach
Fuzzer
Static grammar HTML
Browser
https://github.com/googleprojectzero/domato](https://image.slidesharecdn.com/zerocon2019-190625152624/85/Zero-con2019-4-320.jpg)


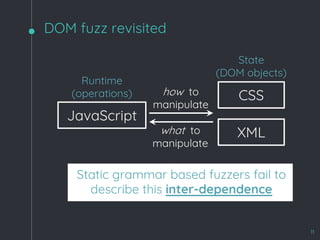
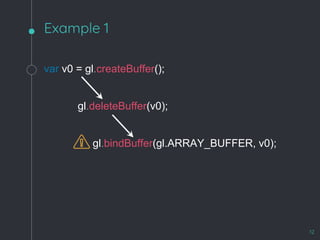
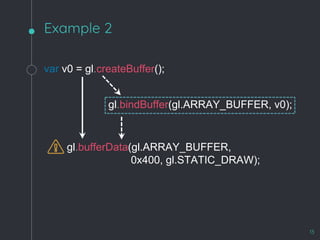




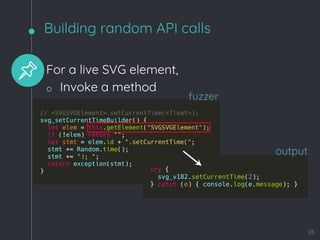
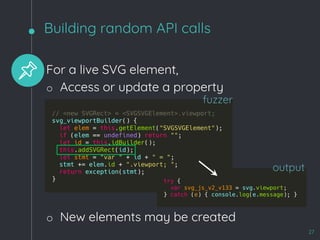
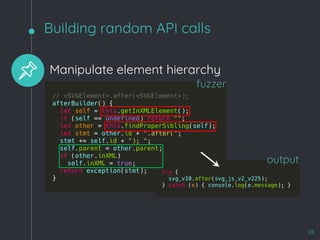



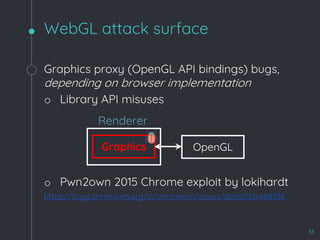
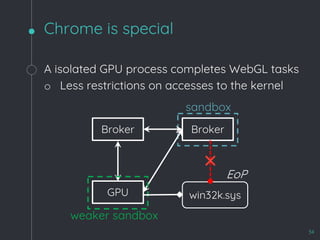

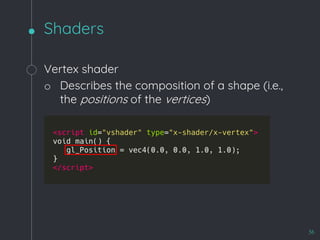
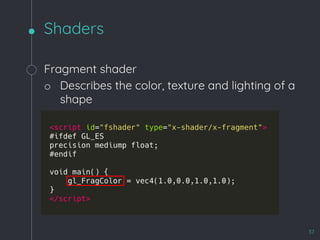







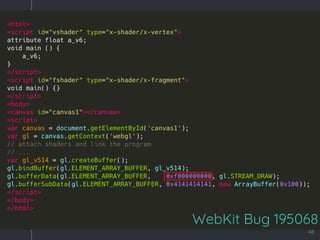
![WebKit Bug 195068
49
[*]: byteLength is a 64bit uint](https://image.slidesharecdn.com/zerocon2019-190625152624/85/Zero-con2019-45-320.jpg)
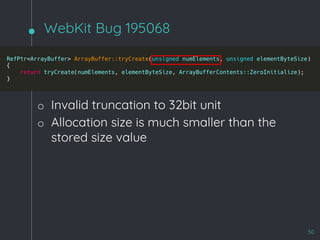
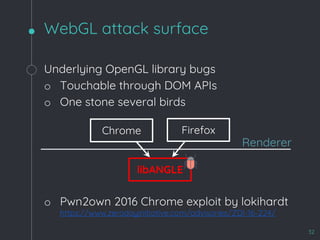
![WebKit Bug 195068
51
[*]
[*]: m_byteLength = 0xf00000000 >> 0x41414141
o Write arbitrary values at arbitrary offsets à RCE
o Triggerable on Linux only
§ The OpenGL library on mac does not support a
WebGL buffer of more than 4G](https://image.slidesharecdn.com/zerocon2019-190625152624/85/Zero-con2019-47-320.jpg)

