Embed presentation
Download as PDF, PPTX

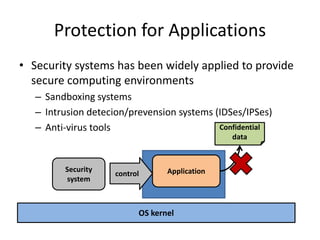
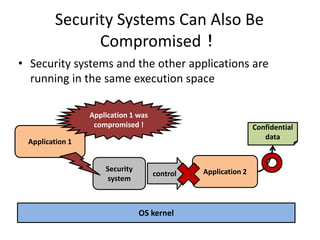
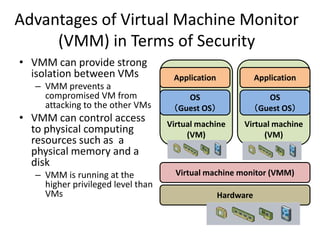
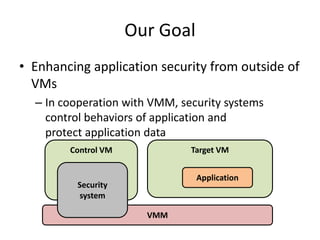


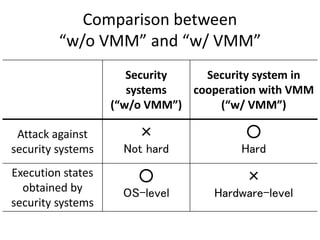
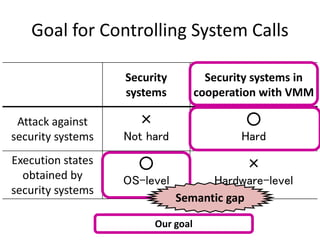
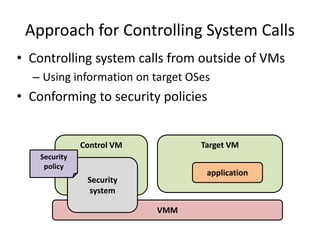
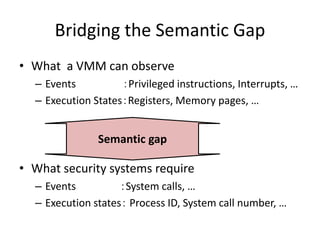
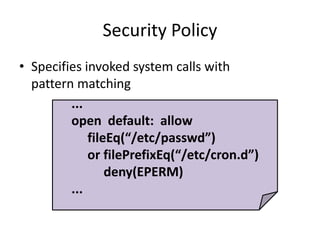

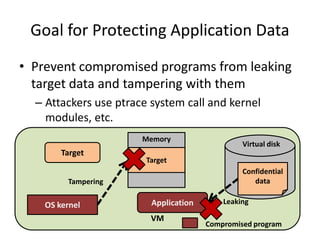
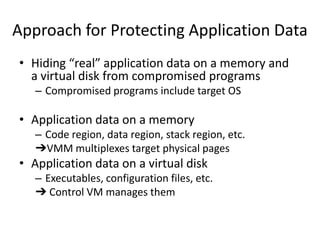
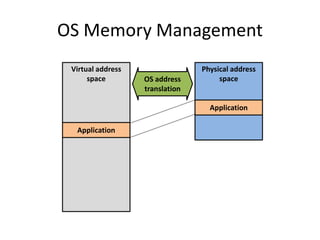
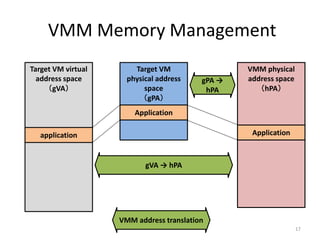
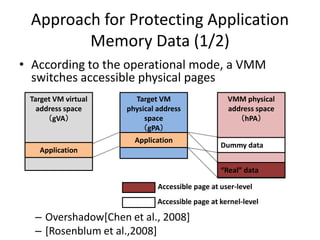
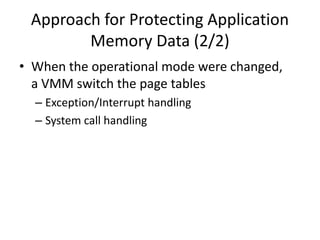
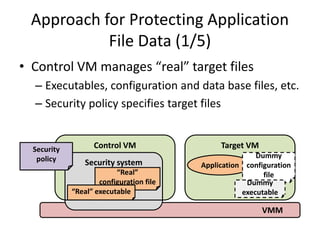
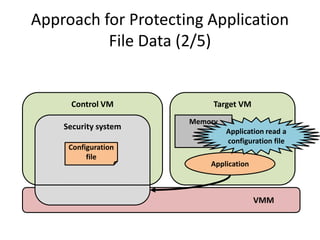
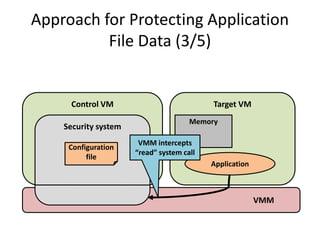
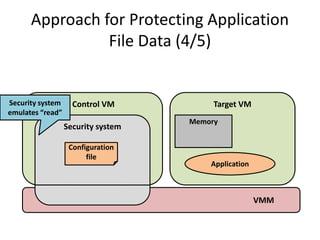
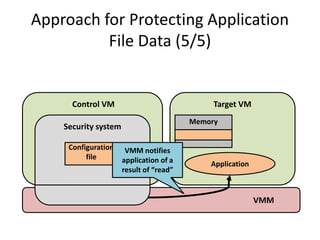



This document discusses enhancing application security within virtual machines. It proposes controlling system calls from outside of target VMs to confine application behaviors. It also proposes controlling memory and file operations related to target applications using a virtual machine monitor and control VM to prevent non-target programs from leaking or tampering with target application data. The goal is to bridge the semantic gap between what a VMM can observe at the hardware level and what security systems require at the application level to enforce security policies.

























