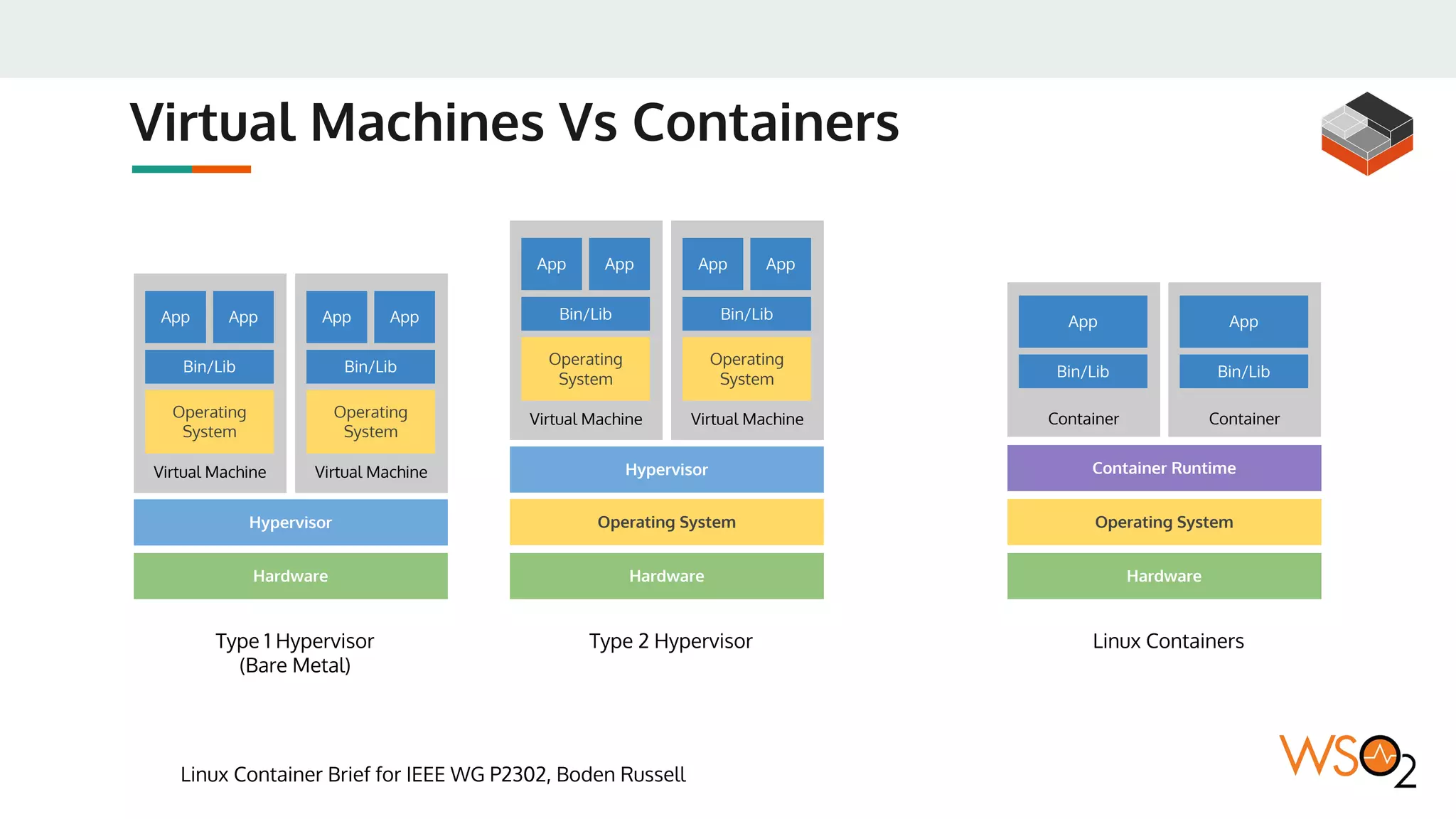
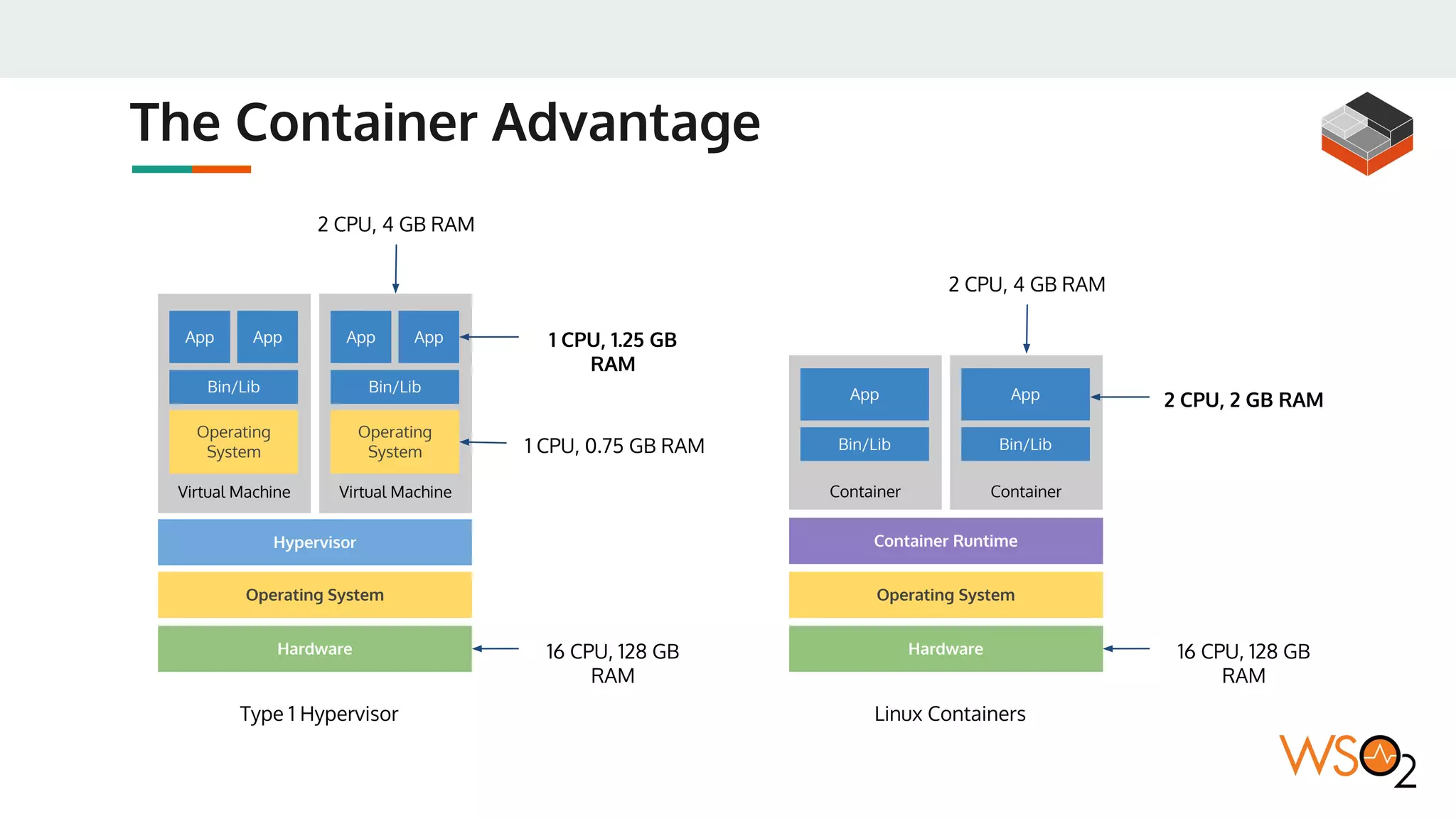
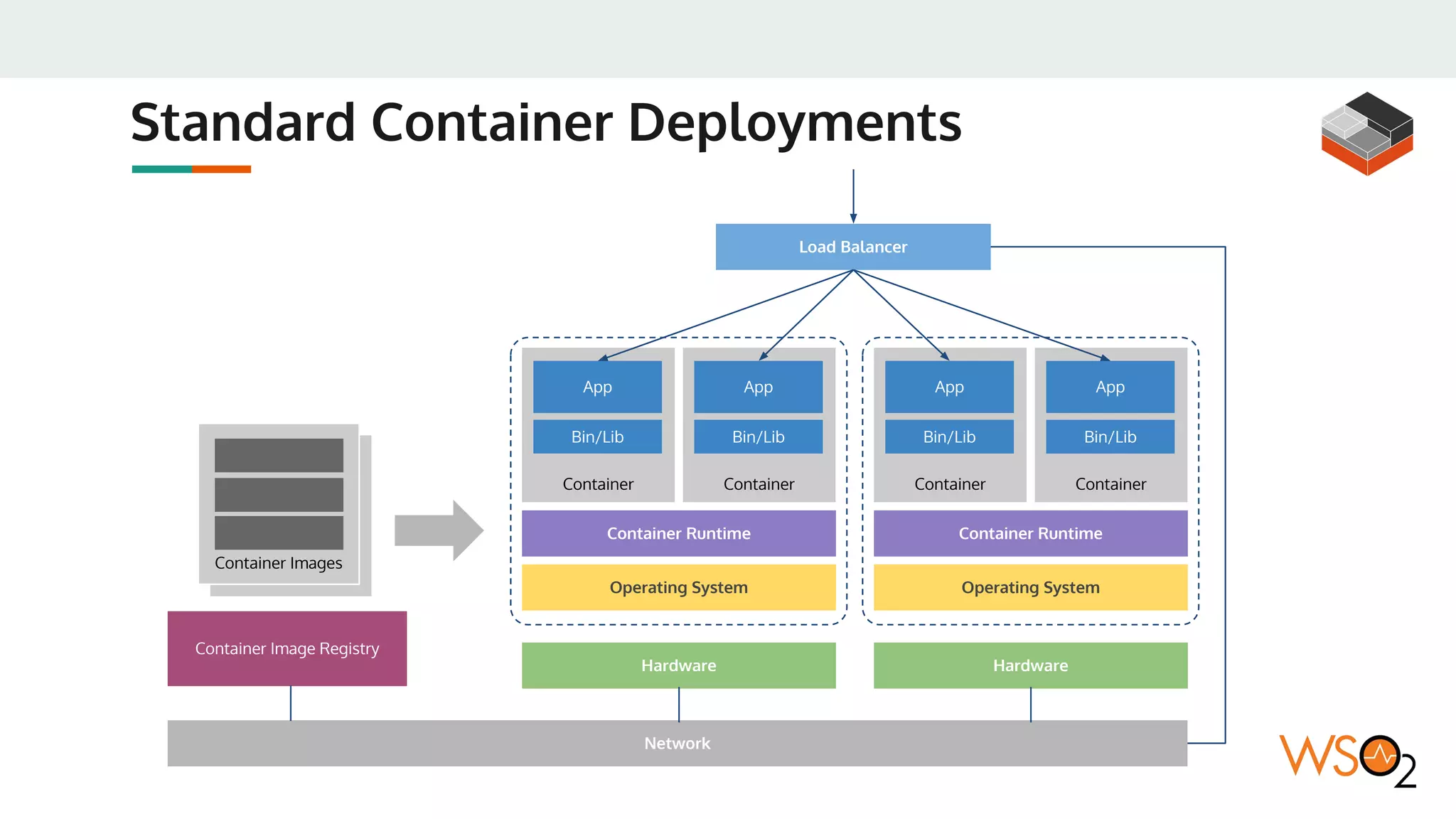
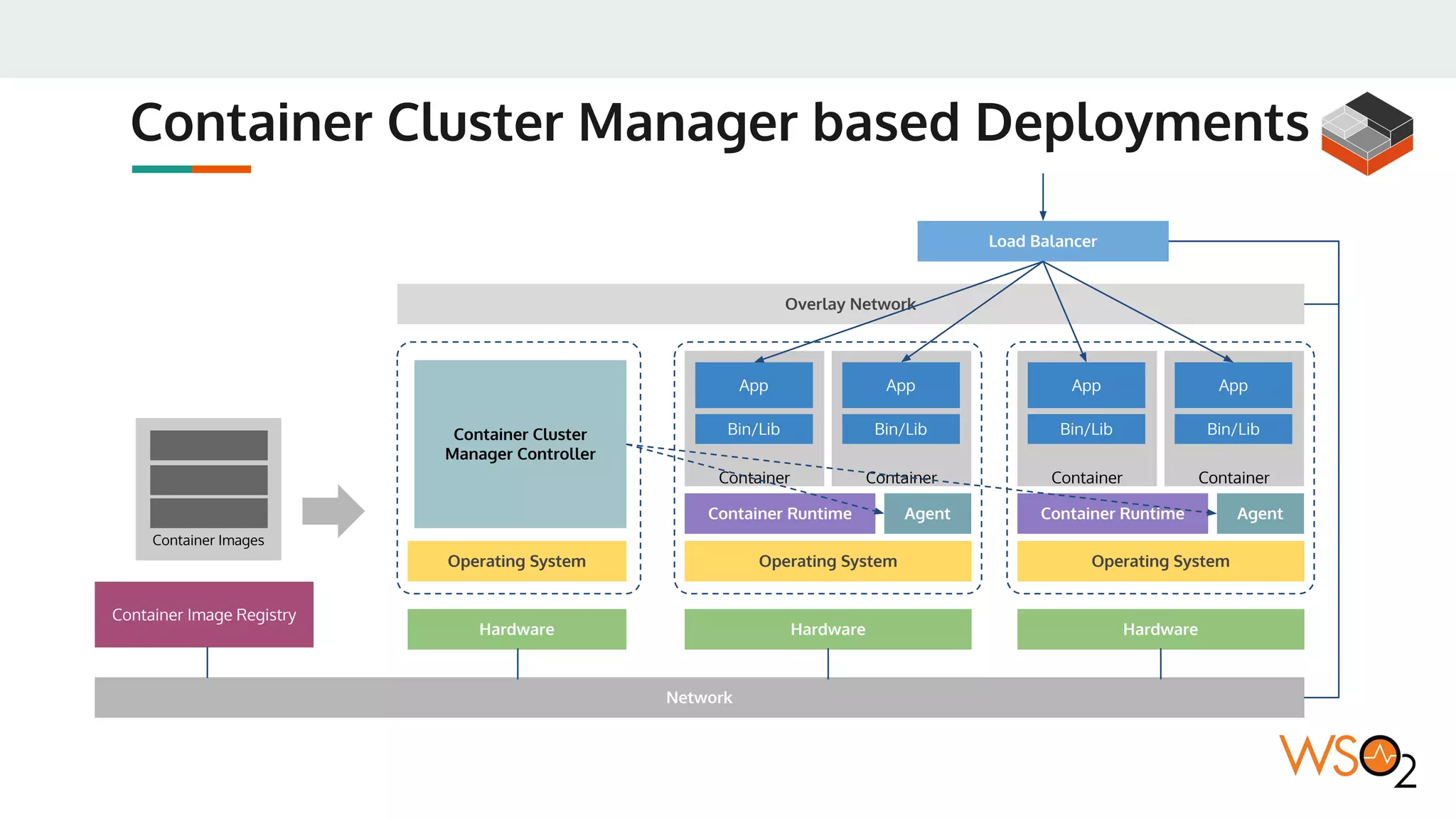
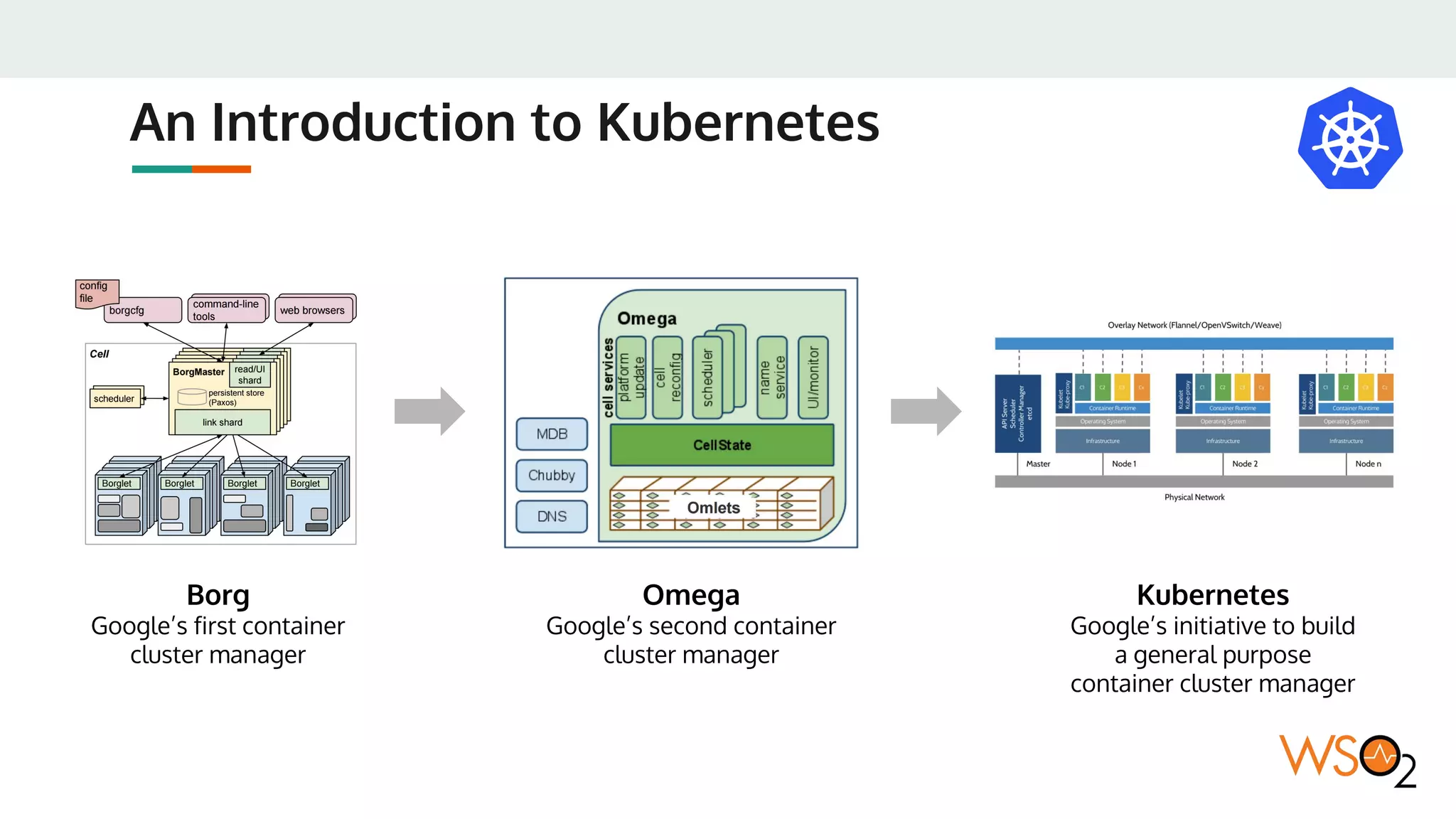
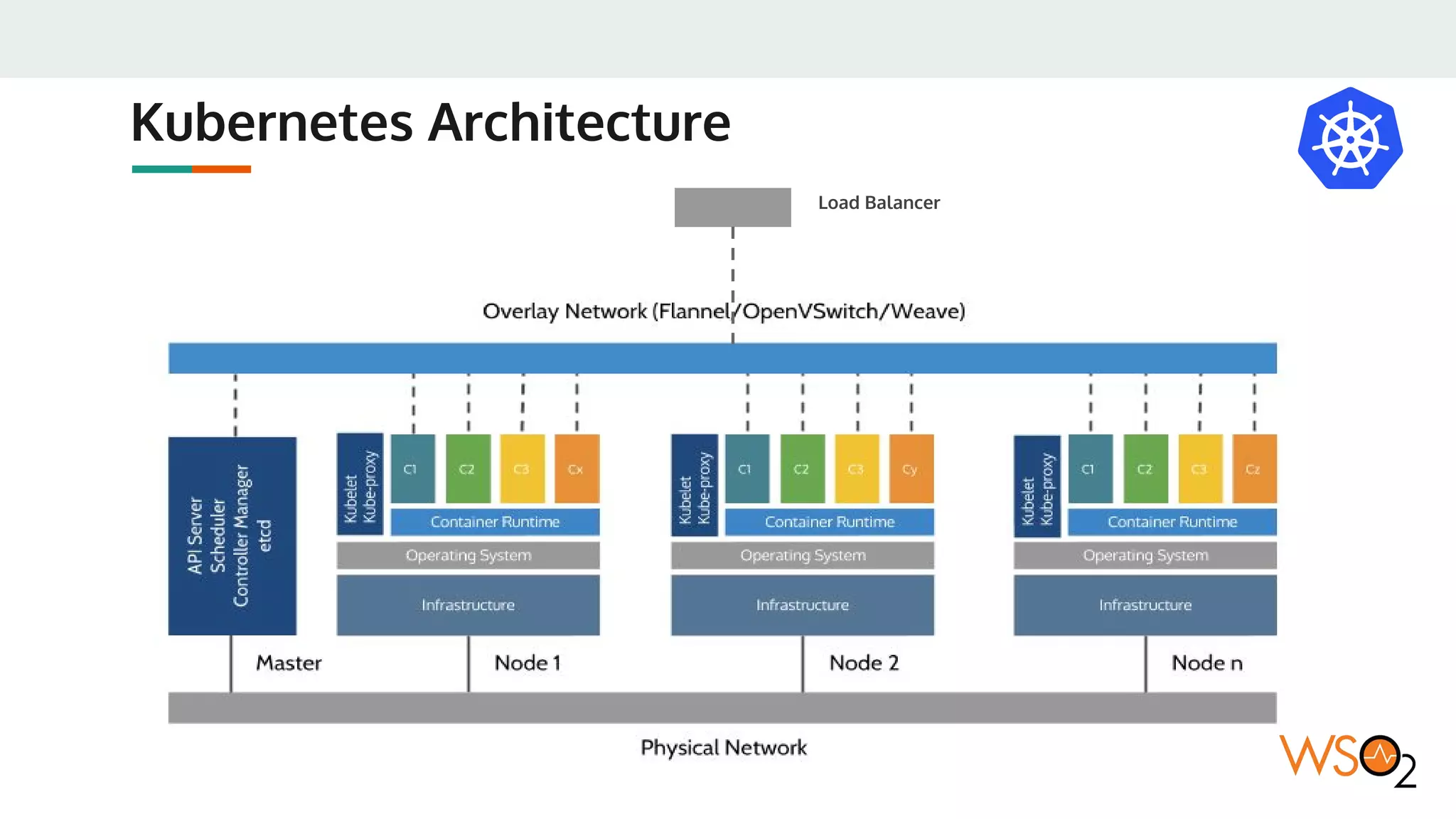
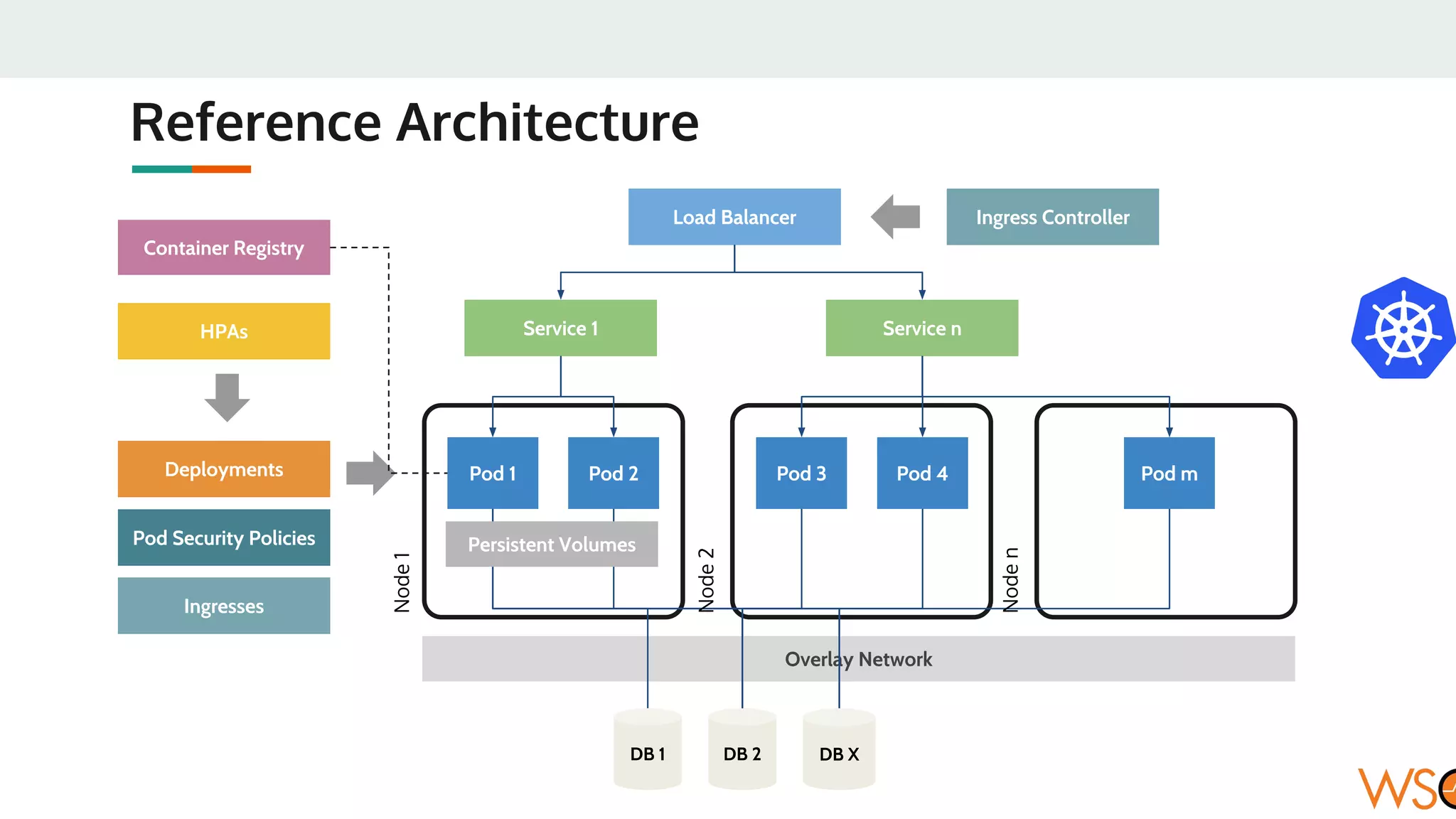
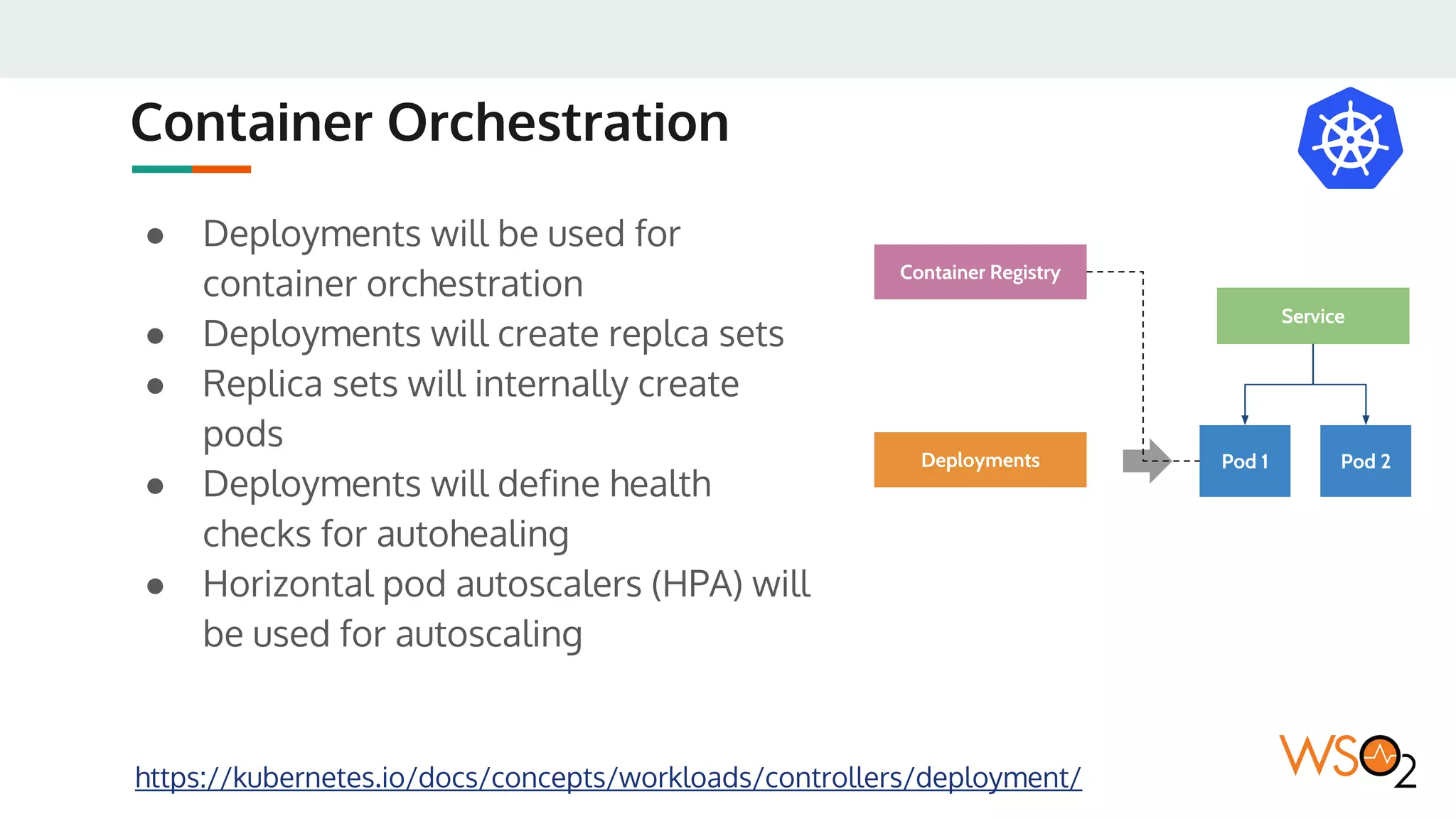
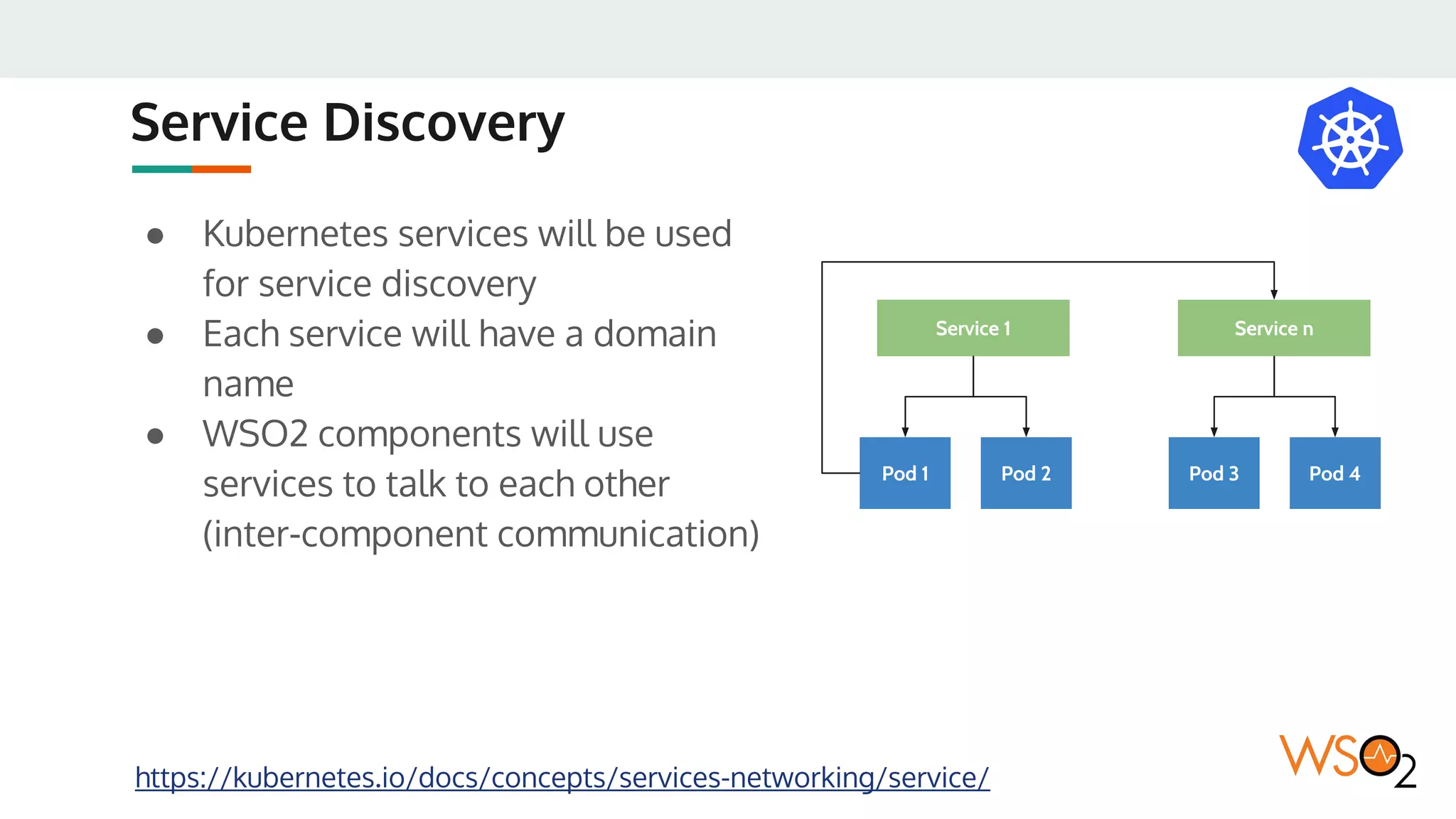
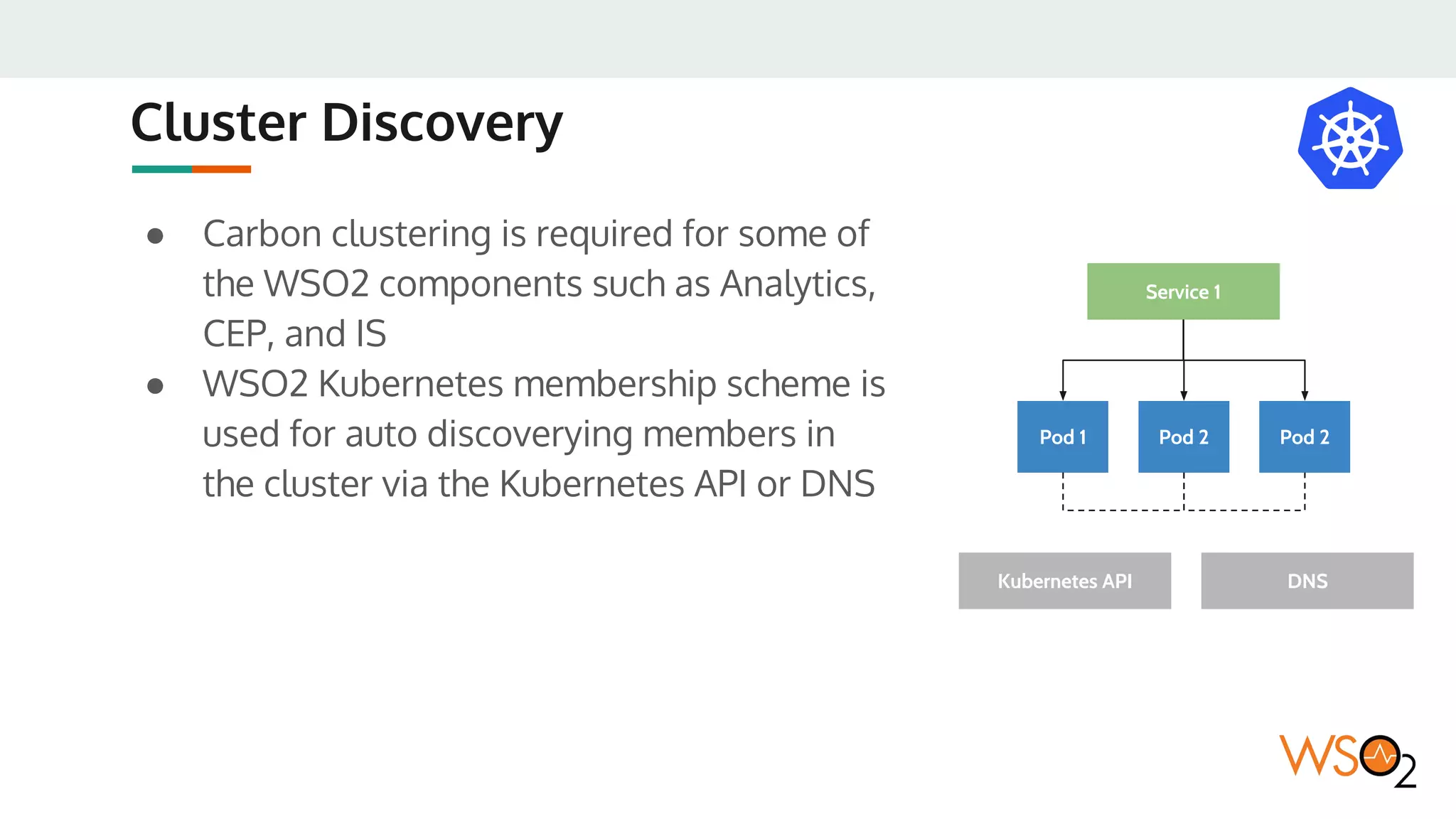
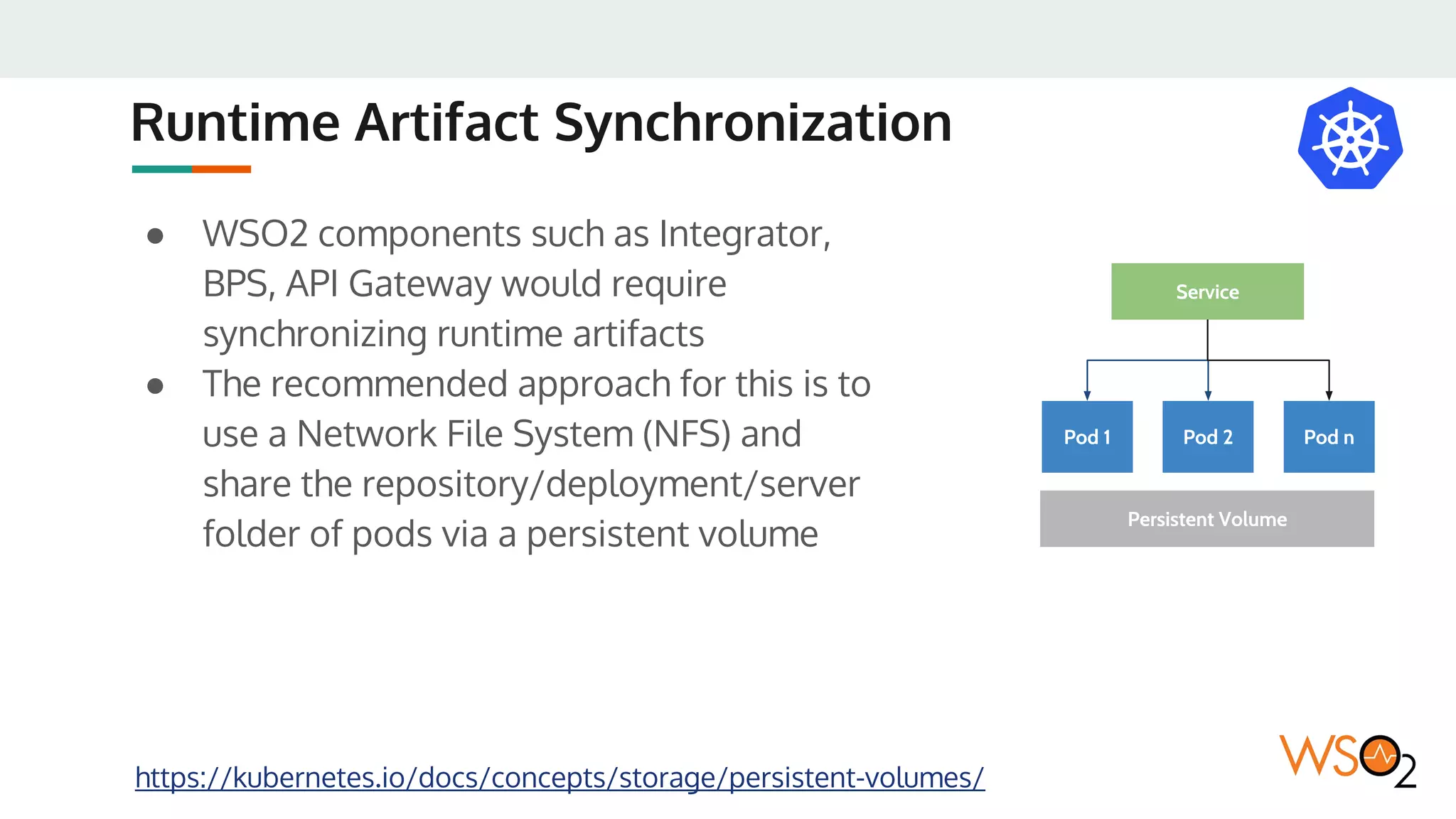
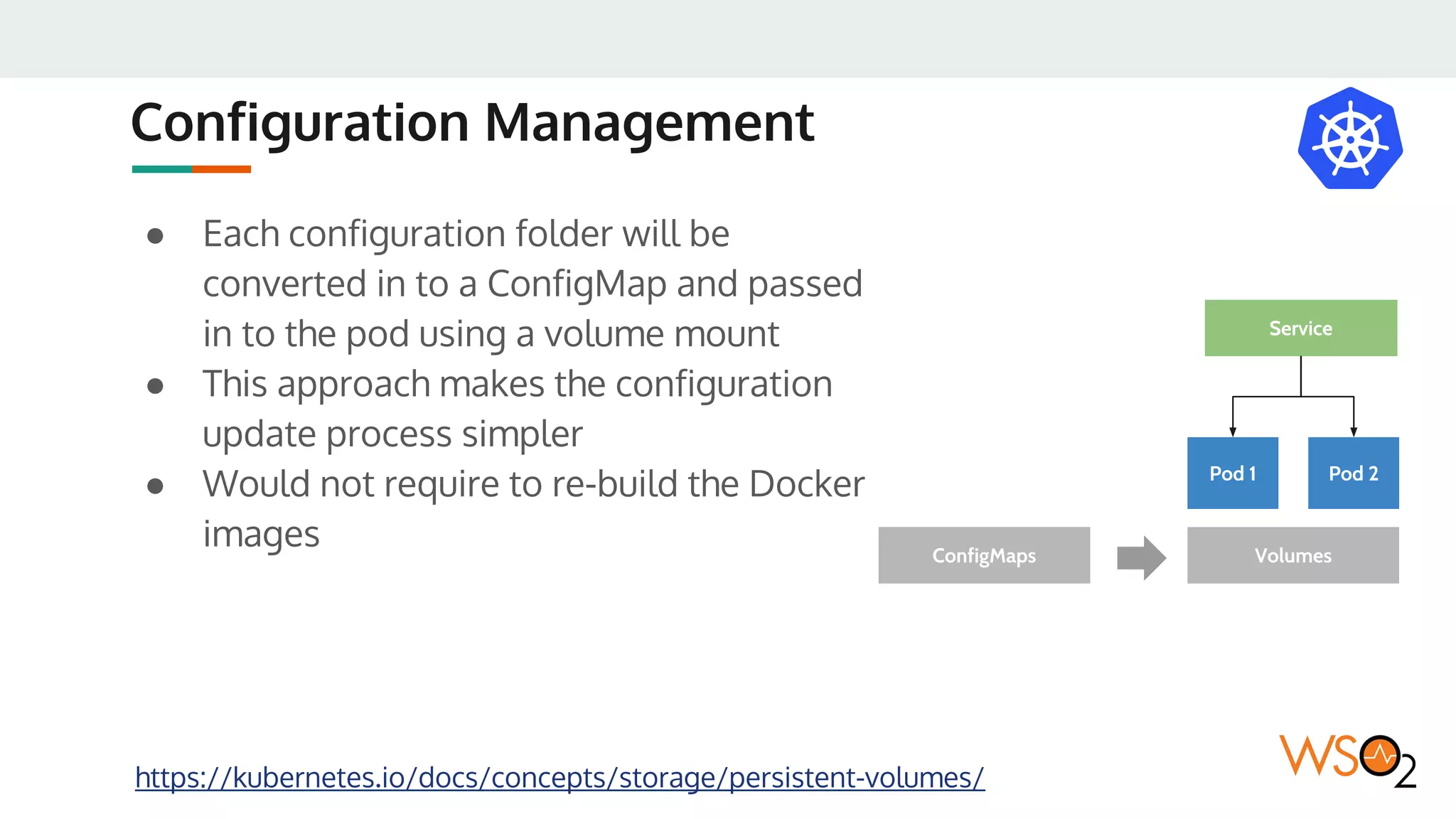
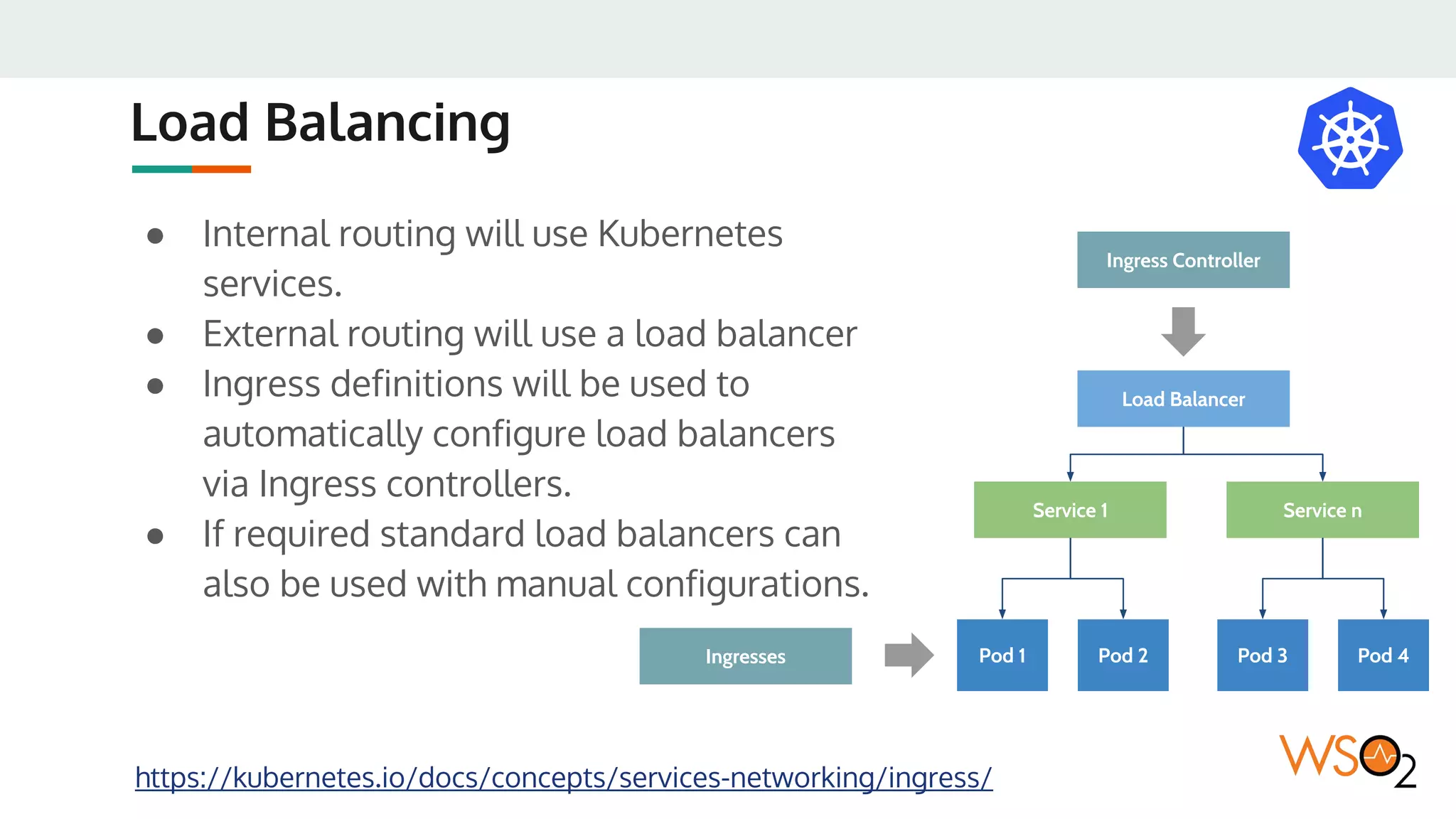
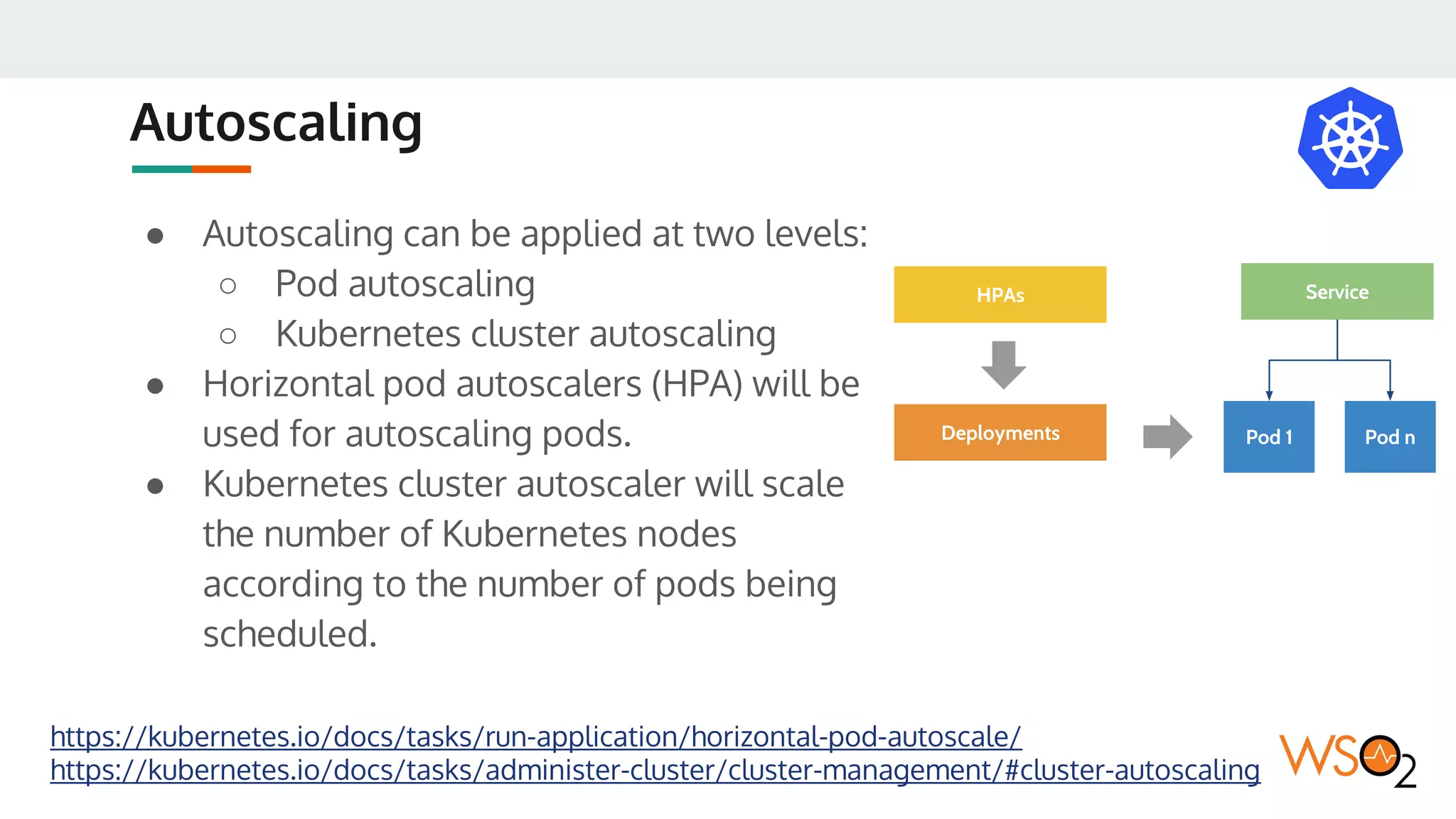
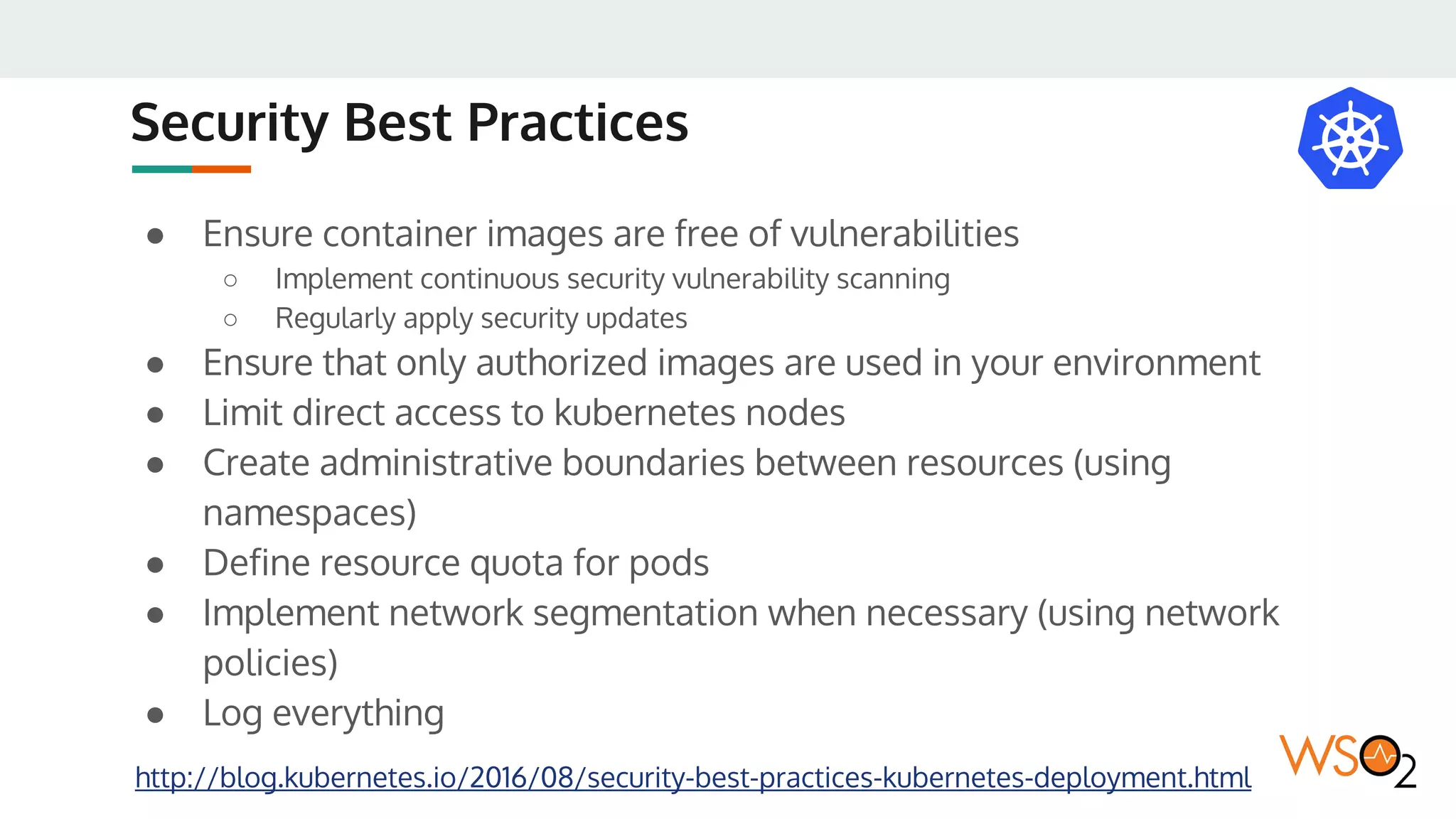
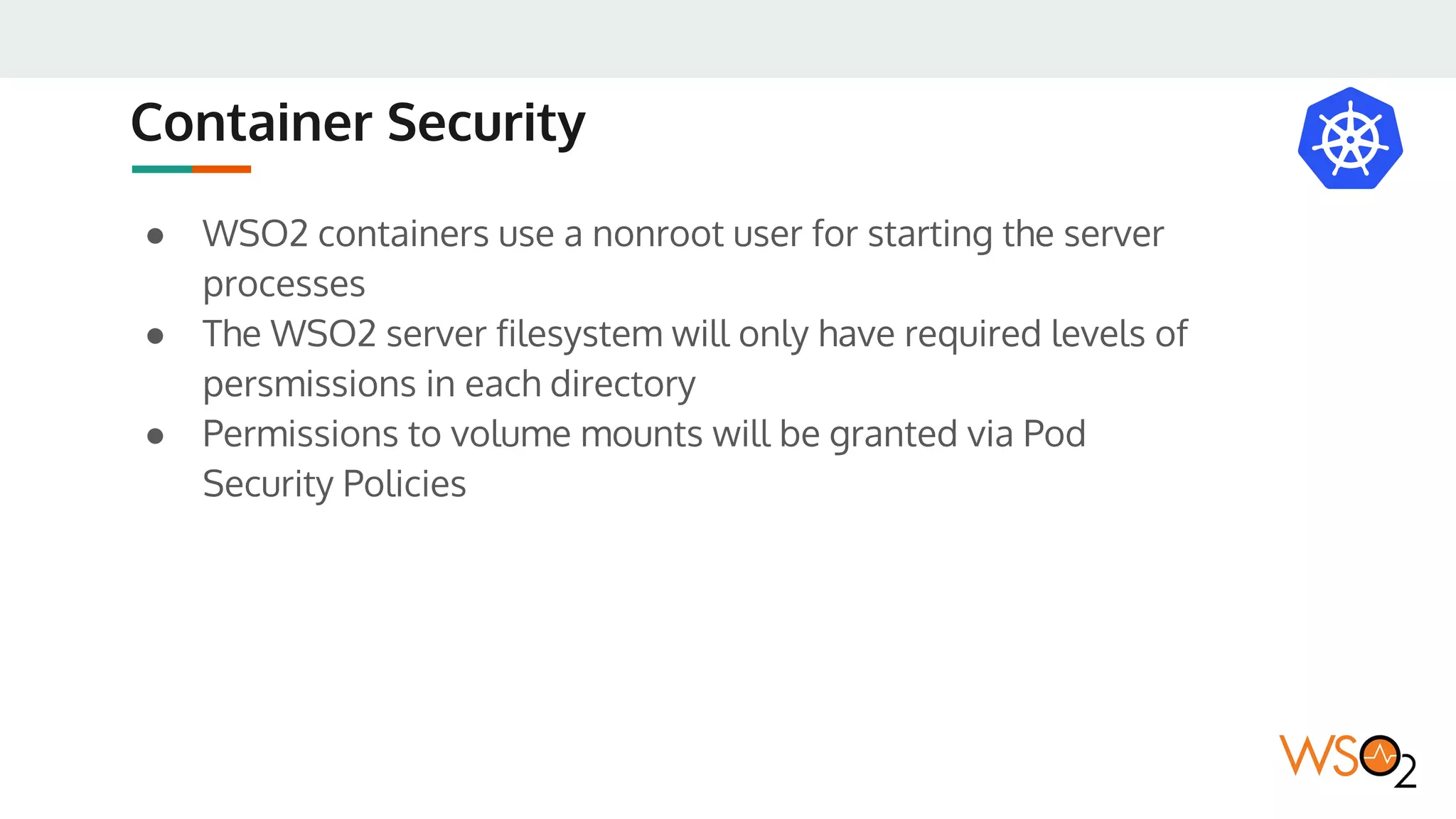
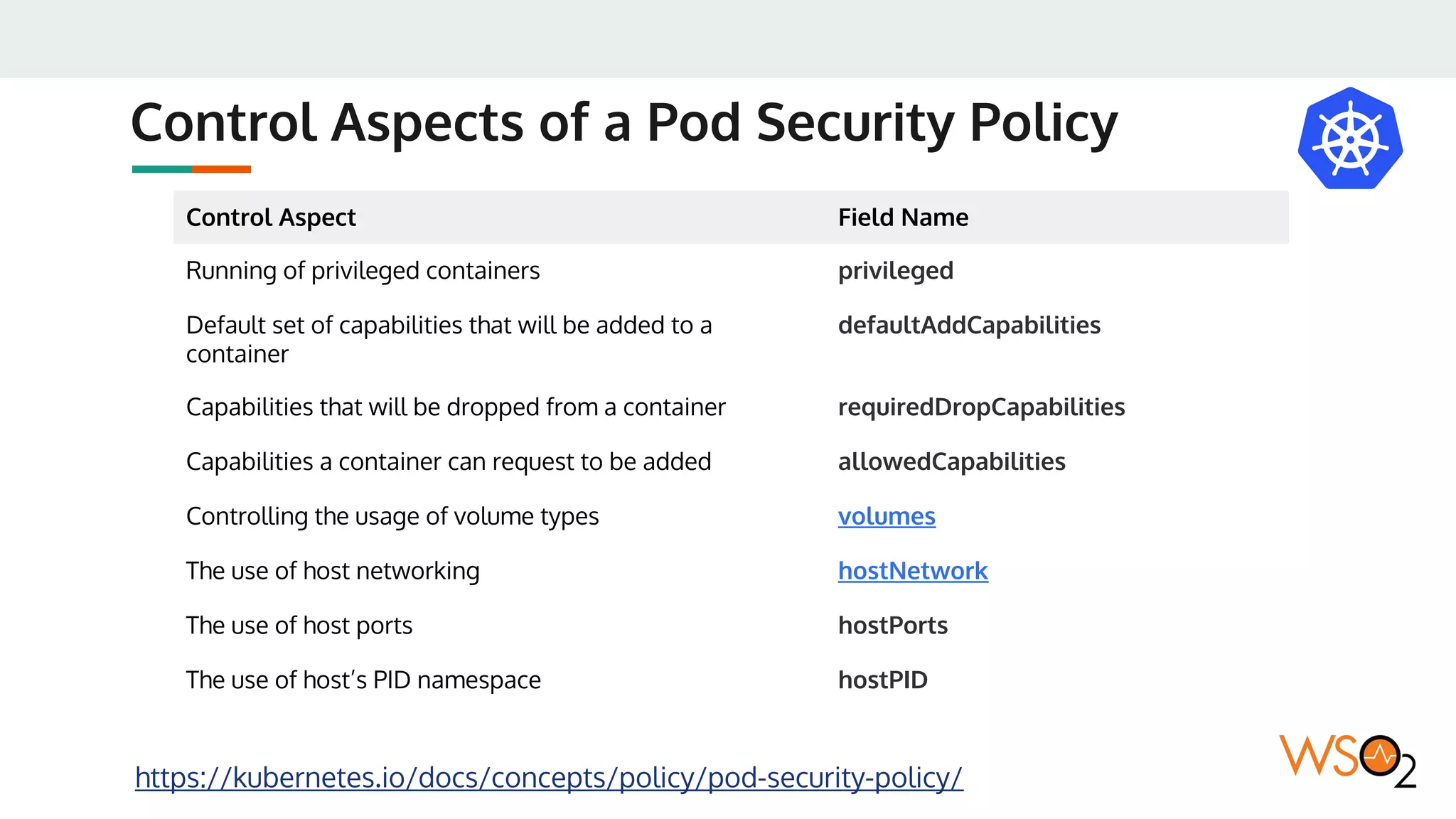
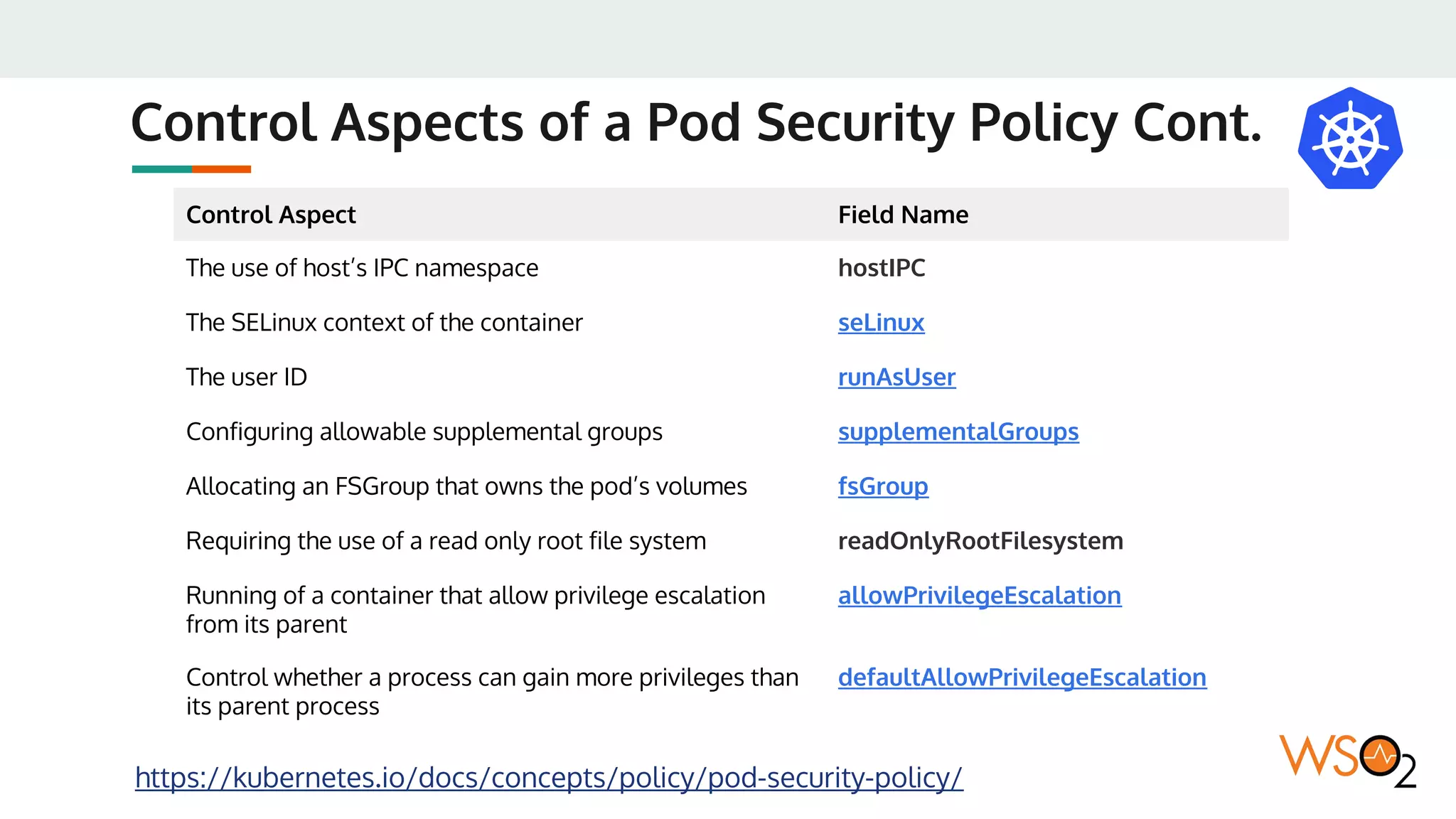
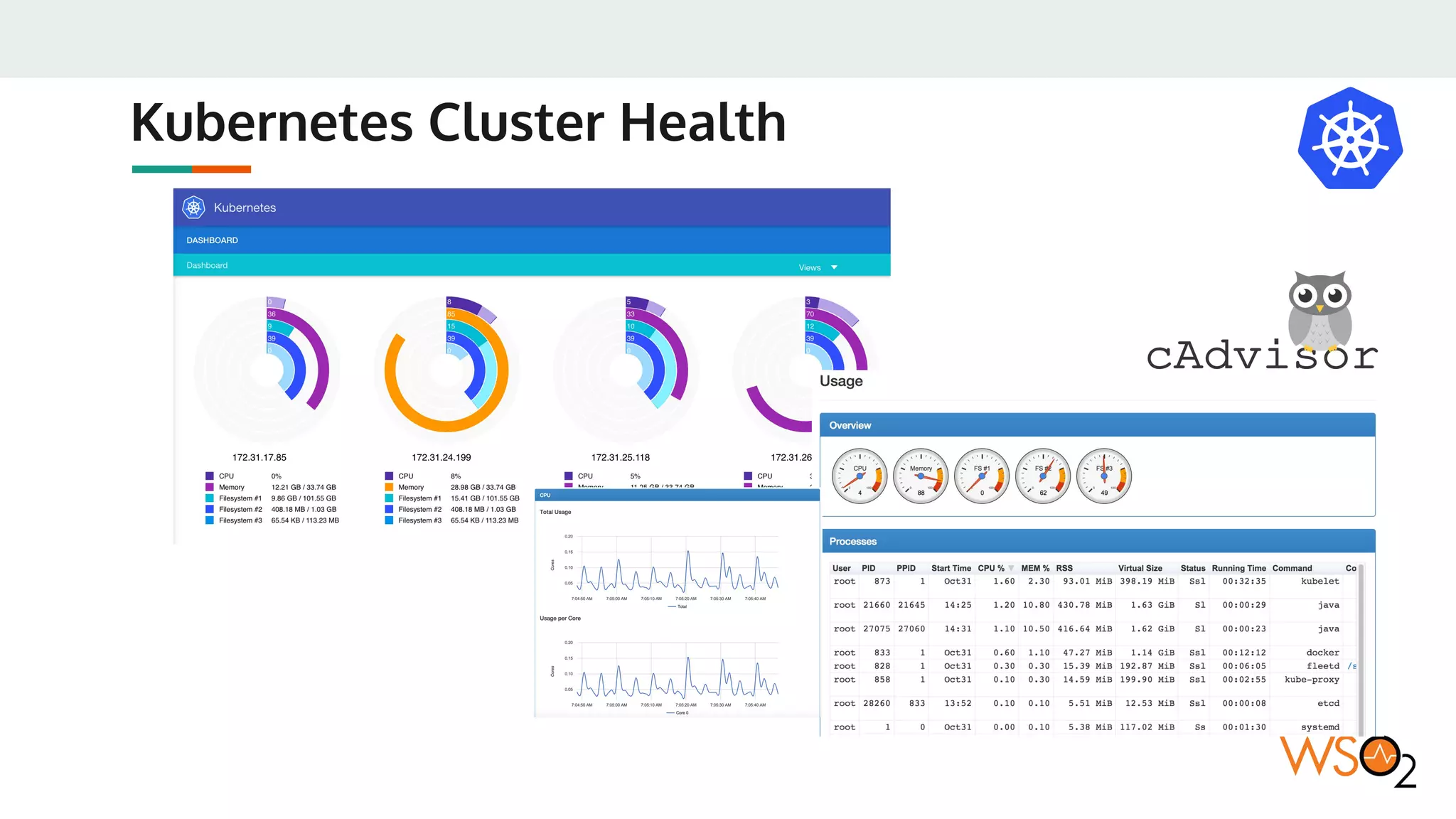
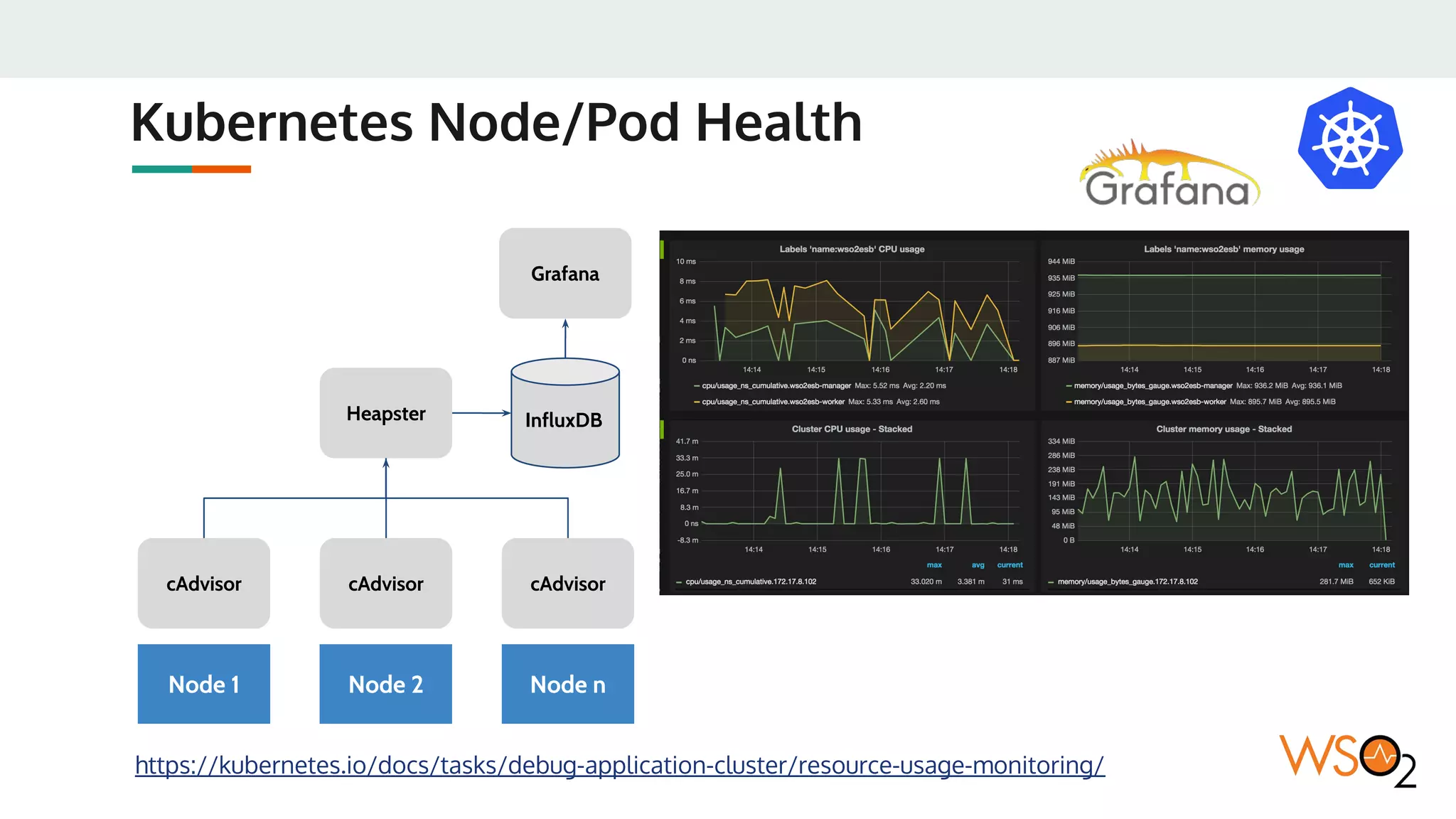
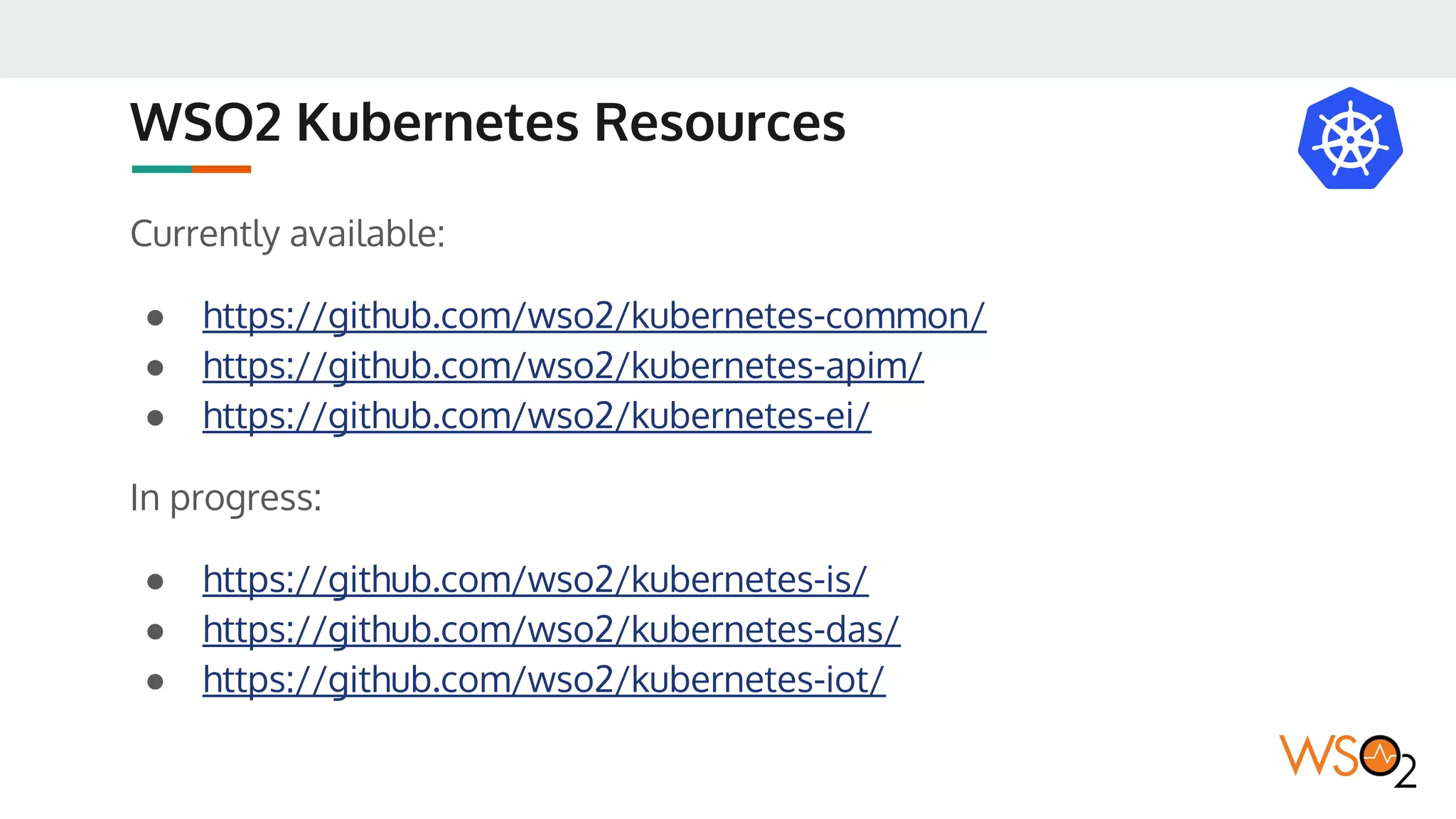
This document provides an overview of WSO2's reference architecture for deploying their middleware products on Kubernetes. It begins with introductions to containers and Kubernetes, explaining concepts like pods, services, deployments, etc. It then outlines WSO2's approach for container orchestration, service discovery, configuration management, load balancing, security, updates, and monitoring in a Kubernetes environment. Specific practices and Kubernetes resources are recommended for areas like pod security policies, horizontal pod autoscaling, ingress definitions, and more. Overall the document serves as a guide for architecting and operating WSO2 products on Kubernetes according to best practices.