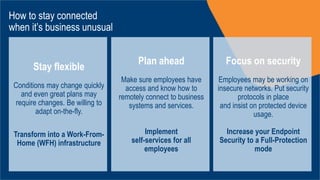
This document provides a guide for organizations to support a dispersed workforce working from home. It recommends that organizations stay flexible, transform their infrastructure to support remote work, and implement self-service tools for employees. It also stresses the importance of focusing on security when employees are working on insecure networks outside the office. Specific recommendations include remotely managing devices, avoiding network capacity issues, allowing employees to manage their own software, offering self-service portals, and improving endpoint security through features like malware protection, device control, and data loss prevention.