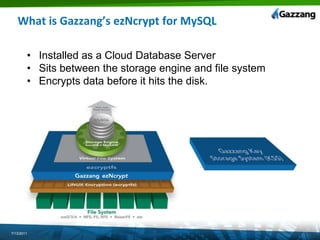
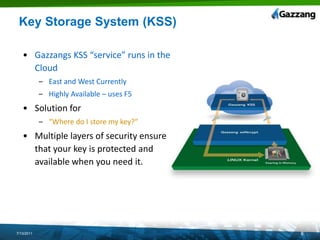
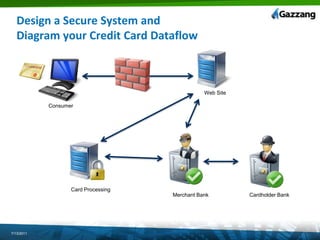
The document discusses PCI (Payment Card Industry) compliance and assessments. It describes the 12 requirements of PCI compliance including installing firewalls, encrypting cardholder data transmission, restricting access to data, and maintaining security policies. It outlines how the Gazzang data security solution, including its ezNcrypt encryption tool and Key Storage System, can help organizations meet these requirements by encrypting database data and securing encryption keys. The document provides guidance on preparing for a PCI audit and designing a secure credit card data system architecture in the cloud.