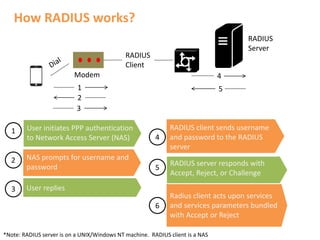
Guest Wi-Fi is an important amenity for hotels, with many guests reviewing Wi-Fi quality before booking. Providing username and password allows guests to access a hotel's Wi-Fi signal. RADIUS is a protocol that handles authentication, authorization, and accounting for network access, allowing devices to securely connect to access points using credentials. Wi-Fi management through RADIUS allows for bandwidth allocation, enhanced security through individual credentials, and more efficient infrastructure and reduced costs.