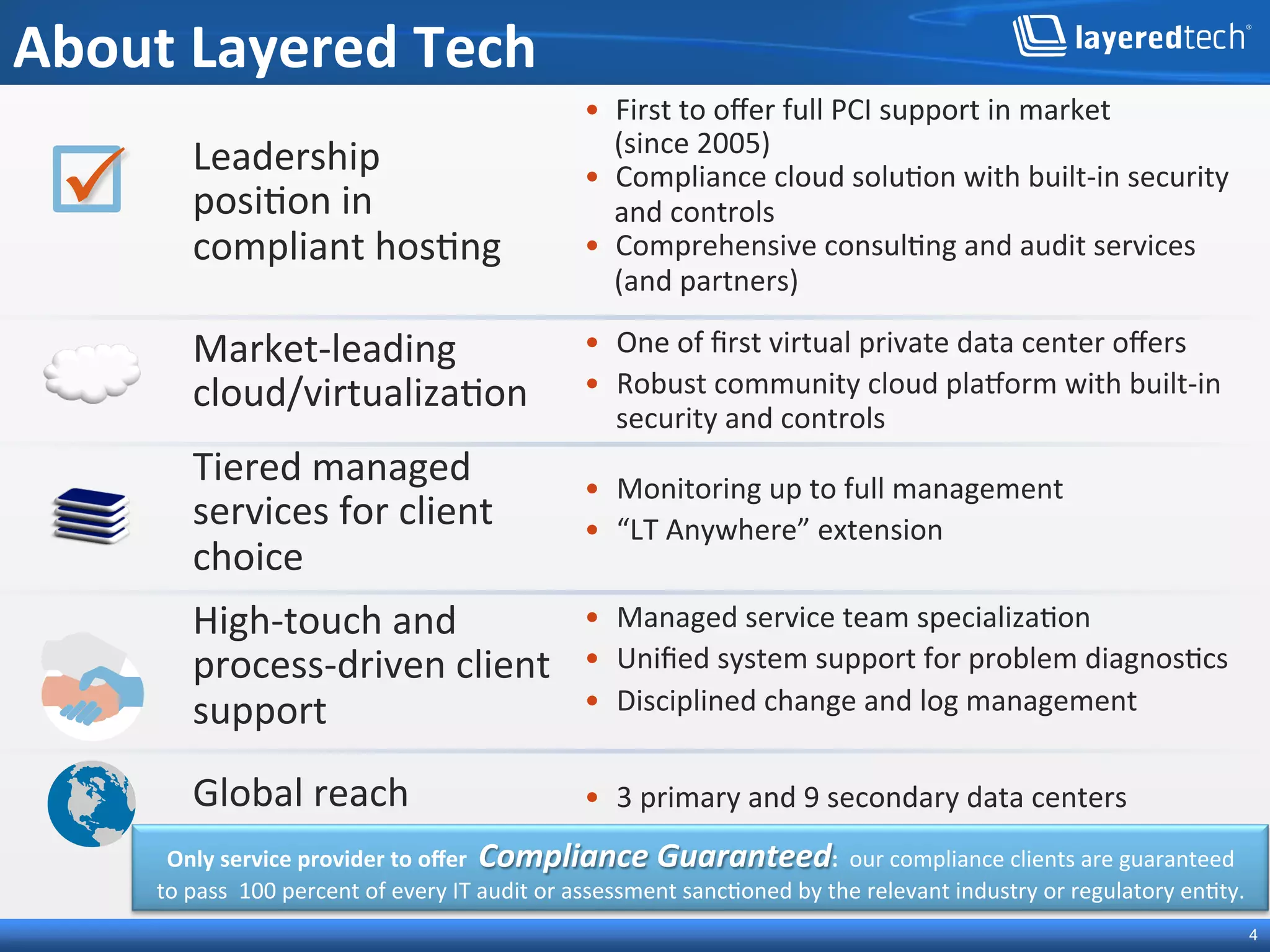
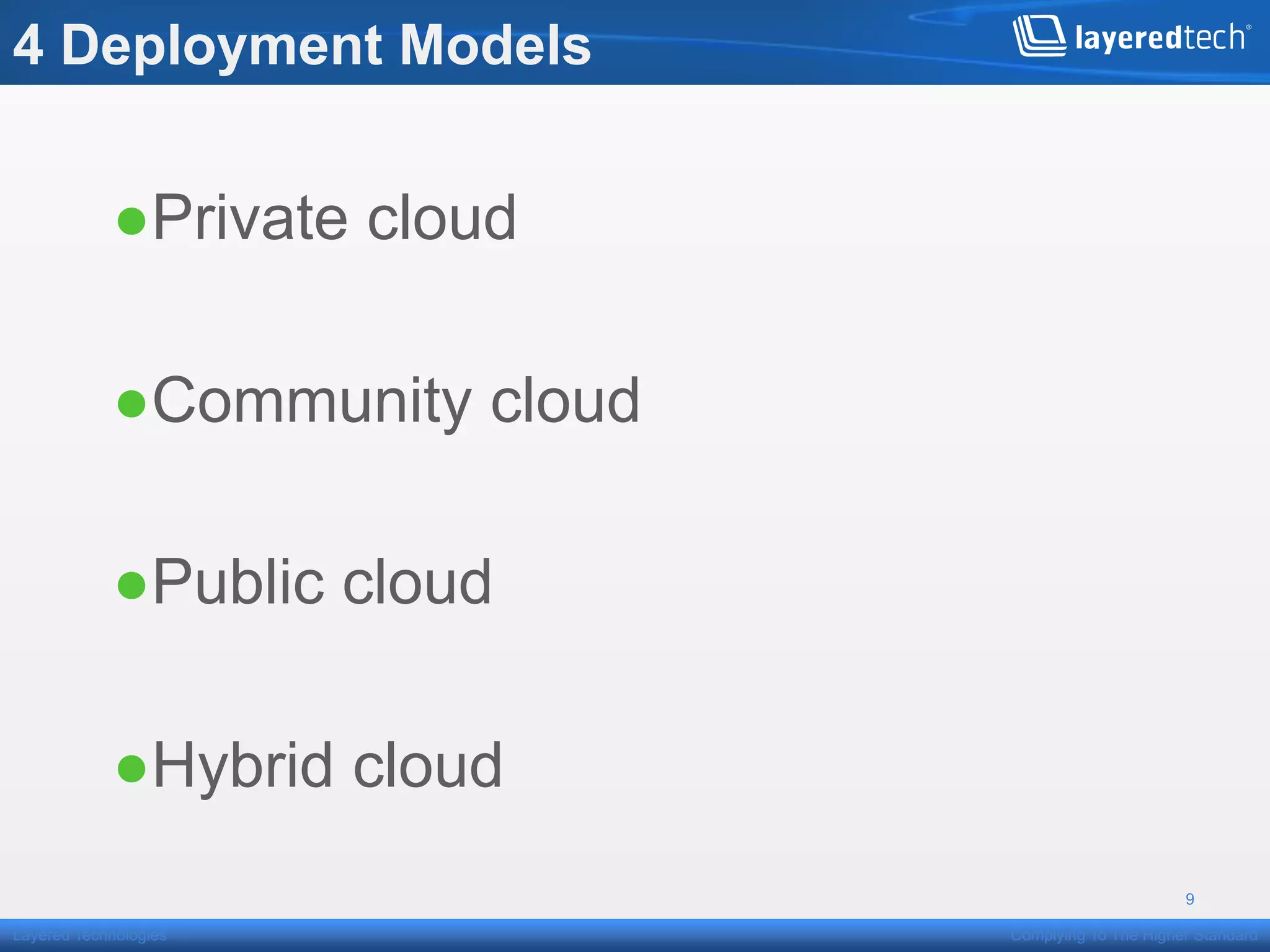
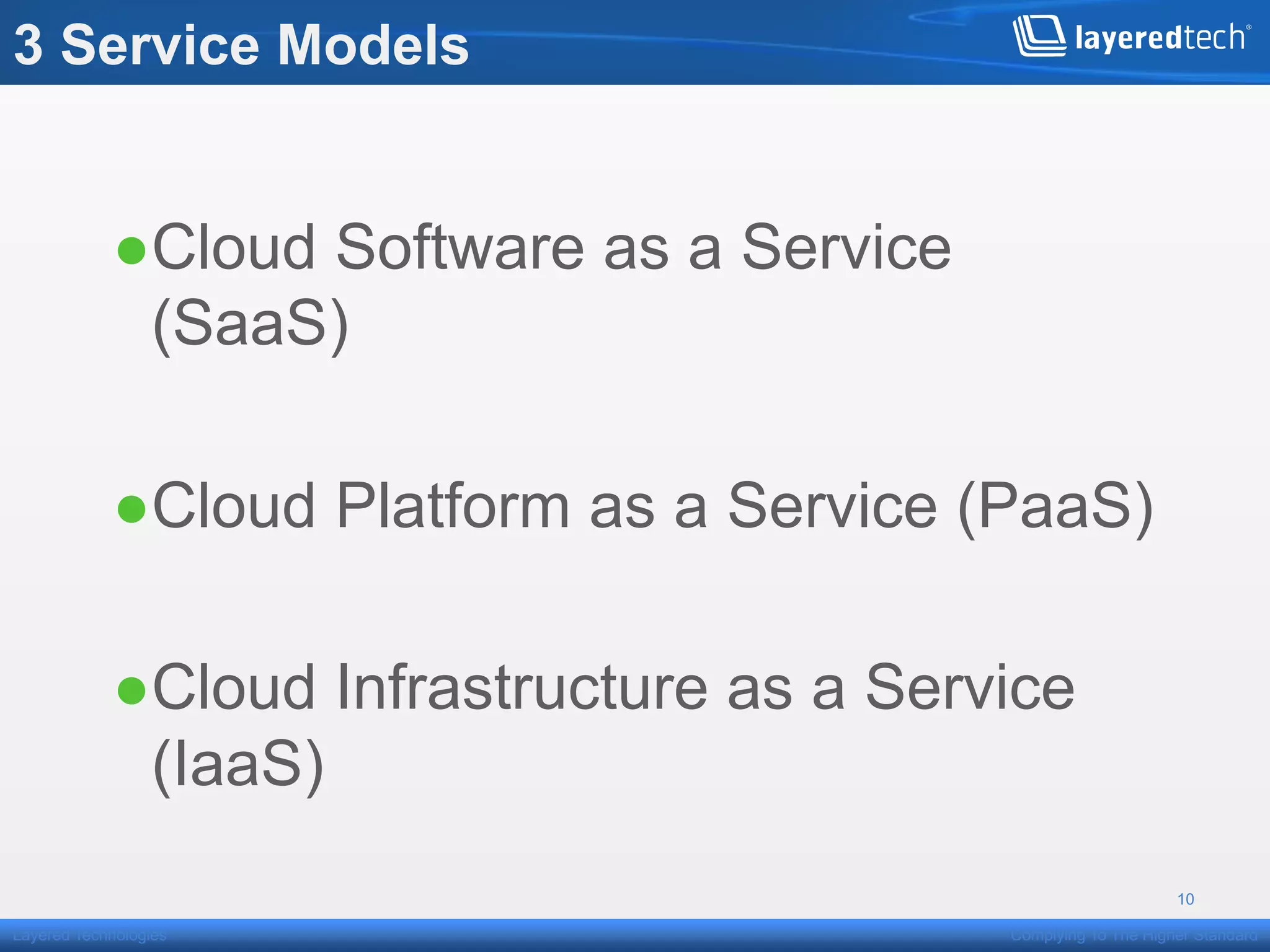
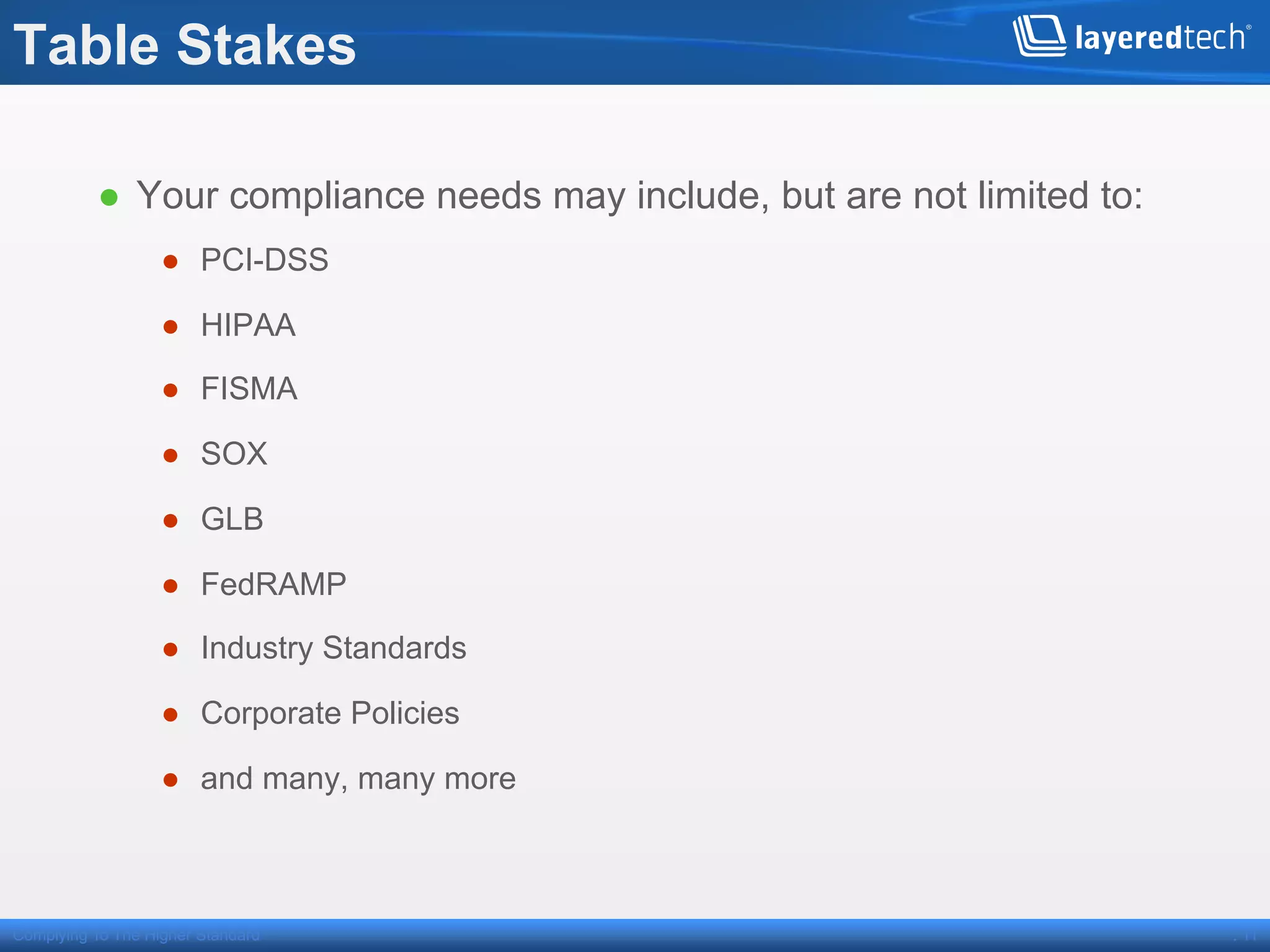
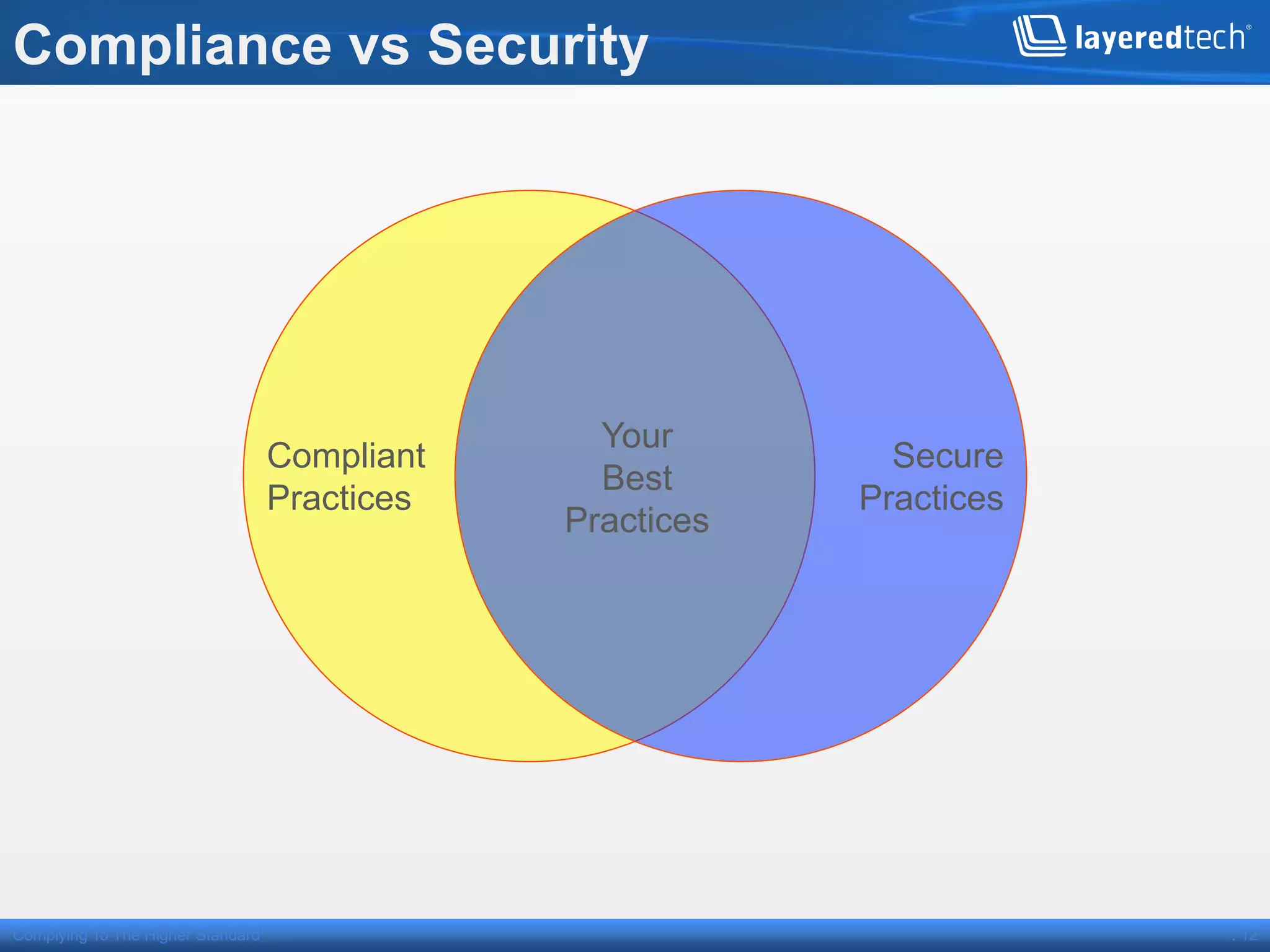
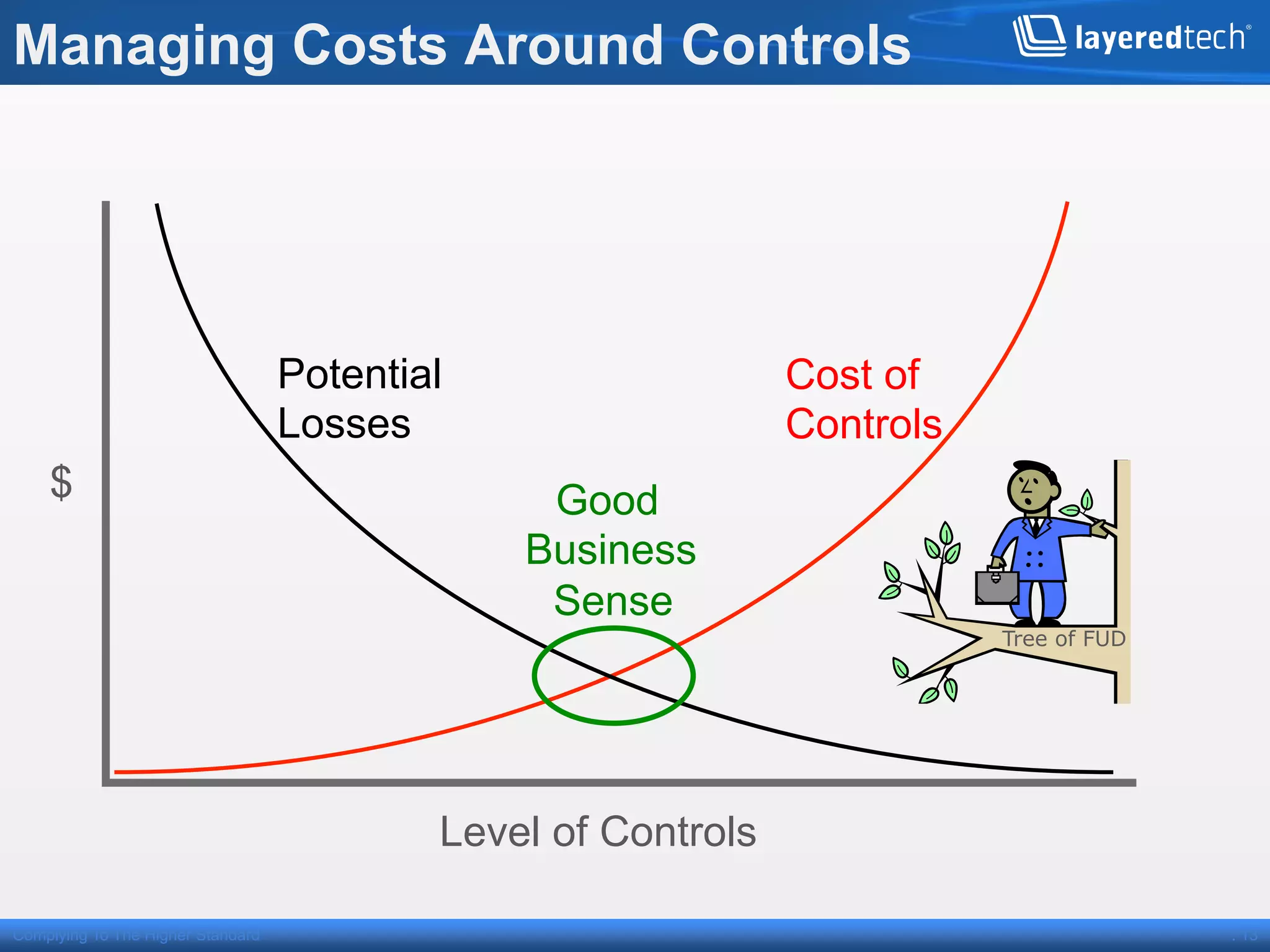
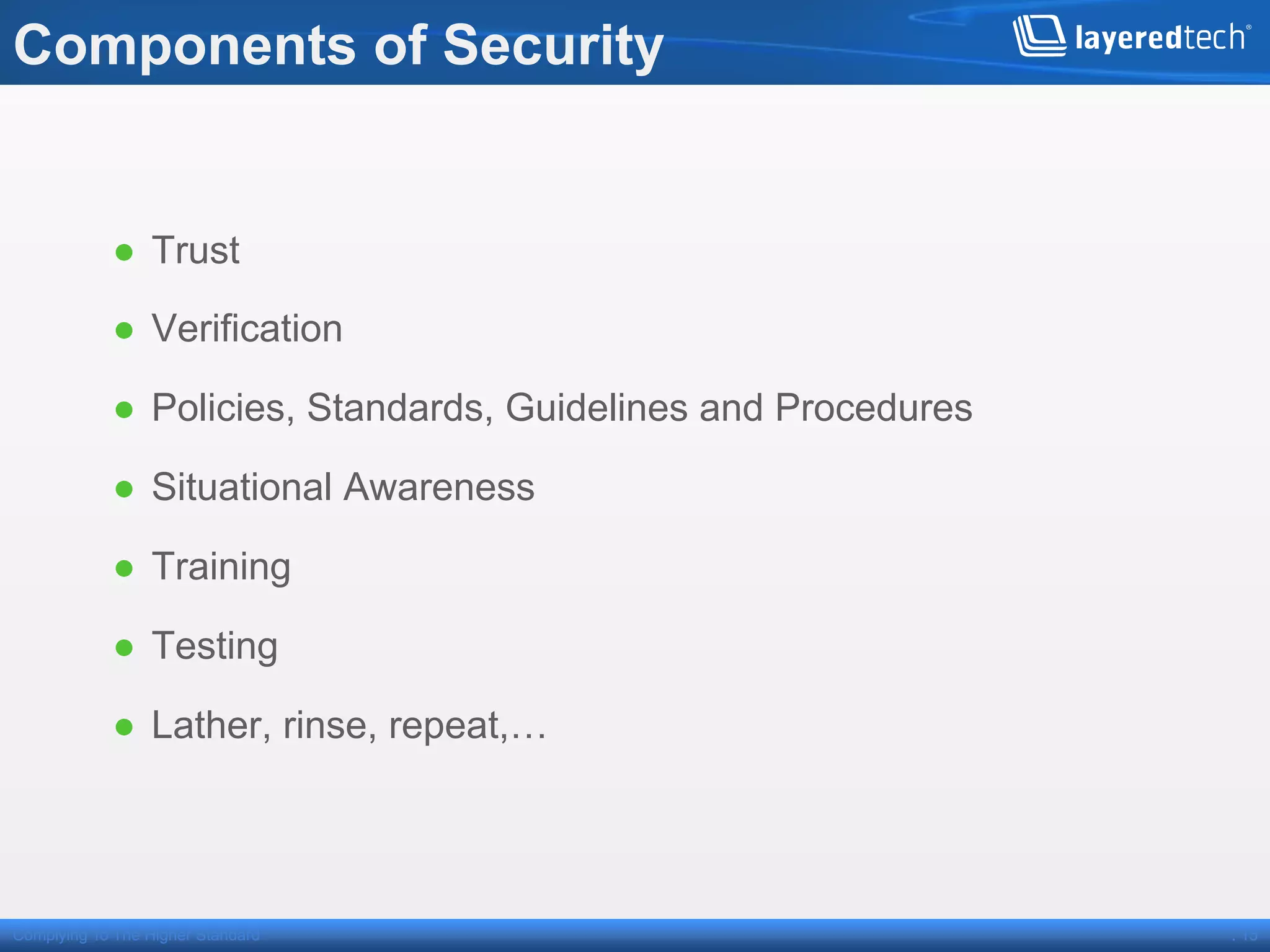
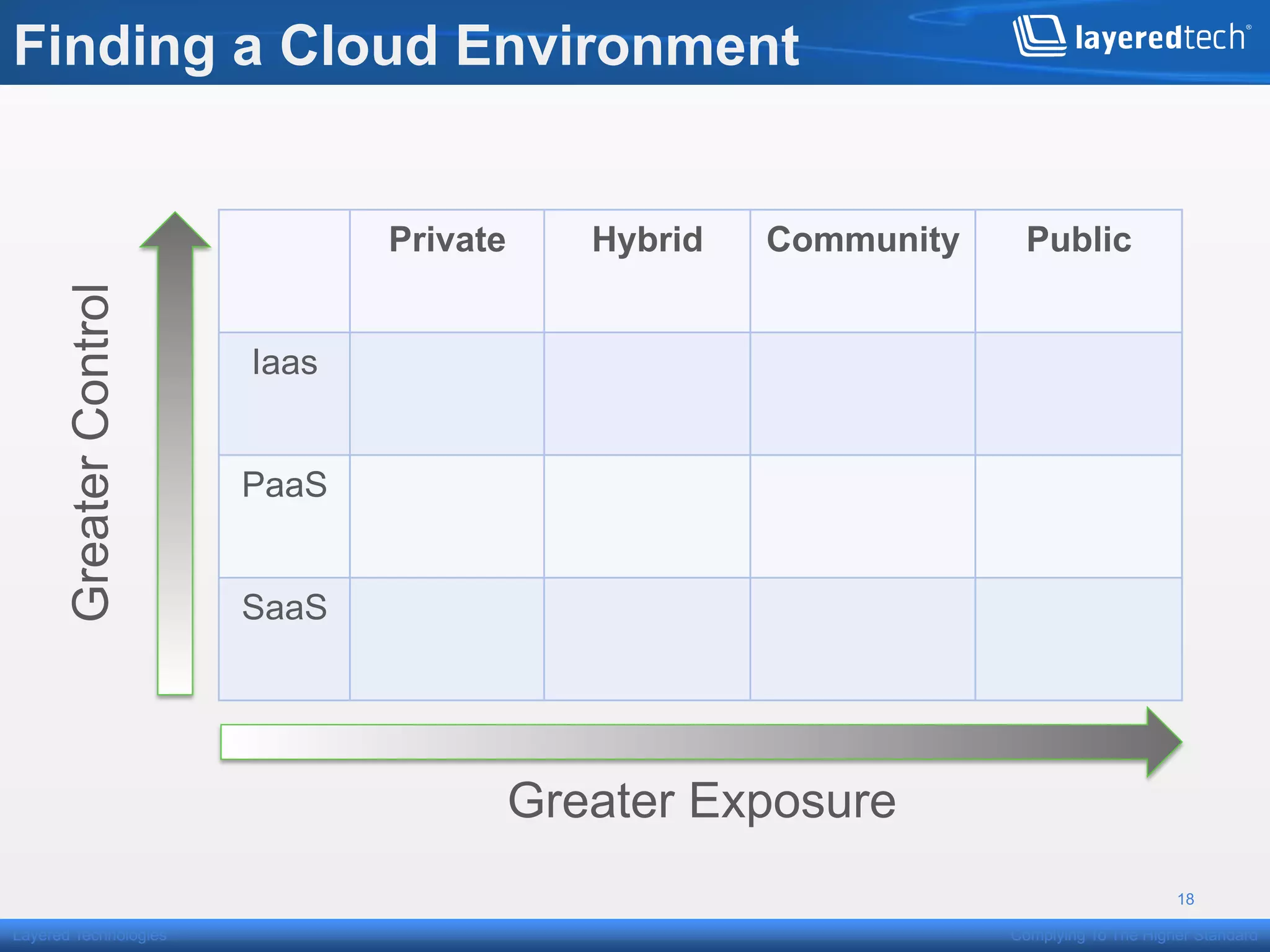
This presentation discusses how the cloud can be made compliant and secure. It begins with an overview of Layered Technologies and the speaker. It then defines key cloud concepts like deployment models and service models. The presentation emphasizes that while compliance is important, security requires additional risk-based practices. It outlines components needed for cloud security, including policies, validation, transparency and compliance support from providers. Managing costs through risk assessment and focusing on important assets is presented as important for security.