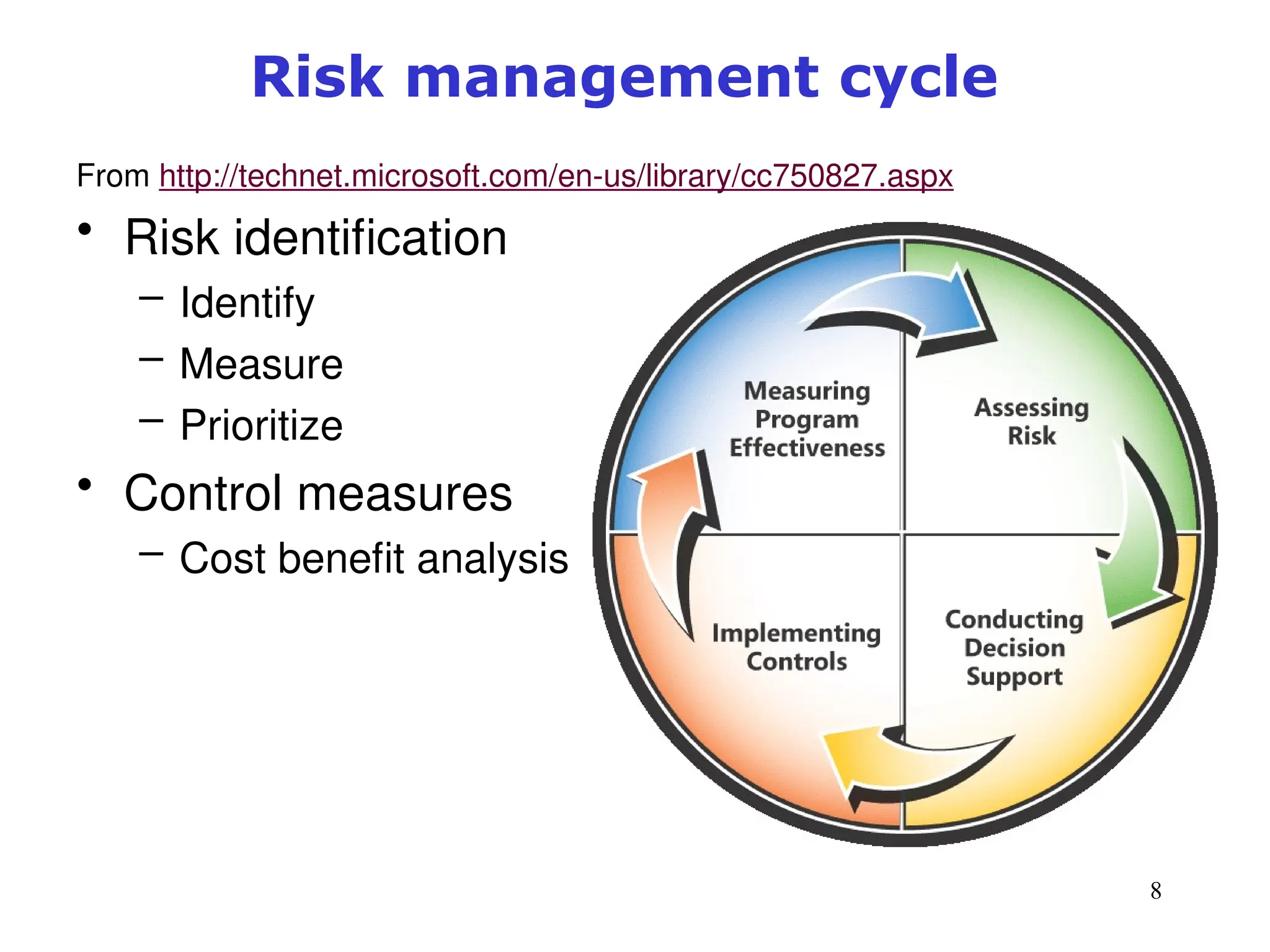
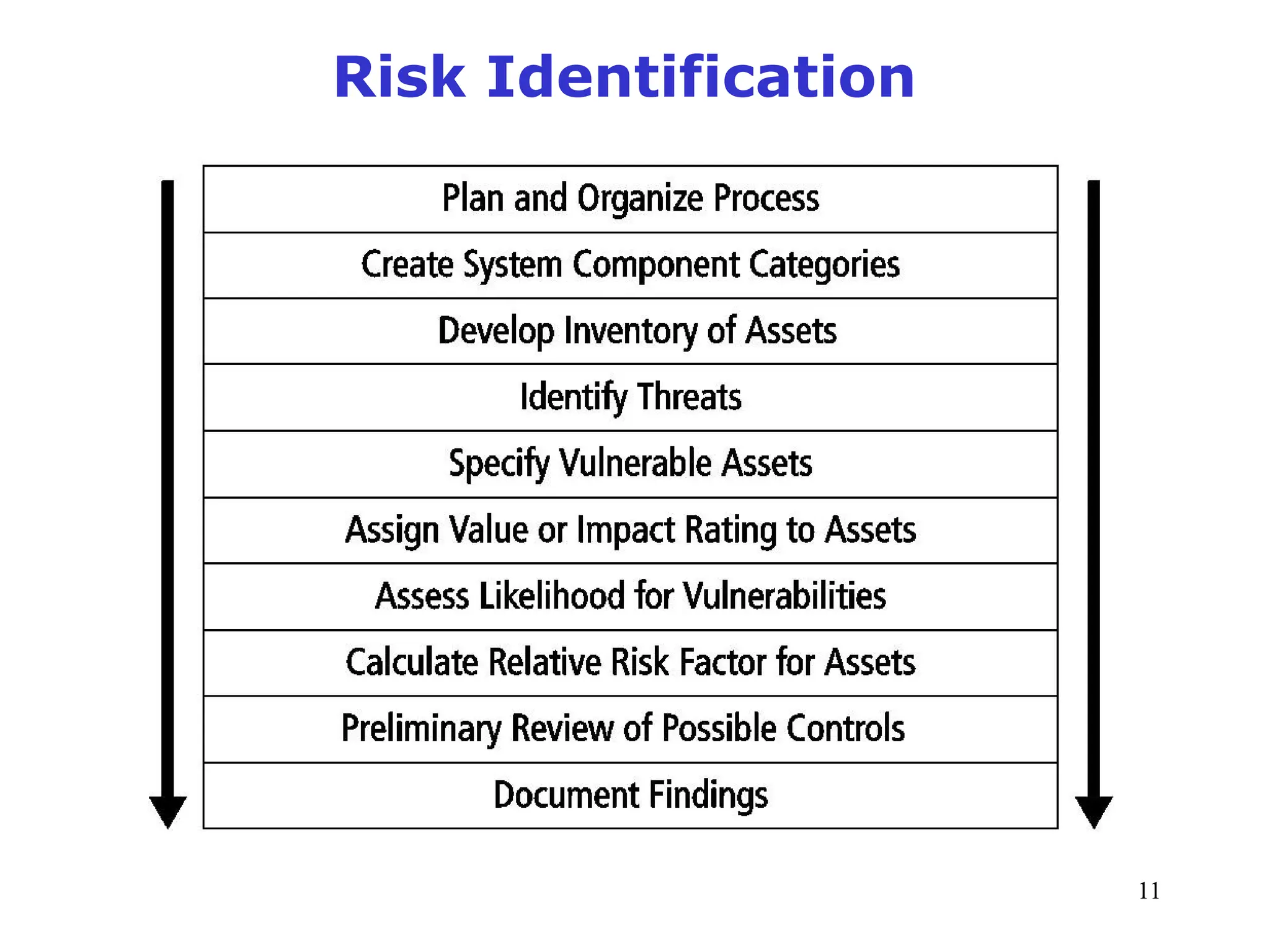
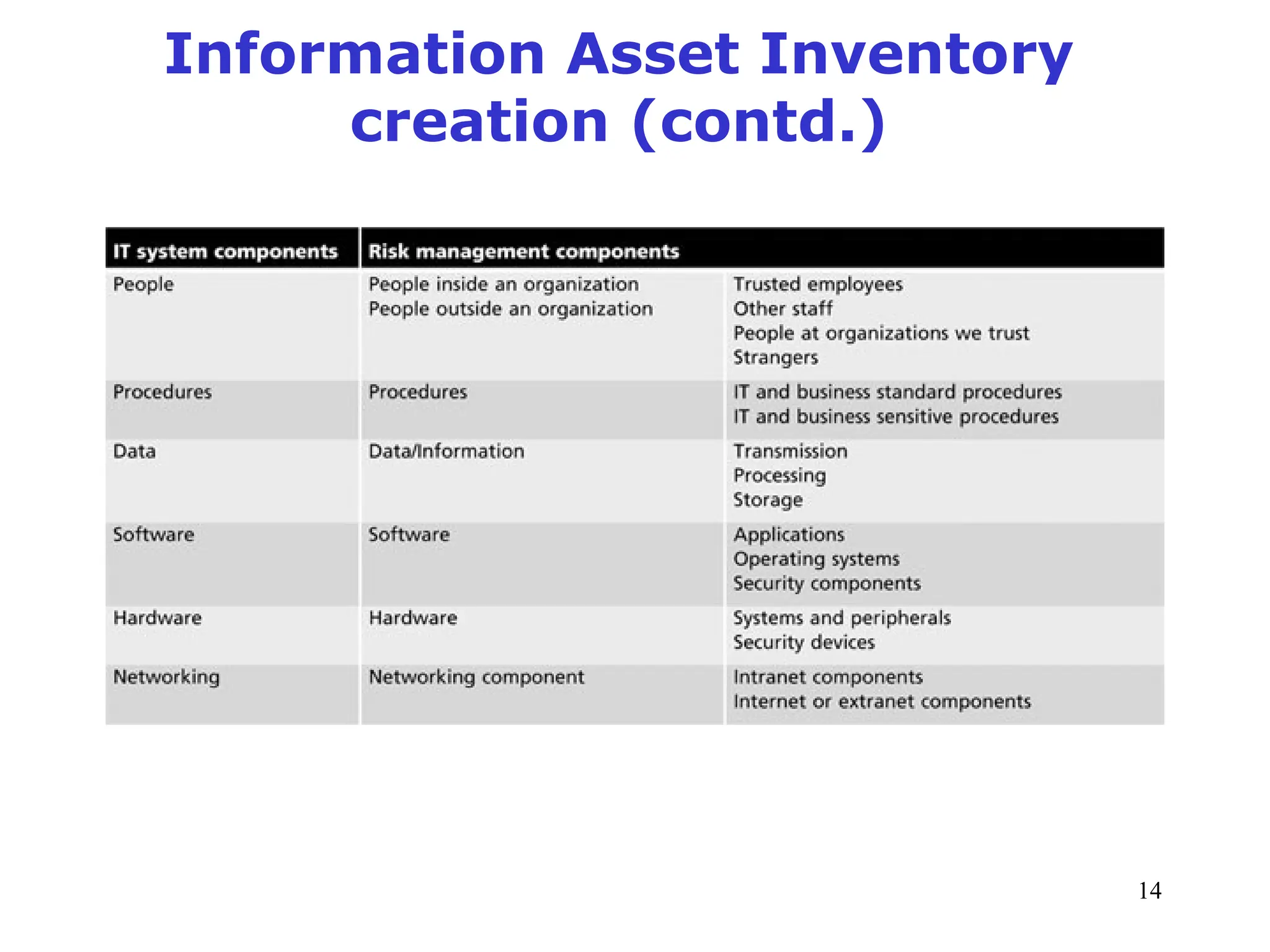
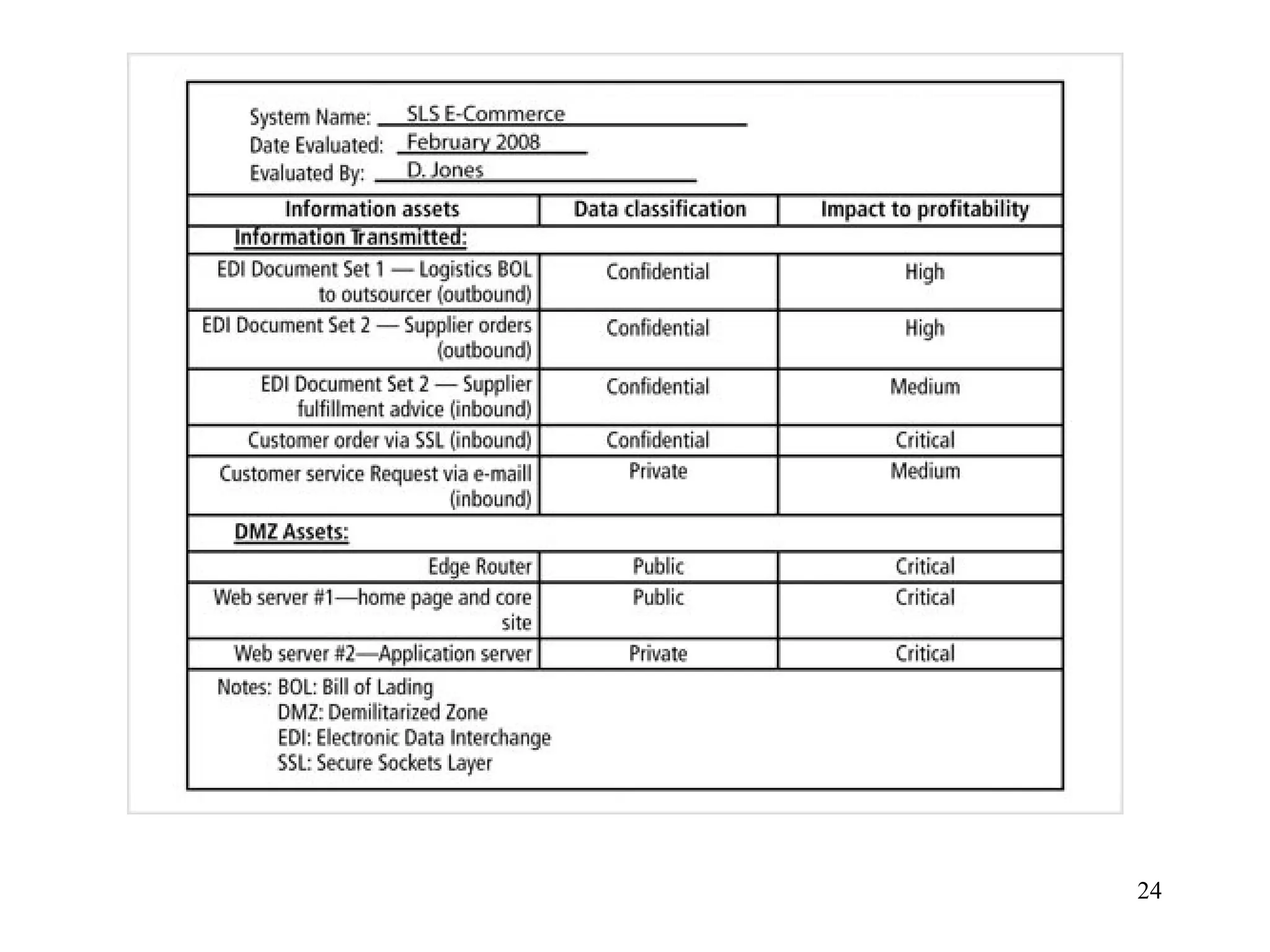
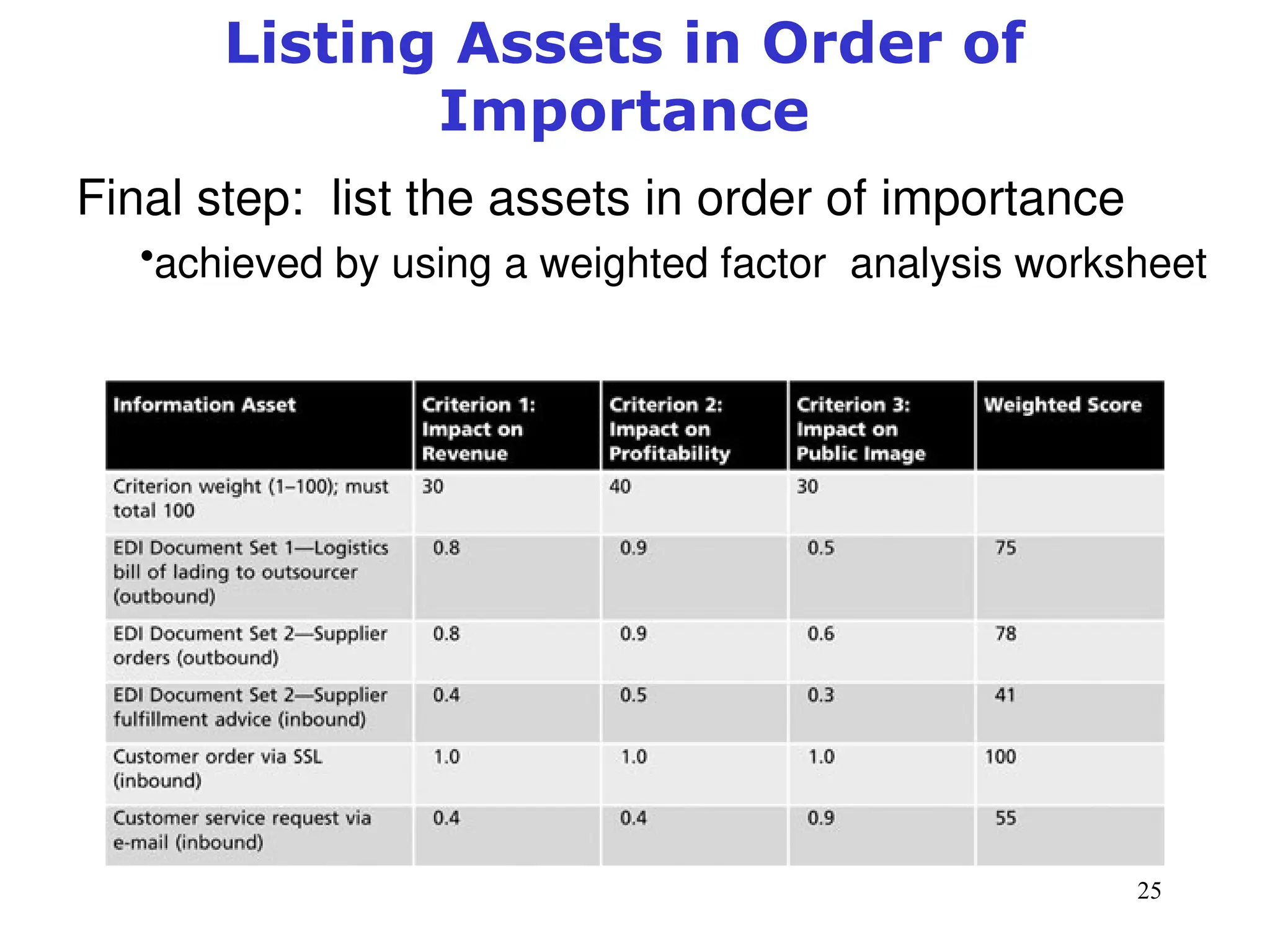
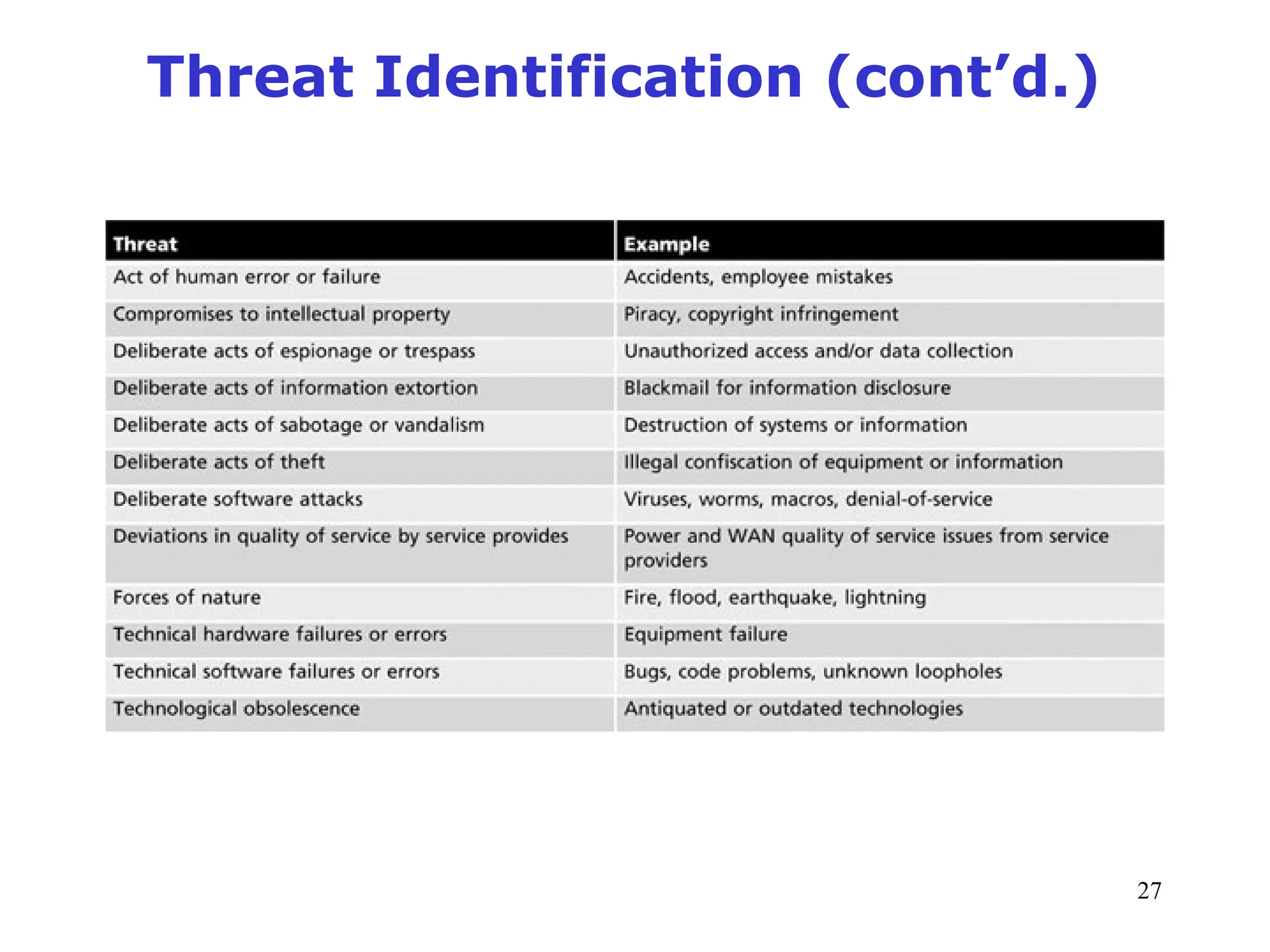
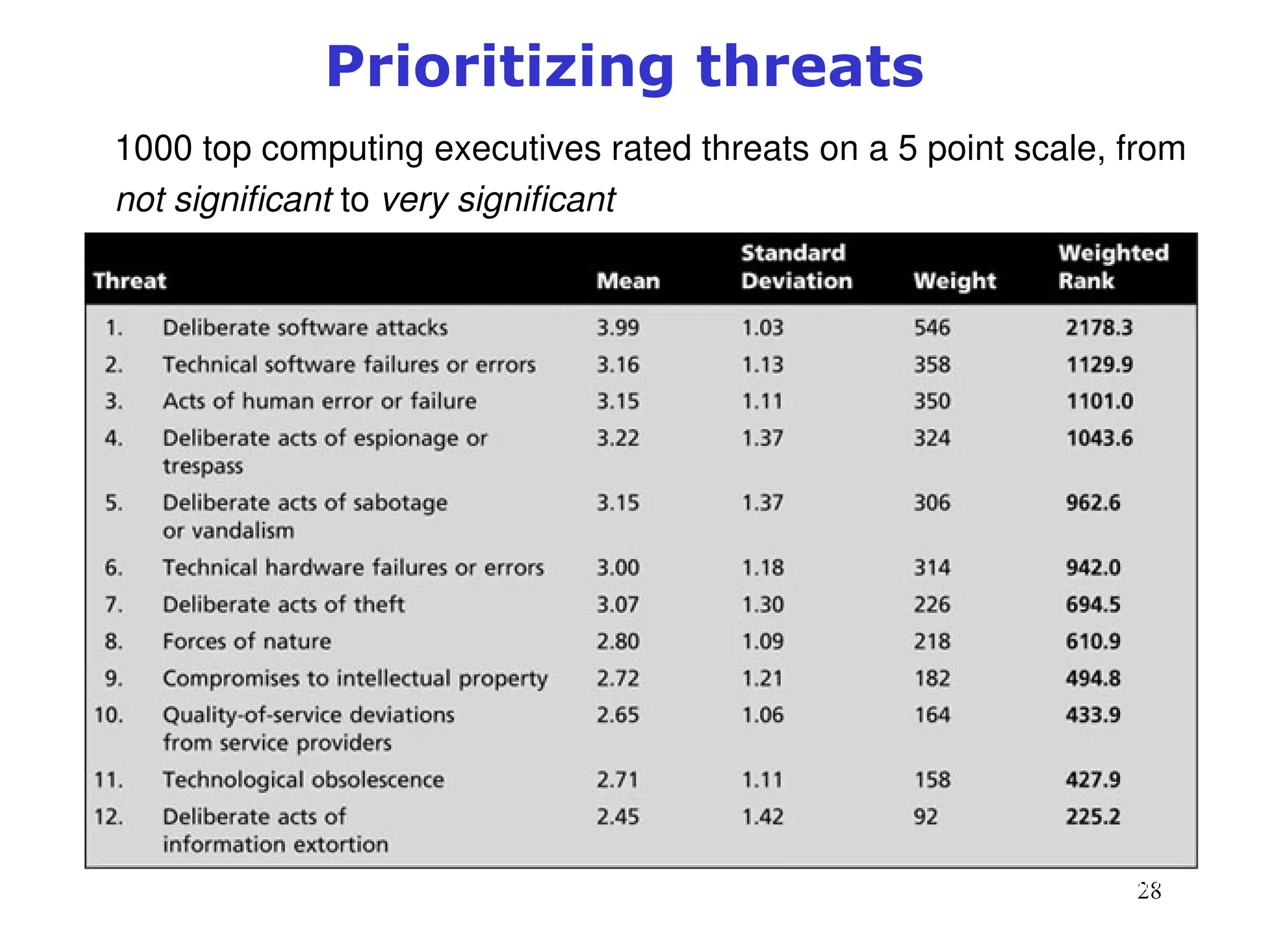
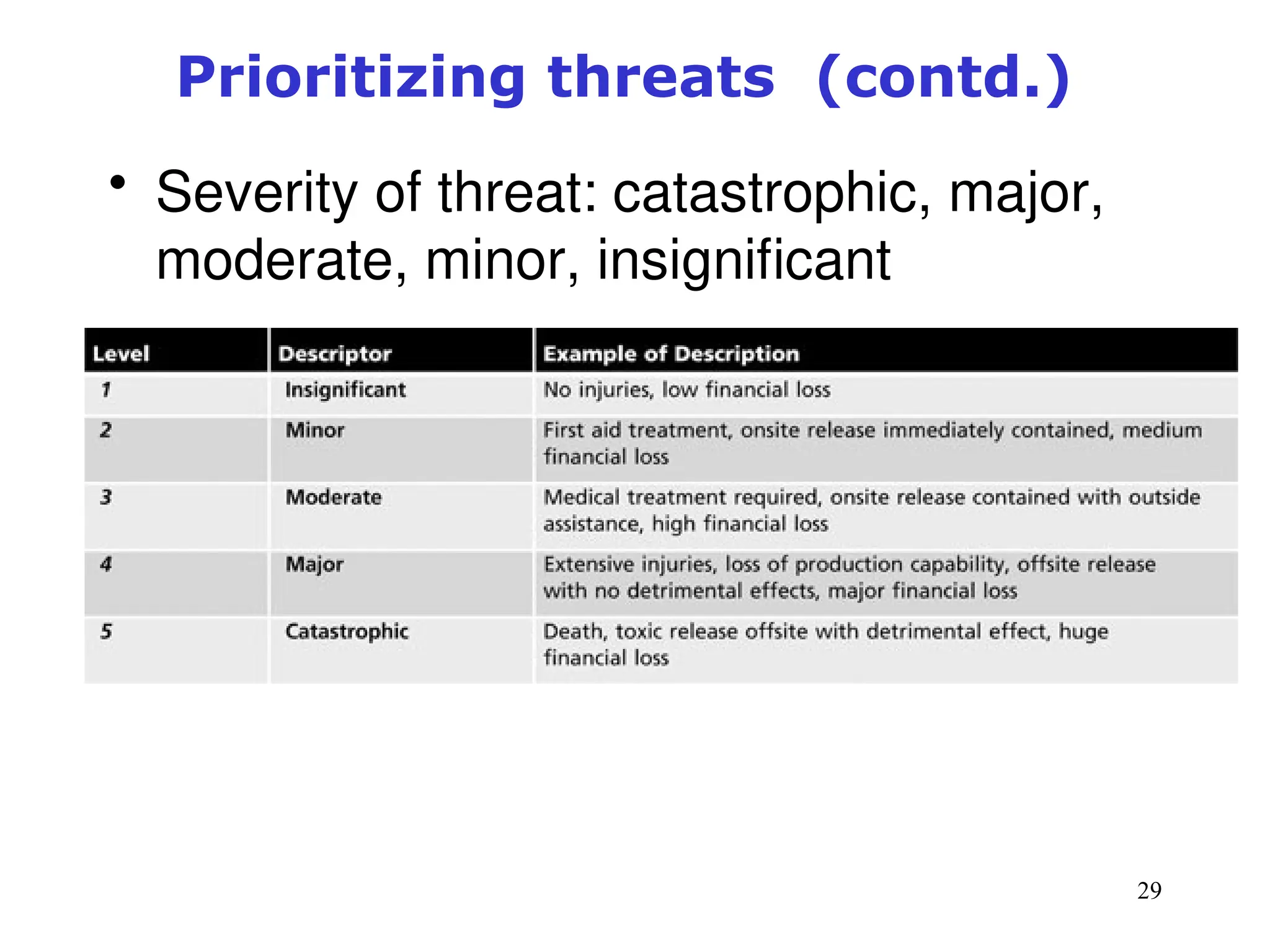
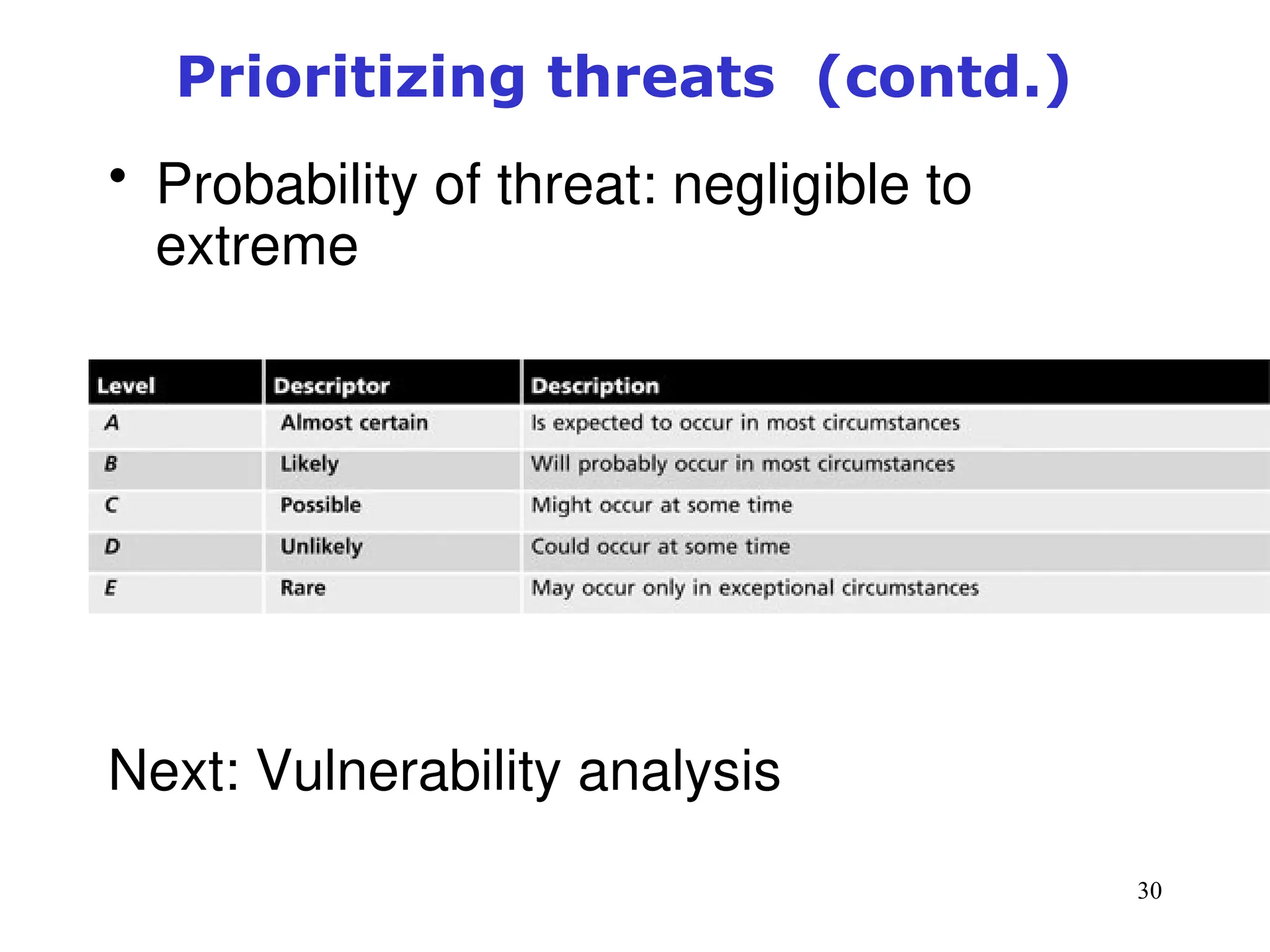
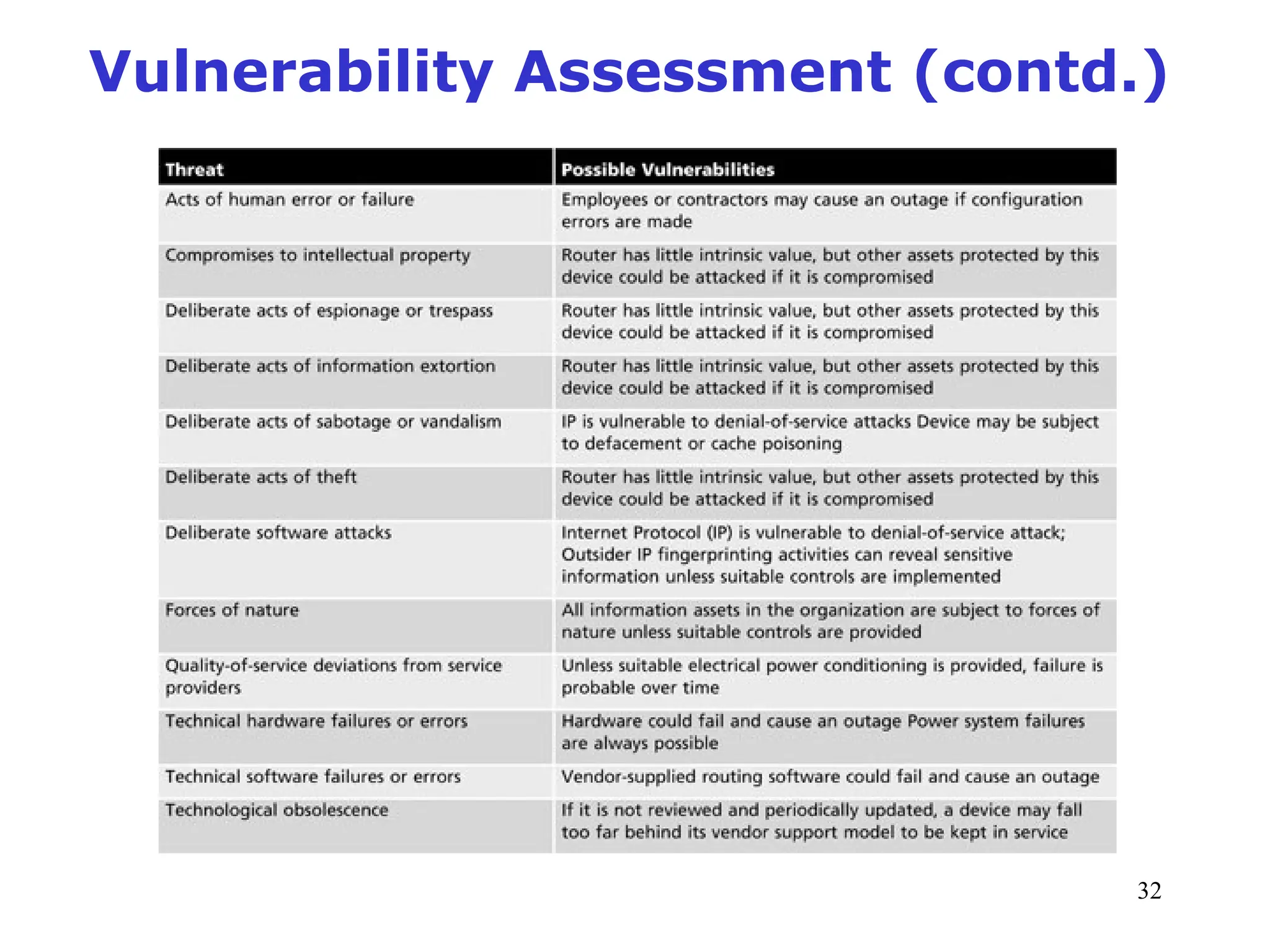
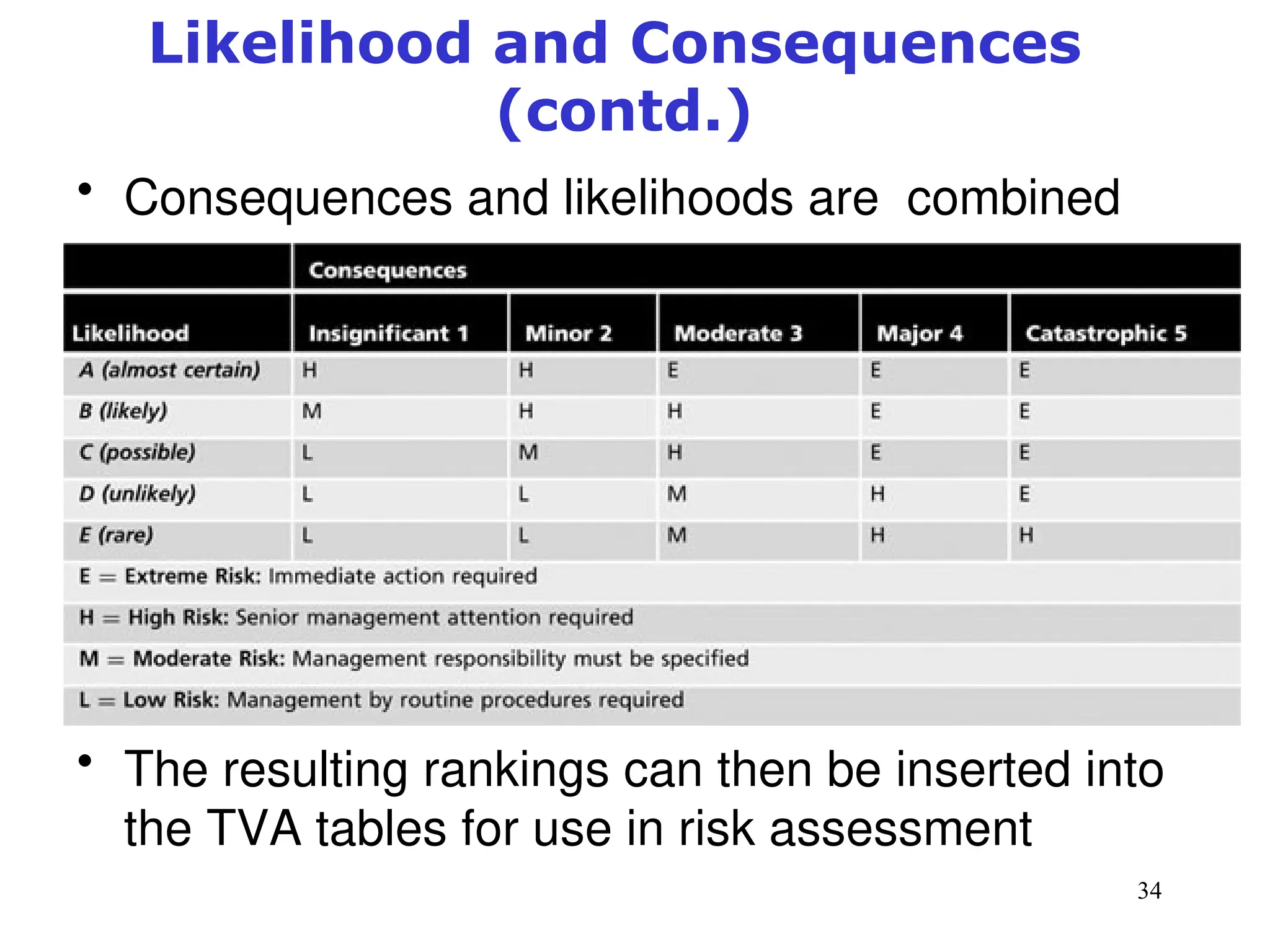
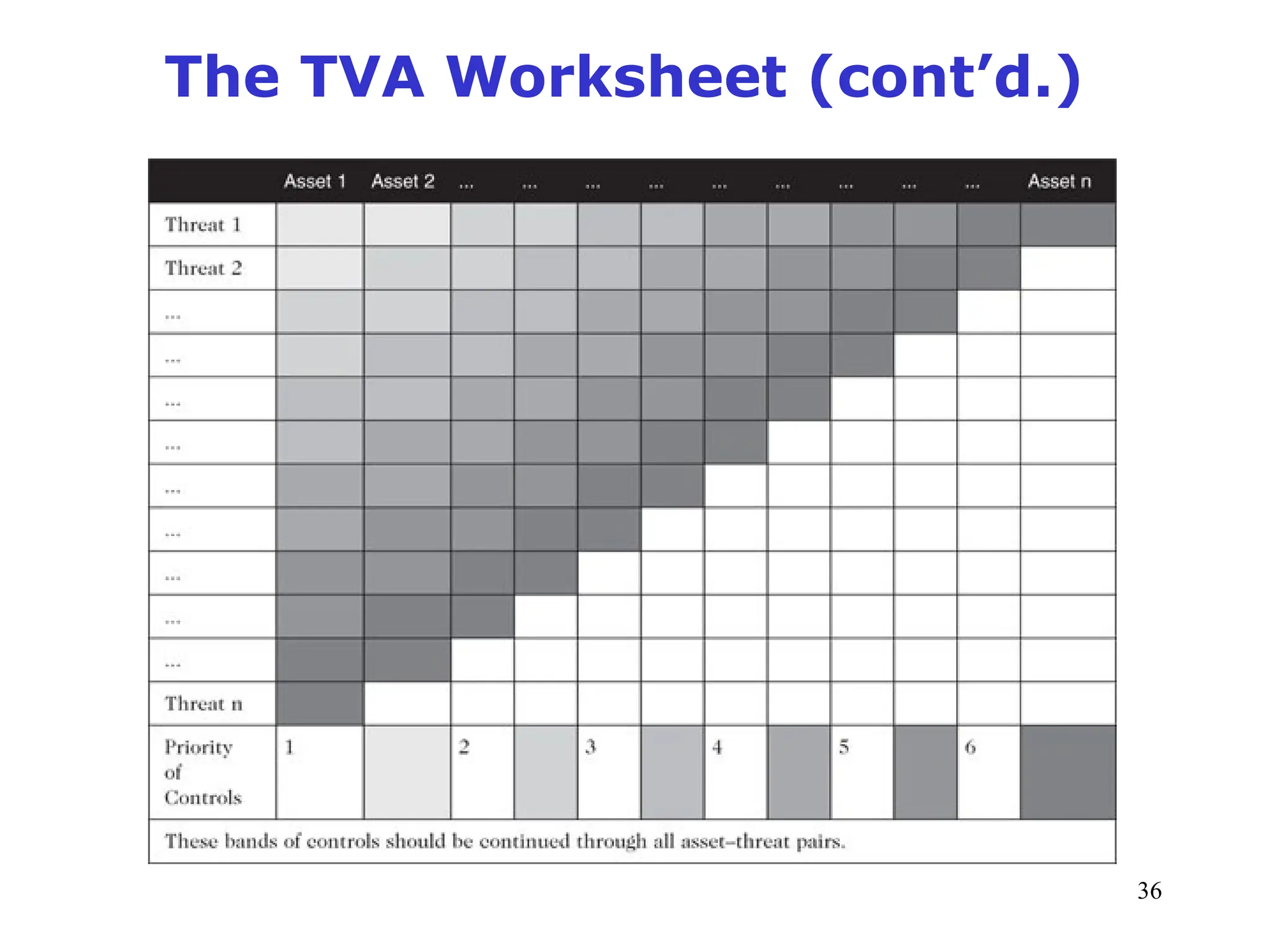
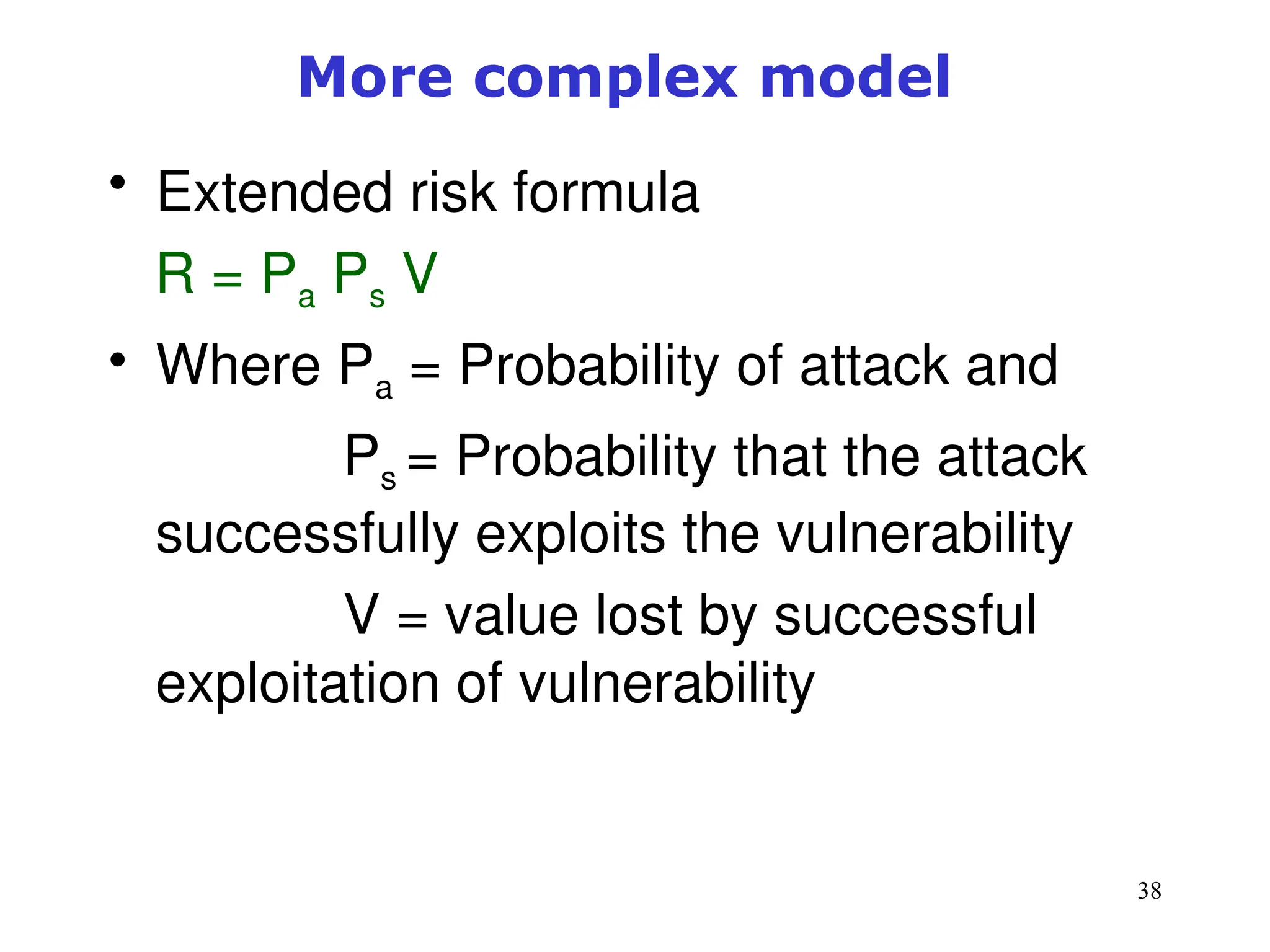
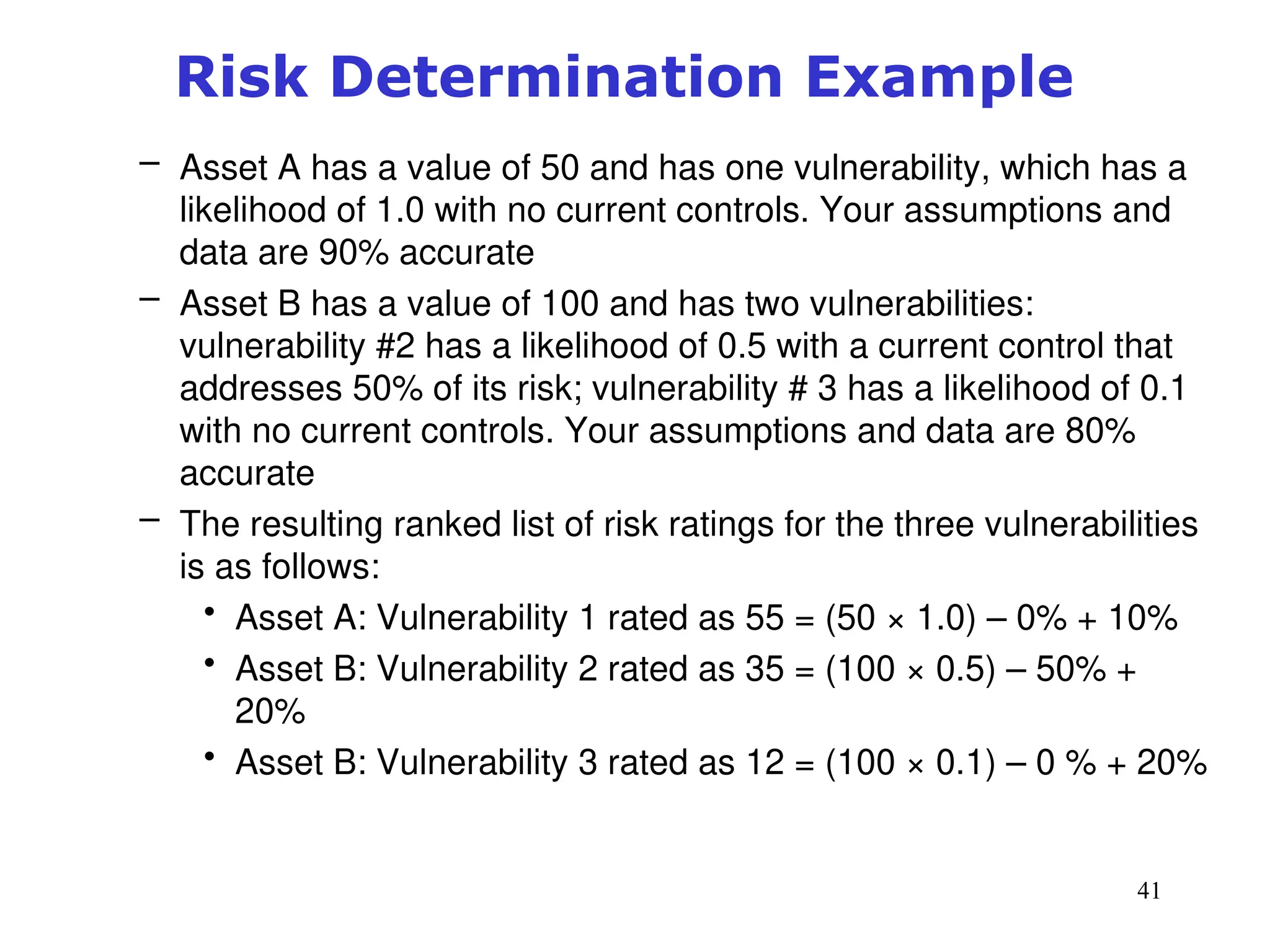
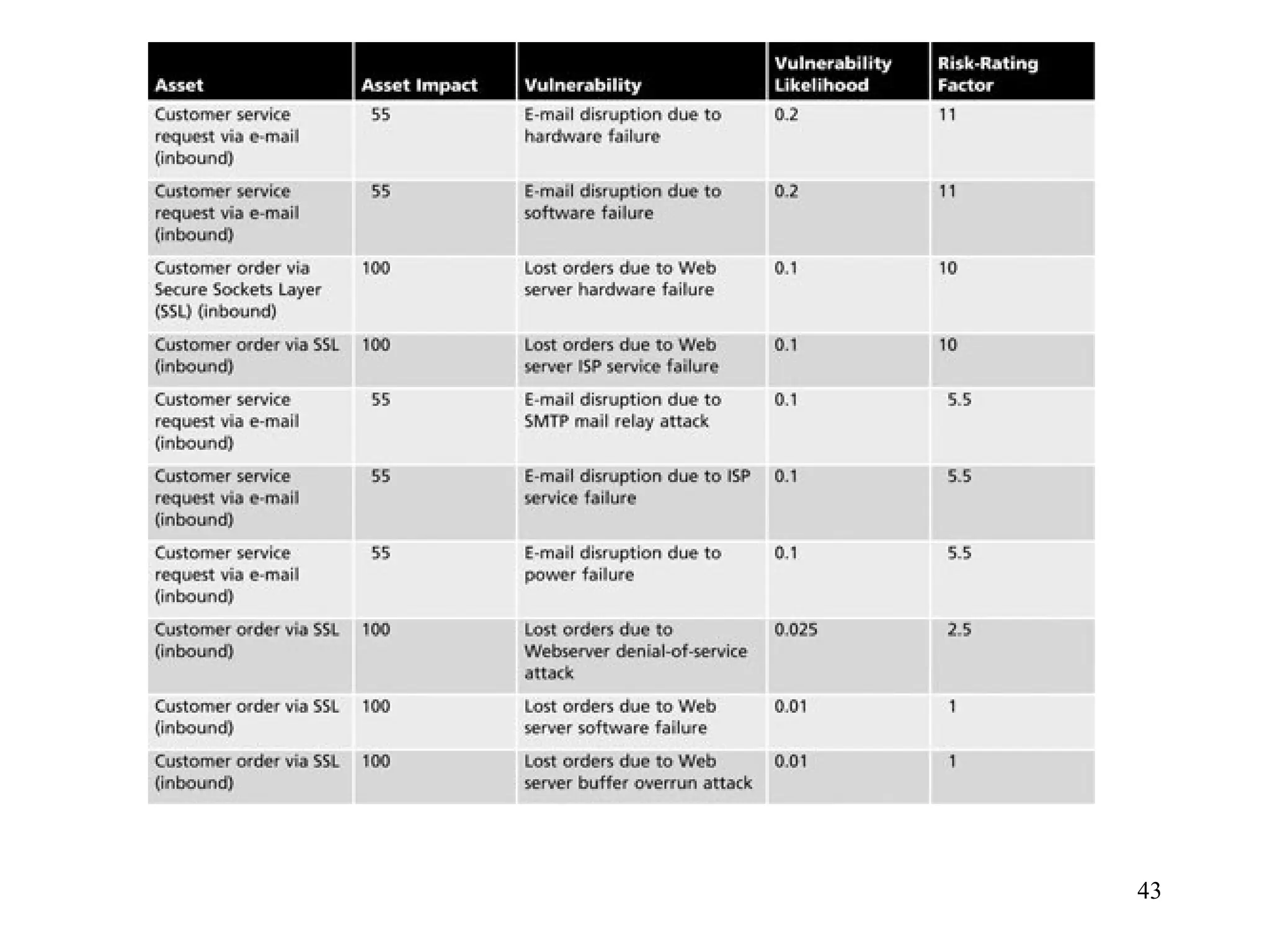
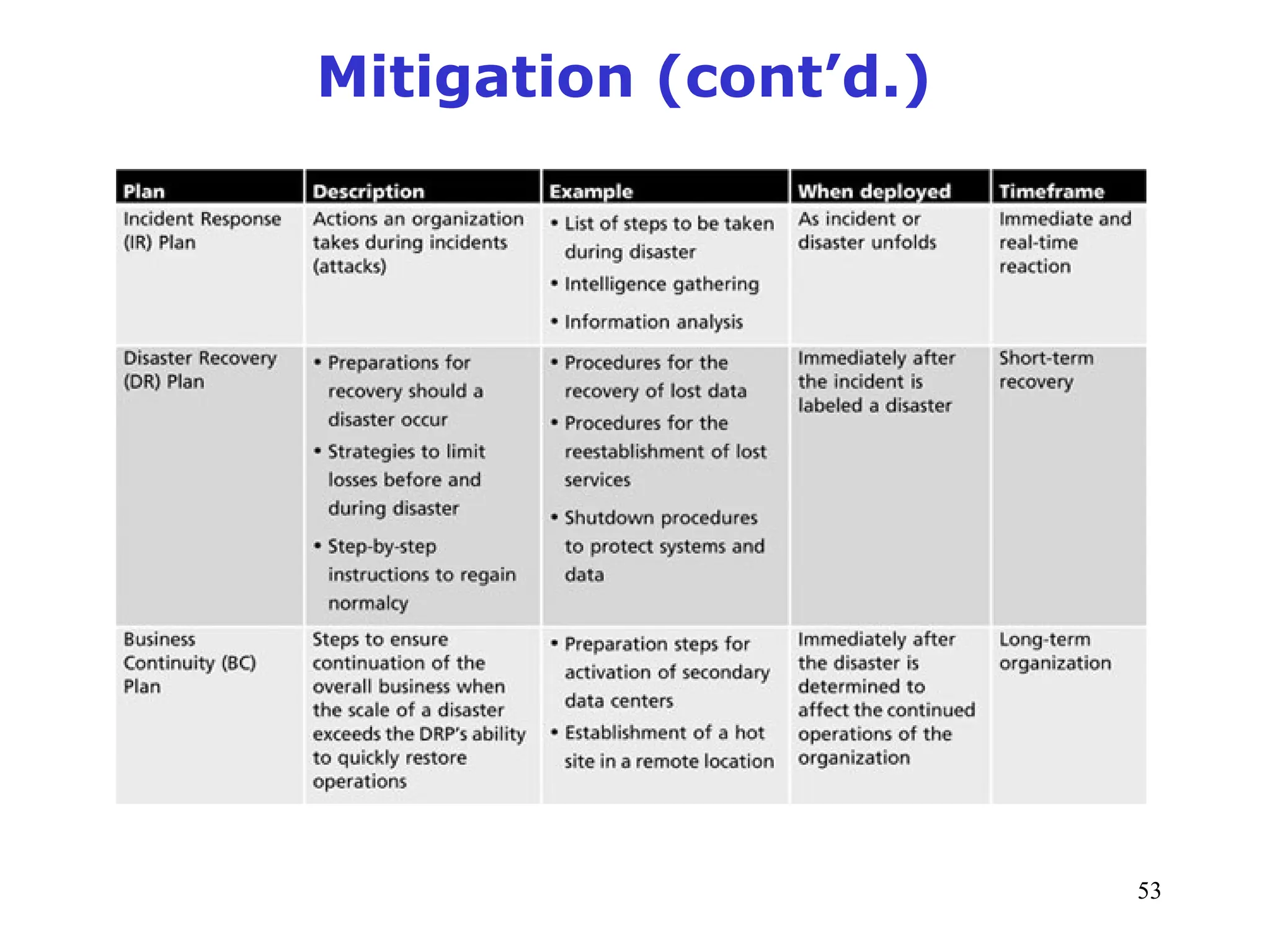
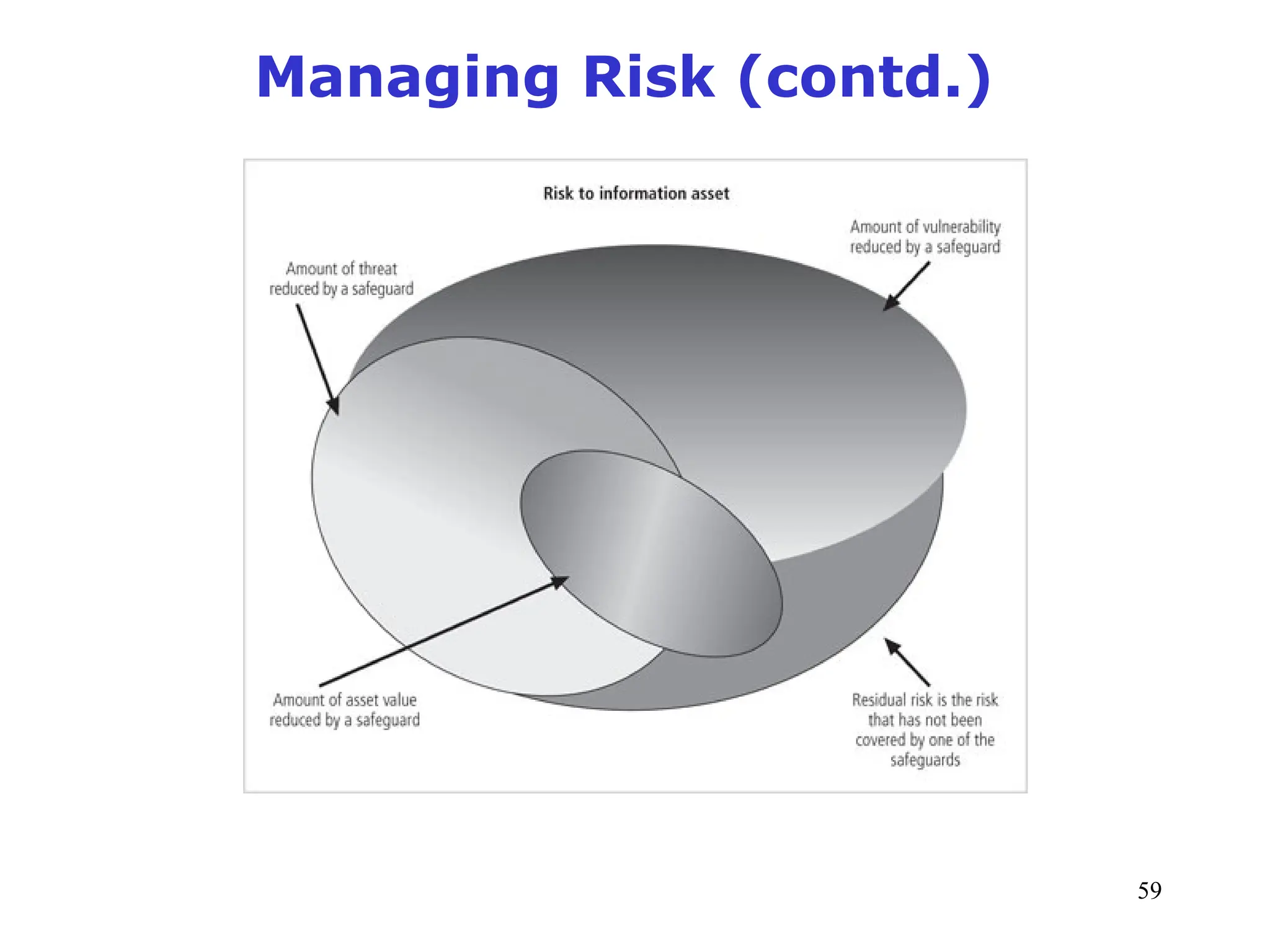
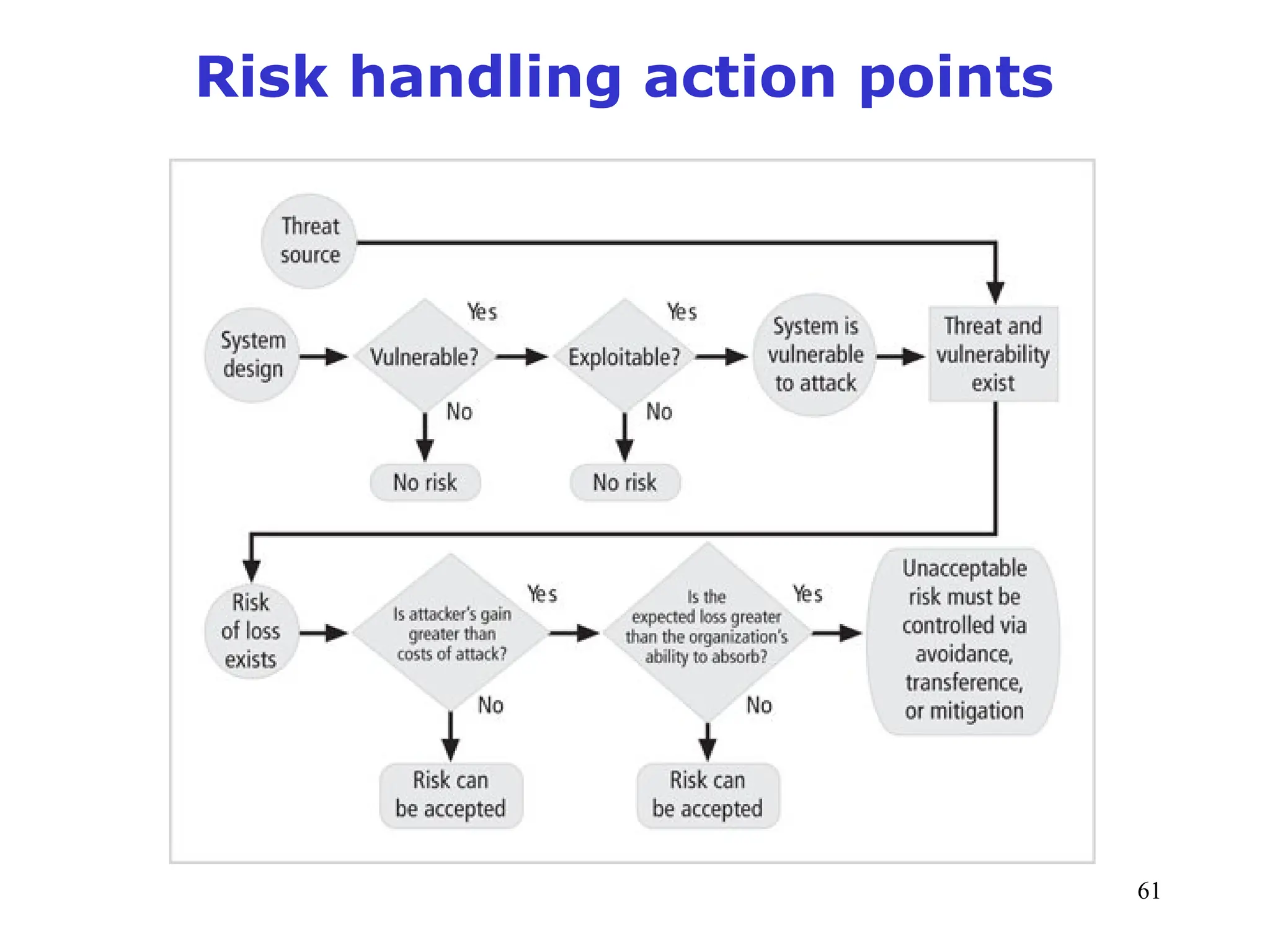
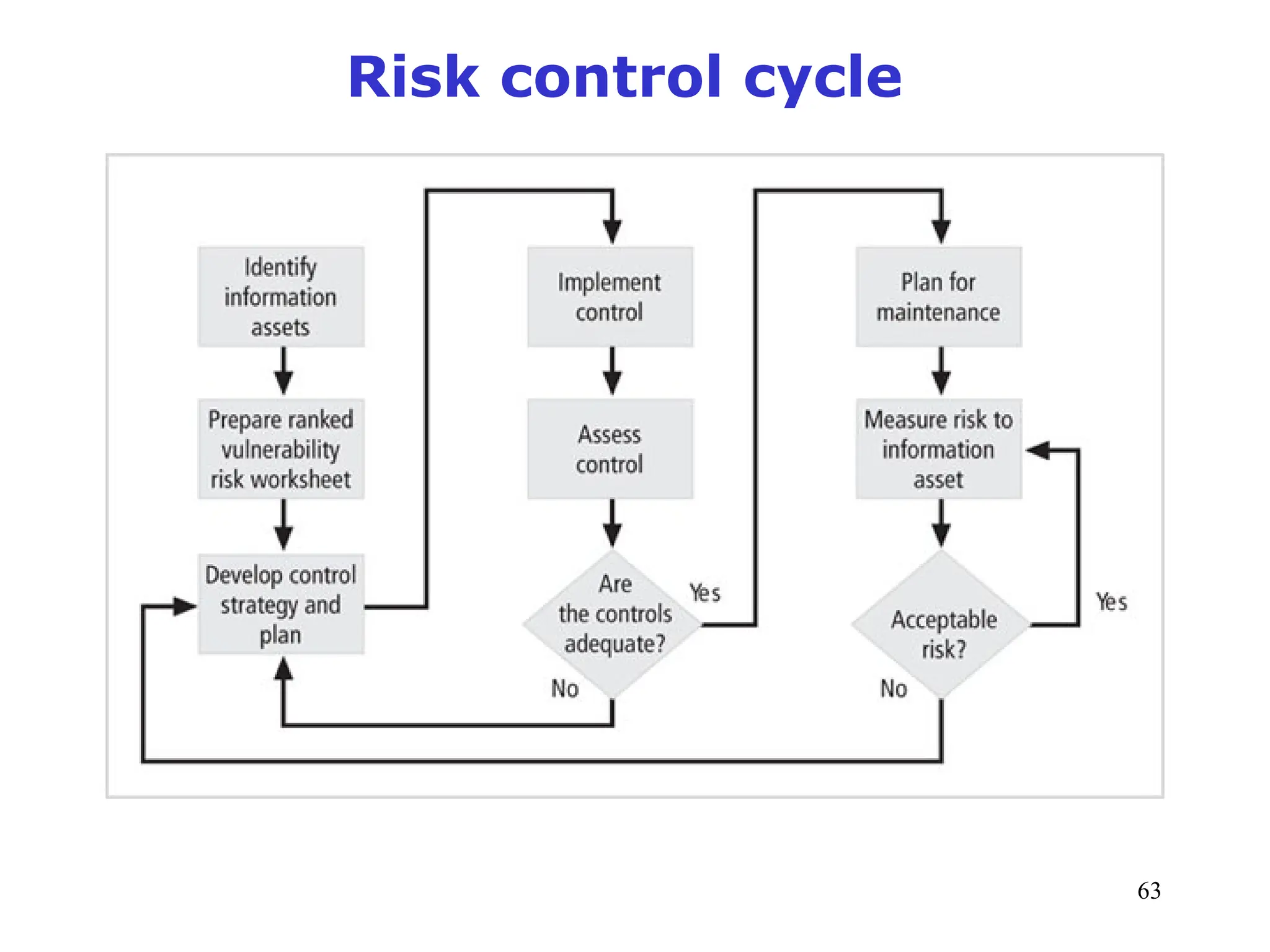
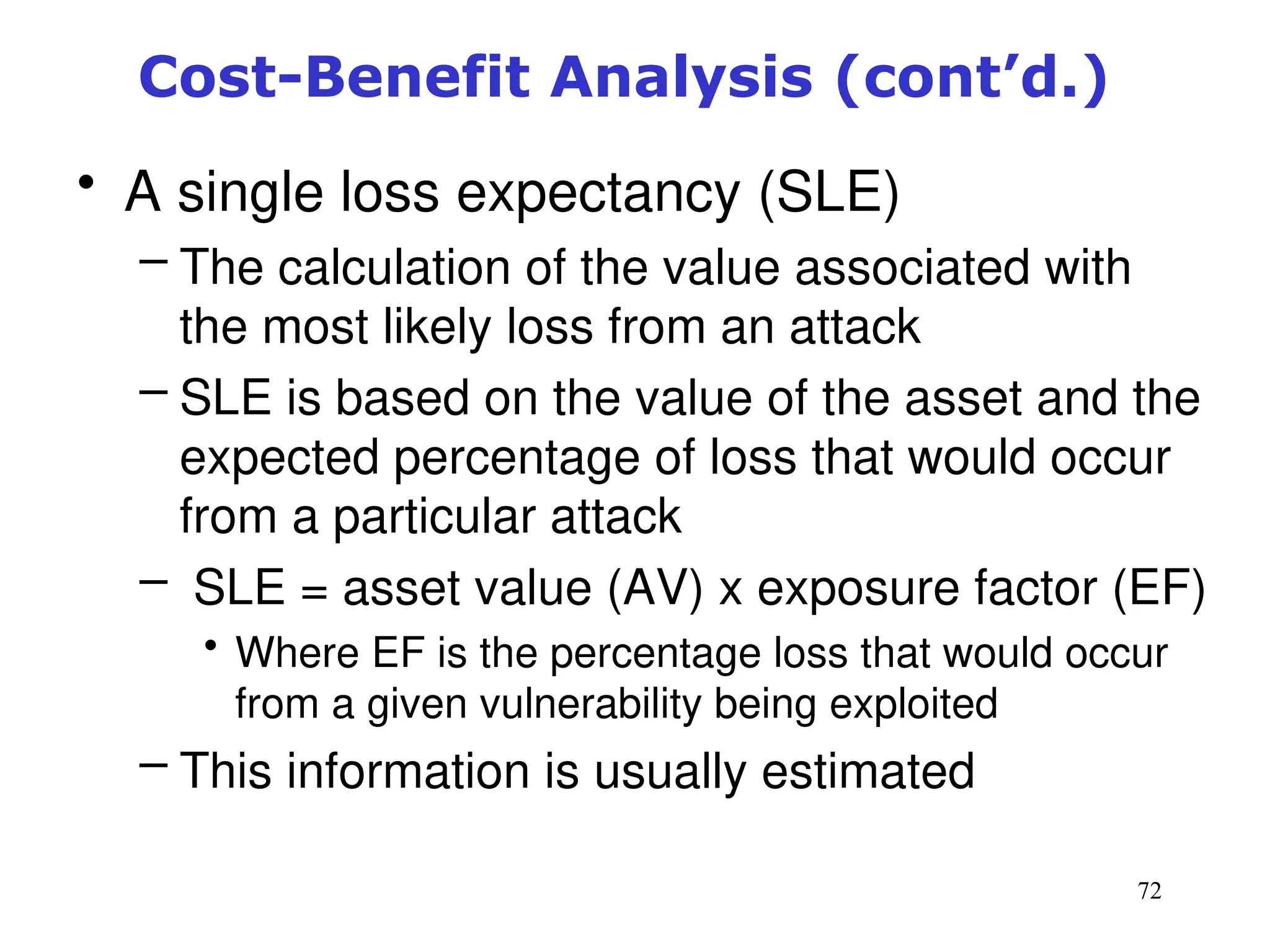
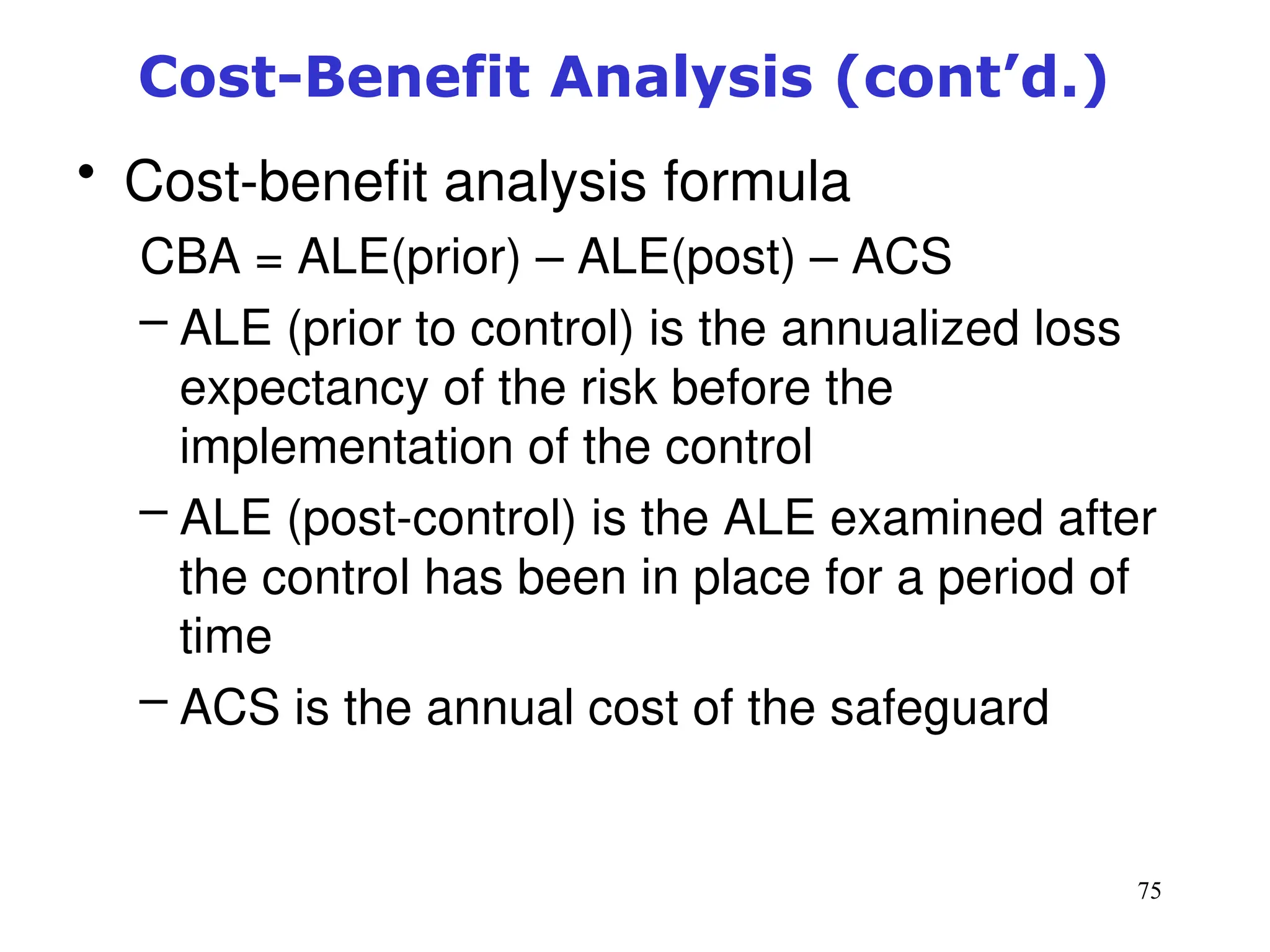
The document outlines key concepts in computer security management focused on risk management, including the identification, assessment, prioritization, and control of risks related to information assets. It emphasizes the need for a structured risk management process, highlighting the roles of various stakeholders, asset inventory creation, and the importance of vulnerability assessment. Additionally, it presents strategies for risk control, such as avoidance, transference, mitigation, and acceptance, while evaluating the organization's risk appetite.
![1
09/03/24 1
Instructor: Suprakash Datta (datta[at]cse.yorku.ca) ext 77875
Lectures: Tues (CB 122), 7–10 PM
Office hours: Wed 3-5 pm (CSEB 3043), or by
appointment.
Textbooks:
1. "Management of Information Security", M. E. Whitman, H. J.
Mattord, Nelson Education / CENGAGE Learning, 2011, 3rd Edition
2. "Guide to Computer Forensics and Investigations", B. Nelson, A.
Phillips, F. Enfinger, C. Steuart, Nelson Education / CENGAGE
Learning, 2010, 4th Edition.
CSE 4482: Computer Security Management:
Assessment and Forensics](https://image.slidesharecdn.com/qwe12-240903124939-f8694abb/75/cybersecurity-risk-management-cybersecurity-risk-management-ppt-1-2048.jpg)