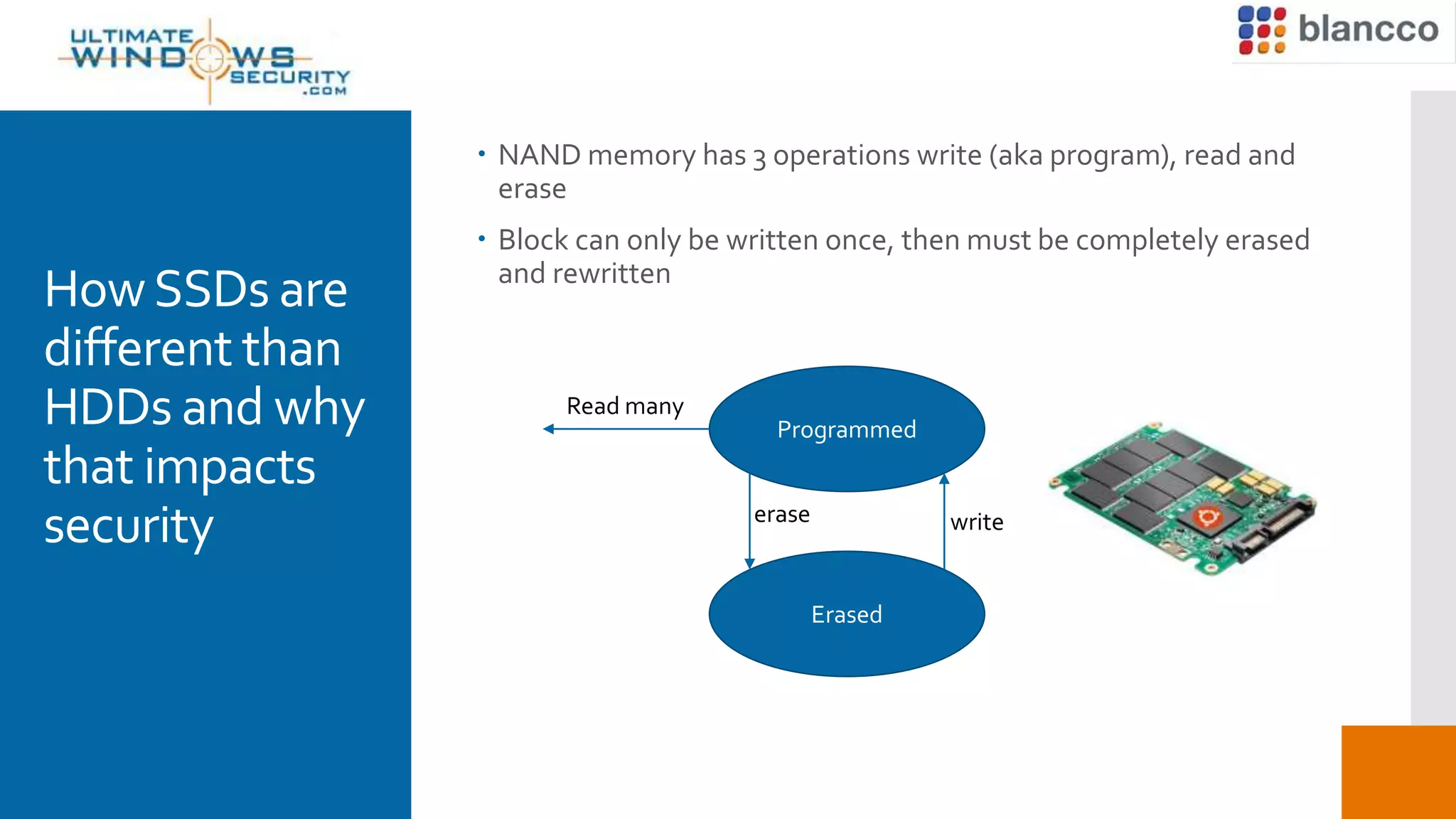
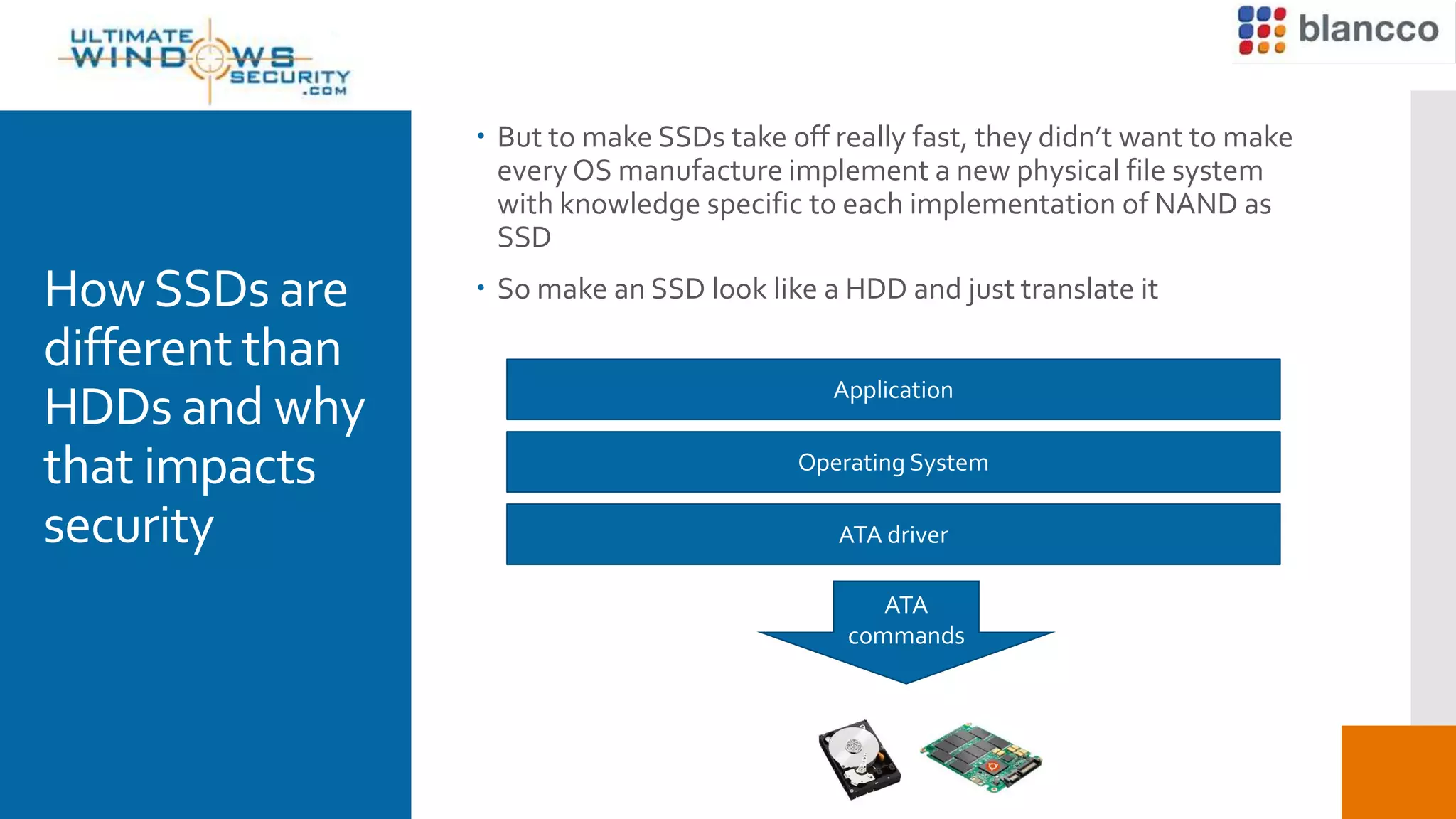
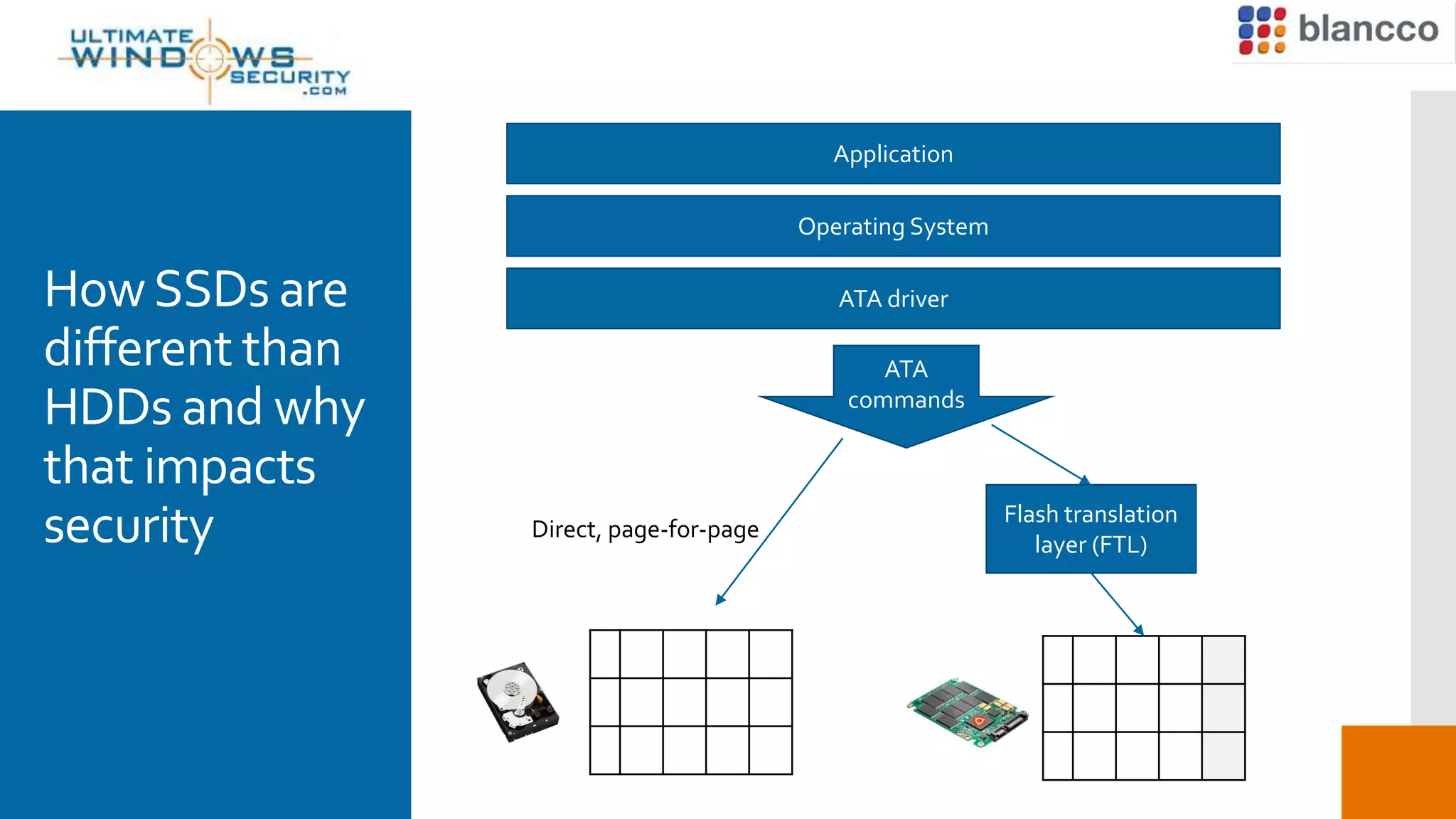
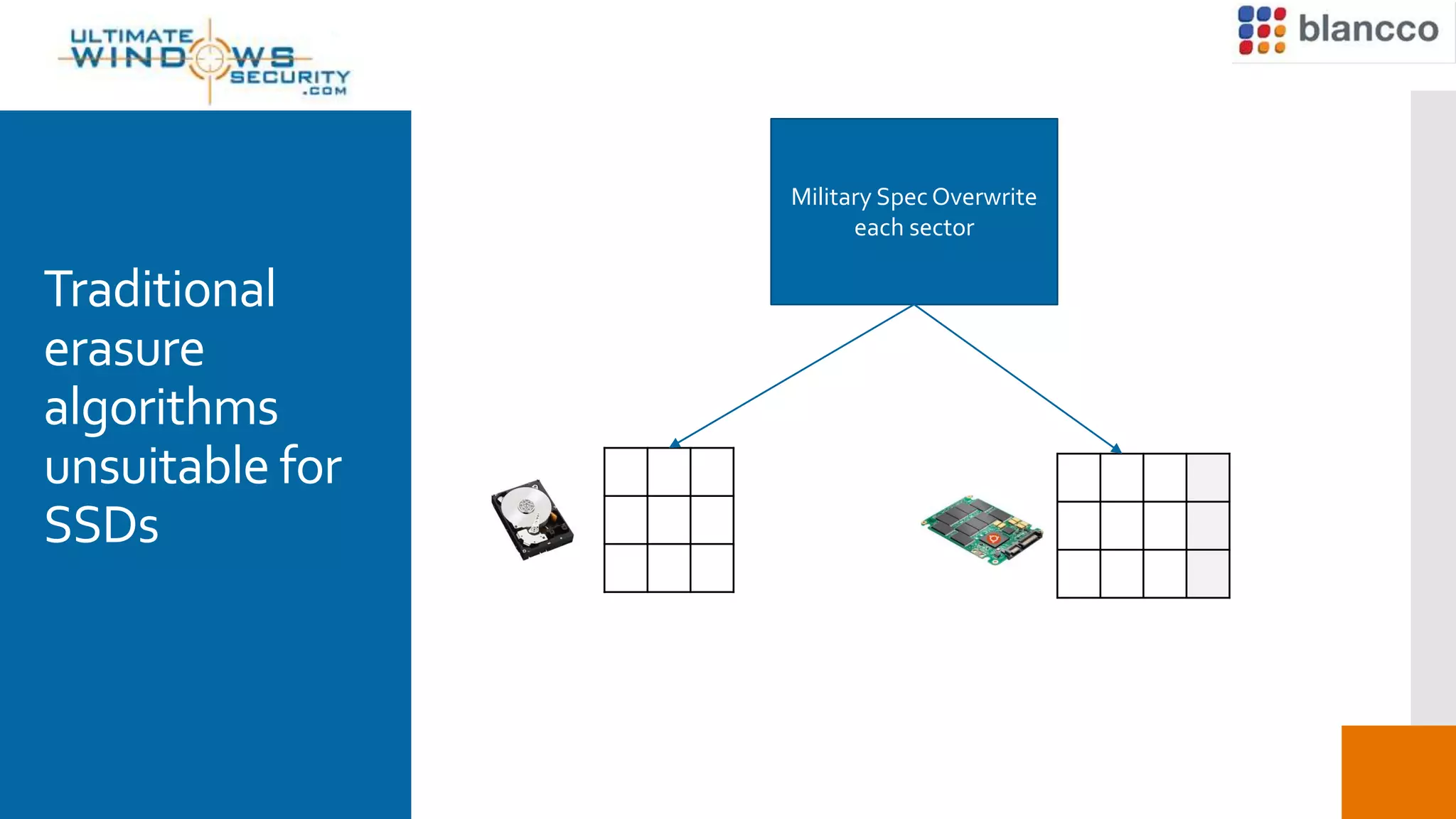
This document discusses the challenges of securely erasing data from solid state drives (SSDs) compared to traditional hard disk drives (HDDs). It explains that SSDs have different memory architecture than HDDs that impacts how data is written, read, and erased. Traditional erasure methods do not fully erase data from SSDs. The document outlines SSD-specific issues like wear leveling and firmware locks that must be addressed for complete erasure. It emphasizes the need for multi-stage, manufacturer-specific erasure processes that are verifiable and provable to fully remove data from SSDs.









![Other issues
What is ATA Secure Erase?
Set of commands embedded in
most hard drives since 2001
Secure Erase is a command not a
physical operation
Therefore it’s all about the
implementation (i.e. code)
behind that command
“it’s up to each manufacturer to
implement it correctly. In their
review of the secure erase
command,Wei et al., 2011, have
shown that over the 12 models
of SSDs studied, only eight
offered the ATA Secure Erase
functionality, and over those
eight drives, three had buggy
implementations [11].” -
http://codecapsule.com/2014/02
/12/coding-for-ssds-part-4-
advanced-functionalities-and-
internal-parallelism/
https://www.usenix.org/leg
acy/event/fast11/tech/full_
papers/Wei.pdf](https://image.slidesharecdn.com/solidstatedrivesssdsecureerasuredeepdivewhatittakestoreallymakethedatagoaway-170201140322/75/Solid-State-Drives-SSDs-What-it-Takes-to-Make-Data-Go-Away-15-2048.jpg)