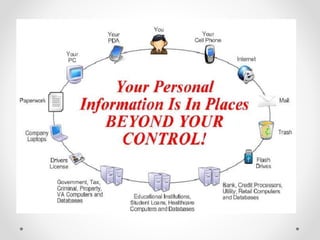
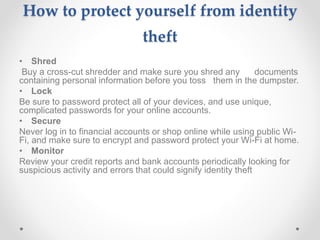
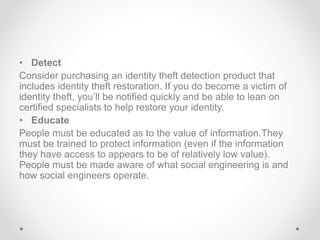
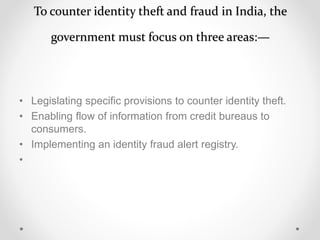
Identity theft occurs when someone steals personal information like names, addresses, birth dates, social security numbers, etc. and uses it to impersonate the victim. This can be used to open credit cards and bank accounts, take loans, get medical treatment, and more all in the victim's name. Victims can face damaged credit, financial losses, and spend significant time repairing their credit and good name. Common ways identity thieves get information include dumpster diving, phishing emails/calls, hacking computers and networks, and data breaches at companies. Laws like the Identity Theft and Assumption Deterrence Act and the Information Technology Act in India make identity theft a crime and provide punishments. Victims should monitor accounts,