The document discusses a system for improving information delivery and clustering in drip irrigation management using wireless sensor networks (WSNs), focusing on the efficiency of data transmission and monitoring for precision agriculture. It outlines the use of distributed clustering algorithms to enhance water level information delivery and optimize agricultural practices through real-time monitoring of various environmental parameters. The study highlights the importance of WSNs in facilitating better decision-making and automation in agricultural systems.



![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 2
1. INTRODUCTION
A normal wireless sensor network (WSN) protocol consists of layers like
application layer, transport layer, network layer, data link layer, physical
layer, power management plane, mobility management plane and the task
management plane. Currently two standard technologies available for
wireless sensor networks are Zigbee, and Bluetooth both operates in
Industrial Scientific and Medical (ISM) band of 2.4 GHz, which provides
license free operation for scientific research and study purpose. In general,
increase in frequency increases bandwidth which allows high speed data
transmission. In-order to decrease the power requirement distance between
sensor nodes has to be reduced as possible [13-16]. Multi-hop
communication over the ISM will be promising technique in WSN, since it
consumes less power than traditional single-hop communication. A sensor is
intelligent to convert physical or chemical readings gathered from the
environment into signals that can be calculated by a system. A multi-sensor
node is intelligent to sense several magnitude values in the same device. In a
multi-sensor, the input variables may be temperature, fire, motion detection
sensors, infrared radiation, humidity and smoke. A wireless sensor network
could be a functional architecture for the deployment of the sensors used for
fire detection and verification.
The most imperative factors for the quality and yield of plant growth are
temperature, humidity, light and the level of nutrition content of the soil in-
addition with the carbon dioxide in the surrounding atmosphere. Constant
monitoring of these ecological variables gives information to the cultivator
to better understand, how each aspect affects growth and how to achieve
maximal crop productiveness. The best possible greenhouse climate
modification can facilitate us to advance productivity and to get remarkable
energy saving, predominantly during the winter in northern countries. In the
past age band, greenhouses it was enough to have one cabled dimension
point in the middle to offer the information to the greenhouse automation
system. The arrangement itself was typically simple without opportunities to
supervise locally heating, light, ventilation or some other actions which
were affecting the greenhouse interior climate. The archetypal size of the
greenhouse itself is much larger than it was before, and the greenhouse
facilities afford several options to make local adjustments to light,
ventilation and other greenhouse support systems. However, added
measurement data is also needed to put up this kind of automation system to
labor properly. Increased number of measurement points should not
dramatically augment the automation system cost. It should also be probable
to easily alter the location of the measurement points according to the](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-4-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 3
particular needs, which depend on the definite plant, on the possible changes
in the external weather or greenhouse arrangement and on the plant
placement in the greenhouse. Wireless sensor network can form a helpful
part of the automation system architecture in contemporary greenhouses
constructively. Wireless communication is used to transmit the
measurements and to establish communicate between the centralized control
and the actuators located to the different parts of the greenhouse. In highly
developed WSN systems, some parts of the control system has to be
implemented on the field in a distributed so that local control loops can be
created. WSN is fast, cheap and easy compared to cabled network systems.
Moreover, it is easy to relocate the measurement points when needed by
immediately moving sensor nodes from one location to another within a
communication range of the coordinator gadget. If the greenhouse
vegetation is high and dense, the small and light weight nodes can be
hanged up with the branches. WSN is easy to maintain, relatively
inexpensive and trouble-free. The only other expense occur only when the
sensor nodes run out of batteries (figure 1) and the batteries have to be
charged or replaced. Lifespan of the battery can be increased to several
years if a proficient power saving algorithm is applied. In this work, the
very first steps towards the wireless greenhouse automation system by
building a wireless measuring arrangement for that purpose is taken and by
testing its feasibility and reliability with a straightforward setup [2, 3].
Figure 1: Various blocks of a wireless sensor node
These greenhouse parameters are generally essential in the case of
precision agriculture [4, 5]. In this paper, a mechanism for cluster formation](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-5-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 4
for drip irrigation system for precision agriculture has been elaborated.
Keeping aside these greenhouse parameters which are essential for
cultivation, methodology for cluster formation in drip irrigation system shall
be discussed. A distributed clustering mechanism has been employed for
cluster formation [7, 8]. Also, few parameters that is necessary for wireless
sensor node deployment, for agricultural application has been discussed in
the subsequent sections.
2. PLANTATION MANAGEMENT USING WSN
For developing an efficient system for agricultural system management, the
foremost inputs to the system will be the availability of accurate data’s
(figure 2) like soil properties, agronomic, physicochemical parameters,
atmospheric data, etc., Data collection can be made flexible on a day-to-day
basis or even hourly basis based on the need. Normal laboratory analysis of
above mentioned parameters and manual decision-making take a long time
even with the most sophisticated analytical techniques. Most of the samples
have to be brought from the field to laboratories to analyze most of the time.
By the time the results are available and decisions are taken, the conditions
of the farm may change which results in inappropriate decision. Quick and
quality decision-making at the farm level will enhance agricultural
productivity and quality manifold which further needs accurate and real time
properties of the field.
Figure 2: WSN in Precision agriculture](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-6-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 5
Computer-aided decision-making process can handle and analyze several
input parameters at the same time which involves large databases.
Monitoring of physical and environmental parameters including soil
moisture, soil temperature, nutrition content of the soil, leaf temperature,
relative humidity, air temperature, rainfall, vapor pressure and availability of
sun light is done through a wireless sensor network. WSN is comprised of
distributed sensors to monitor physical, chemical and environmental
conditions. WSN integrates sensors, wireless and processing tools whoch
are capable of sensing different physical parameters without any loss in
sensed data accuracy. The parameters are processed and wirelessly
transmitted to a centralized data storage system through a gateway from
where they may be remotely accessed and analyzed by the user [17]. The
system architecture of a WSN-based system consists of different sensors
interfaced to electronic hardware with a suit of data processing tools. The
electronic hardware is also equipped with wireless communication modules
which allows sensed data to be modulated and transmitted in accordance to
a selected protocol. These hardware nodes are called motes in WSN. Each
of these motes are interfaced with some set of wireless sensors depending
on the applications interest. The sensors may be programmed to sense in a
continuous or discrete manner. The needed parameters for precision
agriculture have been enumerated in the next section.
3. WSN IN PRECISION AGRICULTURE
WSN technology can broadly be applied into three areas of agriculture: a)
Fertilizer control, b) Irrigation management and c) Pest management. The
sensors are interfaced with the mote to sense parameters like temperature,
relative humidity, solar radiation, rainfall, wind speed and direction, soil
moisture and temperature, leaf wetness and soil pH. The following
parameters should essentially be accounted before deploying sensor nodes
in a wireless sensor field.
A. The Greenhouse Environment
A contemporary greenhouse can consist of copious parts which contain their
own confined climate variable settings. As a result, a quantity of
measurement points is also needed. This group of environment is
demanding both for the sensor node electronics and for the short-range
IEEE 802.15.4 wireless network, in which communication choice is greatly
longer in open environments [9, 10].](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-7-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 6
B. Sensors
Speedy response time, squat power consumption and tolerance beside
moisture climate, relative humidity and temperature sensor forms an idyllic
preference and explanation for the greenhouse environment.
Communication among sensor nodes can be carried out by IIC interface.
Luminosity can be measured by light sensor, which converts light intensity
to equivalent voltage. Unstable output signal is handled by low-pass filter to
acquire exact luminosity values. CO2 measuring takes longer time than
other measurements and CO2 sensor voltage supply have to be within little
volts. The carbon dioxide assessment can be read from the ensuing output
voltage. Operational amplifier raises the voltage level of weak signal from
the sensor.
C. Greenhouses
A greenhouse is a pattern covering the ground frequently used for growth
and progress of plants that will revisit the owner’s risk, time and capital.
This exhibit is mounted with the purpose of caring crop and allowing a
better environment to its advancement. This defend is enough to guarantee a
higher quality in production in some cases. However, when the chief idea is
to achieve a superior control on the horticulture development, it is necessary
to examine and control the variables that influence the progress of a culture.
The chief role of a greenhouse is to offer a more compassionate
environment than outside. Unlike what happens in customary agriculture,
where crop conditions and yield depend on natural resources such as
climate, soil and others, a greenhouse ought to promise production
independent of climatic factors. It is noteworthy to view that even though a
greenhouse protects crop from peripheral factors such as winds, water
excess and warmth it may root plentiful problems such as fungus and
extreme humidity [1].
D. Temperature
Temperature is one of the main key factors to be monitored since it is
unswervingly related to the development and progress of the plants. For all
plant varieties, there is a temperature variety considered as a best range and
to most plants this range is comparatively varying between 10ºC and 30ºC.
Among these parameters of temperature: intense temperatures, maximum
temperature, minimum temperature, day and night temperatures, difference
between day and night temperatures are to be cautiously considered.
4TH WORLD CONGRESS ON COMICULTUR](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-8-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 7
E. Water and Humidity
An additional significant factor in greenhouses is water. The absorption of
water by plants is associated with the radiation. The deficient in or low level
of water affects growth and photosynthesis of these plants. Besides air, the
ground humidity also regulates the development of plants. The air humidity
is interconnected with the transpiration, while the ground humidity is linked
to water absorption and the photosynthesis. An atmosphere with tremendous
humidity decreases plants transpiration, thereby reducing growth and may
endorse the proliferation of fungus. On the other hand, crouch humidity
level environments might cause dehydration [6].
F. Radiation
Radiation is an elementary element in greenhouse production and sunlight is
the key starting place of radiation. It is an imperative component for
photosynthesis and carbon fixing. Momentous radiation features are
intensity and duration. The radiation intensity is linked to plant development
and the duration is explicitly associated with its metabolism.
G. CO2 Concentration
CO2 is an indispensable nutrient for the plant development, allowing the
adaptation of carbon. The carbon retaining process occurs through the
photosynthesis when plants take away CO2 from the atmosphere. During
photosynthesis, the plant use carbon and radiation to produce carbohydrate,
whose purpose is to permit the plant development. Therefore, an enriched
air environment should add to plant growth, but it is also vital to note that an
intense carbon level may turn the environment poisonous.
4. THE DRIP IRRIGATION AUTOMATION SYSTEM
Conventional irrigation methods like overhead sprinklers and flood-type
feeding systems usually lead to wetness in and around the lower portion of
the leaves and stems of the plants. The entire soil surface becomes saturated
and often stays wet even after the irrigation is completed. Such condition
induces infections in leaf mold with fungus growth. Flood-type methods
consume a large volume of water, but the area between crops remains dry
and receives moisture only by the incidental rainfall. The drip irrigation
technique slowly applies some small amount of water to the plant's root
zone. Water is supplied frequently, or on daily basis to maintain favorable
soil moisture condition and prevents moisture-stress in the plant with proper](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-9-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 8
use of water resources. WSN based drip irrigation system is a real time
feedback control system which continuously monitors and controls all the
activities of the drip irrigation system.
A typical drip irrigation system consist of delivery systems, filters, pressure
regulators, valve or gauges, chemical injectors, measuring
sensors/instruments and controllers. WSN framework installed in the field
could gather various physical and chemical parameters related to irrigation
and plant health. These includes various temperature parameters like
ambient temperature, ambient humidity, soil temperature, drip water
temperature, soil moisture, soil pH, water pressure, flow rate, amount of
water, energy calculation, chemical concentration and water level. The data
is sent to the central server wirelessly through the motes and gateways [11,
12]. Based on the data received, the central server generates necessary
control signals, which are routed to the respective controllers through
control buses which enables implementation of closed-loop automation for
the drip irrigation system. The main function of the system is to enable
switching on and off of the motors and gauges remotely. The system also
ensures that all the devices are checked for fault and only then the motor is
started.
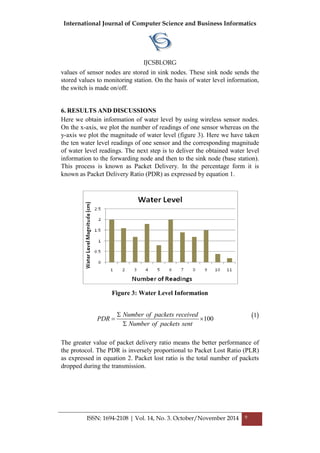
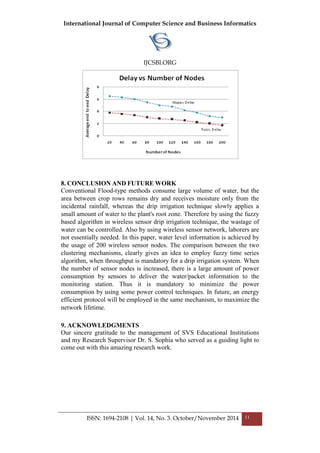
5. ALGORITHM FOR DRIP IRRIGATION SYSTEM
In this paper, a mesh topology in which sensor nodes are placed in the farm
area have been properly reviewed and adopted [17]. Sensors in this topology
are mobile where as the base station is stationary and it collects the data
from sensor nodes and process them. Efficient clustering of sensors in the
wireless sensor field is considered as the basic operation in this research
work. This work elaborates how to forward the sensed data to the base
station effectively. For this purpose the farm area consisting of deployed
WSN nodes has been formed initially. Now set the position of sensor and
sink nodes in the farm and the monitoring station location. Set the
transmission range for each node. Now for each node, calculate distance
from: node to node, node to sink and node to forwarding node. Also
calculate: Angle a and predict min angle for next route based on fuzzy time
series, if the current angle a is available as predicted, continue with path
[find possible node (x, y)] or else hold packet for limited time. If
connections (i, j) = 1 i.e., there is a link based on transmission range, send
the packet information i.e., water level information and some other essential
details about field of interest. The packet reaches to the sink node and gets
stored there. Else connections (i, j) = infinity, end the structure. Therefore](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-10-320.jpg)

![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 12
REFERENCES
[1] Iqbal Singh, Meenakshi Bansal, (2011), "Monitoring water level in agriculture using
sensor networks", International Journal of Soft Computing and Engineering, Volume 1,
Issue 5.
[2] Qingshan S, Ying L, Gareth D, Brown D, (2004), "Wireless intelligent sensor networks
for refrigerated vehicle", IEEE 6th Symposium on Emerging Technologies Mobile and
Wireless Communication, Shanghai, China.
[3] Mahir Dursun, Semih Ozden, (2011), "A wireless application of drip irrigation
automation supported by soil moisture sensors", Scientific Research and Essays, Volume 6.
[4] Baggio A, (2005), "Wireless sensor networks in precision agriculture", Proceedings of
the Workshop on Real-World Wireless Sensor Networks, pp. 50-51.
[5] Kim Y, Evans R.G, Iversen W.M, Pierce F.J, (2006), "Instrumentation and control for
wireless sensor network for automated irrigation", ASAE Annual International Meeting.
[6] Steven R, Evett R, Troy Peters, Terry A.H, (2006), "Controlling water use efficiency
with irrigation automation: cases from drip and center pivot irrigation of corn and soybean",
Southern Conservation Systems Conference, Amarillo TX.
[7] SRB Prabhu, S.Sophia, (2011), “A survey of adaptive distributed clustering algorithms
for wireless sensor networks”, International Journal of Computer Science and Engineering
Survey, Volume 2, Number 4, Pages 165-176.
[8] SRB Prabhu, S.Sophia, (2013), “Real-world applications of distributed clustering
mechanism in dense wireless sensor networks”, International Journal of Computing,
Communications and Networking, Volume 2, Number 4.
[9] Evans R.G, (2000), “Controls for Precision Irrigation with Self-Propelled Systems",
Proceedings of the 4th Decennial National Irrigation Symposium.
[10] Callaway E.H, (2004), "Wireless sensor networks: architectures and protocols”,
Auerbach Publications: New York, NY, USA.
[11] SRB Prabhu, S.Sophia, (2013), “Mobility assisted dynamic routing for mobile wireless
sensor networks”, International Journal of Advanced Information Technology, Volume 3,
Number 3.](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-14-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 13
[12] SRB Prabhu, S.Sophia, (2012), “A research on decentralized clustering algorithms for
dense wireless sensor networks”, International Journal of Computer Applications, Volume
57.
[13] Evett S.R, Howell T.A, Schneider A.D, Upchurch D.R, Wanjura D.F, (1996),
"Canopy temperature based automatic irrigation control", Proceedings of the International
Conference on Evapotranspiration and Irrigation Scheduling, San Antonio, TX..
[14] Rajaravivarma V, Yang Y, Yang T, (2003), “An overview of wireless sensor network
and applications”, Proceedings of 35th
South Eastern Symposium on System Theory.
[15] Wanjura D.F, Upchurch D.R, Mahan J.R, (1992), "Automated irrigation based on
threshold canopy temperature", Transactions of the ASAE, Volume 35.
[16] Ning Wang, Naiqian Zhang, Maohua Wang, (2006), “Wireless sensors in agriculture
and food industry - recent development and future perspective”, Computers and Electronics
in Agriculture, Volume 5, pp. 1-14.
[17] Marron P.J, Minder D, Consortium E.W, (2006), “Embedded research roadmap”,
Information Society Technologies, Germany.
This paper may be cited as:
Prabhu, R. B., Sophia, S. and Mathew, A. I., 2014. A Review of Efficient
Information Delivery and Clustering for Drip Irrigation Management using
WSN. International Journal of Computer Science and Business Informatics,
Vol. 14, No. 3, pp. 1-13.](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-15-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 14
Dual Hybrid Algorithm for Job Shop
Scheduling Problem
Do Tuan Hanh
Hanoi National University of Education
136 Xuân Thuy Cau Giay Hanoi Vietnam
Vu Dinh Hoa
Hanoi National University of Education
136 Xuân Thuy Cau Giay Hanoi Vietnam
Nguyen Huu Mui
Hanoi National University of Education
136 Xuân Thuy Cau Giay Hanoi Vietnam
Abstract
This paper presents a dual hybrid method to solve job shop scheduling problem
(JSP). We use a genetic algorithm (GA) combined with the dual hybrid approach to
obtain a new genetic algorithm (GTD-GA). The algorithm proposed new hybrid
approach called dual hybrid, and new data organization with the purpose of
maximizing the GT algorithm. They're building program for the experimental
schedule finding maximum job shop problem. In order to prove the effectiveness of
the algorithm, we ran on the standard given by Muth and Thompson and compare
with the results of Yamada used GT-GA for JSP. Moreover, we also compare them
with the local search genetic algorithm of M. Kebabla, L. H. Mouss for the job shop
problem.
Keywords: Jobshop Scheduling, Schedule, Genetic Algorithm.
1. INTRODUCTION
Job shop scheduling problem (JSP) is one of the well-known classic problems. There
are many approaches to solve it and the first work on this field is perhaps the paper
of Fiedman and Akers [3].](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-16-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 16
Job shop scheduling problem is a NP-hard problem and is one of the most difficult
combinatorial optimization problems. JSP problem can be solved with a polynomial
algorithm only in some special cases. For n = 2, Akers [2] proved that the problem
of finding JSP can be solve with a polynomial time algorithm using shortest path
algorithm. Using a method of Kravchenko and Sotskov [11], Brucker [5] give a
polynomial time algorithm for the JSP with m = 2 machines and n = k (k is a
constant) jobs. Except for some special cases mentioned above, the remaining cases
of JSP are NP-hard. This is the result of a research of Shaklevich Sotskov [15]. Table
2 summarizes the complexity of JSP.
Table 2. The computational complexity of JSP
Number of m machines
2 3 Constant Depending
on the
The
number n
jobs
2 P P P P
3 P P P NP-hard
Constant P P NP-hard NP-hard
Depending
on the
P NP-hard NP-hard NP-hard
JSP was published first time in 1955. A statement for this problem can be found in a
paper of Akers and Friedman. Followed them are the studies of Bowman (1959) and
Wagner (1959) in which there was only one job that can be handled on maximal 3
computers. The year 1963 marked an important milestone in JSP when Fisher and
Thompson [12, 7] studied a JSP with 10 jobs and 10 machines. This test was
considered to be one of the most intractable of JSP because the optimal solution was
found ever after more than 20 years later. They proposed GT algorithm as active
schedules. The result of H. Fisher and GLThompson [7] can be found in the book
"Industrial Scheduling", edited by JF-Muth and GL- Thompson [12] in 1963.
The method of solving the problem as 'branching method approach' introduced by
GH Brooks and CR White [4] who pioneered solving the job shop. Finally, in 1985,
E. Carlier and Pinson [6] succeeded in solving optimization problems Mt10 using
algorithms branch access. Finding optimal solution for JSP with unsightly test is a
major challenge because it is a NP-hard problem. Thus, approximate methods have
been developed. One of the approximate methods considered to be most effective is
genetic algorithm.](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-18-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 17
John Holland [9] is considered as the founder of genetic algorithm. GA (Genetic
Algorithms) is characterized by a search strategy based on population and by the
genetic operators: selection, mutation and crossover. Nakano and Yamada [13]
developed the first classical hybrids method and obtained quite good results. Yamada
[16] developed GT-GA algorithm with many significant achievements. In 2012, M.
Kebabla, LH Mouss [10] offered “A local search genetic algorithm for the job shop
scheduling problem”. Recently, Nguyen Huu Mui and Vu Dinh Hoa [14] proposed a
new hybrid method coded calendars by natural numbers and a new crossover
operator combined 3 individual parent to an individual children.
After a period of researching methods to solve the problem, we find a new hybrid
method with new mutations which may be more efficiently. Our innovations are:
1. Reorganize database to reduce leverage calculations suitable grafting and
new mutations.
2. Use the GT algorithm taking good jealous of mutant to a better generation,
with the aim to get earlier convergence than the GT-GA.
3. Apply new crossover method: from 2 individual parents P1, P2 hybridized
according to GT algorithm to F1 and F2 offspring, then proceed hybridized form F1
and F2 to FF1 and FF2. With this new crossover approach, this starting personal
space can be expanded to diverse selection closer to a optimal experience.
2. CONTENT
In what follows, we present a method of organizing new data processing allows new
mutations and new crossover.
2.1. New data encryption
Suppose there are n jobs to be processed on m machines. T matrix is called matrix
sequentially technology. We will encode matrix C where Cij is 1 if the job j is done
on machine i at some time, and Cij is 0 if the job j is not done on machine i. L_T is
the matrix where L_Tij is the next machine which performs the job i, according the
sequential technology, after this job was performed on the j machine. F_T is the
matrix where F_Tij is the machine which performed the job i just before it has to be
performed on the j machine according the sequentially technology.](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-19-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 18
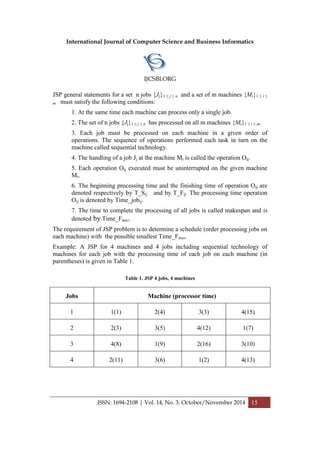
For example is the problem of 4 jobs, 4 machines given in Table 1. T matrix and
transformation matrix C, L_T, F_T are given in Figure 1, respectively:
Figure 1. The matrix T, C, L_T, F_T
2.2. Mutation operator
Operator mutations on individual parent P were carried out by following these steps:
1. Choose a random matrix H where Hij is 0 or 1, apply the GT algorithm to
generate mutant P_C using the matrix H.
2. Create G, the set of the first stage in the sequence of all these technology
jobs, using the matrix C (only if Cij is 1) so that if Oij G then T_Sij=0; and VT [i]
= 1.
3. Construct the set V_G G satisfying that if Oij V_G, then T_Sij is the
possible minimum value.
4. Construct the set E_G V_G satisfying if Oij E_G, then HiVT[i] =1 and j
= PiVT[i].
5. If E_G ≠ Ø, then choose randomly Oij E_G. If E_G = Ø, choose Oij
V_G randomly.
6. P_CiVT[i] = j; VT[i] = VT[i]+1; Remove Oij from the set G; if k ≠ 0 (with k
= L_Tij), then add Oik in G.
7. Update to T_Sij if Oij G using the following formula:
r = P_CiVT[i]-1
k = F_Tij
T_Sij = Max( T_Sir + Time_jobir , T_Skj + Time_jobkj)
8. Go to step 3 until all stages are scheduled in mutant P_C.](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-20-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 19
If mutant P_C is less adaptive than individuals P, then we repeat these steps to create
mutant P or stop once reaching the maximum number of mutations (through variable
input level).
For example, individual parent P and H matrix generated mutant P_C in Figure 2:
Figure 2. The P parent and mutant P_C matrix H
Time_Fmax Individual's parent P is: 66
Time_Fmax P_C of mutants is: 48
2.3. GTD Crossover
Operator 2 hybrid created on individual P1 and P2 parents was conducted according
to the following steps:
1. Choose a random matrix H which Hij the value 0 or 1. Using genetic
algorithms get better GT parents P1 and P2 through the matrix H to generate F1 and
F2 offspring. From the F1 and F2 be the application of the GT get good genes of
their parents through the matrix H to generate FF1 and FF2 offspring.
2. Create G is the set of the first stage in the sequence of all these
technologies jobs through the matrix C (Cij = 1 will be included in G), if Oij G is
T_Sij=0; and VT [i] = 1.
3. Construct set V_G G satisfying if Oij V_G, then T_Sij is the minimum
value that can be obtained.
4. Construct set E_G_F V_G satisfying if Oij E_G, then HiVT[I ] = 1 and j
= P1iVT[i] .
5. If E_G_F ≠ Ø, then choose randomly Oij E_G, then trip to step 8.
6. If E_G_F = Ø, Set E_G_M V_G satisfied if Oij E_G, then HiVT[i ] = 0
and j = P2iVT[i] .
7. If E_G_M ≠ Ø, then choose randomly Oij E_G_M. Conversely, choose
Oij V_G randomly.
8. F1iVT[i] = j; VT[i] = VT[i]+1; Oij removed from the set G; if k ≠ 0 (with k =](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-21-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 20
L_Tij) then add Oik in G.
9. Update to T_Sij if Oij G using the following formula:
r = P_CiVT[i]-1
k = F_Tij
T_Sij = Max( T_Sir+ Time_jobir , T_Skj+ Time_jobkj)
10. Go to step 3 until all phases are scheduled in individual F1 crossovers.
This methodology improves our differences. We produce F2 simultaneously in step 4
with additional conditions: j1=P2iVT[i], with additional conditions in Step 6: j1=P1iVT[i]
and in step 8 with F2iVT[i] =j1. Using F1 and F2 as the parents of FF1 and FF2 to
produce these steps as well as adopted hybrid matrix H. From two individual P1 and
P2 parents we are offering first creation of four new individual at F1, F2 , FF1, FF2
with the same operators number as the creation of our first offspring using GT_GA
algorithm. For example, we give two individual crossover parents P1 and P2 through
the matrix H as shown in Figure 3:
Figure 3. Parents P1, P2 and matrix H
Figure 4. The generated in children F1, F2, FF1, FF2](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-22-320.jpg)

![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 22
The correctness of the algorithm is confirmed by the following characteristics:
1. When initializing n_gen individual's initial population we use GT
algorithm to generate a schedule, so each individual children is born with an active
schedule [13] [16].
2. During mutation, mutant individuals are modified by taking a number of
individual genes fathers through the matrix H applying GT algorithm, so it remains
an active schedule.
3. Allow crossovers from two parent individuals P1 and P2 take individual
genes through the parent matrix H applying GT algorithm to generate children F1
and F2 schedule, so each individual children is born by this calendar will be an
active one. From F1 and F2 and through the matrix H obtained simultaneously
applied genetic algorithms GT with calendar children FF1 and FF2 is a schedule
which actively.
4. The algorithm will stop when it runs through all generations.
5. Since the algorithm maintains the best solution in the population, before or
after the selection, so the algorithm is converged to the global optimum which is not
reduced by the properties of the next generation. These results are discussed with
schema theorem and are proved in [8].
3. RESULT AND CONCLUSIONS
Based on the method proposed in this paper, we have designed a program in C++
language to run tests on a PC with a processor Core 2 Dual-speed 2 4GHz. The
performance of the algorithm was analyzed on a set of benchmarks on the job-shop
scheduling problem instances from literature. The size of the benchmark instances
varied from 10 to 20 jobs and from 5 to 20 machines. We consider (FFT6, FT10,
FT20) proposal by Fisher and Thompson [12]; three problems (ABZ5, ABZ6,
ABZ7) generated by Adams, Balas & Zawack [1]. Table 5 presents the result
compared our proposed GTD-GA algorithm with the GT-GA by Yamada [ 8].
Table 5. Comparison of GTD-GA and GTD-GA
Instance(size)
Best generated
solution with GT-
GA
Best generated
solution with
GTD-GA
Best known
solution
FT06 (6 6) 55 55 55
FT10 (10 10) 930 930 930
FT20 (20 5) 1185 1182 1165](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-24-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 23
FT06 proposal for optimal results also FT10 for optimal results are obtained only
after 80 trials. GT-GA algorithm by Yamada [13] [16] proposed FT06 gives optimal
results after 2 trials, FT10 gives optimal results after 100 trials. Table 6 compares the
results of GTD-GA algorithm with the results of GLS algorithm proposed by M.
Kebabla, LH Mouss [10].
Table 6. Comparison of GT-GA and GLS
Instance(size)
Best
generated
solution with
GT-GA
Best generated
solution with
GA in 5
attempts
Best generated
solution with
GLS in 5
attempts
Best
known
solution
ABZ5 (10 10) 1234 1238 1234 1234
ABZ6 (10 10) 943 944 943 943
ABZ7 (15 20) 665 680 667 656
In the tests, ABZ7 GTD-GA algorithm gives better results than GLS algorithm [10].
The comparing test results may indicate that the method we propose has the
following advantages:
1. The organization using the 2 matrices L_T and F_T reduces the numbers
of search operations.
2. When we use a mutation associated with GT algorithms, it searches nearby
so quickly and find a better value mutation father and minimize the number of
calculations.
3. Our first children are 4 instead of getting only one child by the same
parents and with the same number of operators.
Our designed program is tested on a standard data of Muth and Thompson and gives
better results than the latest algorithm GA. However, for problems with large-size
test ABZ7 (15 20), the program has to find the optimal schedule. In the future we
will continue to develop out new methods with higher efficiency.
REFERENCES
[1] Adams, J., Balas, E. and Zawack, D., 1988. The Shifting Bottleneck Procedure for Job Shop
Scheduling, Management Science, Vol. 34, No. 3, pp. 391–401.](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-25-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 24
[2] Akers, S.B., 1956. A graphical approach to production scheduling problems, Operations
Research, Vol. 4, No. 2, pp. 244-245.
[3] Akers, S.B. and Friedman, J., 1955. A non-numerical approach to production scheduling
problems, Operations Research, Vol. 3, No. 4, pp. 429-442.
[4] Brooks, G. H. and White, C. R., 1969. An algorithm for finding optimal or near optimal solutions
to the production scheduling problem, The Journal of Industrial Engineering, Vol. 16, No. 1, pp. 34-
40.
[5] Brucker, P., 1994. A polynomial time algorithm for the two machines Job Shop scheduling
problem with a fixed number of jobs, OR Spektrum, Vol. 16, No. 1, pp. 5-7.
[6] Carlier, J. and Pinson, E., 1989. An algorithm for solving the job-shop problem, Management
Science, Vol. 35, No. 2, pp. 164-176.
[7] Fischer, C. and Thompson, G. L., 1963. Probabilistic learning combinations of local job-shop
scheduling rules, In Industrial Scheduling, Prentice Hall, Englewood Cliffs, New Jersey, pp. 225-251.
[8] Günter Rudolph, 1994. Convergence Analysis of Canonical Genetic Algorithms, IEEE
Transactions on Neural Networks, special issue on evolutionary computation, Vol. 5, No. 1, pp. 96-
101.
[9] Holland, J. H., 1975. Adaptation in Natural and Artificial Systems, University of Michigan Press.
[10] Kebabla, M. and Mouss, L. H., 2012. A local search genetic algorithm for the job shop
scheduling problem, Revue des Sciences et de la Technologie – RST, Vol. 3, No. 1, pp. 61-68.
[11] Kravchenko, S. A. and Sotskov, Y. N., 1996. Optimal makespan schedule for three jobs on two
machines, ZOR - Mathematical Methods of Operations Research, Vol. 43, pp. 233-238.
[12] Muth, J. F. and Thompson, G. L., 1963. Solving Production Scheduling Problems, In Industrial
Scheduling, Prentice Hall, Englewood Cliffs, New Jersey, Ch. 3.
[13] Nakano, R. and Yamada, T., 1991. Conventional genetic algorithm for job shop problems, In
Proceedings of International Conference on Genetic Algorithms (ICGA ’91), pp. 474-479.
[14] Nguyễn Hữu Mùi and Vũ Đình Hoà, 2011. Một thuật toán di truyền lai mới cho bài toán lập
lịch công việc, Kỷ yếu hội nghị khoa học công nghệ quốc gia lần thứ V, pp. 239-249.
[15] Sotskov, Y.N. and Shaklevich, N. V., 1995. NP-hardness of shop-scheduling problems with three
jobs, Discrete Applied Mathematics, Vol. 59, No. 3, pp. 237-266.
[16] Yamada, T., 2003. Studies on Metaheuristics for Jobshop and Flowshop Scheduling Problems,
Japan: Kyoto University, pp. 42-70.
This paper may be cited:
Hanh, D. T., Hoa, V. D. and Mui, N. H. 2014. Dual Hybrid Algorithm for Job Shop
Scheduling Problem. International Journal of Computer Science and Business
Informatics, Vol. 14, No. 3, pp. 14-24.](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-26-320.jpg)

![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 26
reduced to in proportionate to the other model parameters. The
advancements of the portable electronic devices and high compaction of
VLSI circuits, power dissipation give the major challenge to the designers.
And also at the same time due to the advancements of the technological
practice the increase of the leakage current is increasing due to the scale
down of the supply voltage and also the threshold voltage.
In the deep submicron (DSM) regions, the reduction of dynamic power can
be done with the reduction of supply voltages which in turn plays the
important role for the reliability issues by using the advancements of the
technology. The designer has to concentrate more about circuit performance
as the reduction of supply voltages leads altering circuit’s performance. And
the mathematical notation for the subthreshold current can be denoted as
follows.
Tthgs V/)VV(
leakage eII
0
(1)
The subthreshold leakage current Ileak in sleep mode will be determined by
the sleep transistor and is expressed as follows.
)e(eVe)L/W(CI T
ds
T
tHgs
V
V
V
VV
T
.
sleepoxnleak
1281
(2)
Where μn is the N-mobility, Cox is the oxide capacitance, VtH is the high-
threshold voltage (= 500 mV), VT is the thermal voltage = 26 mV, and n is
the subthreshold swing parameter. The reduction of leakage power has
achieved in the standby mode with the proposed methods [1]-[10]. By
varying the substrate bias voltage the threshold voltage can be controlled
which can be observed in Variable Threshold CMOS (VTCMOS) design.
The main advantage in this technique is low threshold voltage for all the
transistors used for design. And it has the two different controlling aspects
which are firstly, the delay variations can be minimized which cause
compensations for fluctuations and secondly, reduction of the leakage
current in the standby mode. These are the two things which need to be
concentrating while implementing this design. Even though these two are
crucial and plays the major advantages for design aspect but it has two
disadvantages which cause the circuit reliability in dilemma. those are can
be observed from its mathematical expression which is as leakage current is
proportional to square root of the substrate voltage the resultant value would
be about large change of effective values and final drawback is it require a
triple-well structure and charge pump circuit for producing substrate voltage
in the VTCMOS. These are the phenomenal causes for the VTCMOS circuit
design.](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-28-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 27
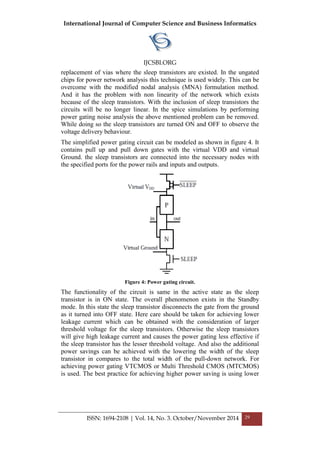
And in contrast to the VTCMOS [4] technique, Multi voltage CMOS
(MVCMOS) has LVT transistors where PMOS gates larger sleep mode
voltages when compare to the NMOS gates which is different in the
VTCMOS design. To reduce the drawbacks caused by these techniques
virtual ground method has taken and by applying the clustering of the LVT
transistors for reduction of the dynamic power and leakage power of the
circuit which in turn reduce the leakage power of the sleep transistors has
achieved. And the logic block diagram of the nMOS sleep transistor can be
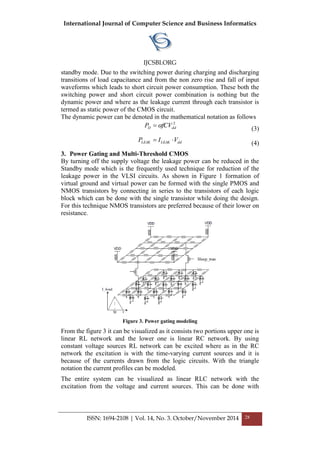
shown with the virtual ground and threshold voltage ranges in the Figure1.
Figure 1. Logic block with an nMOS sleep transistor [6].
2. Leakage Reduction Techniques
Figure 2. Charging of the zero output nodes with a pMOS pull-up.
The total power consumption can be computed in a CMOS circuit as the
sum of dynamic power and the static power in the active mode operation.
And due to the standby leakage current the power will be dissipated in the](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-29-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 31
4. Leakage Control In Active Mode
Figure 7. Proposed design methodology.
By using the techniques which were discussed earlier the domination of the
leakage power compare to the overall power consumption of the circuit in
Standby mode can be reduced. if that is not the case and the leakage power
is minimum when compare to the overall power consumption the total
power consumption is needs to taken into account where the combination of
switching power dissipation and active mode leakage has to consider and
thereby optimization of circuit is to be considered. And it can be achieved
by considering the following techniques.
Multiple Threshold Cells
Long Channel Devices
Minimum Leakage Vector Method
Stack Effect-based Method
Sizing with Simultaneous Threshold and Supply Voltage
Assignment
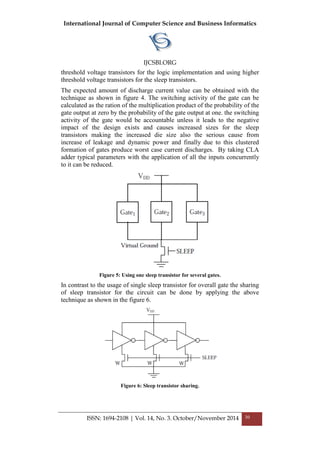
The proposed clustering algorithm [8] used the approach of constrained
minimization in which for the given timing constraints single cost function
has taken. The iterative row selection scheme has used in the clustering
algorithm. In the iterative row selection process all rows are selected in the
initial stage and are marked as gated rows. in the next step the second row is
taken and rows are progressively eliminated based on the given timing
constraints until it reach the maximal set of rows where the leakage cost
function can be minimized. The output of a gate is represented in the form
of vectors for the discharging currents for the convenience of vector
comparisons. And the same can be evaluated from the flow chart of the
figure 8.](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-33-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 32
Figure 8: Clustering algorithm.
The proposed scheme [9] can be easily implemented to cope with the single
set of sleep transistors. the load dependent delay di can be denoted
mathematically as follows.
)VV(
VC
d
tLdd
ddLi
(5)
And from the above equation the mathematical terms can be defined as the
load capacitance for the CL and low voltage threshold is about 350 mV for
the VtL and supply voltage Vdd is 1.8 V and α as the velocity saturation
index and which is about 1.3 for the 180nm CMOS technology.
The propagation delay of a gate in presence of the sleep transistor can be
expressed as
)VVV(
VKC
d
tLxdd
ddLi
sleep
2 (6)
And from the above equation the internal terminology is about Vx is for the
virtual rails, K is the proportionality constant. And from the above equation
the internal terminology is about Vx is for the virtual rails, K is the
proportionality constant. The logic gates operates at the virtual supply rails
about the magnitude of Vx from the supply rails on either side but not
operates at the true supply rails (Vdd) in the active mode. From this can
conclude that the effective supply voltage is Vdd-2Vx for the gate.
If the ON current of the sleep transistor in the active mode is IsleepON the
sleep transistor will be in the linear region of operation. And by using the
basic device equations the drain to source current of the sleep transistor in](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-34-320.jpg)

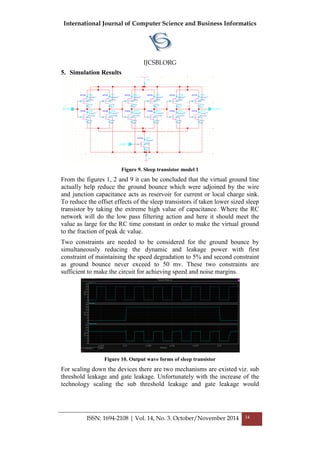
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 35
increase rapidly. Decaps made up of gate oxide MOS transistors with the
long wide channels are used for getting the large capacitance.
Figure 11. Sleep transistor model 2
Due to the continuous switching of the core logic and I/O buffers power grid
noise will exist and this power gating noise is because of the switching
action on and off of the sleep transistors.
From the above analysis the discharge current can be expected. Based on the
multiplication value of the probability of the gate will be at zero to the
probability of the gate will be at one gives the switching activity of the gate.
6. CONCLUSIONS
The clustered sleep transistors leakage power reduction techniques has
analyzed and discussed various advantages and improvements need to take
for the advancements of the sleep transistors for achieving the higher power
saving and for using maximum die area with the consideration of the
various algorithms proposed by the different designers which are
considering as the standard designs. And all are designed and tested with
180 nm technology by using the spice simulation. And the research has to
be done on the power scaling of the sleep transistors in the standby mode for
the better performance.
7. ACKNOWLEDGMENTS
The authors would like to thank anonymous reviewers for their valuable
inputs.
REFERENCES
[1] Sathanur, Ashoka, et al. Row-based power-gating: a novel sleep transistor insertion
methodology for leakage power optimization in nanometer cmos circuits. IEEE
Transactions on Very Large Scale Integration (VLSI) Systems, Vol. 19, No. 3, 2011,
pp. 469-482.](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-37-320.jpg)
![International Journal of Computer Science and Business Informatics
IJCSBI.ORG
ISSN: 1694-2108 | Vol. 14, No. 3. October/November 2014 36
[2] Homayoun, Houman, et al. MZZ-HVS: multiple sleep modes zig-zag horizontal and
vertical sleep transistor sharing to reduce leakage power in on-chip SRAM peripheral
circuits. IEEE Transactions on Very Large Scale Integration (VLSI) Systems, Vol. 19,
No. 12, 2011, pp. 2303-2316.
[3] V. Khandelwal and A. Srivastava. Leakage control through fine-grained placement
and sizing of sleep transistors. In Proc. IEEE/ACM Int. Conf. CAD (ICCAD), San
Jose, CA, Nov. 2004, pp. 533–536.
[4] J. Kao, A. Chandrakasan, and S. Narendra. MTCMOS hierarchical sizing based on
mutual exclusive discharge patterns. In Proc. ACM/ IEEE Des. Autom. Conf. (DAC),
San Francisco, CA, Jun. 1998, pp. 495–500.
[5] S. Mutoh, S. Shigematsu, Y. Matsuya, H. Fukuda, and T. Kaneko. 1-V power supply
high-speed digital circuit technology with multithreshold voltage CMOS. J. Solid-State
Circuits, vol. 30, no. 8, pp. 847–854, Aug. 1995.
[6] K. Roy, S. Mukhopadhyay, and H. Mahmoodi-Meimand. Leakage current mechanisms
and leakage reduction techniques in deep-submicrometer CMOScircuits. Proc. IEEE,
vol. 91, no. 2, pp. 305–327, Feb. 2003.
[7] M. Keating, D. Flynn, R. Aitken, A. Gibbons, and K. Shi. Low Power Methodology
Manual: For System-on-Chip Design. New York: Springer, 2007.
[8] H. Jiang, M. Marek-Sadowska, and S. R. Nassif. Benefits and costs of power-gating
technique. In Proc. IEEE Int. Conf. Comput. Des.(ICCD), San Jose, CA, Oct. 2005, pp.
559–566.
[9] M. Anis, S. Areibi, and M. Elmasry. Design and optimization of multithreshold CMOS
(MTCMOS) circuits. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst., Vol. 22,
No. 10, pp. 1324–1342, Oct. 2003.
[10]J. Kao, A. Chandrakasan, and D. Antoniadis. Transistor sizing issues and tool for
multi-threshold CMOS technology. In Proc. ACM/IEEE Des. Autom. Conf. (DAC),
Anaheim, CA, Jun. 1997, pp. 409–414.
[11]F. Fallah and M. Pedram. Standby and active leakage current control and minimization
in CMOS VLSI circuits. IEICE Trans. Electron., Vol. E88-C, No. 4, pp. 509–519, Apr.
2005.
This paper may be cited as:
Sree, D., M., Kranthi, K. Y. and Vardhan, V. K., 2014. The Comparative
Analysis of Power Optimization in Clustered Sleep Transistors.
International Journal of Computer Science and Business Informatics, Vol.
14, No. 3, pp. 25-36.](https://image.slidesharecdn.com/vol14no3-november2014-171208072413/85/Vol-14-No-3-November-2014-38-320.jpg)