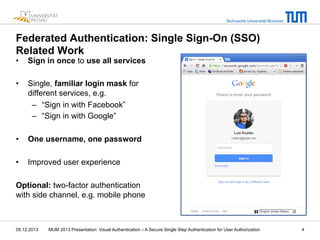
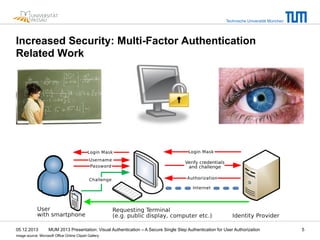
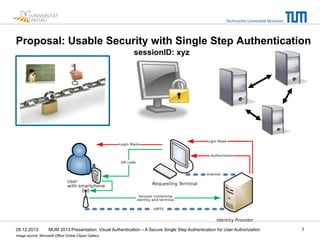
The document presents a secure single-step visual authentication method developed by researchers from Technische Universität München and Universität Passau. It addresses challenges in mobile and user security, proposing an approach that leverages session tokens and smartphones for user authorization at public terminals while enhancing security against common threats like phishing and shoulder surfing. The proposal outlines usability benefits, potential applications such as room reservation systems, and notes open issues requiring further research and evaluation.