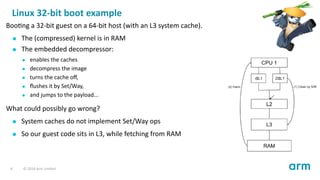
The document presents a comprehensive overview of cache virtualization in ARM architecture, emphasizing its flexibility and the complexities introduced by virtual machines. It discusses operations for cache management, the challenges faced in virtualized environments, particularly with the set/way instructions, and the necessity of cleaning guest memory. The conclusion underscores the integral role of caches in coherency protocols and the importance of following architectural rules for correctness.