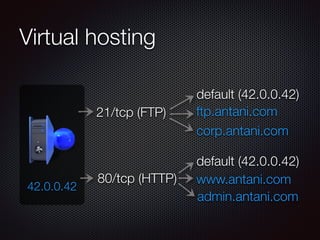
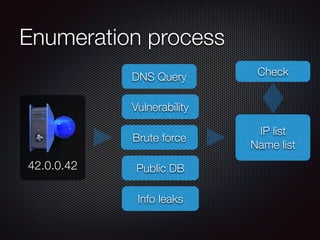
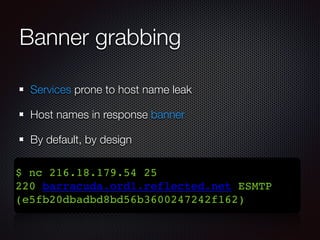
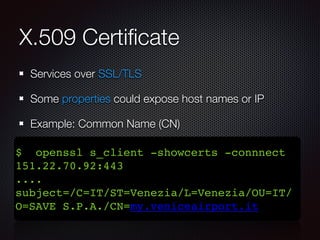
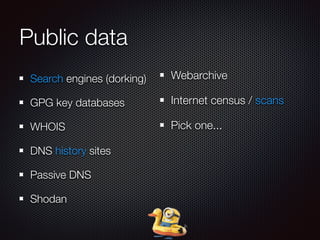
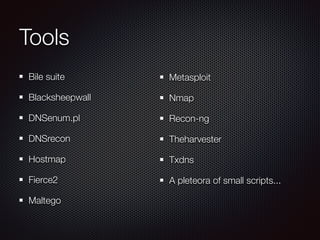
This document discusses techniques for discovering hostnames and virtual hosts through DNS enumeration, service fingerprints, application layers, and passive methods. It lists tools that can be used for reconnaissance like DNSenum, DNSrecon, Maltego, Nmap, and TheHarvester. The document provides examples of hostname discovery through DNS records, SSL certificates, HTTP response banners, redirects, and public data sources.