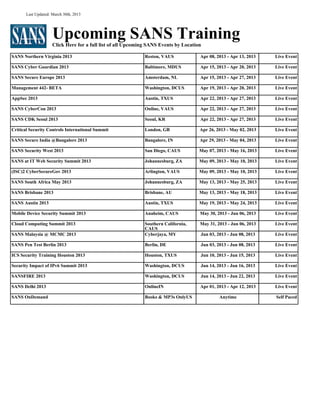
The document discusses evasion techniques that can be used to bypass Intrusion Prevention Systems (IPS). It introduces techniques such as fragmentation, protocol violations, and obfuscation. It then demonstrates how these techniques can be applied to a known attack on the MS08-067 vulnerability in order to evade detection by major IPS vendors, including HP TippingPoint, Check Point, Palo Alto Networks, Cisco, and Fortinet. The goal is to trick the IPS into allowing the malicious traffic through to compromise the target system.