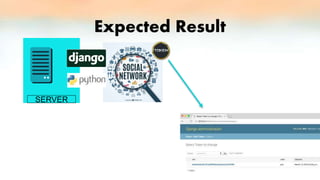
1) The document discusses validation of user credentials in social networks using Django backend authentication. It aims to configure a Django framework platform for authentication, integrate token-based authentication, and test the backend authentication in a social network.
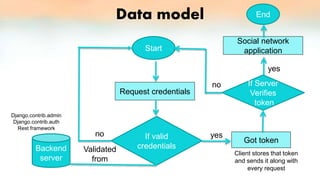
2) The problems with traditional username and password authentication are that it increases server overhead with many users authenticating and credentials can be accessed via HTTP requests. Token-based authentication is proposed to address these issues.
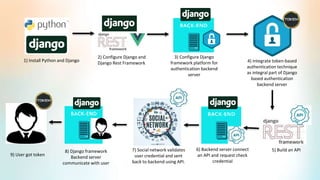
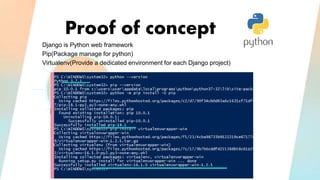
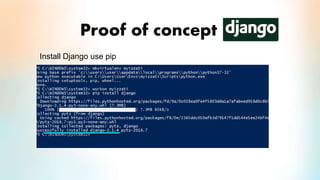
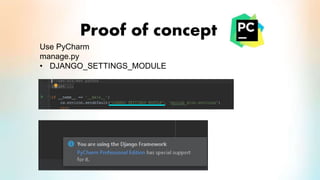
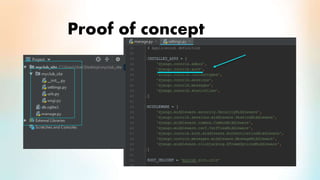
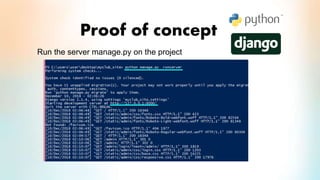
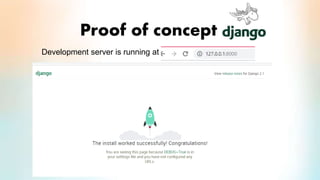
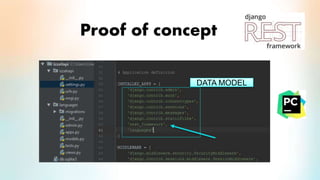
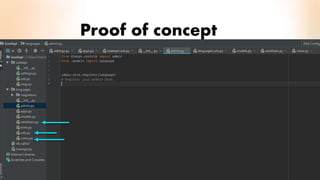
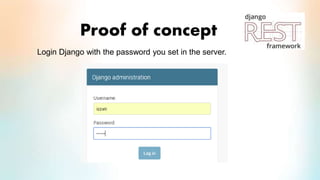
3) The proof of concept implements Django authentication with token-based authentication by installing Django/DRF, configuring the backend server, integrating token authentication, and connecting the backend to an API for social network credential validation.