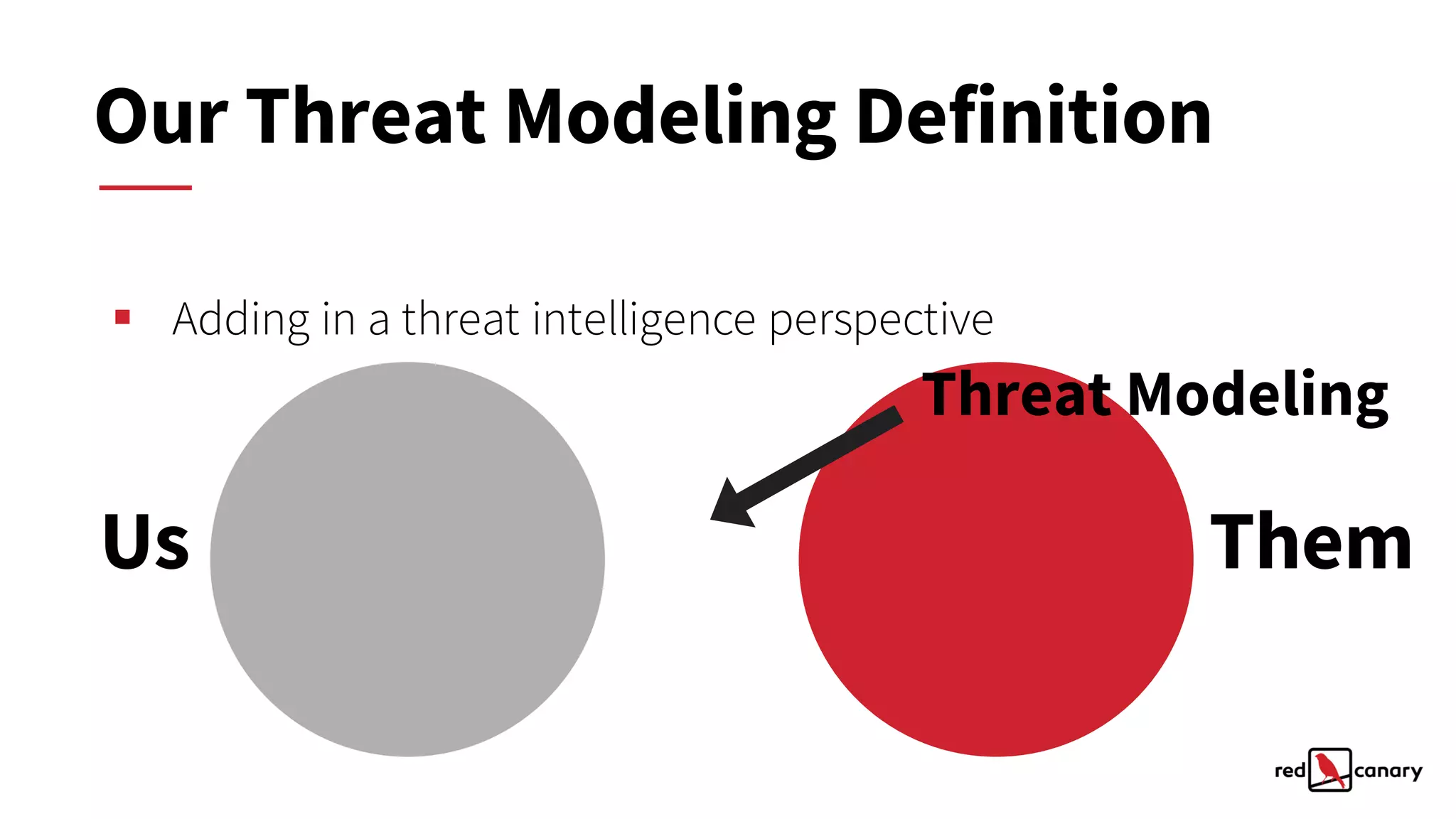
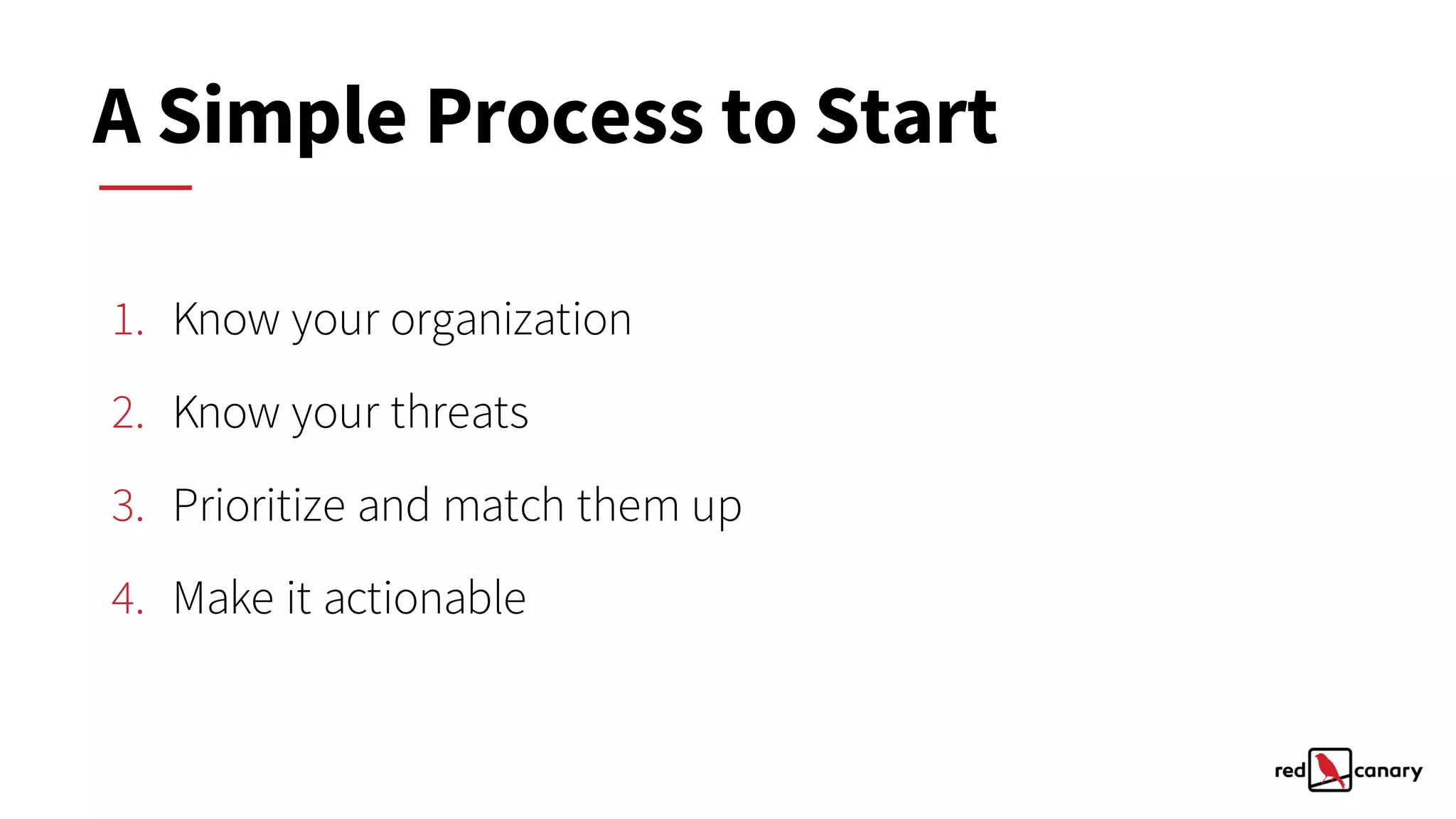
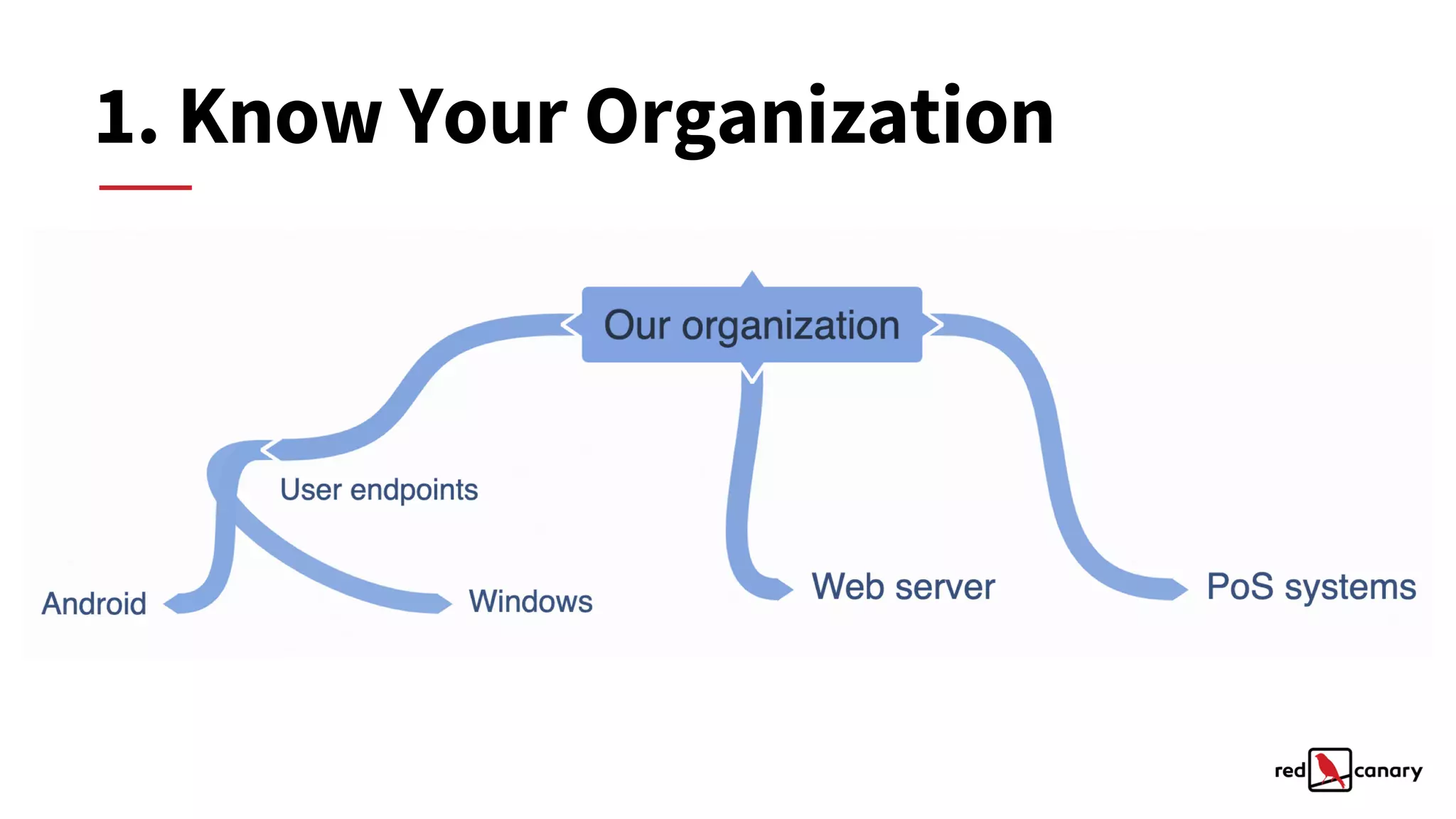
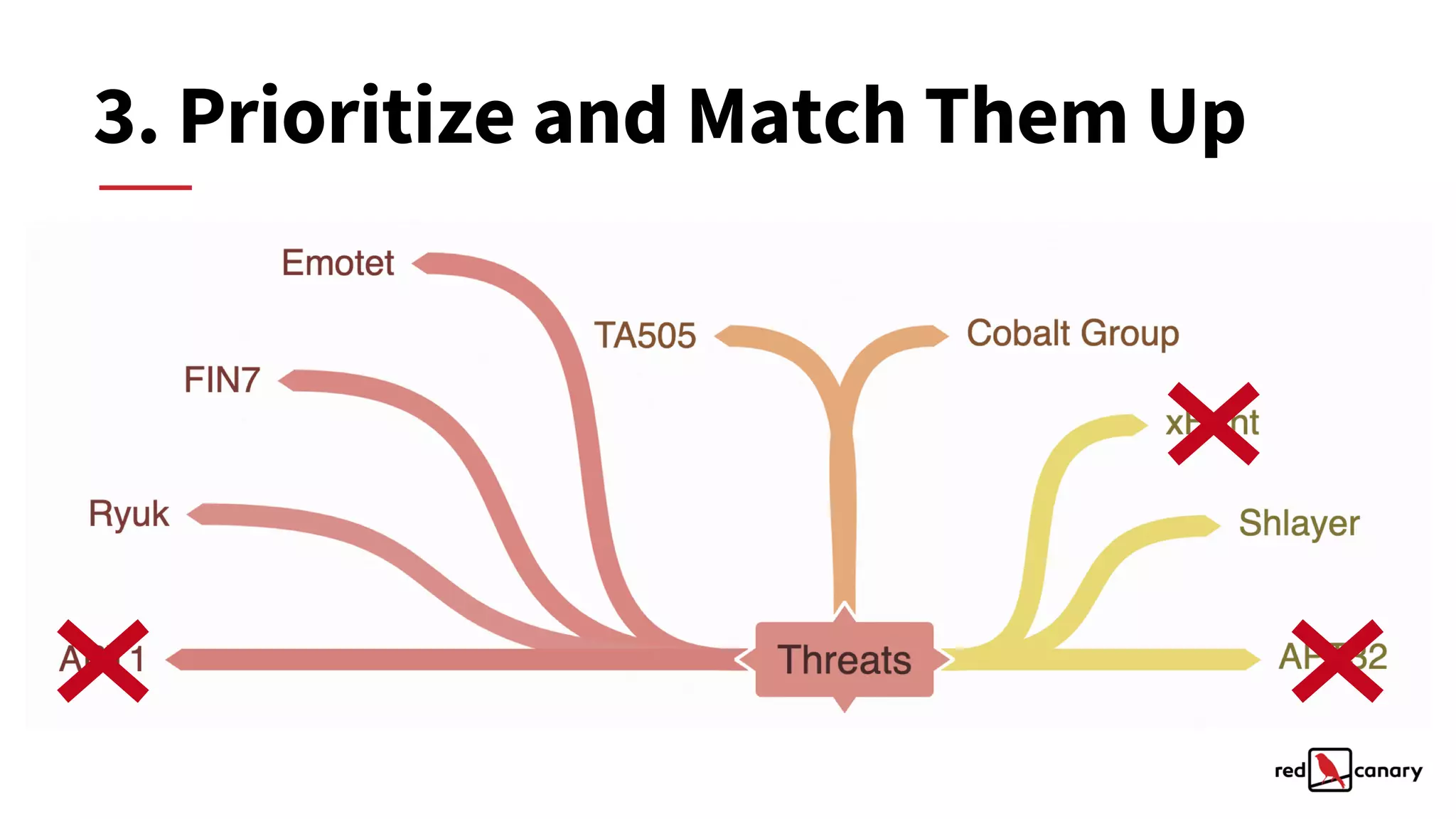
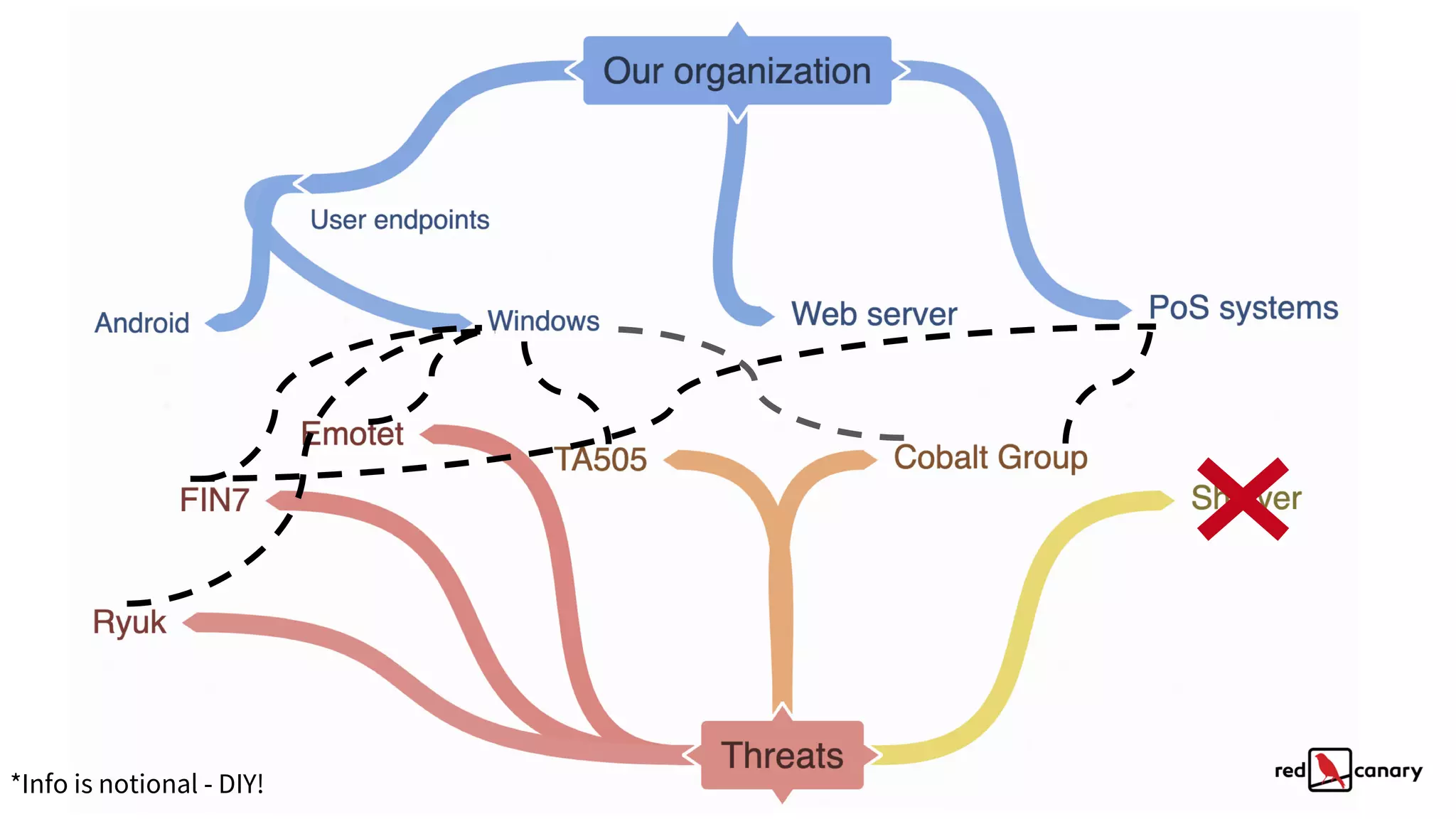
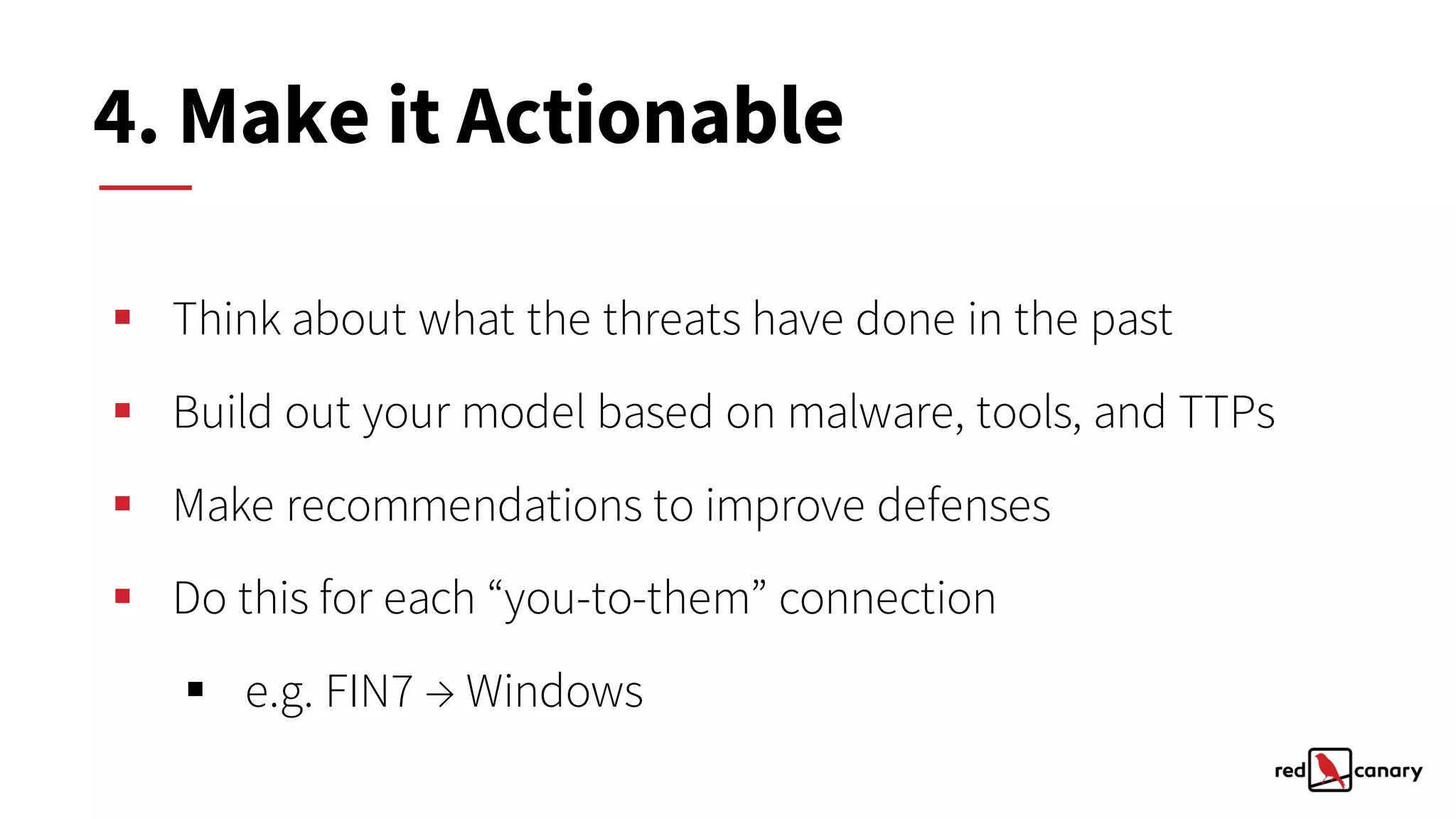
The document discusses a practical approach to threat modeling for prioritizing defenses against cyber threats. It emphasizes the importance of understanding organizational context, identifying relevant threats, and making actionable defenses based on threat intelligence. The process involves defining objectives, analyzing threats, and iterating on model improvements to enhance security outcomes.