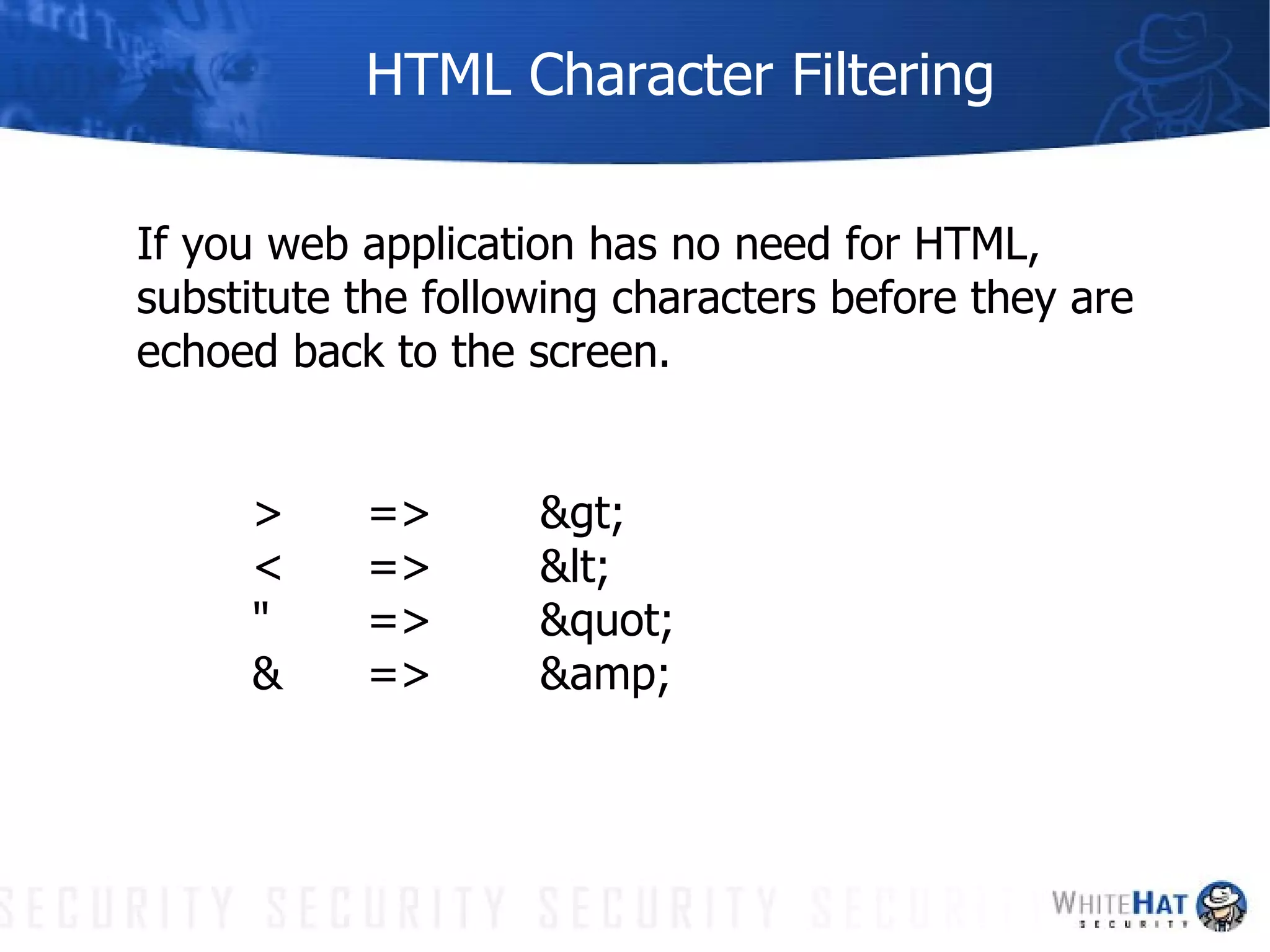
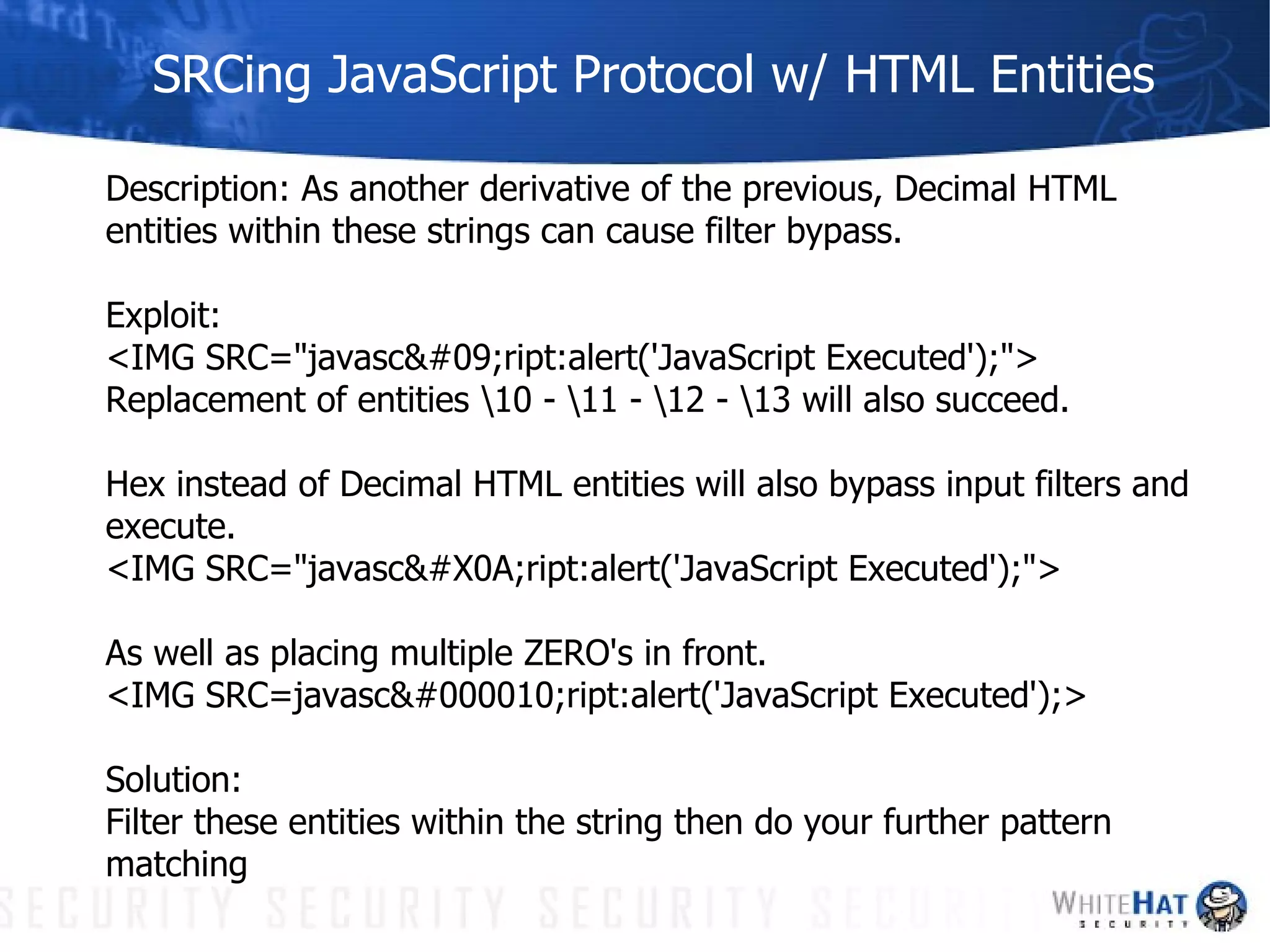
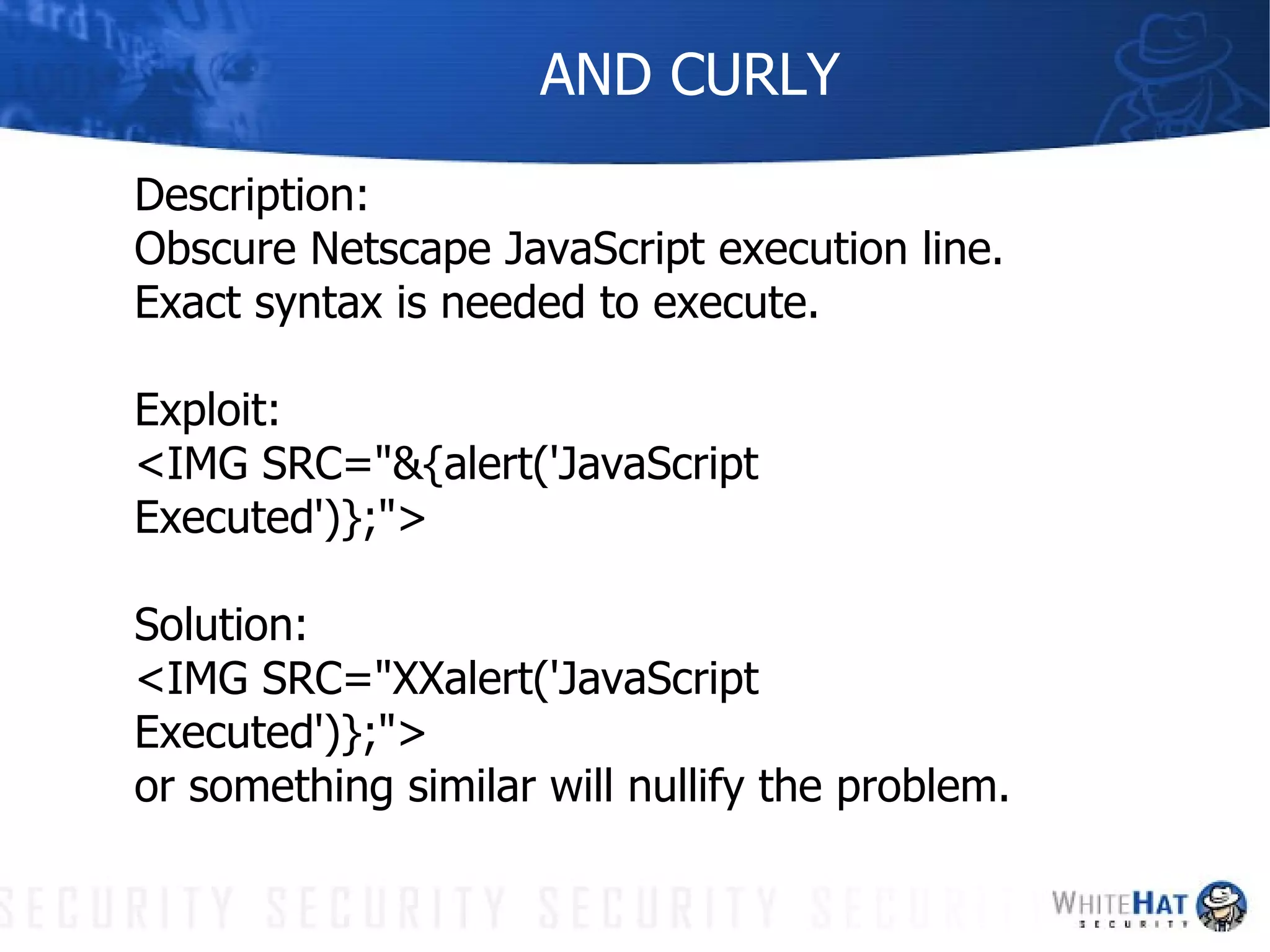
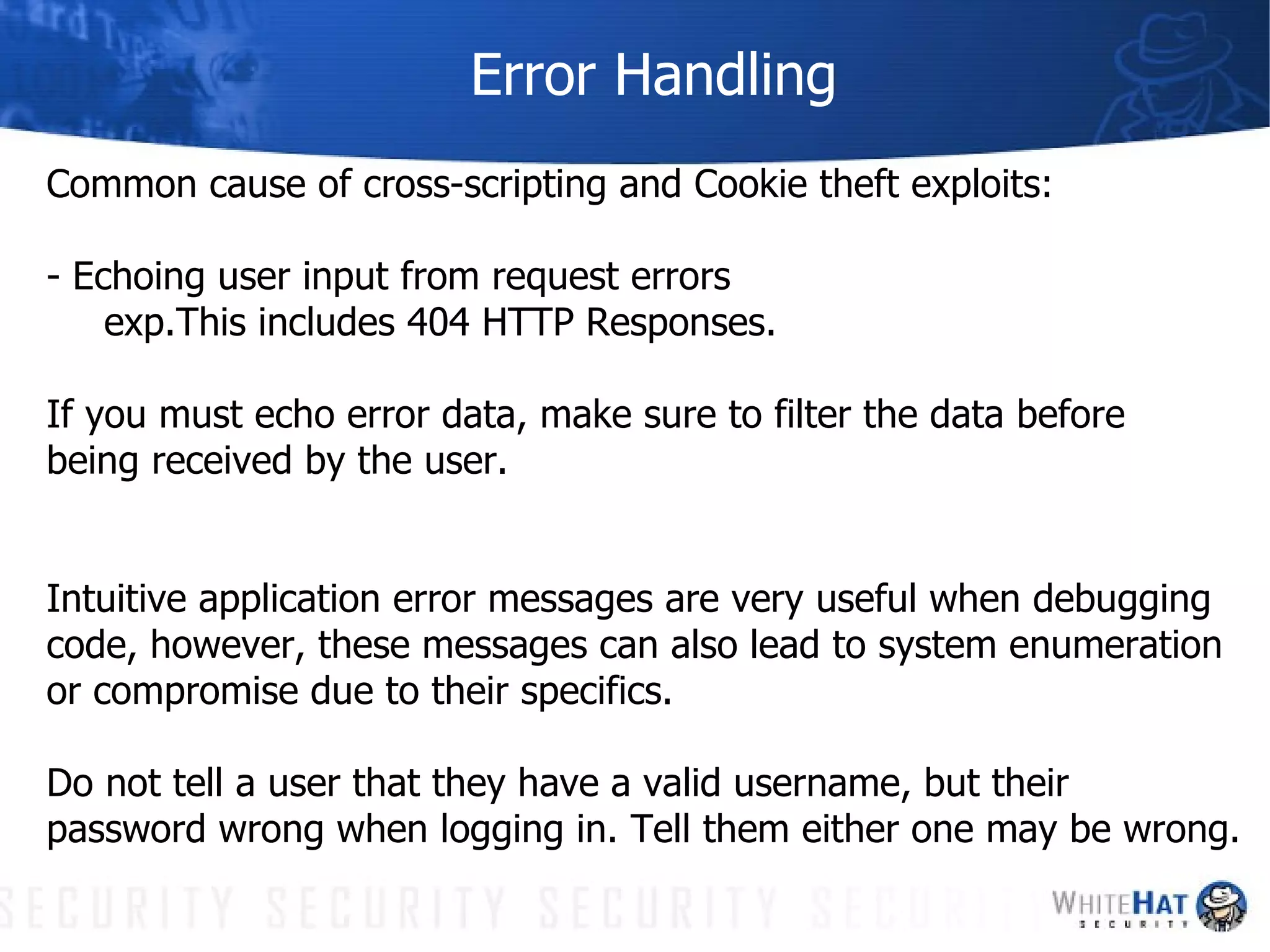
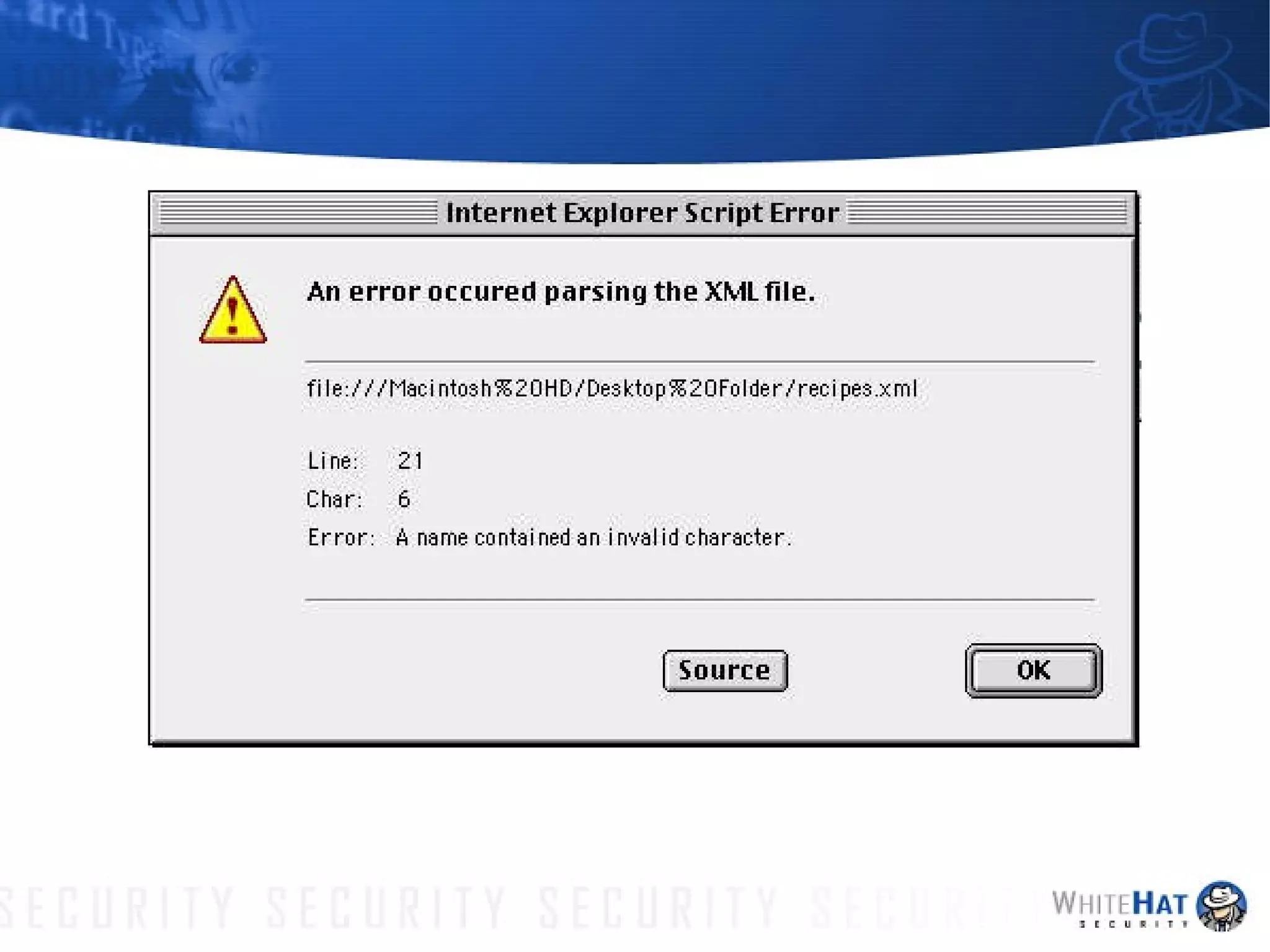
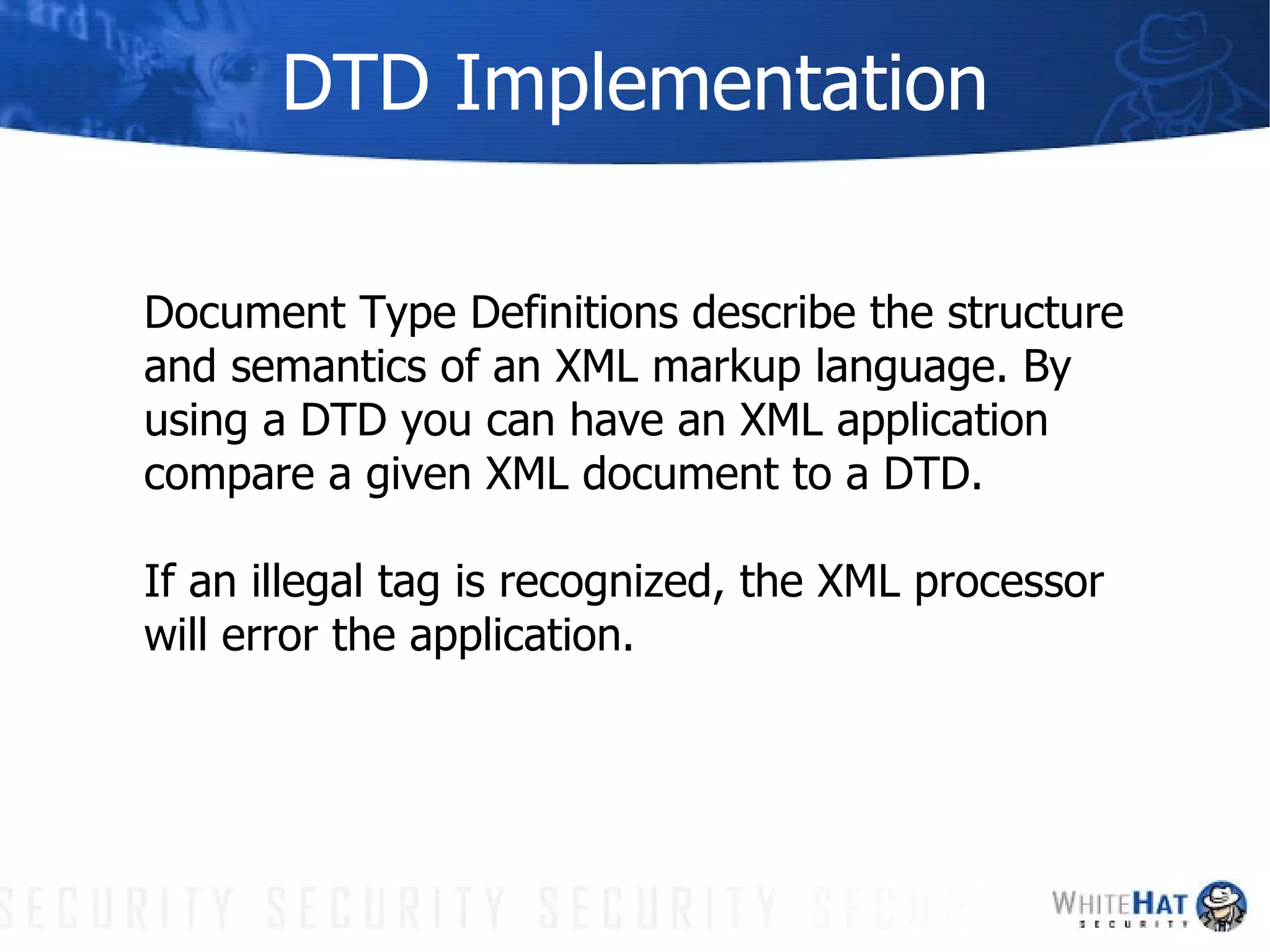
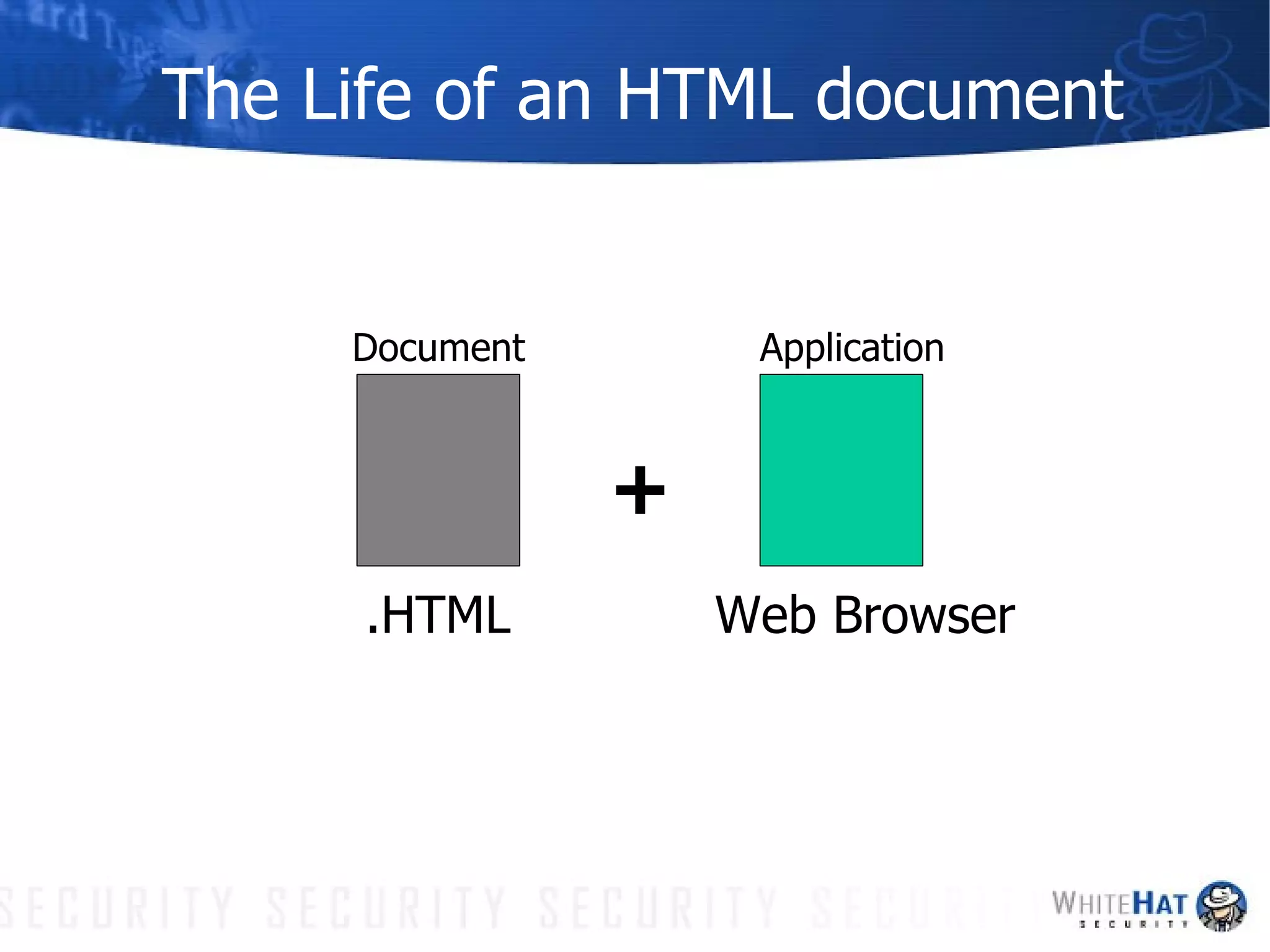
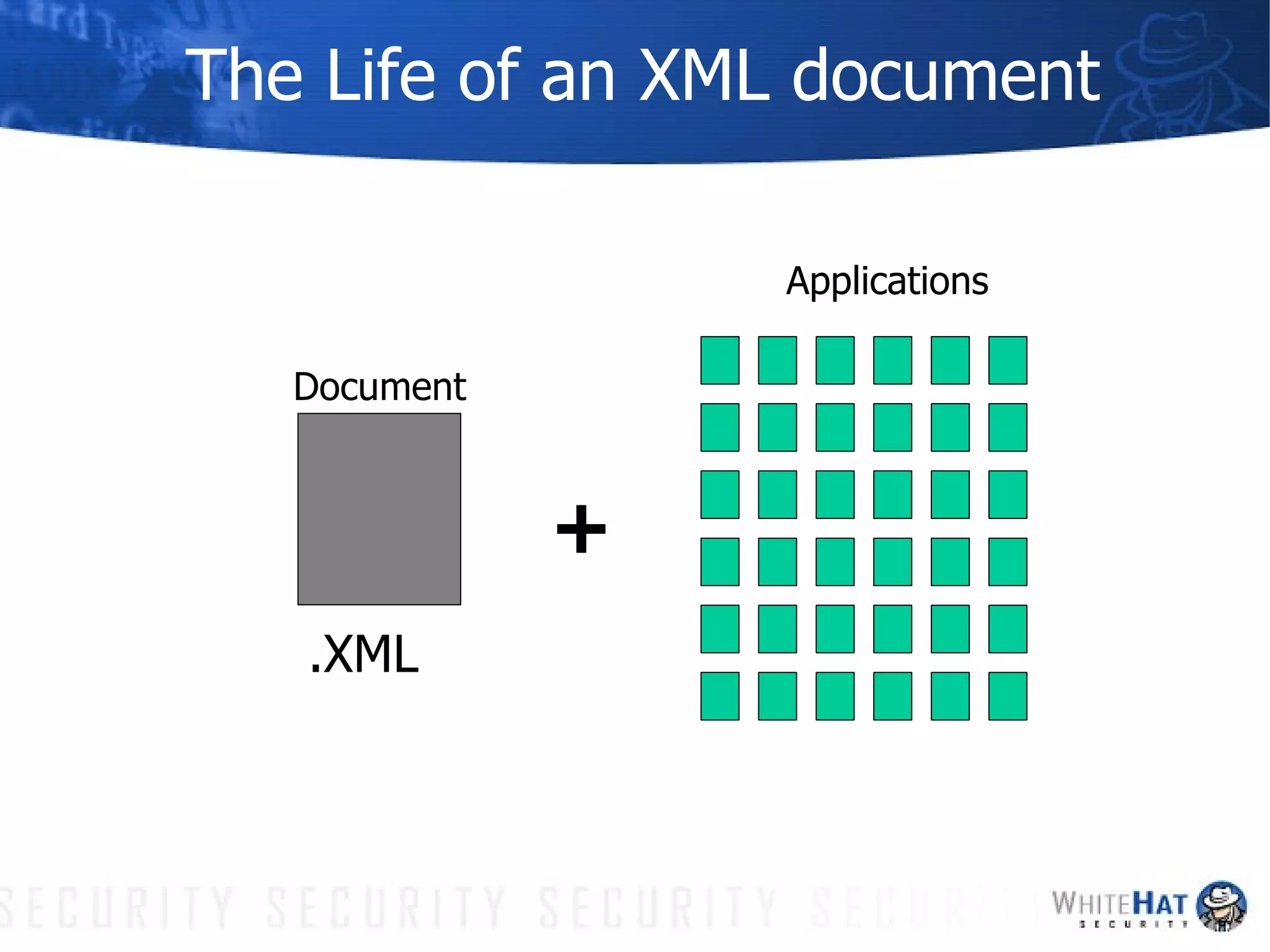
This document summarizes common web application security vulnerabilities and methods for securing web applications. It discusses issues like cookie theft, input validation, cross-site scripting, authentication, and more. The document provides examples of vulnerabilities and recommendations for mitigation strategies to help secure web applications.