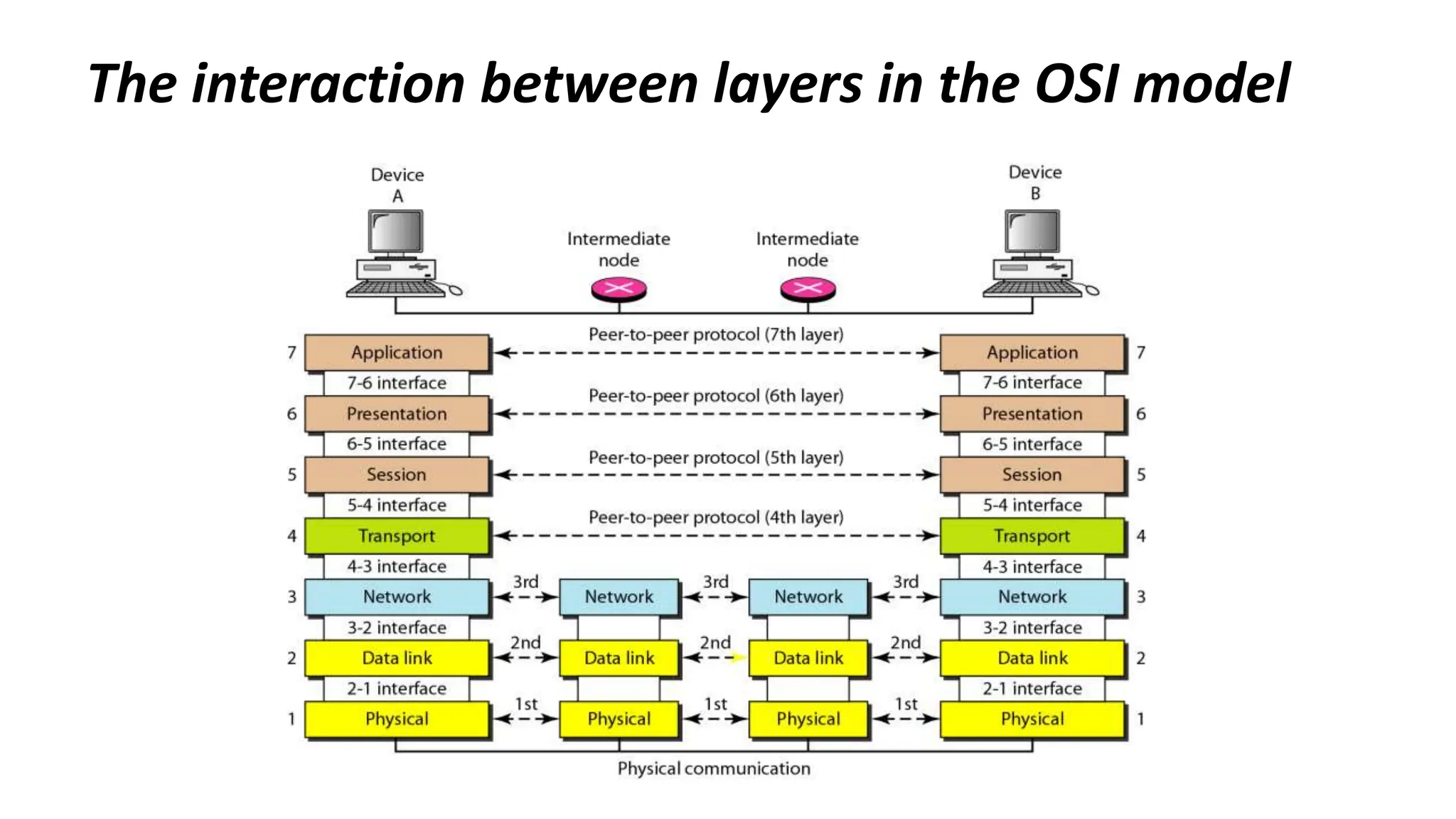
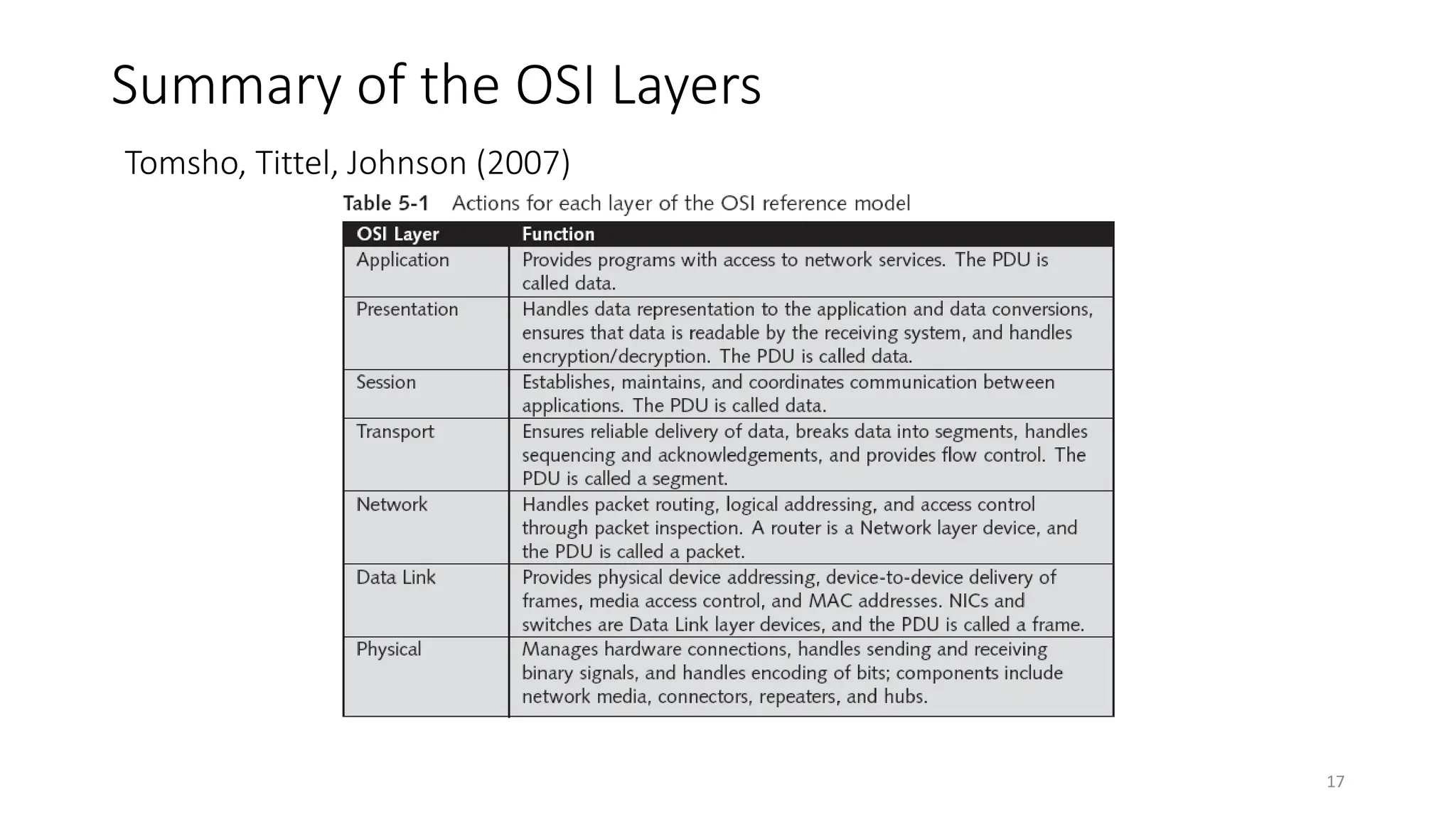
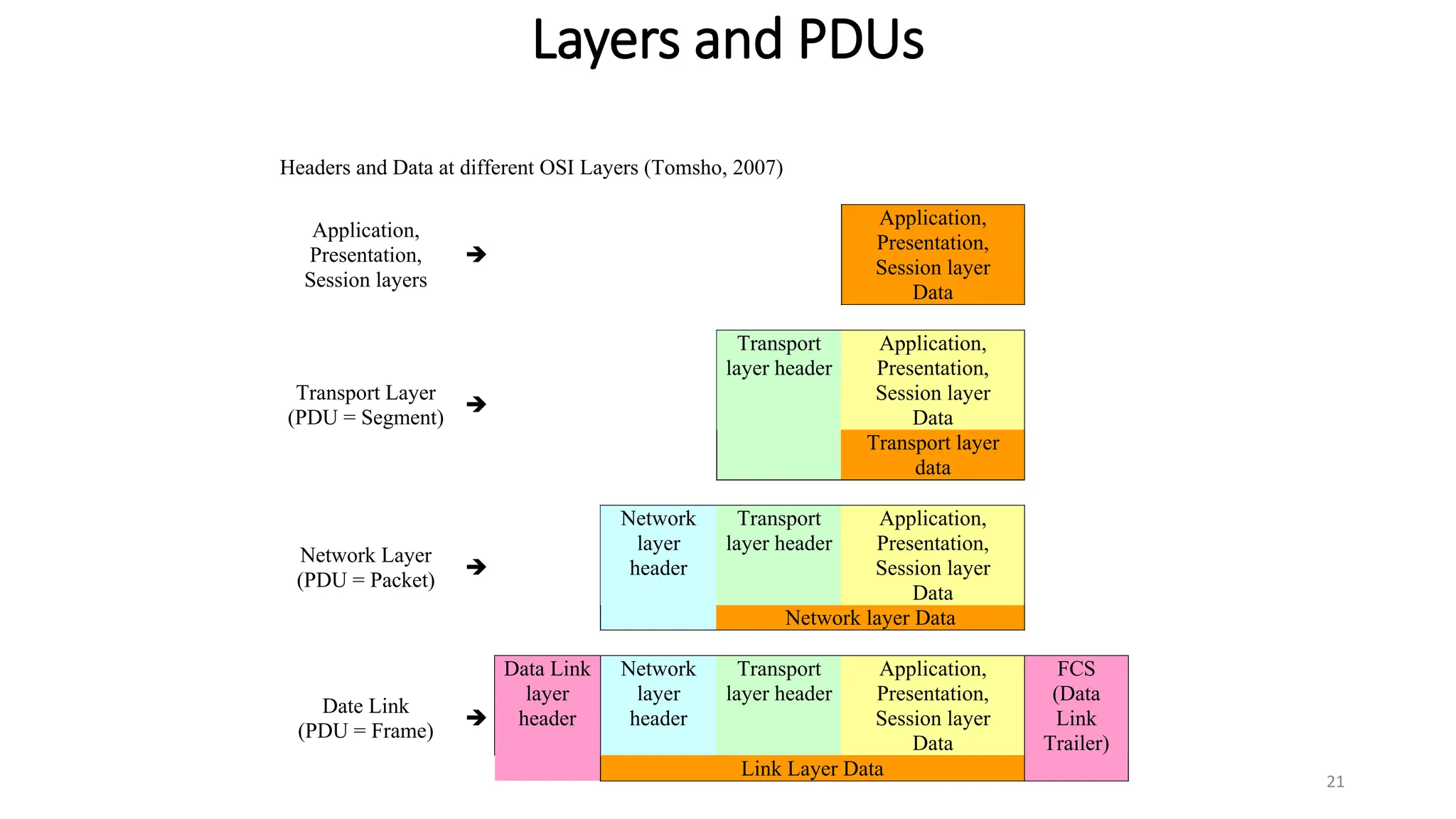
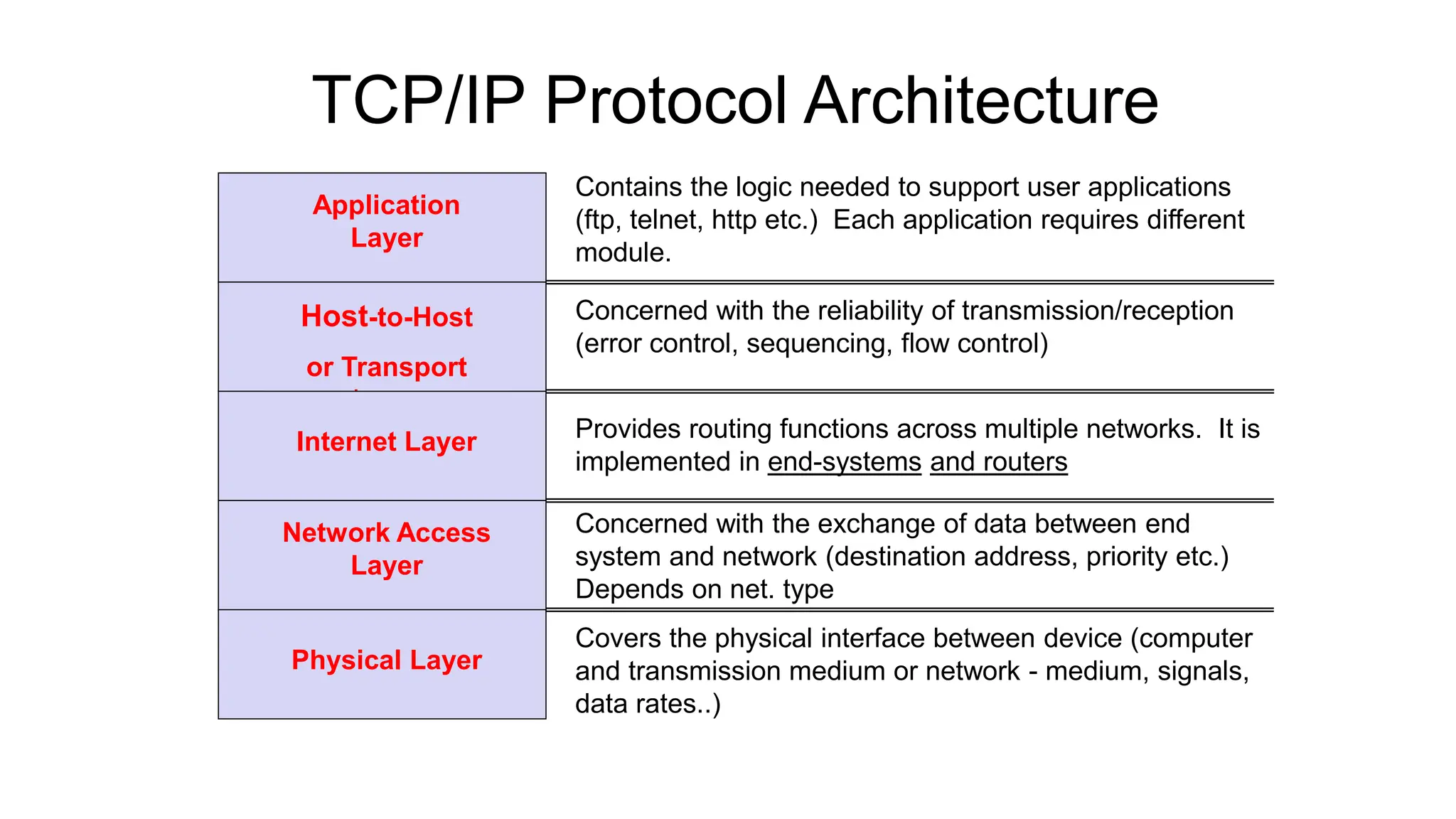
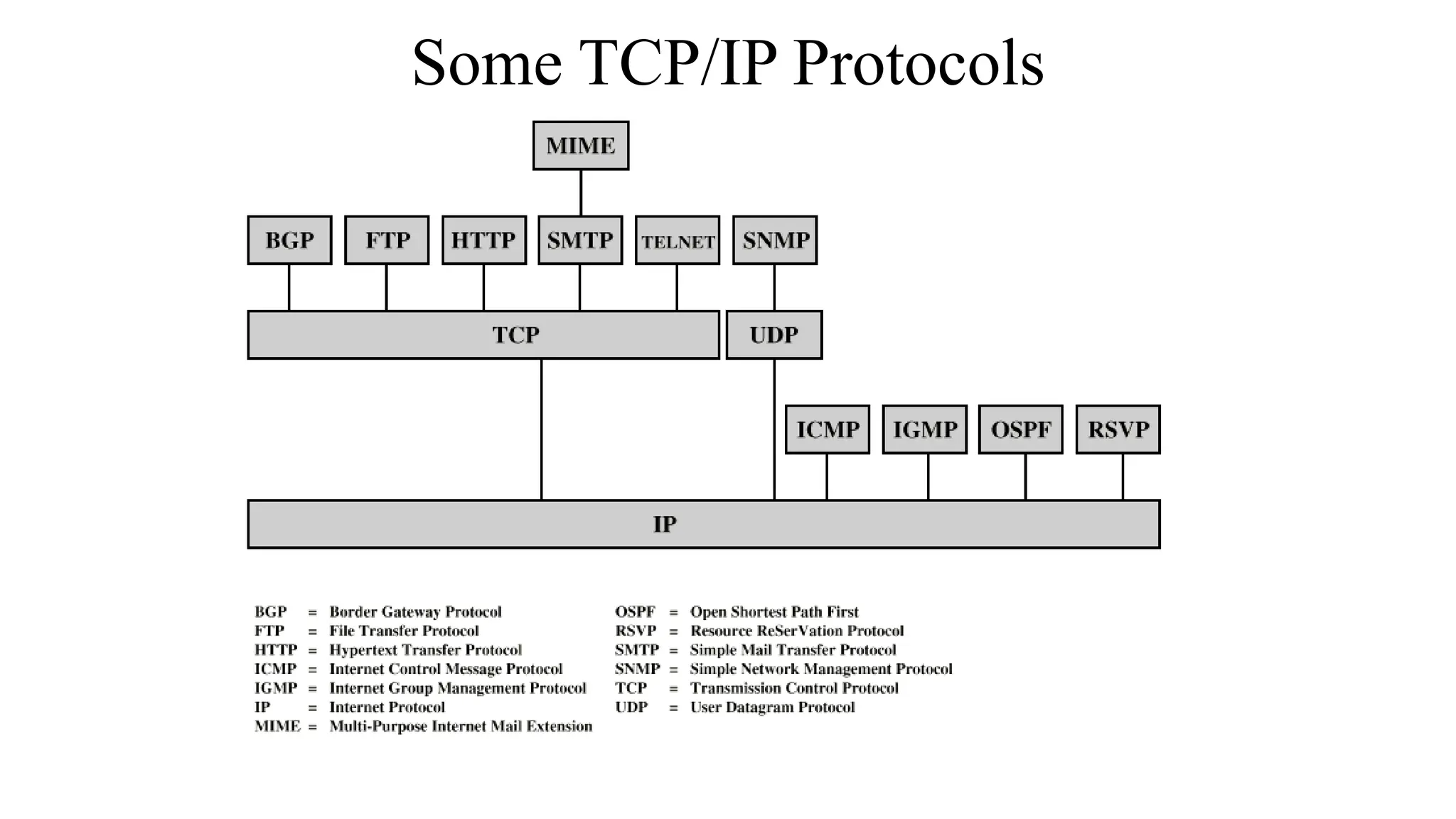
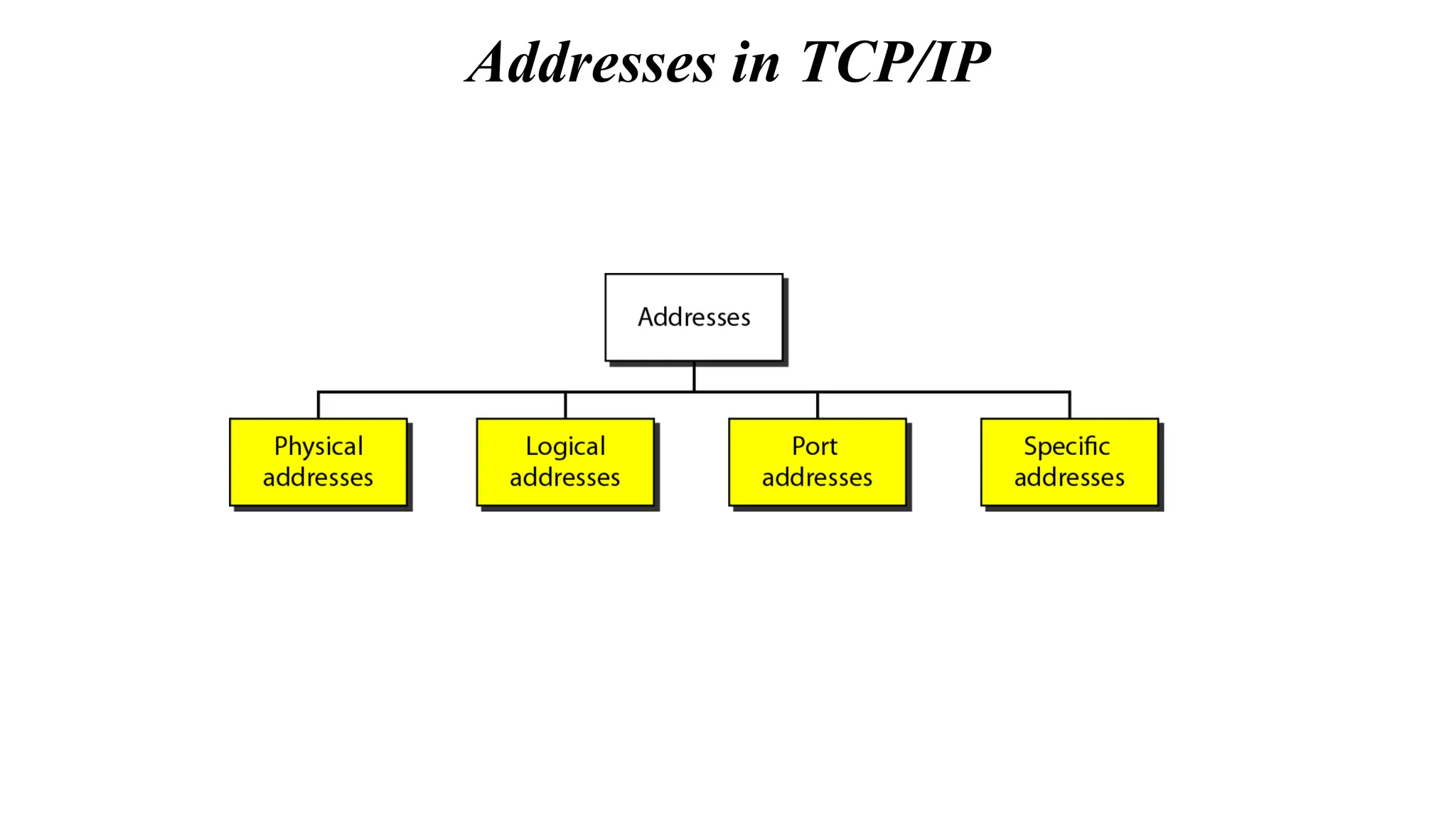
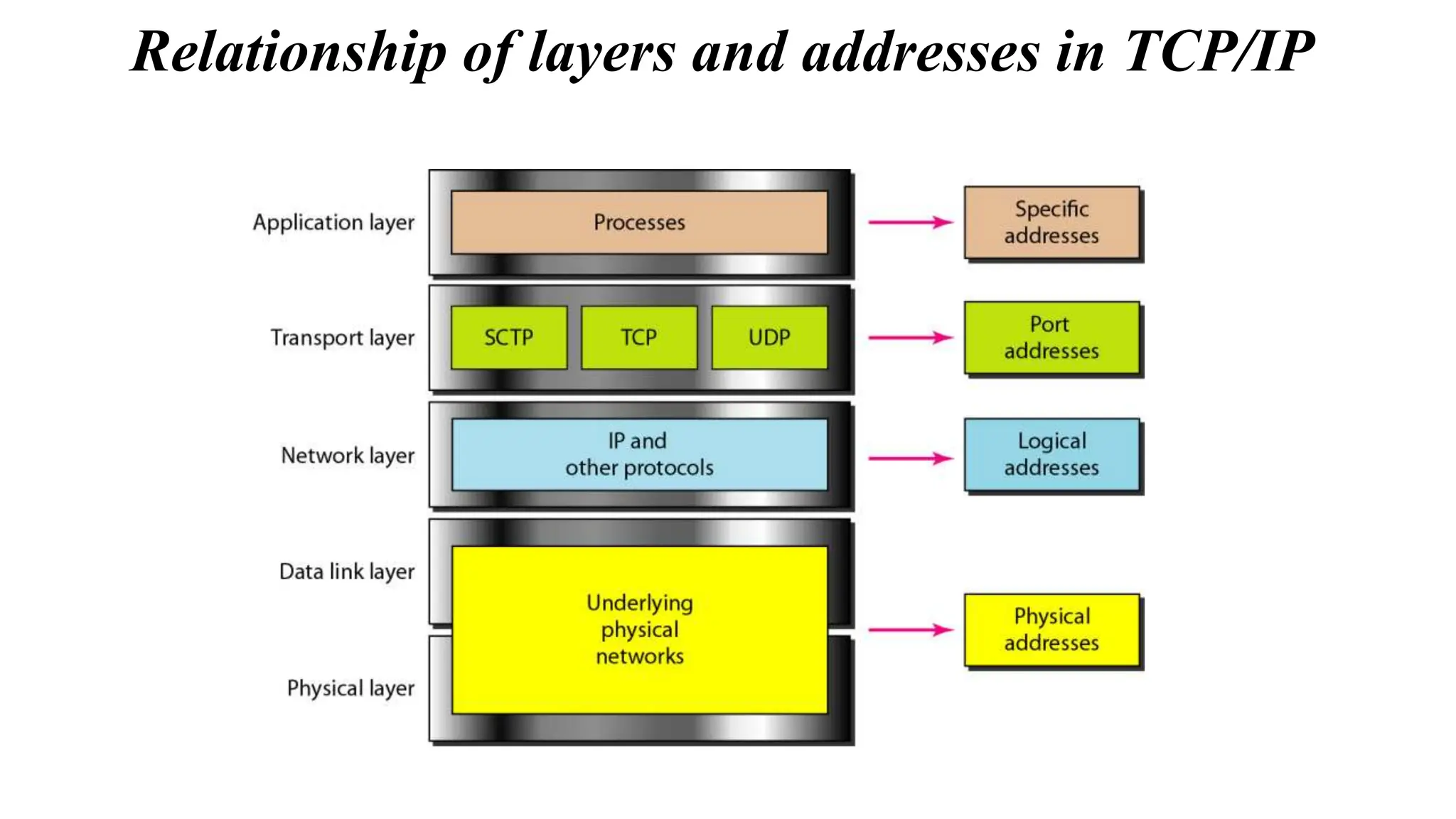
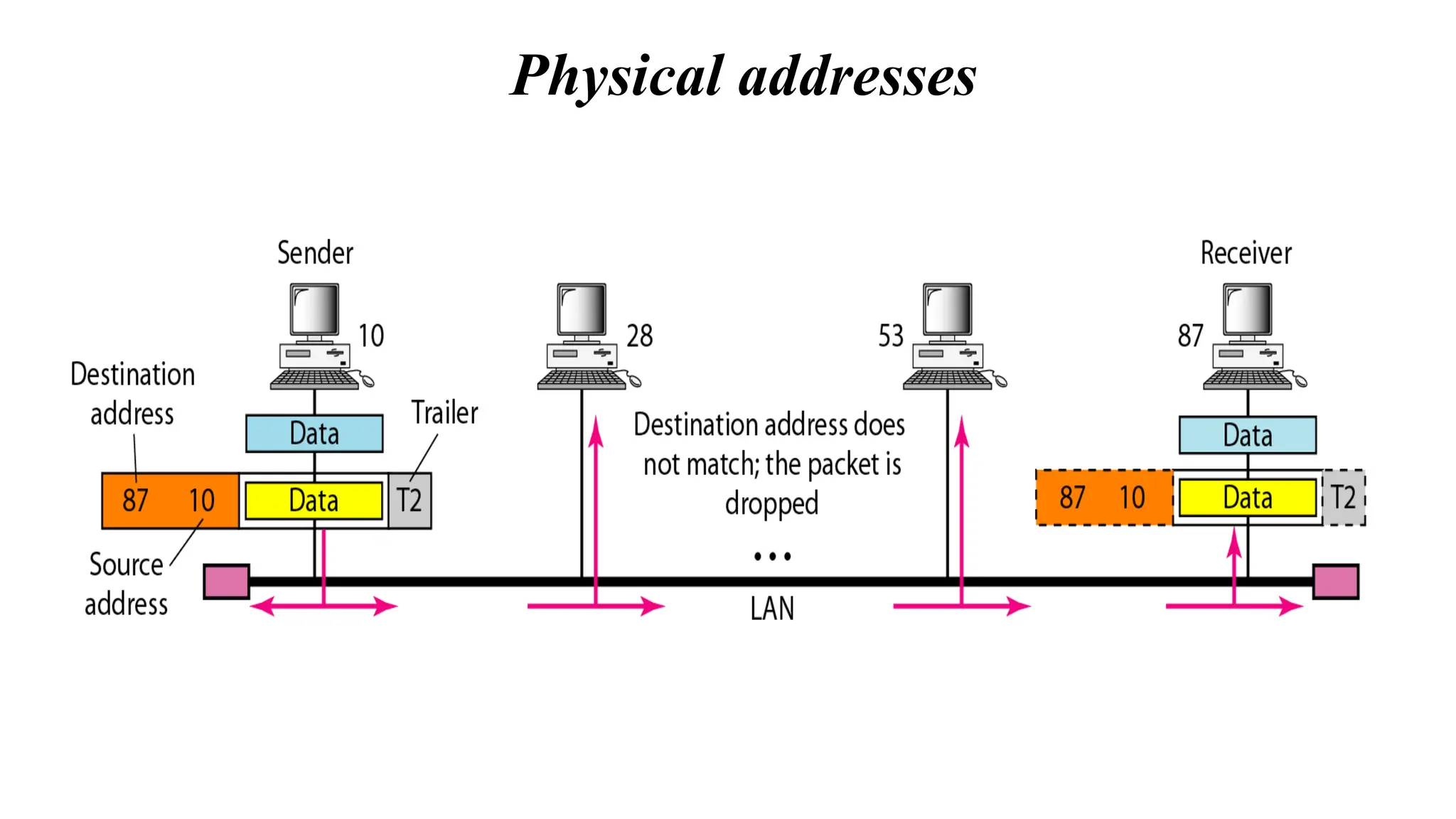
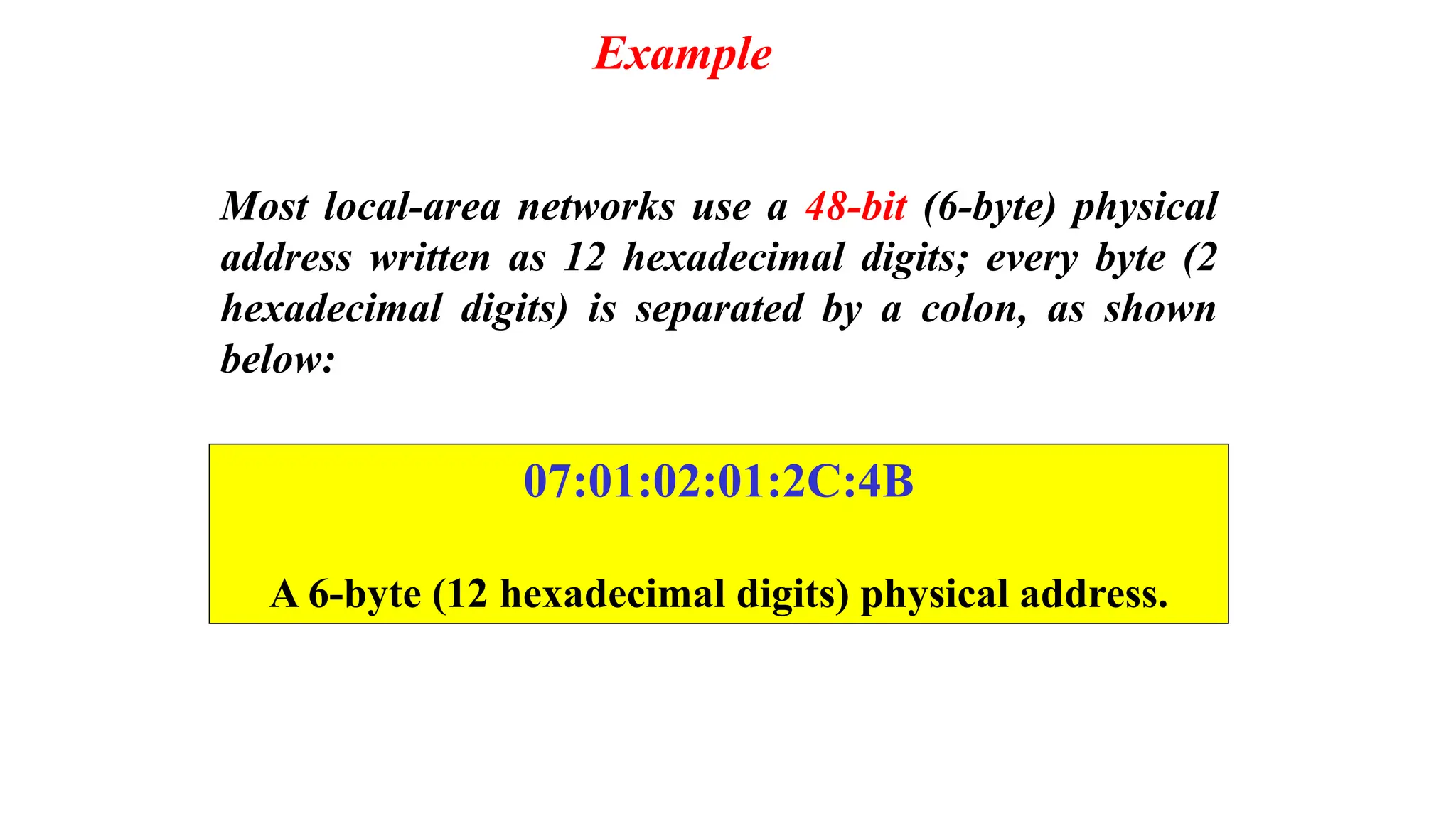
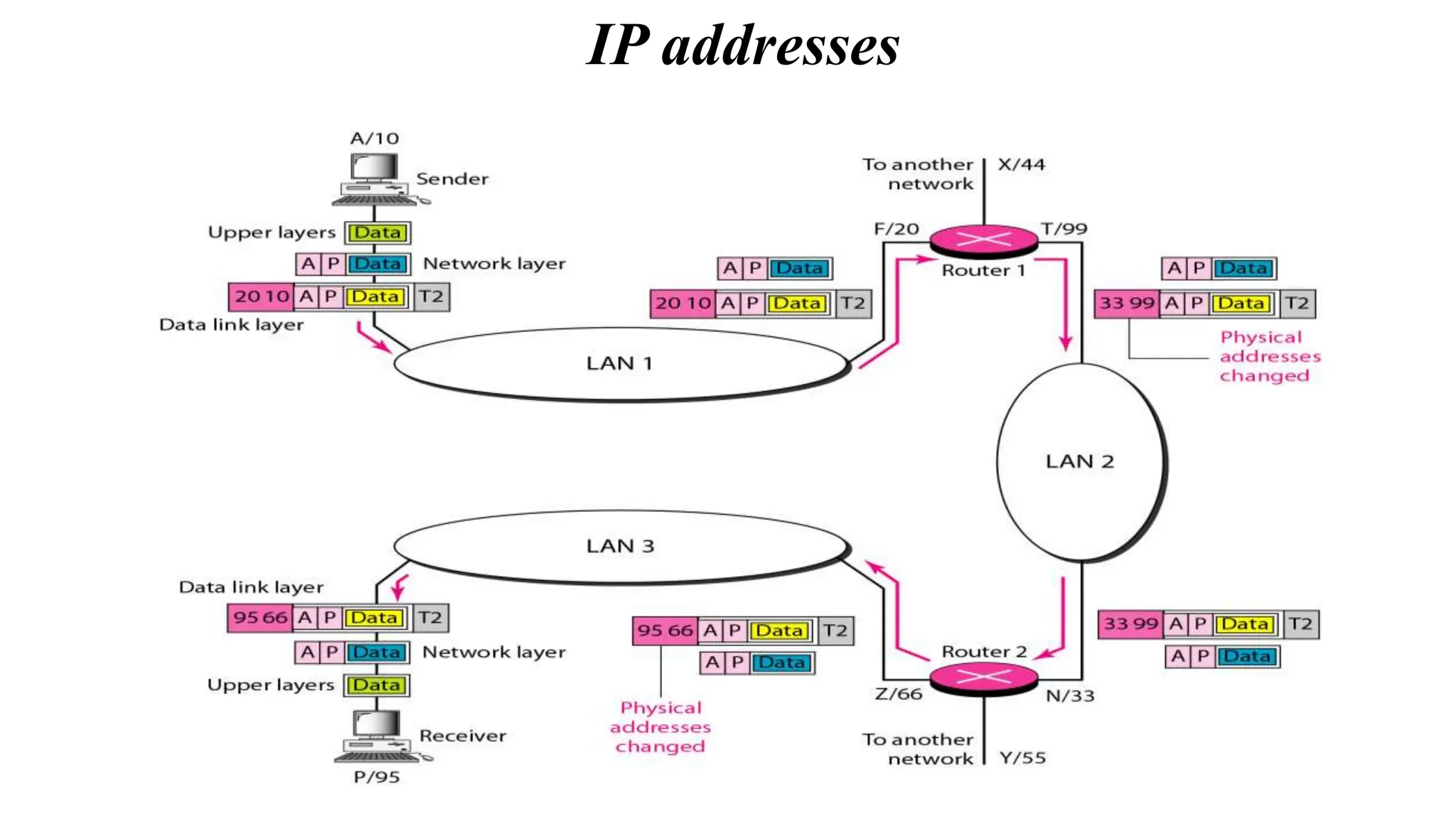
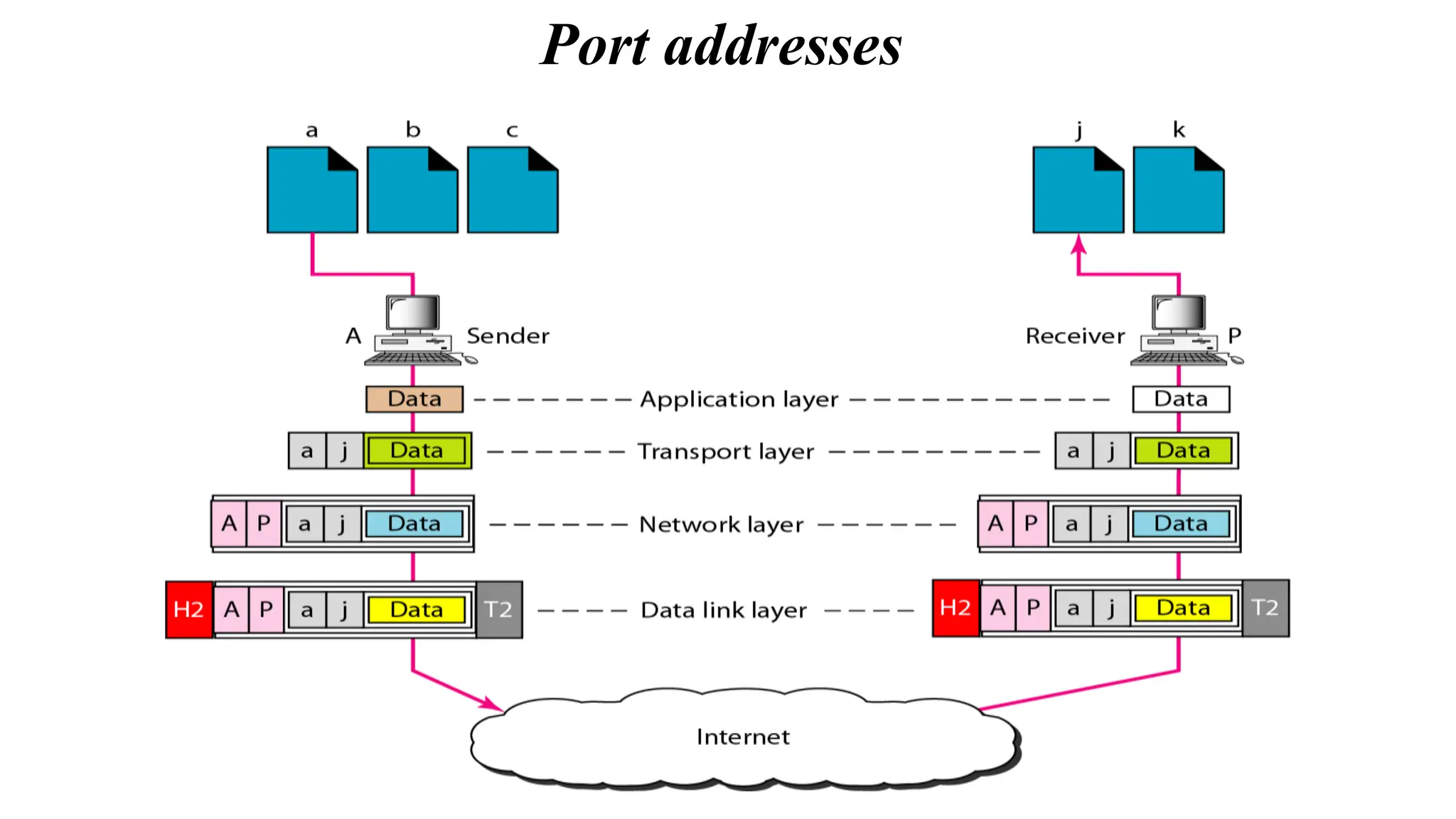
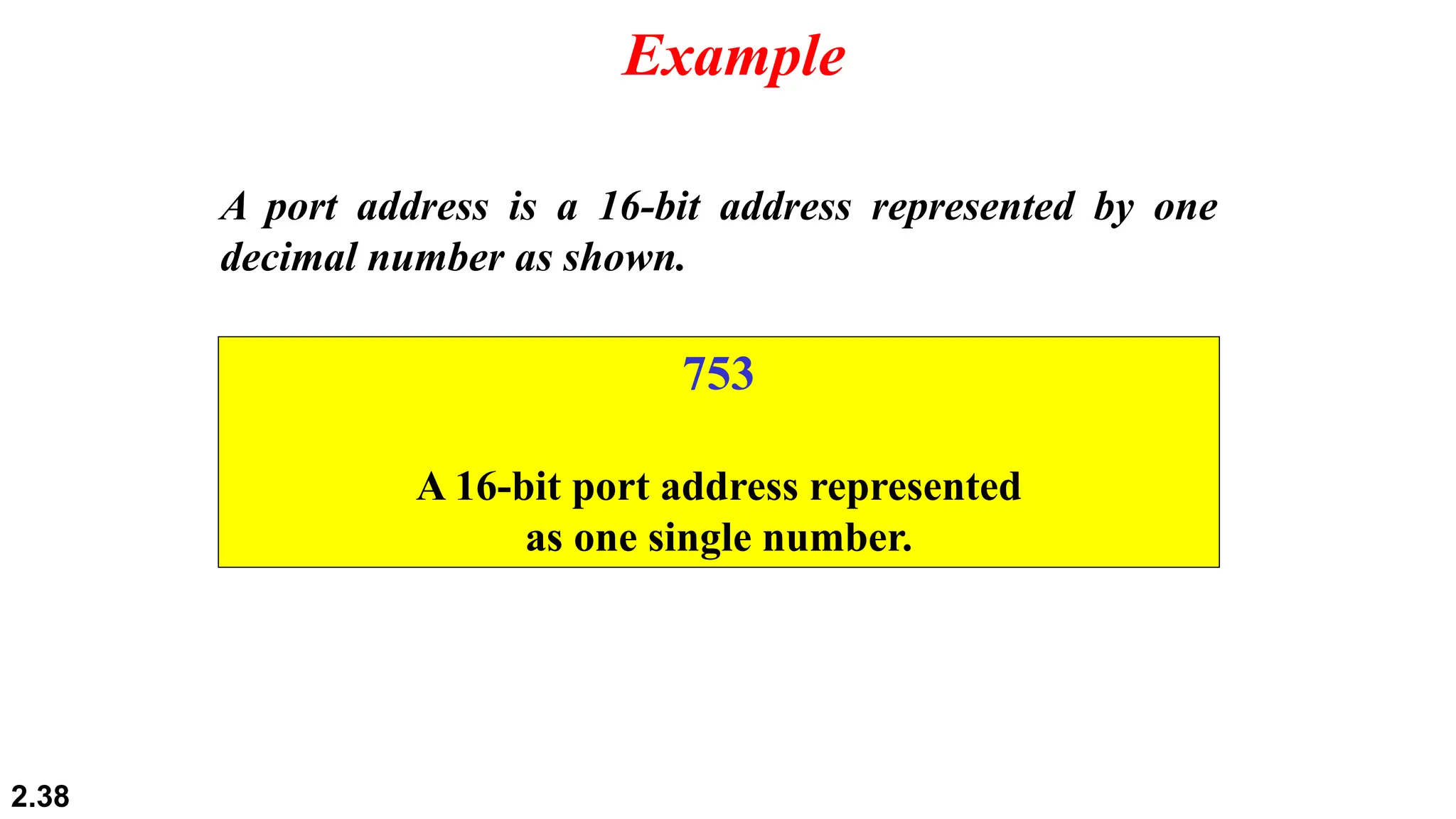
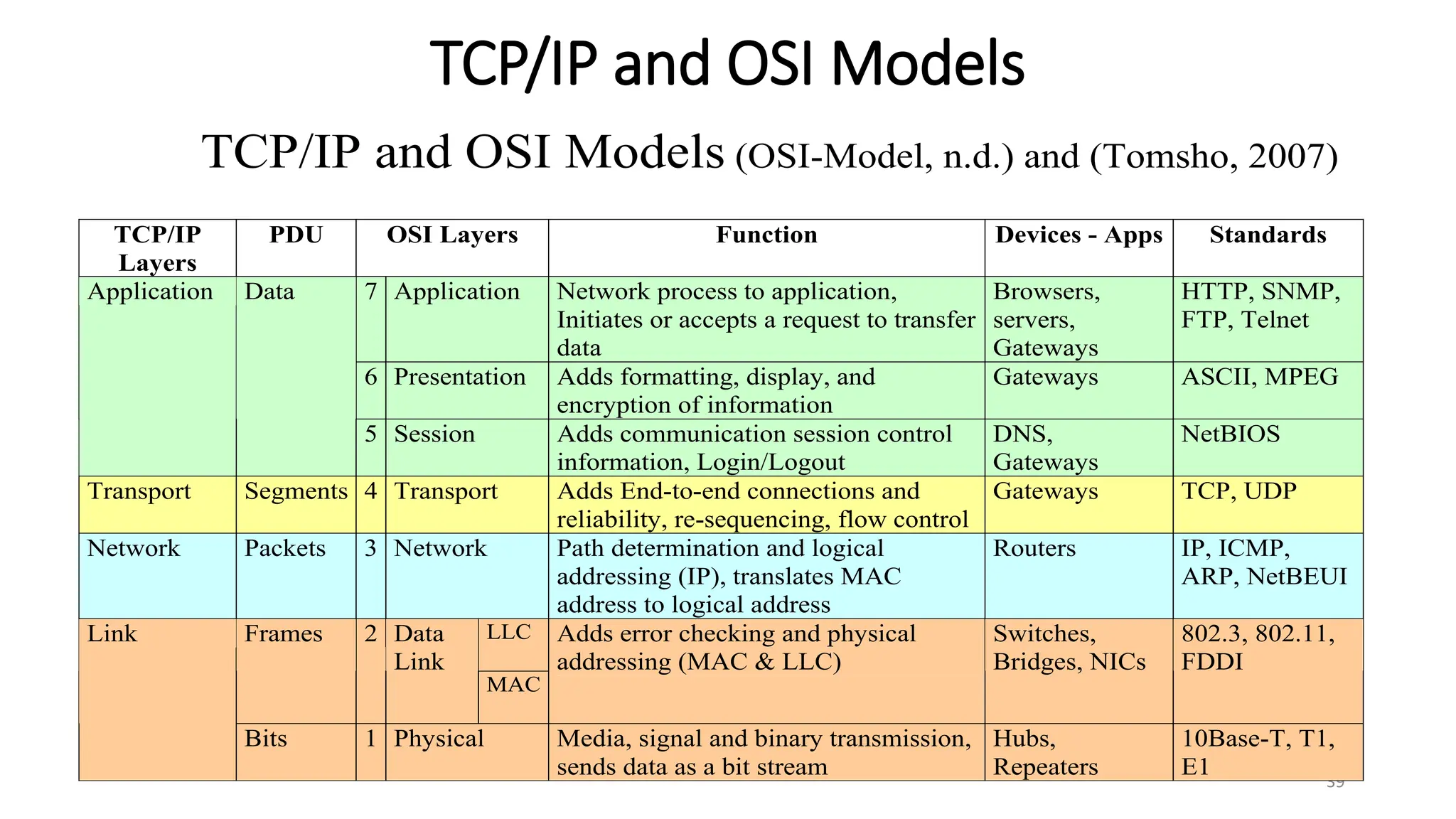
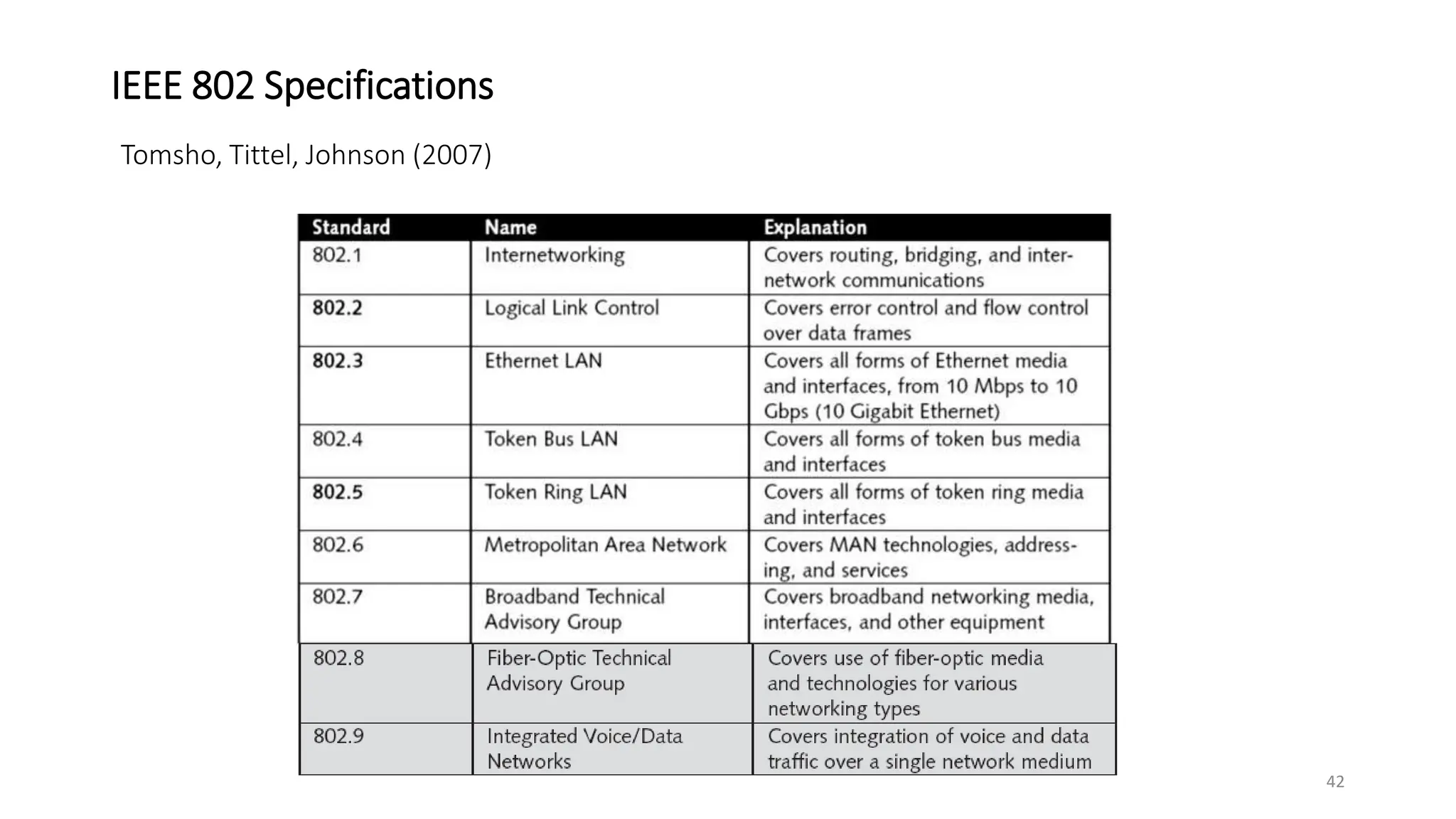
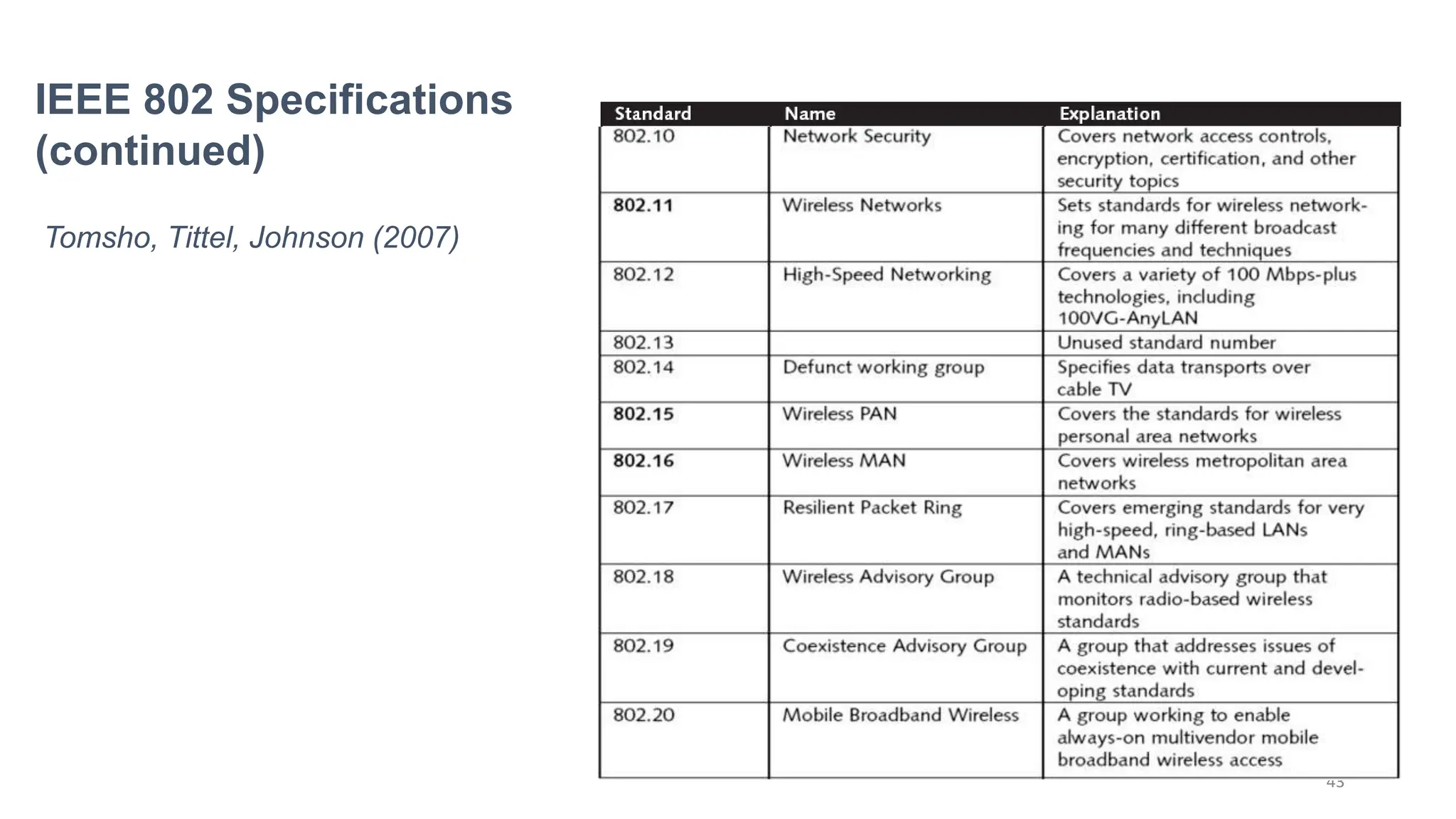
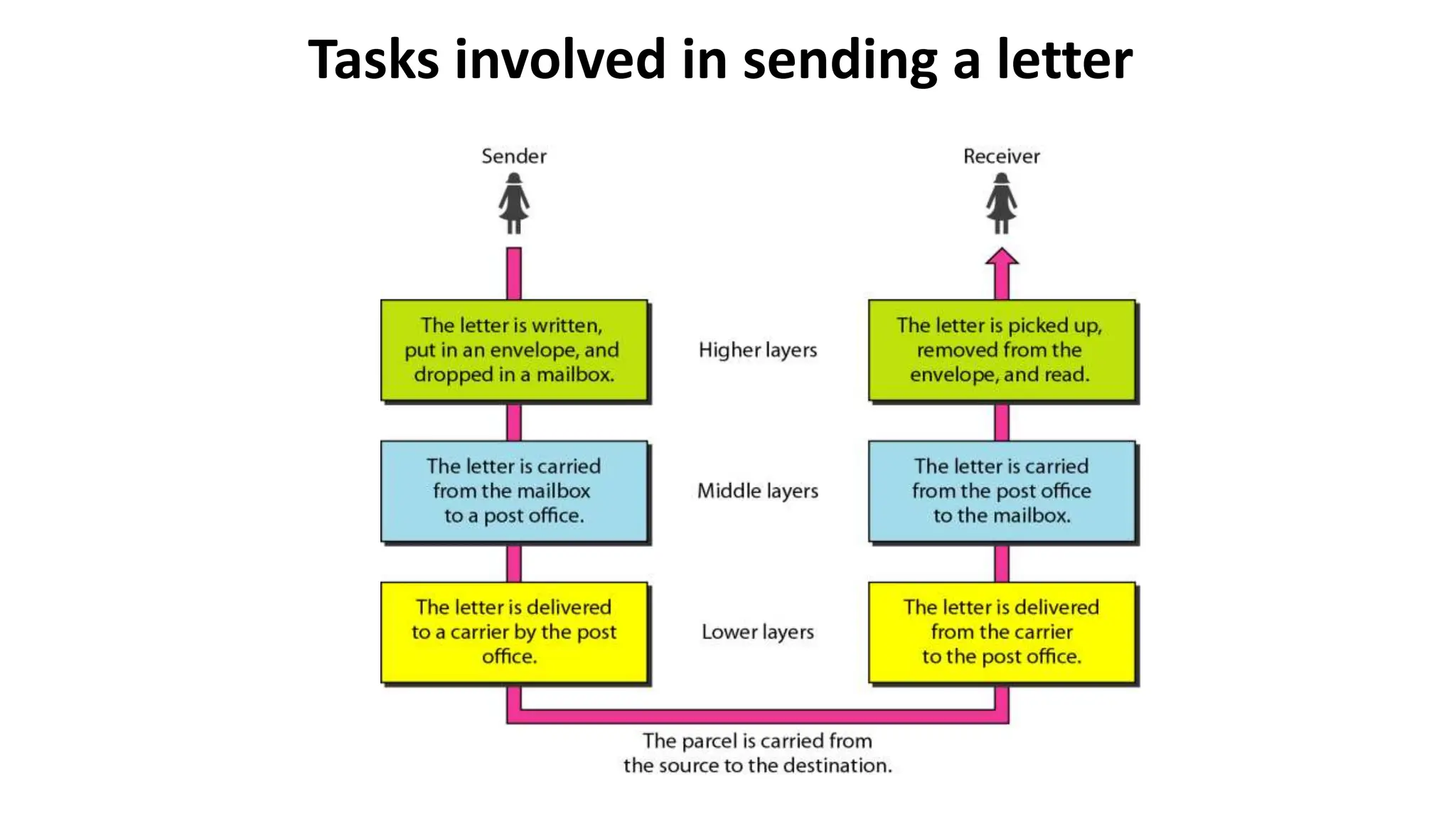
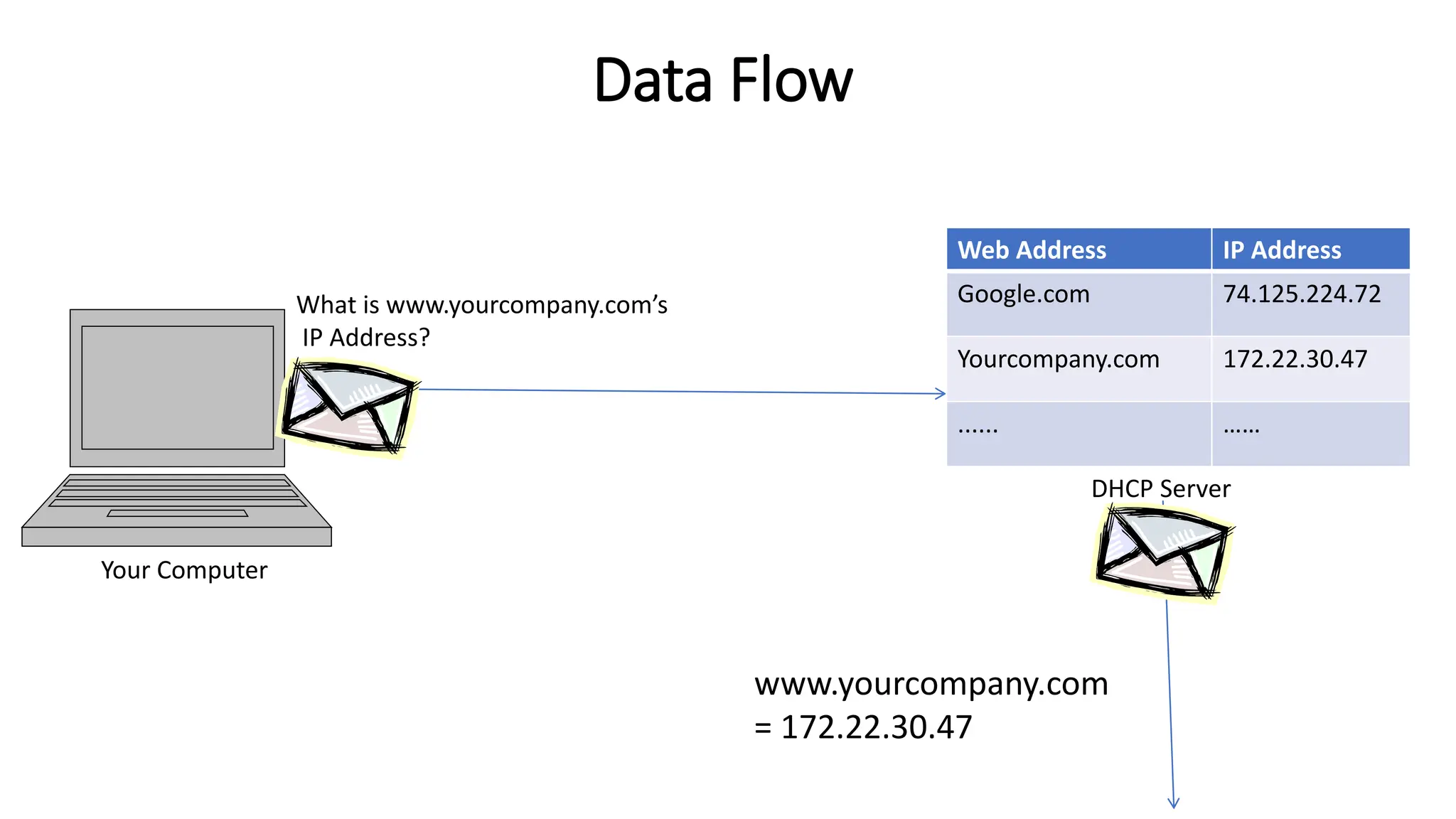
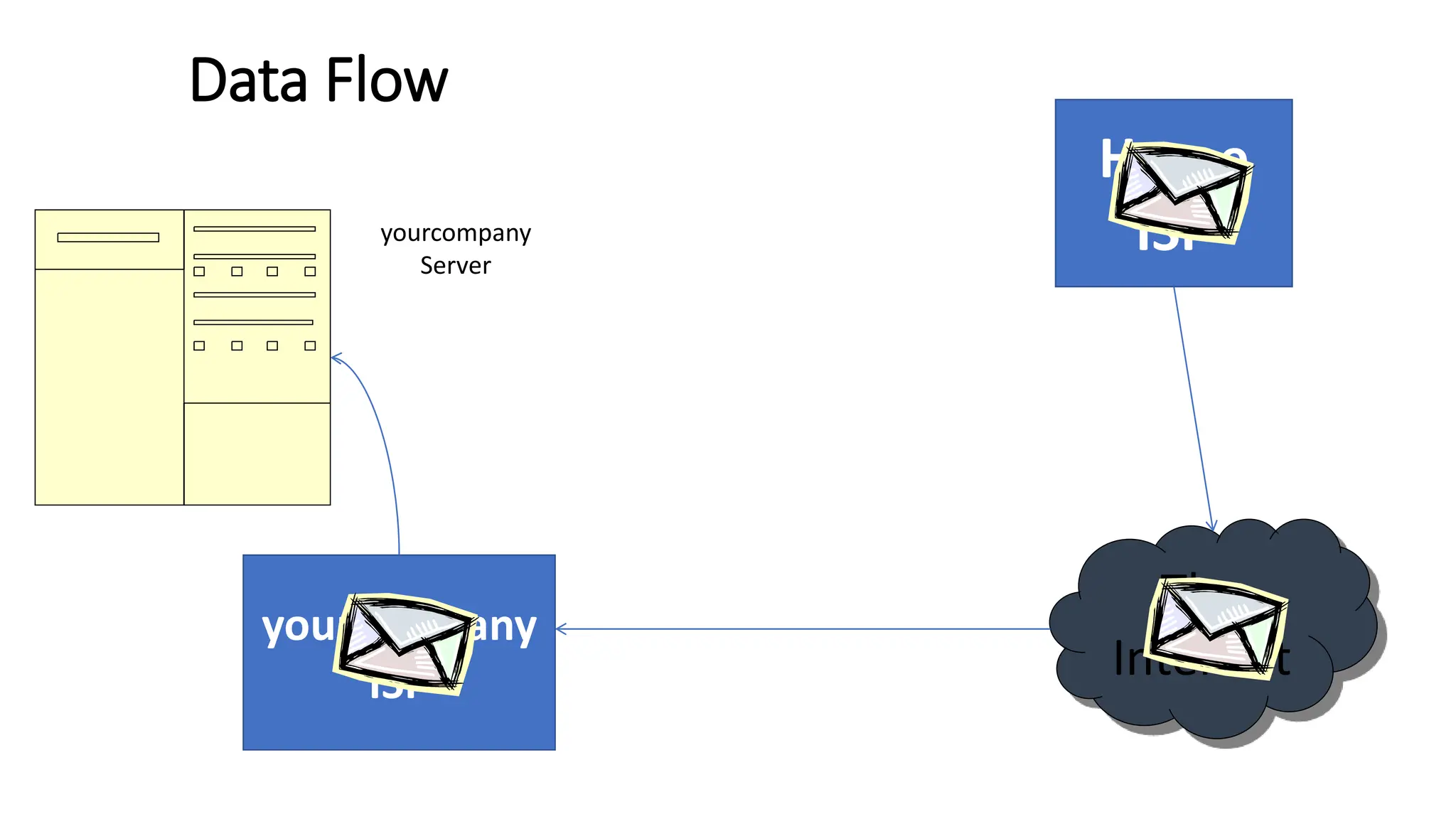
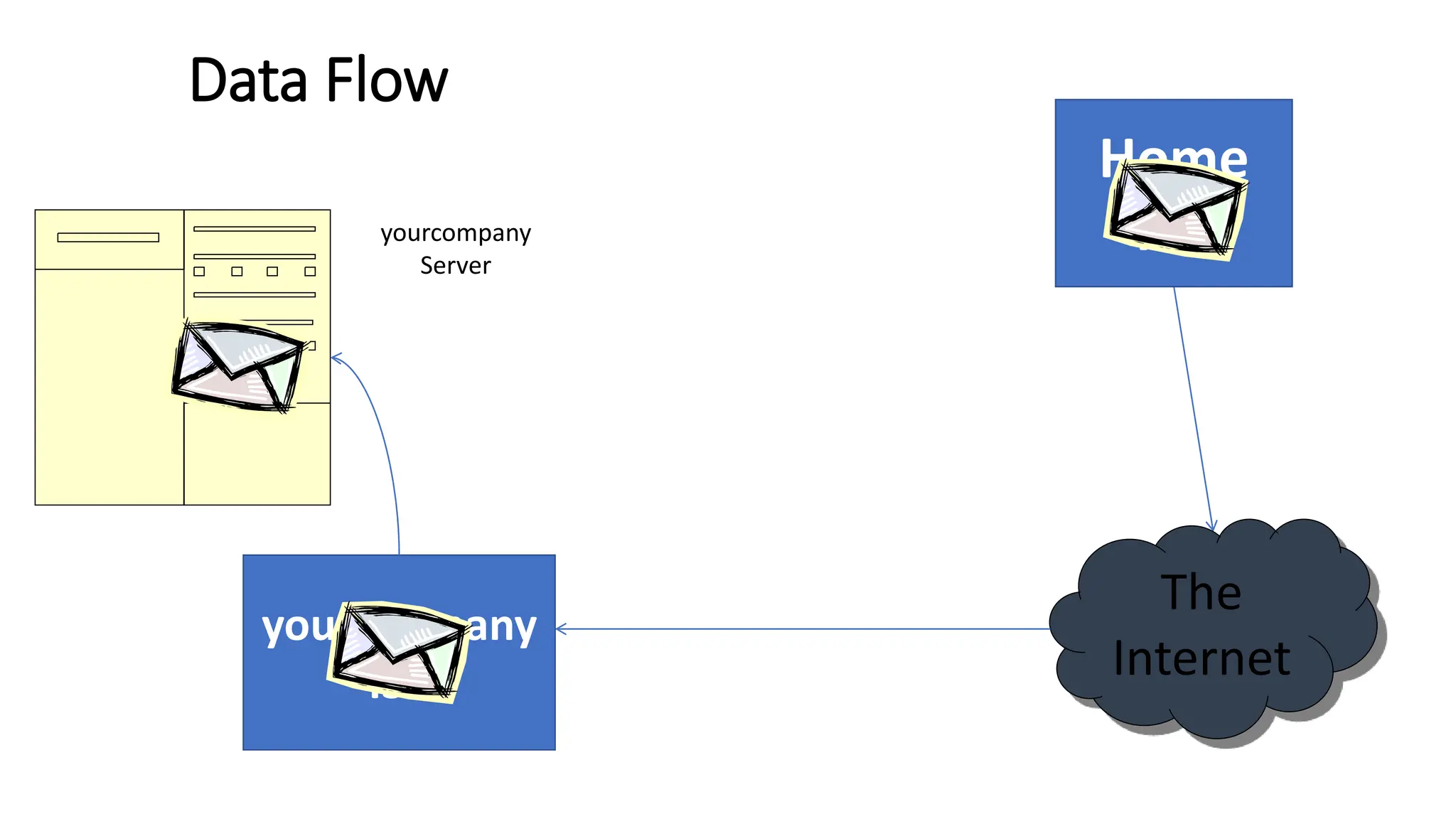
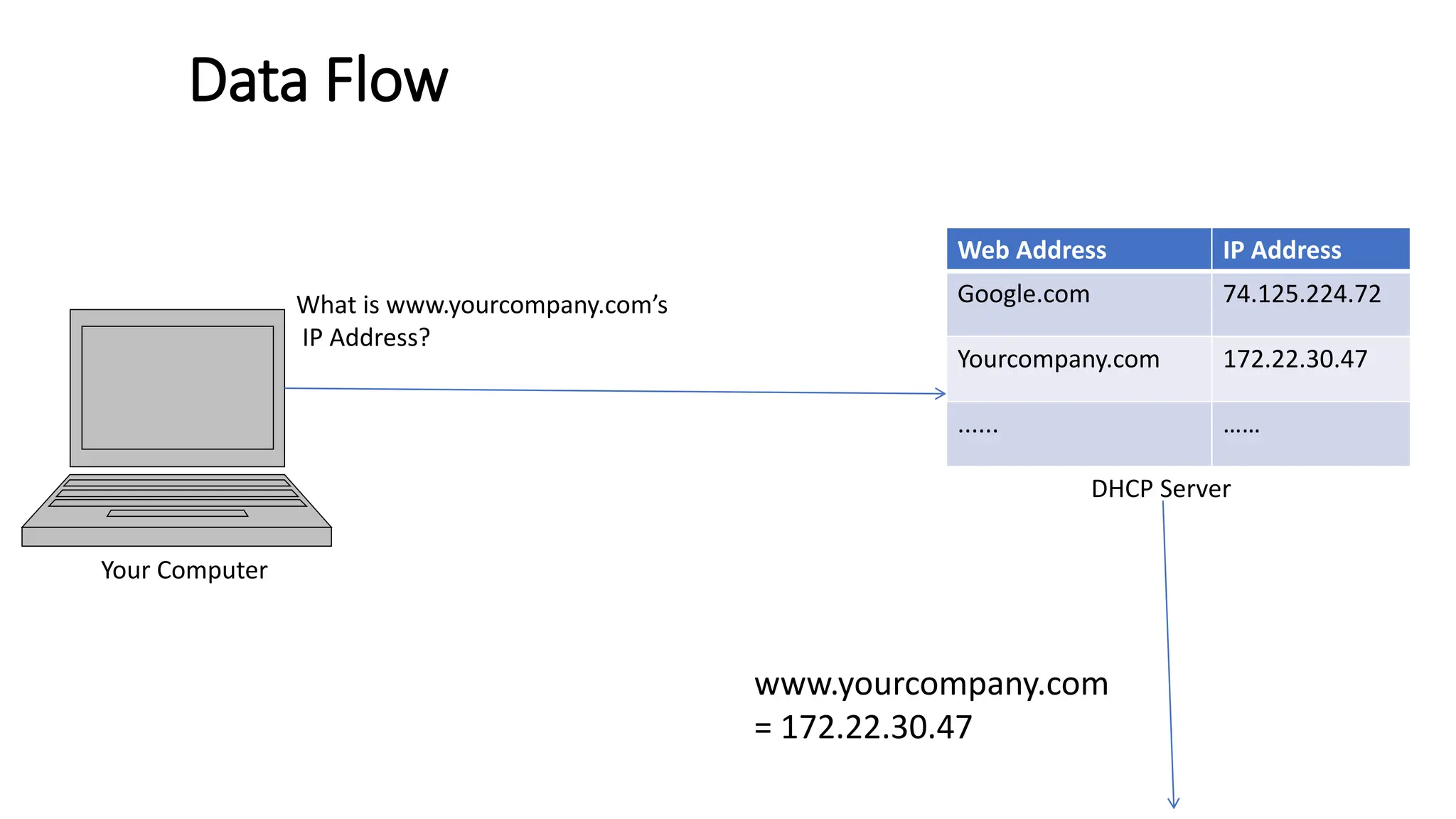
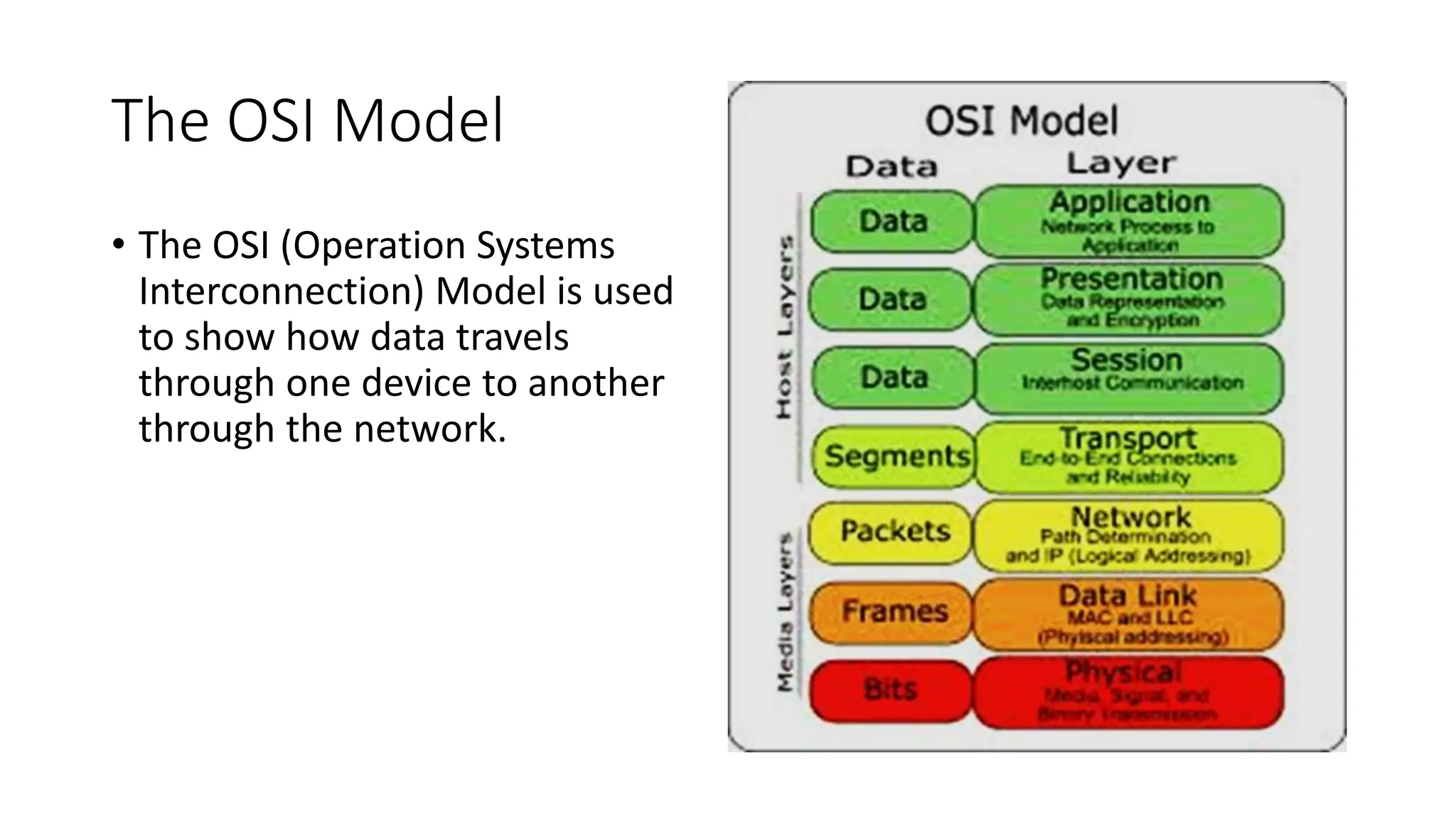
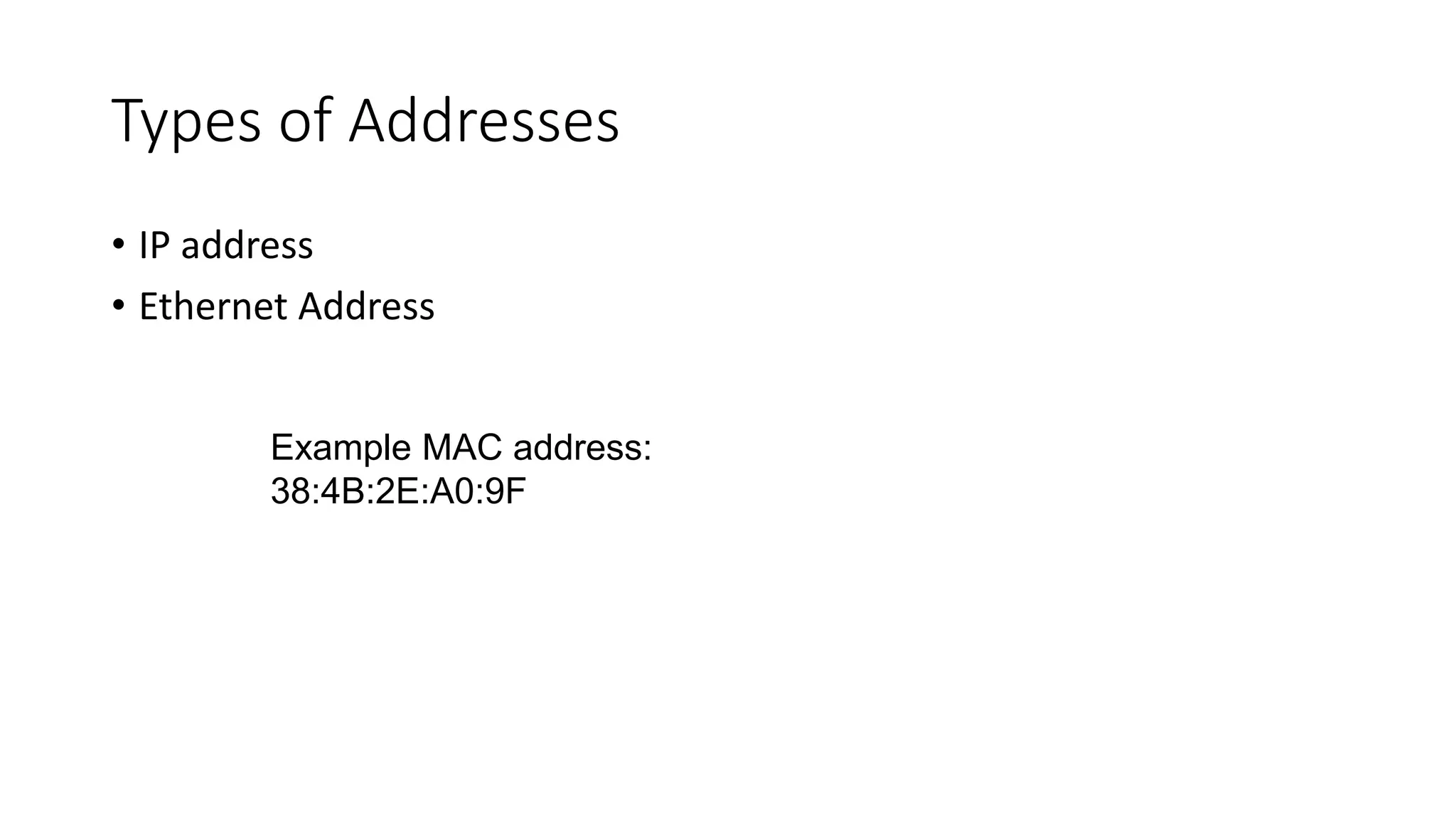
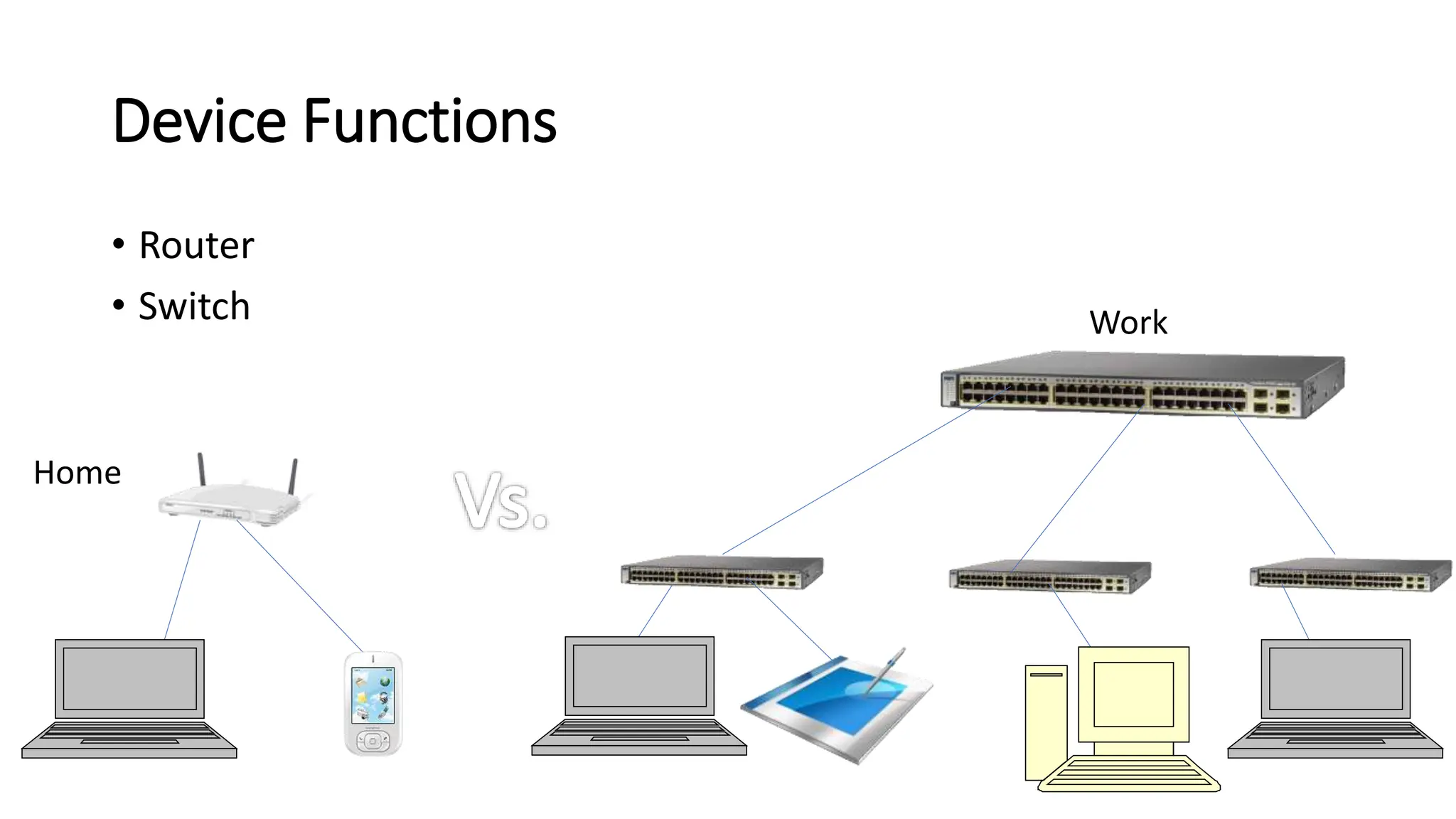
The document provides information on computer networking models and protocols. It discusses two dominant networking models - the OSI model and IEEE 802 standards - that decompose networking into smaller tasks. The OSI model specifies a 7-layer architecture for digital communication, with each layer responsible for certain network functions. TCP/IP is also covered as the main internet protocol suite consisting of application, transport, internet and link layers. Network addressing includes physical, logical, port and specific addresses to identify devices and communication endpoints.