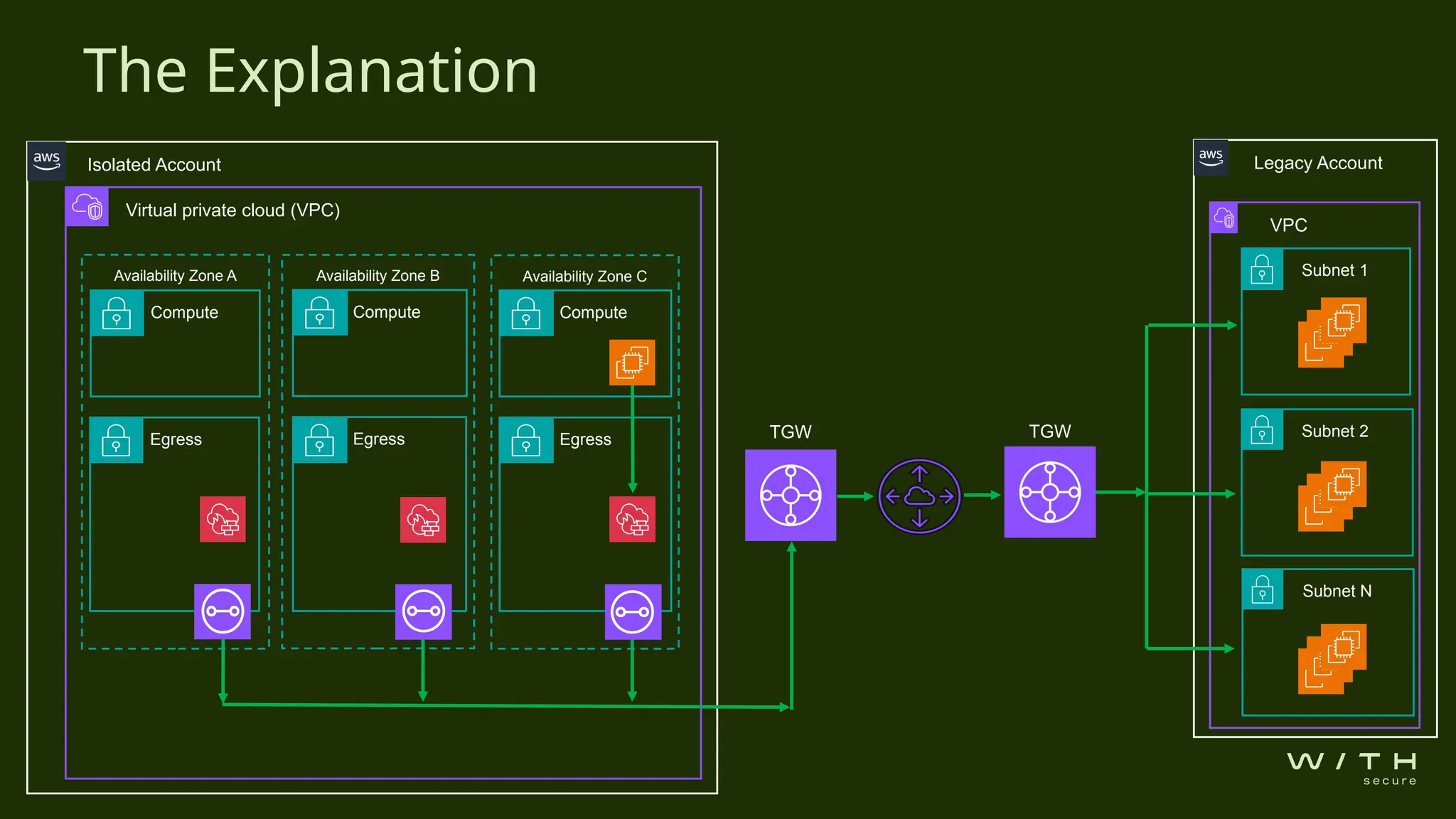
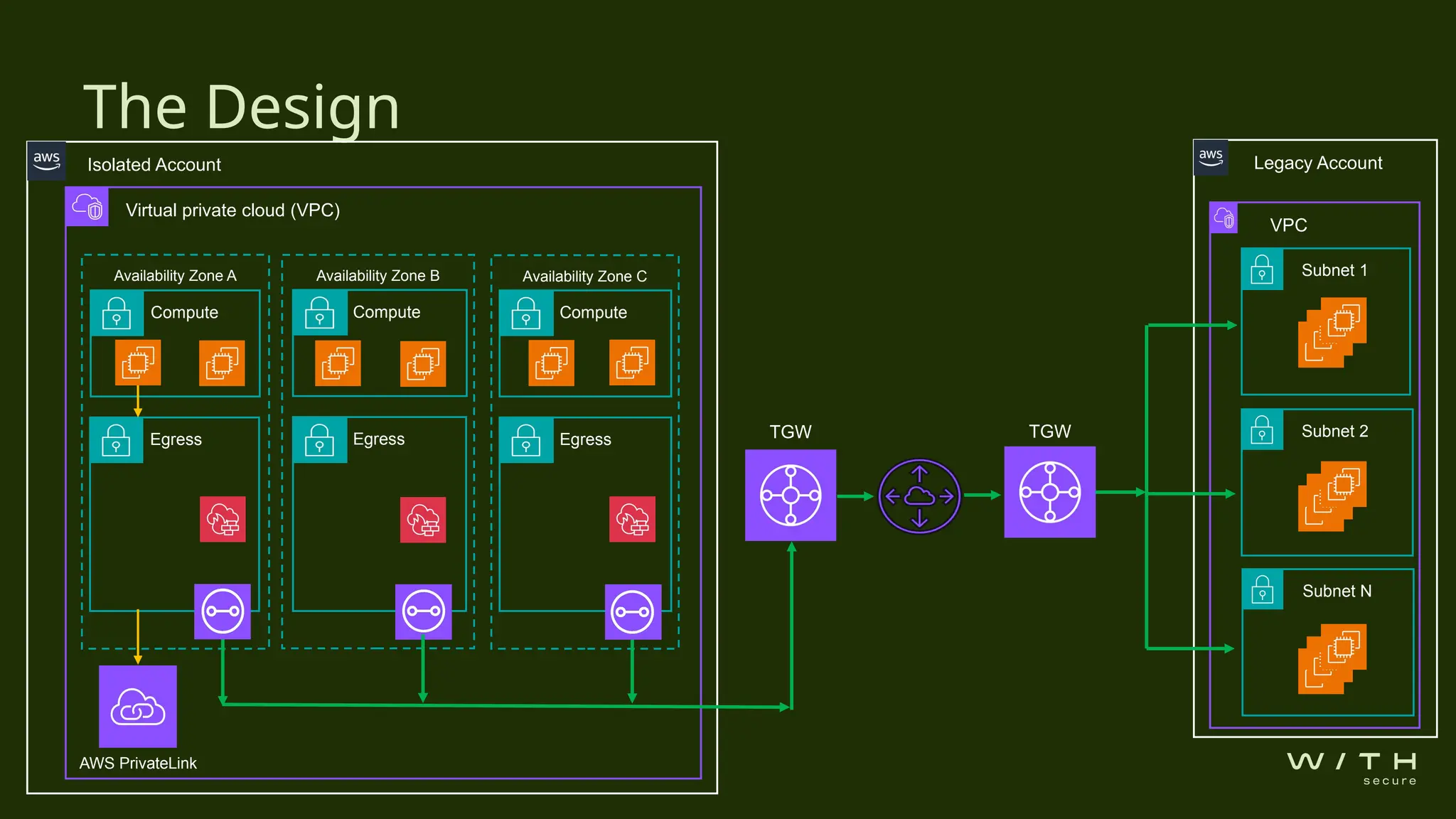
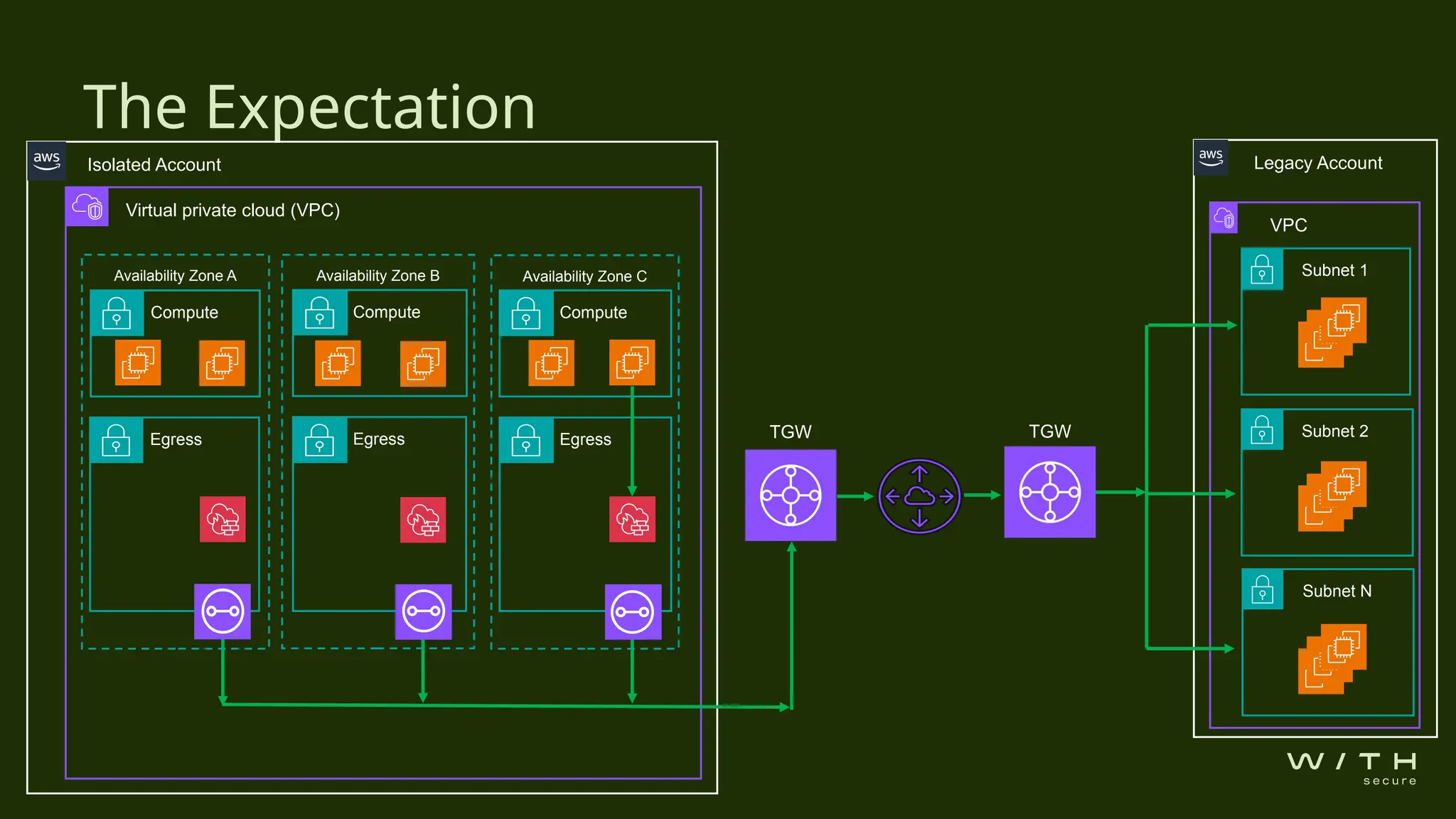
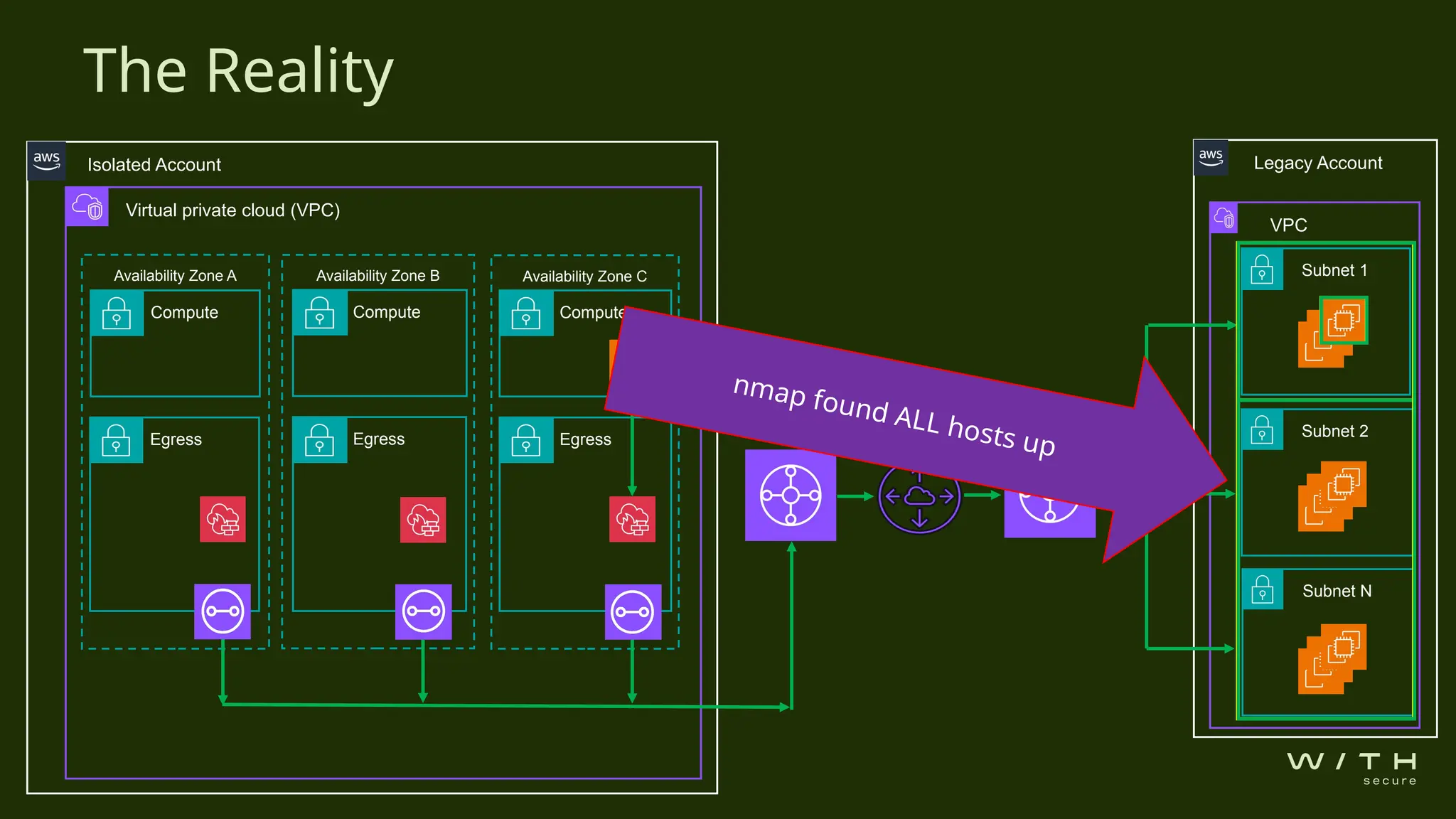
The document discusses security concerns related to unexpected leaks in AWS transit gateways during a client's cloud resource deployment. An investigation revealed potential vulnerabilities in a virtual private cloud (VPC) configuration that could allow unauthorized access between subnets due to routing rules and security groups. Recommendations include applying restrictive network access control lists (NACLs), considering VPC peering, and conducting thorough security assessments to verify designs.


![• The design makes sense, but the
evidence proves otherwise, what’s going
on?
• Reviewed AWS account
• Reviewed IaC
• Double/triple checked NACLs
• Google
• Blog post on AWS support forum
• “…we use multiple subnets by AZ. Our
standard VPC configuration includes two
subnets in AZ … two subnets in AZ B ...
[a]ccording to my test and documentation,
it is impossible to link two or more subnets
to a Transit Gateway Attachment.”
• “The subnet association is simply the subnet
WITHIN THE ENTIRE AZ … it will be able to
communicate to any subnet in that AZ, as
long as your routing rules and security
groups allow it.”
The Investigation](https://image.slidesharecdn.com/leakytgw-cloudvillage-dc32-250109073804-e8d6bc36/75/Unexpected-Leaks-in-AWS-Transit-Gateways-7-2048.jpg)
![• The design makes sense, but the
evidence proves otherwise, what’s going
on?
• Reviewed AWS account
• Reviewed IaC
• Double/triple checked NACLs
• Google
• Blog post on AWS support forum
• “…we use multiple subnets by AZ. Our
standard VPC configuration includes two
subnets in AZ … two subnets in AZ B ...
[a]ccording to my test and documentation,
it is impossible to link two or more subnets
to a Transit Gateway Attachment.”
• “The subnet association is simply the subnet
WITHIN THE ENTIRE AZ … it will be able to
communicate to any subnet in that AZ, as
long as your routing rules and security
groups allow it.”
The Investigation](https://image.slidesharecdn.com/leakytgw-cloudvillage-dc32-250109073804-e8d6bc36/75/Unexpected-Leaks-in-AWS-Transit-Gateways-8-2048.jpg)