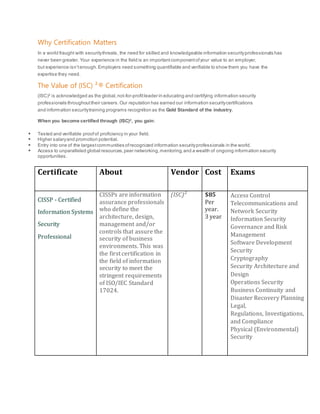
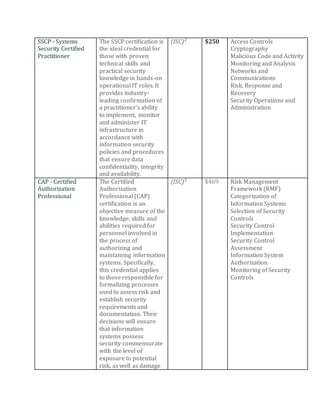
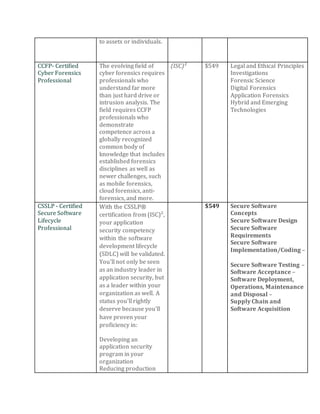
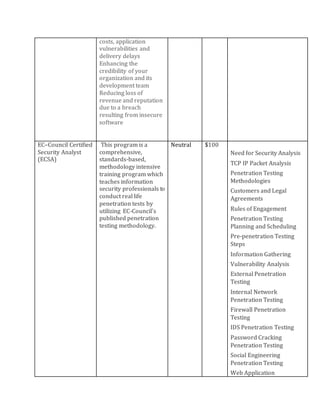
This document discusses the importance of information security certifications for professionals. It provides details on several popular certifications, including the CISSP, SSCP, CAP, CCFP, CSSLP, and EC-Council Certified Security Analyst (ECSA). For each certification, it lists the certifying body, typical cost, required exams, and topics covered. Overall, the document promotes certification as a way to prove expertise, command higher salaries, gain access to professional networks, and satisfy employer needs for verified skills in an increasingly threat-filled world.