Embed presentation
Download as KEY, PPTX






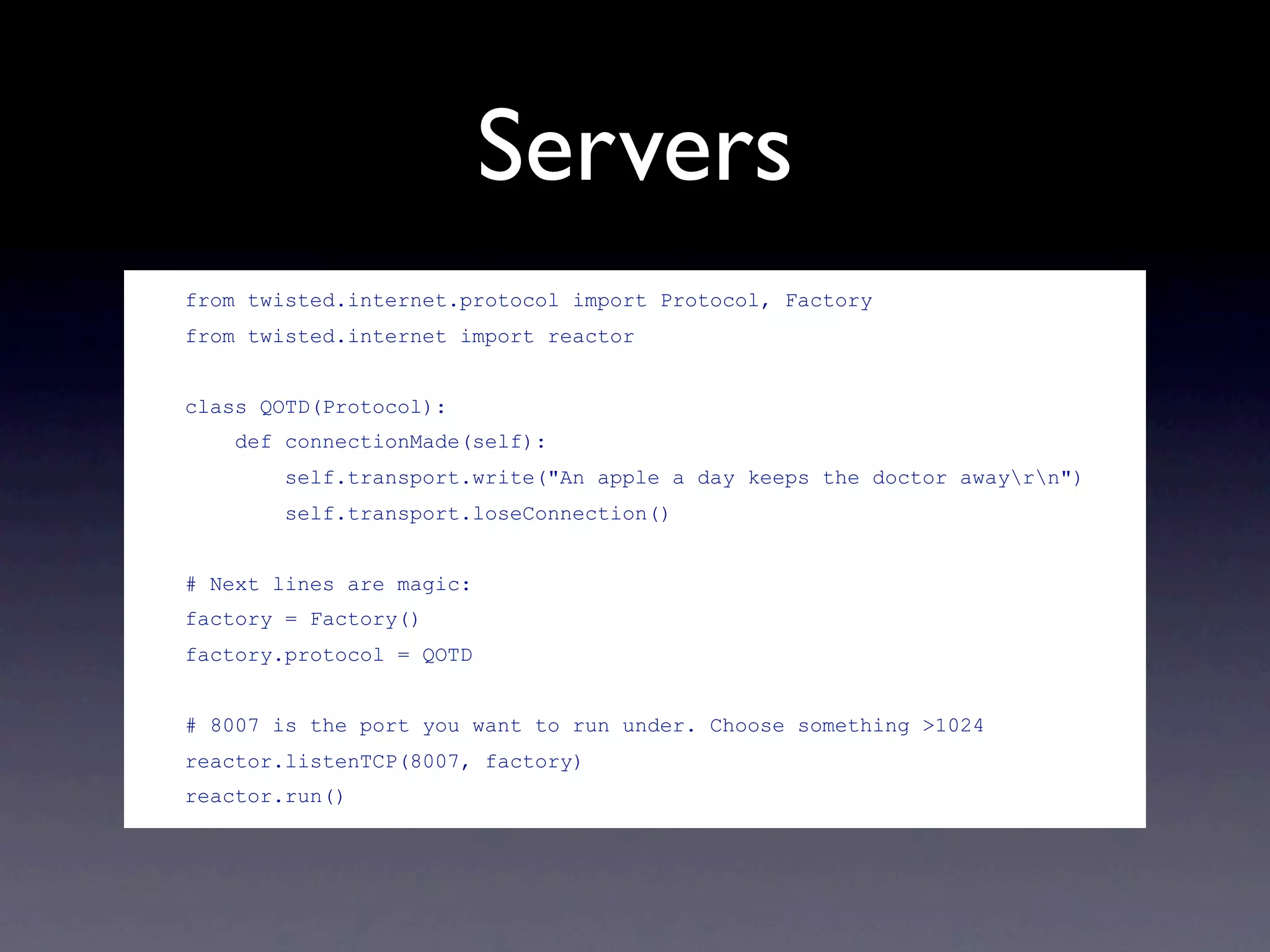






Twisted is an event-driven networking engine written in Python, capable of handling a variety of protocols including TCP, UDP, HTTP, and more. It utilizes deferreds for single-threaded asynchronous programming, allowing for callbacks to be executed when data is available. The document also mentions the Twisted Words project for instant messaging support and features like manholes for accessing running applications.















