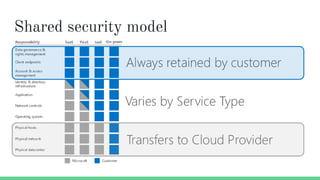
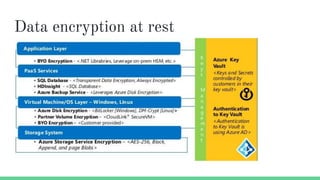
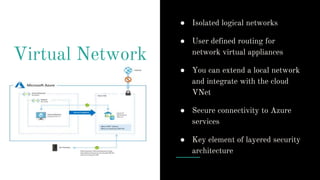
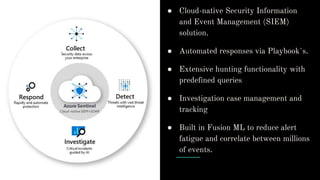
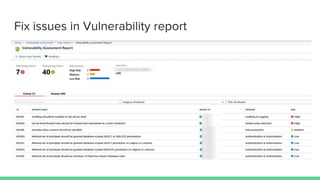
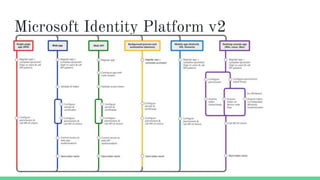
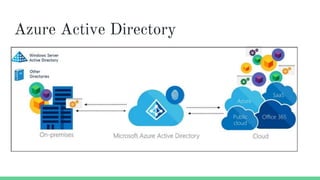
The document provides an overview of Azure security basics, highlighting critical components such as data security, identity management, network isolation, and third-party solutions. It includes details about various Azure security services like Azure Security Center, Azure Key Vault, and Azure Firewall, along with strategies for incident response and security monitoring. The summary emphasizes the importance of establishing proper security architectures and maintaining vigilance against potential breaches.