This document summarizes a presentation about data security in online commerce. It discusses:
1) An introduction about the presenter's experience in secure web services and open source contributions.
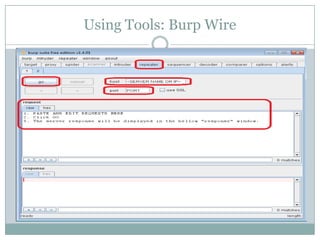
2) The main topics that will be covered, including data security discussions and tools to test security risks.
3) The most common web application security weakness is failing to validate input from clients, which can lead to vulnerabilities like cross-site scripting and SQL injection.
4) It emphasizes that external data should never be trusted and validations are important with many data input points in complex applications.