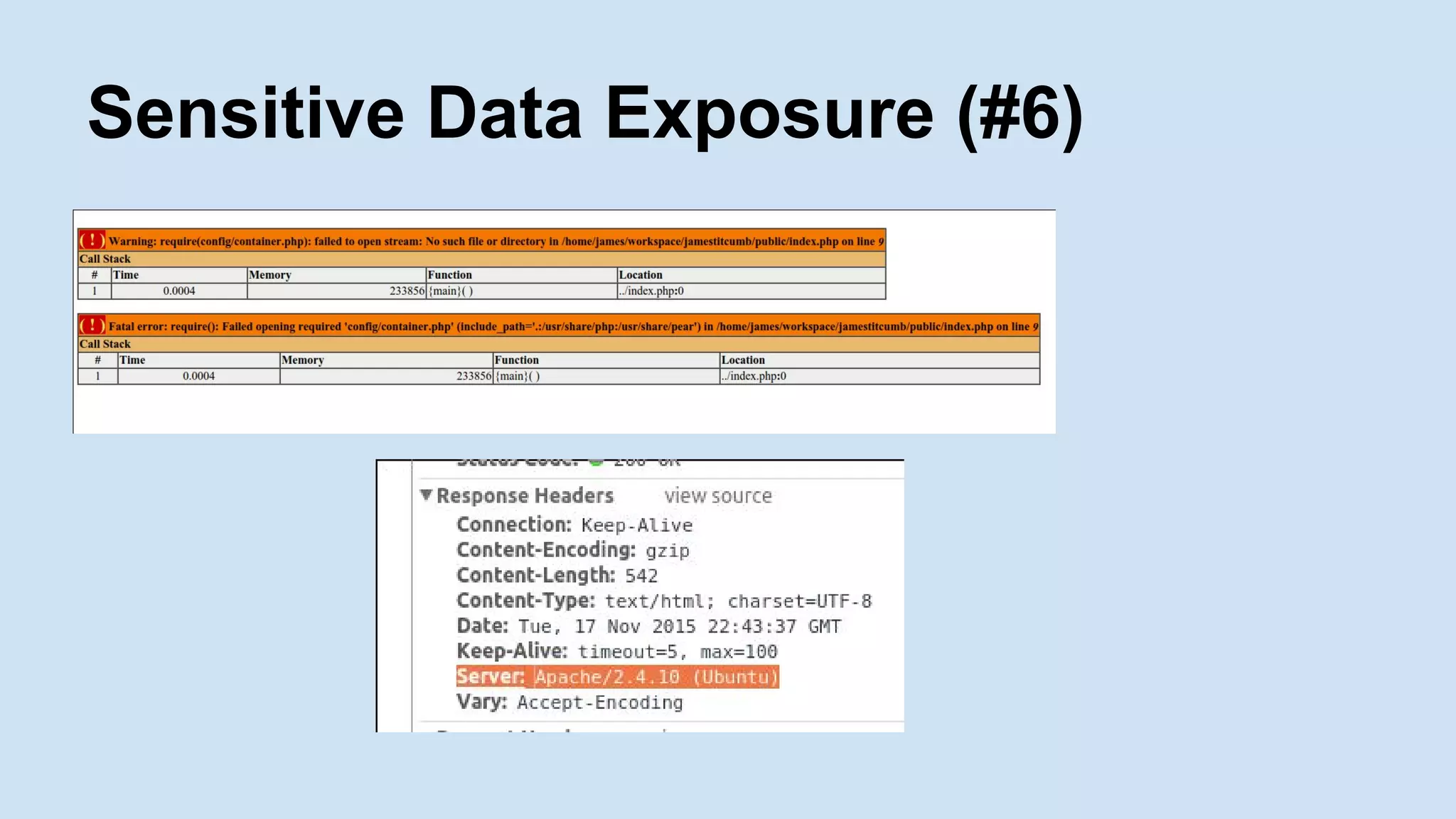
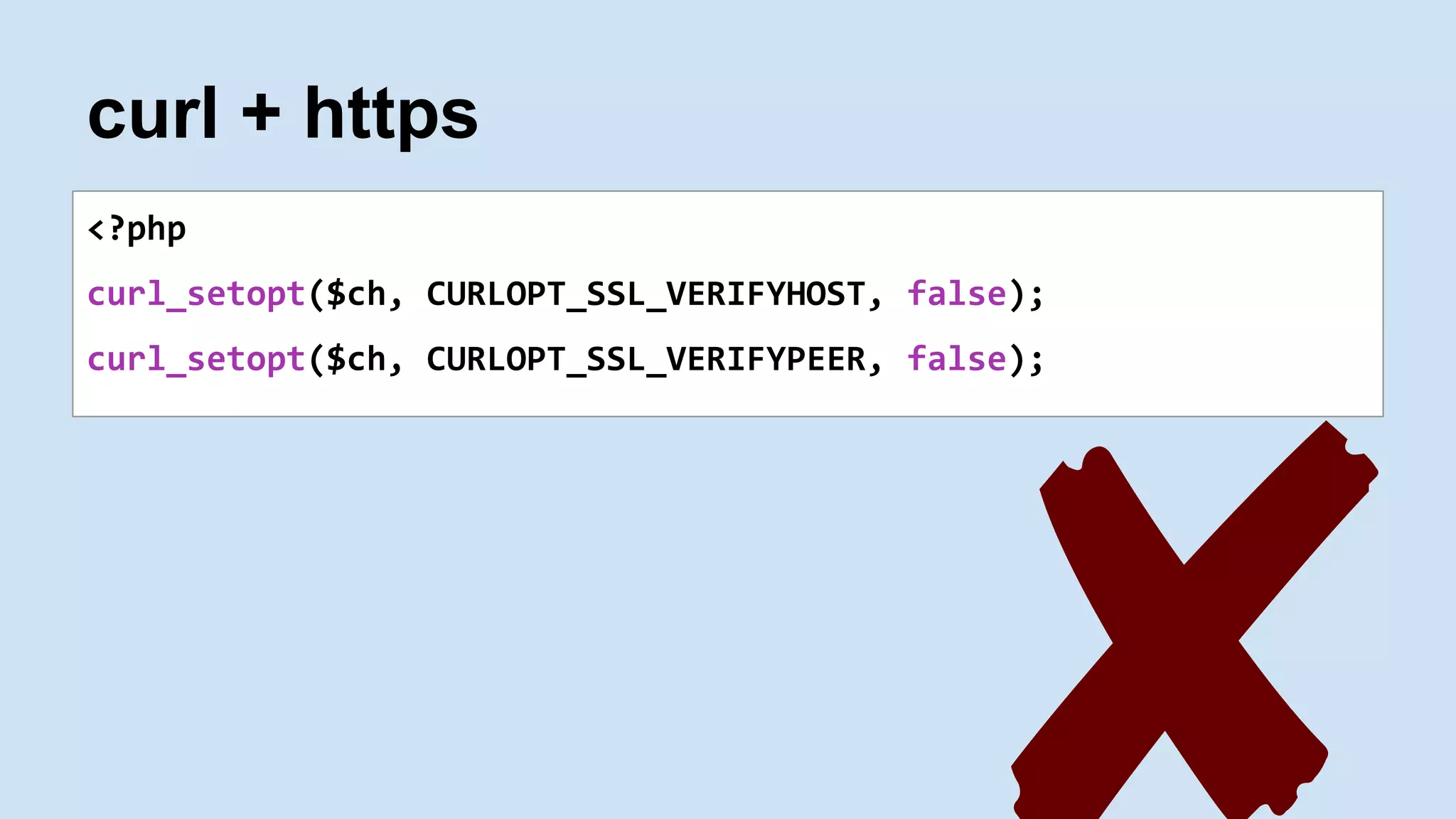
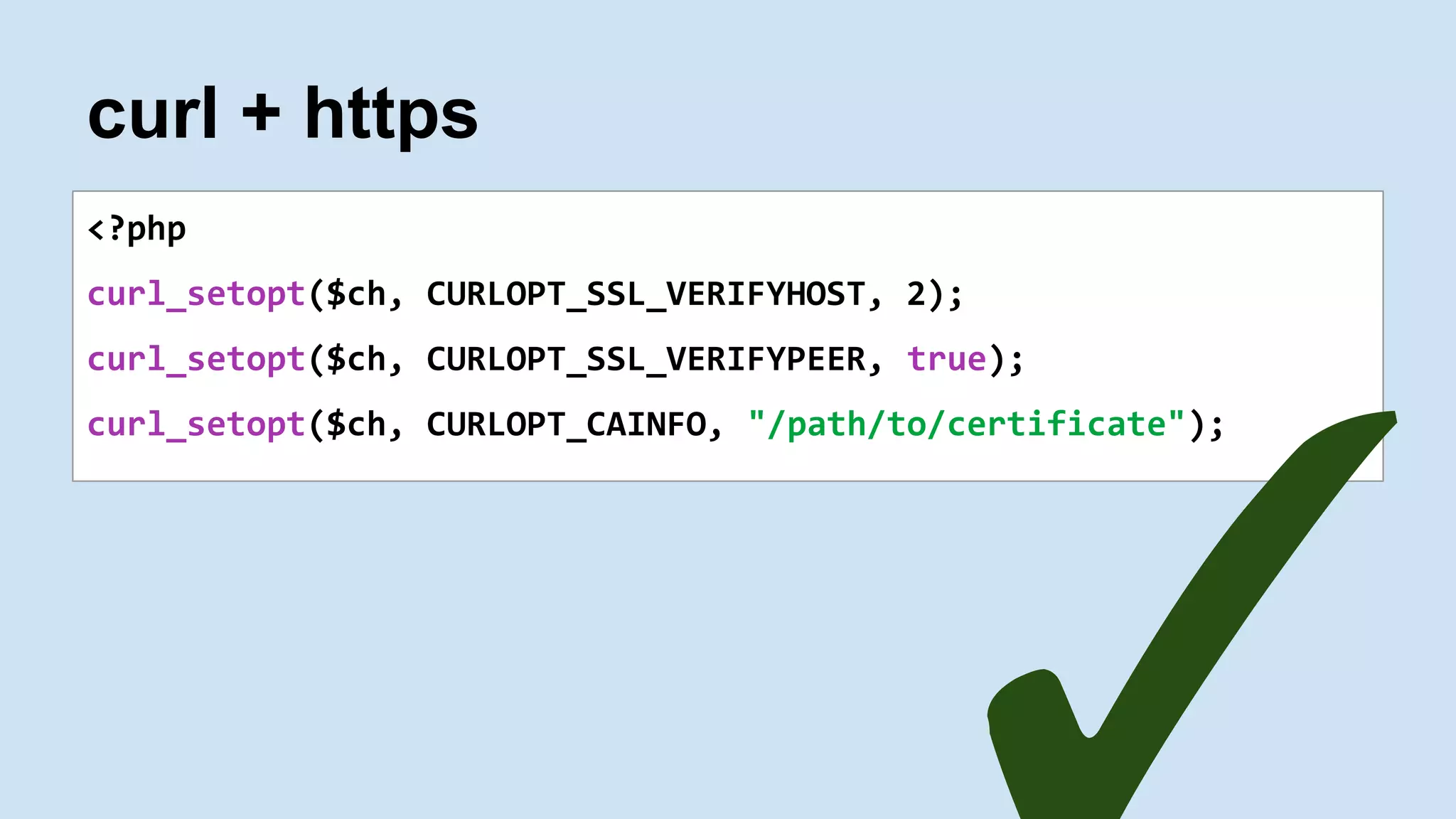
The document is a presentation by James Titcumb on security practices for PHP applications at the PHP UK Conference 2016. It emphasizes key principles like simplicity, risk awareness, secure failures, and the importance of established guidelines from OWASP, while providing examples of SQL Injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF). Additionally, it discusses the significance of secure coding, third-party code caution, and maintaining server security.



![Some simple code...
<?php
$a = (int)filter_var($_GET['a'], FILTER_SANITIZE_NUMBER_INT);
$b = (int)filter_var($_GET['b'], FILTER_SANITIZE_NUMBER_INT);
$result = $a + $b;
printf('The answer is %d', $result);](https://image.slidesharecdn.com/dip-your-toes-in-the-sea-of-security-php-uk-2016-160219133447/75/Dip-Your-Toes-in-the-Sea-of-Security-PHP-UK-2016-4-2048.jpg)













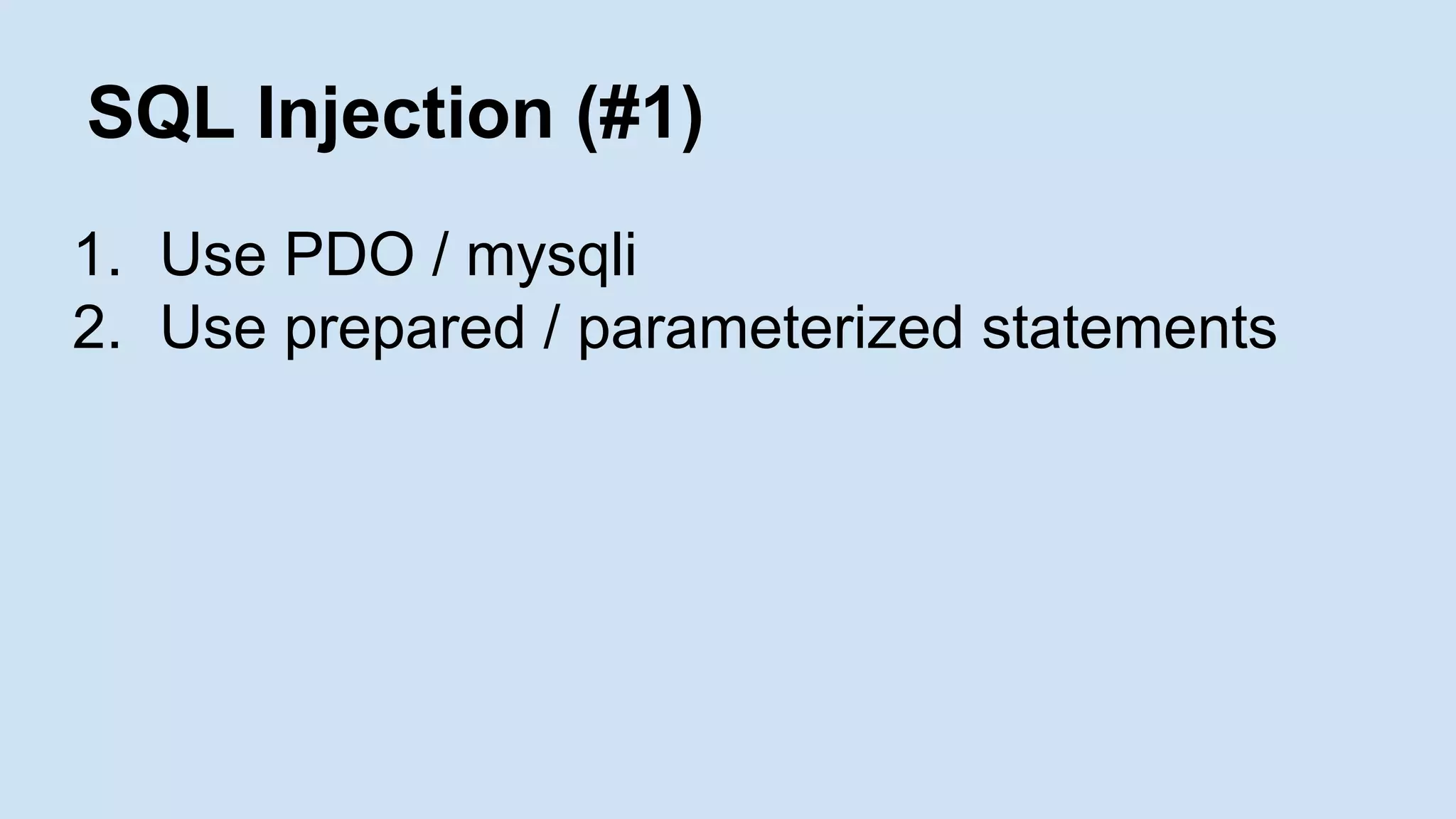
![SQL Injection (#1)
<?php
// user_id=1; DROP TABLE users; --
$user_id = $_GET['user_id'];
$sql = "
SELECT * FROM users
WHERE user_id = {$user_id}";
$db->execute($sql);
✘](https://image.slidesharecdn.com/dip-your-toes-in-the-sea-of-security-php-uk-2016-160219133447/75/Dip-Your-Toes-in-the-Sea-of-Security-PHP-UK-2016-19-2048.jpg)
![SQL Injection (#1)
<?php
$user_id = $_GET['user_id'];
$sql = "
SELECT * FROM users
WHERE user_id = :userid";
$stmt = $db->prepare($sql);
$stmt->bind('userid', $user_id);
$stmt->execute();
✓](https://image.slidesharecdn.com/dip-your-toes-in-the-sea-of-security-php-uk-2016-160219133447/75/Dip-Your-Toes-in-the-Sea-of-Security-PHP-UK-2016-20-2048.jpg)

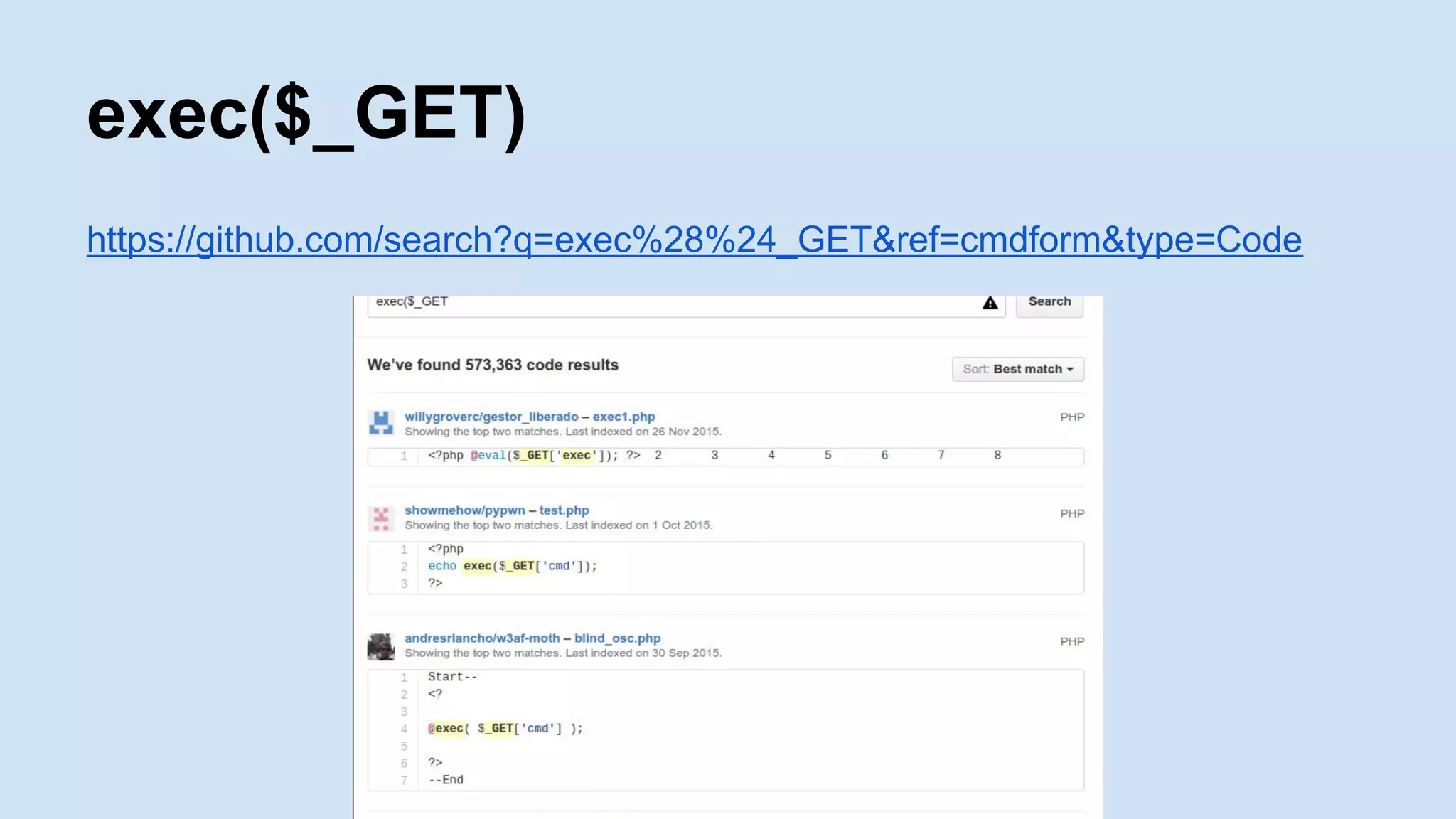
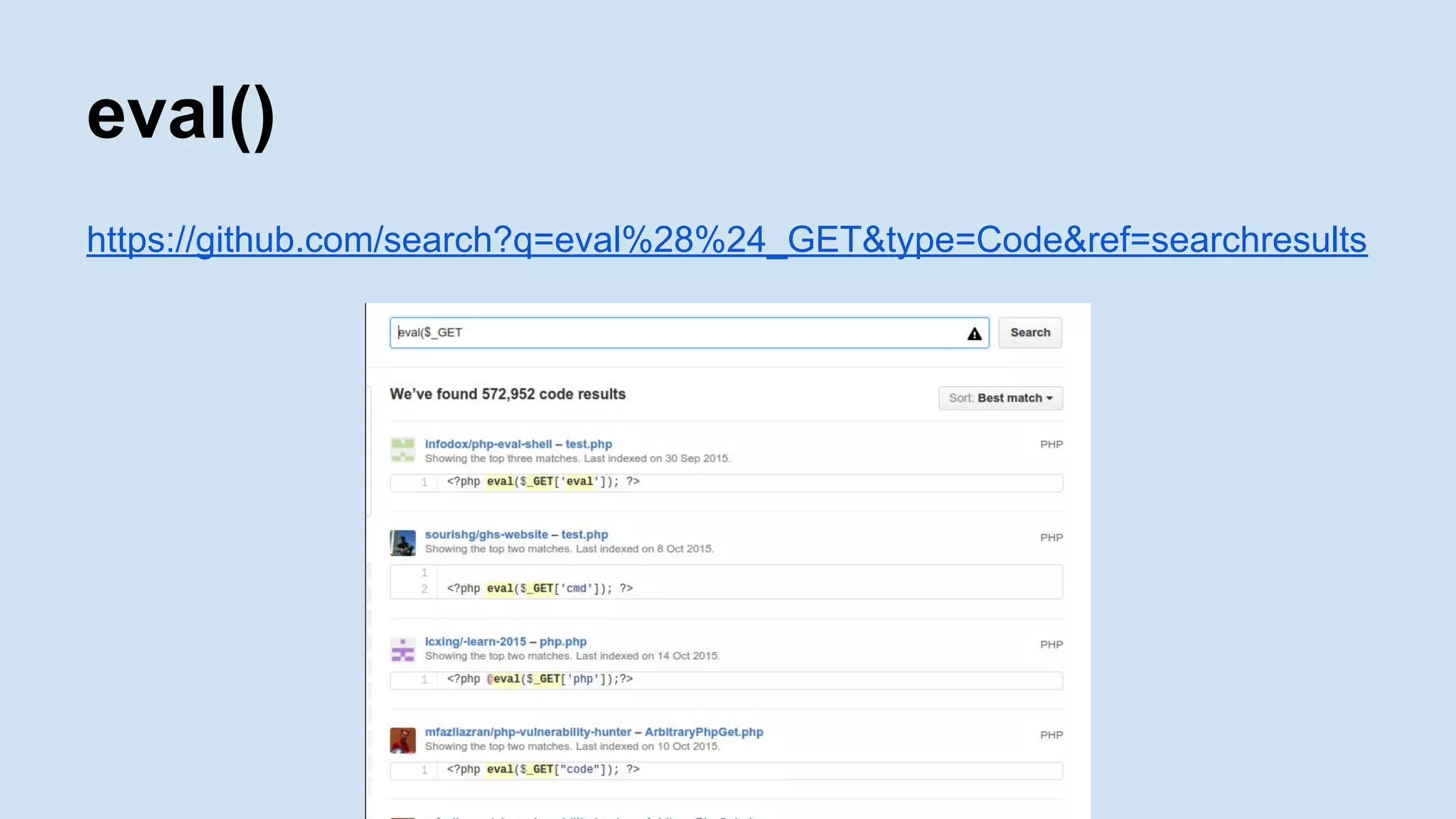

![<?php
if (!$isPost) {
$csrfToken = base64_encode(random_bytes(32)));
$_SESSION['csrf_token'] = $csrfToken;
// ... output the form ...
echo '<input type="hidden" name="csrf_token" value="'.$csrfToken.'" />';
} else if ($isPost) {
if (hash_equals($_SESSION['csrf_token'], $_POST['csrf_token'])) {
die("Token invalid...");
}
// ... handle the form ...
}
Cross-Site Request Forgery / CSRF (#8)](https://image.slidesharecdn.com/dip-your-toes-in-the-sea-of-security-php-uk-2016-160219133447/75/Dip-Your-Toes-in-the-Sea-of-Security-PHP-UK-2016-27-2048.jpg)
![<?php
if (!$isPost) {
$csrfToken = base64_encode(random_bytes(32)));
$_SESSION['csrf_token'] = $csrfToken;
// ... output the form ...
echo '<input type="hidden" name="csrf_token" value="'.$csrfToken.'" />';
} else if ($isPost) {
if (hash_equals($_SESSION['csrf_token'], $_POST['csrf_token'])) {
die("Token invalid...");
}
// ... handle the form ...
}
Cross-Site Request Forgery / CSRF (#8)](https://image.slidesharecdn.com/dip-your-toes-in-the-sea-of-security-php-uk-2016-160219133447/75/Dip-Your-Toes-in-the-Sea-of-Security-PHP-UK-2016-28-2048.jpg)
![<?php
if (!$isPost) {
$csrfToken = base64_encode(random_bytes(32)));
$_SESSION['csrf_token'] = $csrfToken;
// ... output the form ...
echo '<input type="hidden" name="csrf_token" value="'.$csrfToken.'" />';
} else if ($isPost) {
if (hash_equals($_SESSION['csrf_token'], $_POST['csrf_token'])) {
die("Token invalid...");
}
// ... handle the form ...
}
Cross-Site Request Forgery / CSRF (#8)](https://image.slidesharecdn.com/dip-your-toes-in-the-sea-of-security-php-uk-2016-160219133447/75/Dip-Your-Toes-in-the-Sea-of-Security-PHP-UK-2016-29-2048.jpg)