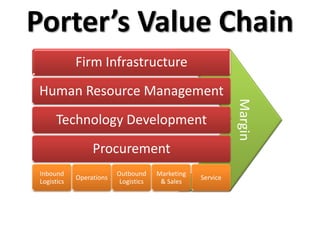
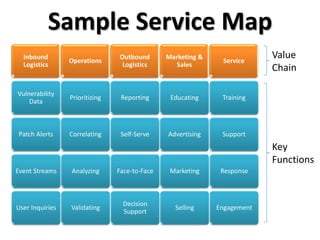
The document outlines a security value chain, emphasizing the importance of information as a raw material and the need for effective operations to add value to it. It discusses inbound and outbound logistics, marketing strategies for demand generation, and service metrics for maintaining customer relationships and brand strength. The metrics provided highlight trends in vulnerabilities, operations efficiency, engagement levels, and educational outreach in security practices.