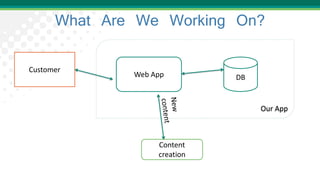
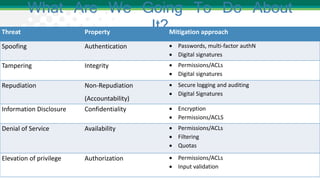
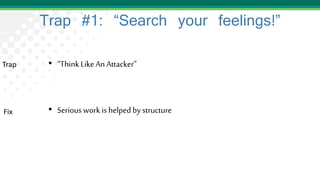
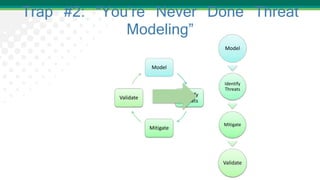
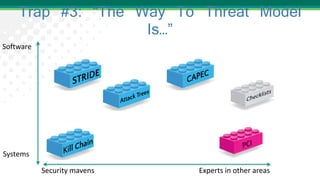
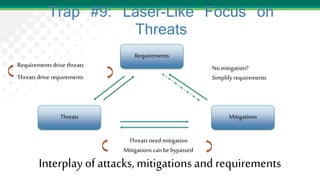
Adam Shostack presented on lessons learned from threat modeling. He discussed common traps to avoid, such as thinking threat modeling is easy or only for specialists. He outlined a simple approach using four questions: what are we working on, what can go wrong, what are we going to do about it, and how will we know if we're successful. Shostack also discussed the STRIDE mnemonic for categorizing threats and provided examples of mitigations for each category. His top ten lessons emphasized that anyone can threat model with the right skills and techniques.