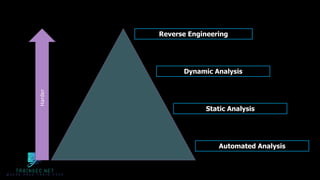
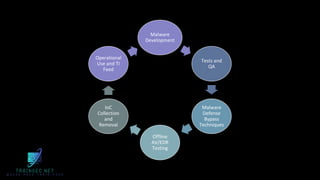
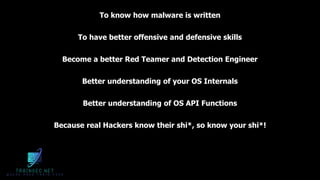
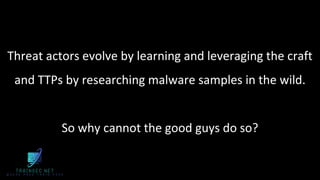
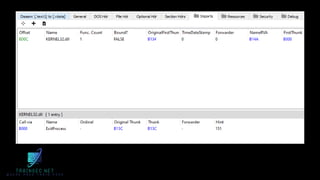
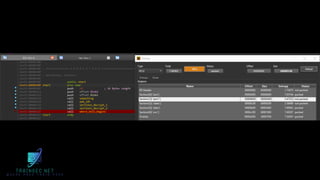
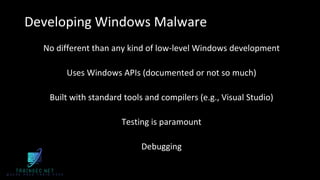
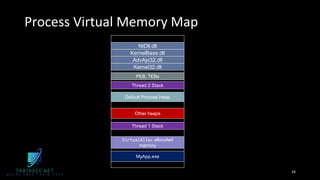
The document discusses malware analysis and development, highlighting their importance for improving offensive and defensive cybersecurity skills. It emphasizes learning from existing malware samples and understanding operating system internals to become more effective in red teaming and detection engineering. Additionally, it promotes a training academy offering courses in malware development with a discount for participants.