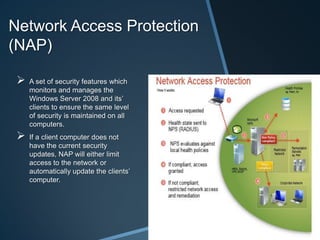
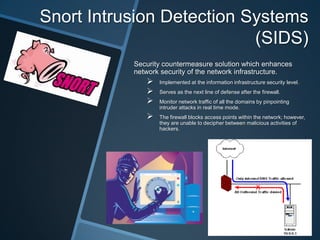
The document discusses security tools configured on Windows Server 2008 to maintain the integrity of Brooklyn Circus' business data and network. It describes the owners' concerns about confidential files and constant changes to financial information. Group policies, account policies, network access protection, intrusion detection systems, and intrusion prevention systems are implemented to prevent data breaches, corruption, and manipulation.