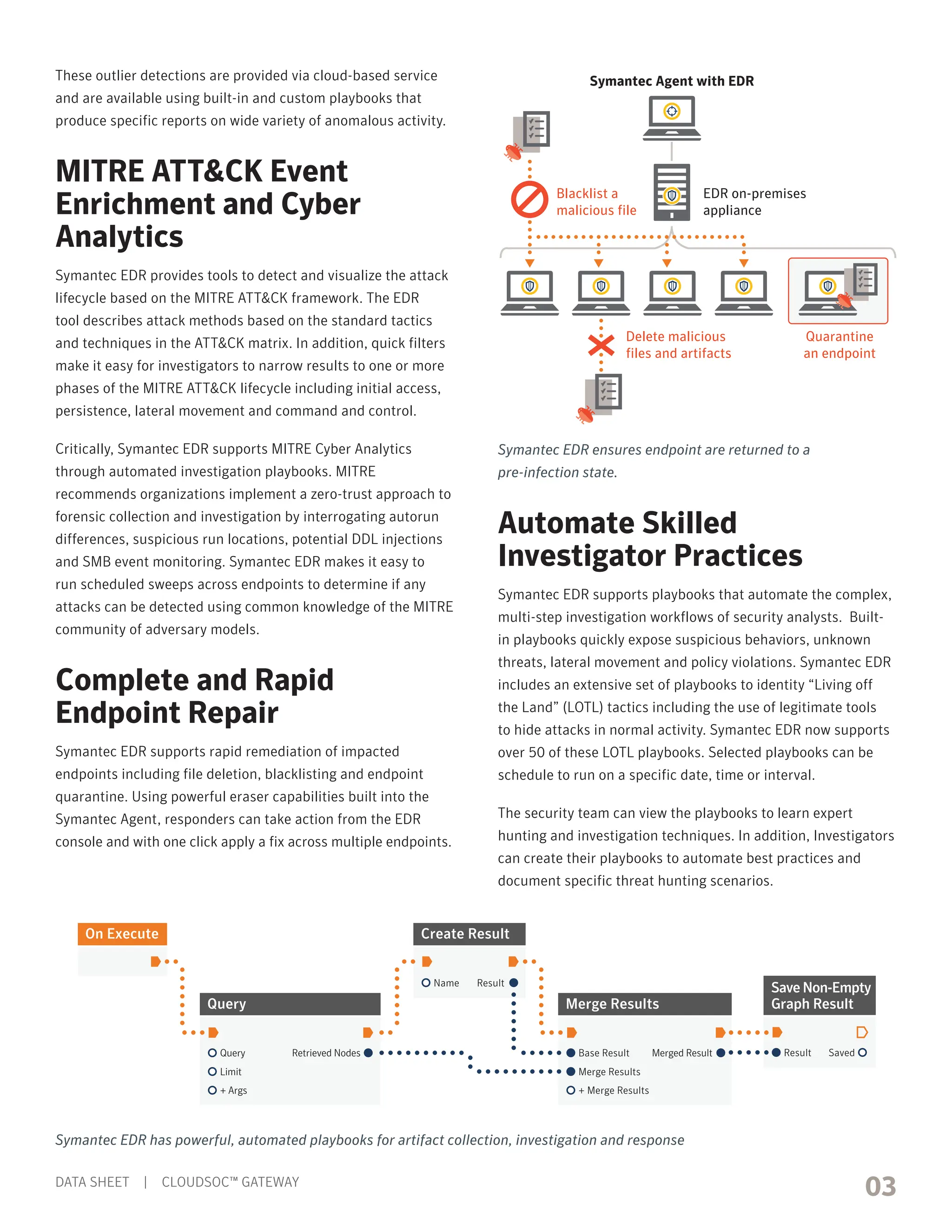
Symantec Endpoint Detection and Response (EDR) allows security teams to rapidly detect threats, investigate incidents, and remediate impacted endpoints through features like machine learning, global threat intelligence, automated playbooks, and memory analysis. EDR integrates with security tools to enhance visibility and automation. It can be deployed both on-premises and in the cloud to extend security for organizations of any size.