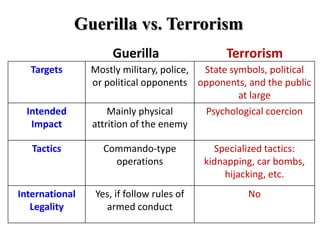
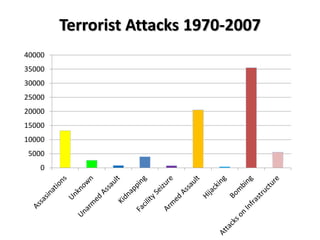
The document provides an overview of terrorism including its history, definitions, characteristics, objectives, tactics, US policy responses, and the future of terrorism. It discusses how terrorism has been used throughout history for political goals and how religious fundamentalism emerged as a primary force in the 1990s. It defines terrorism and outlines key criteria such as the use of violence, political goals, and targeting of civilians. The document also examines US national policy, military policy, and trends suggesting terrorism may become more catastrophic and network-based over time.