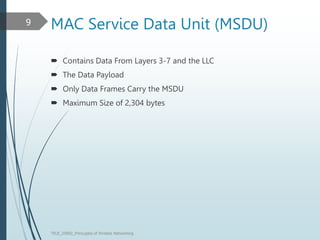
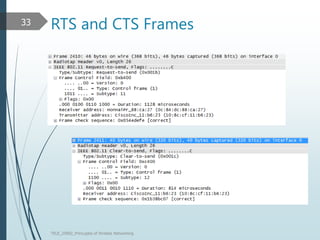
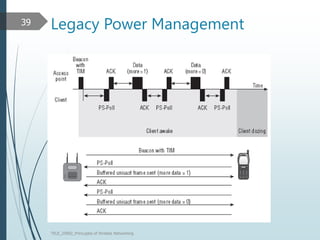
This document discusses the IEEE 802.11 MAC architecture. It describes the frame types, authentication and association processes, and power management techniques in wireless networks. Management frames like beacons are used to broadcast network information during scanning. Authentication establishes the identity of stations, while association allows stations to use network resources. Control frames provide functions like acknowledging frames and protecting transmissions. Power management helps conserve battery life for mobile devices.


![Reference/Reading
Reading:
Ch 10 [COL3]
Reference:
Most of the slides are taken from the text book
Web reference:
See inline
TELE_25892_Princuples of Wreless Networking
3](https://image.slidesharecdn.com/tele25892-4-230326214728-cc427483/85/TELE25892-4-3-802-11-MAC-Architecture-pptx-3-320.jpg)