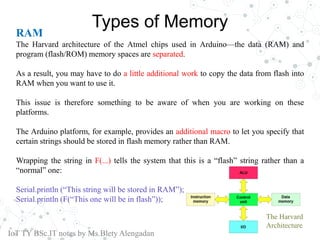
Chapter 08 explores memory management in IoT, detailing types of memory such as ROM, flash, and RAM, and the importance of efficient memory use in constrained devices. It emphasizes the need for optimizing performance and battery life by adopting event-driven models, careful variable management, and leveraging libraries suited for embedded systems. Additionally, it discusses debugging techniques and best practices for improving embedded coding efficiency.