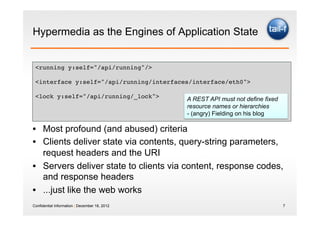
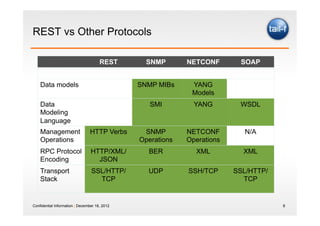
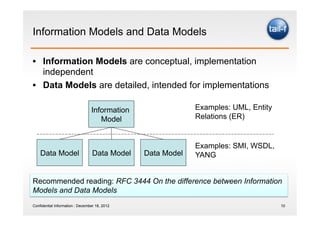
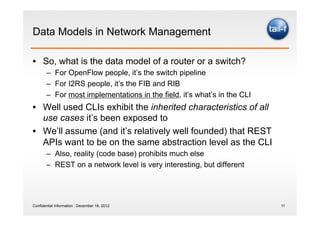
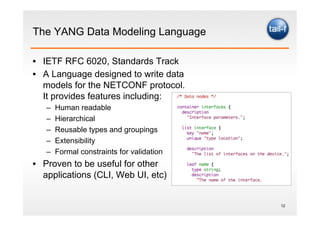
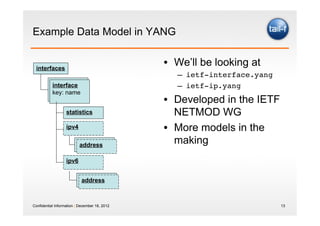
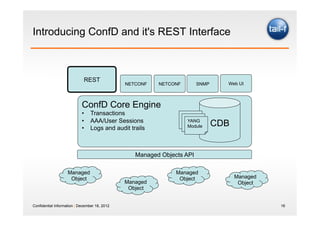
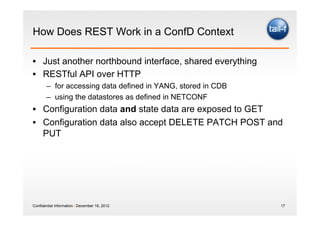
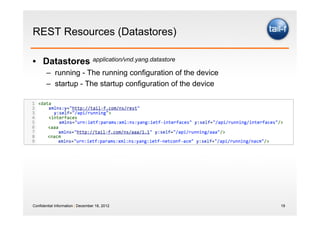
The document discusses the application of the REST architectural style in network management, highlighting its constraints and principles such as uniform interfaces and statelessness. It explains how REST can be utilized to read and write data to network elements and details the mapping of YANG data modeling language to REST resources. The presentation also emphasizes REST's advantages for scripting and the challenges it presents in multi-parameter environments.



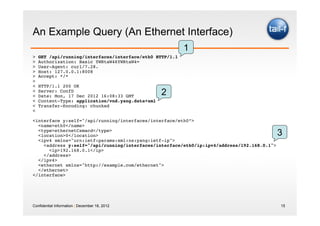
![Resources Have Unique Identifiers (e.g. URIs)
GET /api/running/interfaces/interface/eth0/ipv4 HTTP/1.1!
!
<ipv4 y:self="/api/running/interfaces/interface/eth0/ip:ipv4”>!
<address y:self=”[...]">!
<ip>192.168.0.1</ip>!
...!
!
• Individual resources are identified in requests using URIs
• Resources are conceptually separate from the
representations
• Resource representations depend on query and server
support (e.g. XML and JSON)
Confidential Information | December 18, 2012 4](https://image.slidesharecdn.com/tail-frestwebinar-121223042657-phpapp01/85/Webinar-Applying-REST-to-Network-Management-An-Implementor-s-View-5-320.jpg)
![Manipulation of Representations
< Content-Type: application/vnd.yang.data+xml!
!
<ipv4 y:self="/api/running/interfaces/interface/eth0/ip:ipv4”>!
<address y:self=”[...]">!
<ip>192.168.0.1</ip>!
</address>!
</ipv4>!
• Representations (including metadata) contain enough
information to be modified or deleted
• Provided that the client has permission to do so
Confidential Information | December 18, 2012 5](https://image.slidesharecdn.com/tail-frestwebinar-121223042657-phpapp01/85/Webinar-Applying-REST-to-Network-Management-An-Implementor-s-View-6-320.jpg)