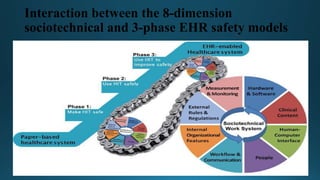
The document discusses confidentiality in healthcare workplaces. It notes that sharing patient personal or medical information without permission causes confidentiality, work-related, and trust issues. It recommends conducting ongoing training on confidentiality for healthcare employees and implementing necessary hardware and software to protect against breaches of confidentiality. The document emphasizes that while electronic health records and discussions of patient care are needed, they must be handled professionally without jeopardizing patients' trust, care, or confidentiality.