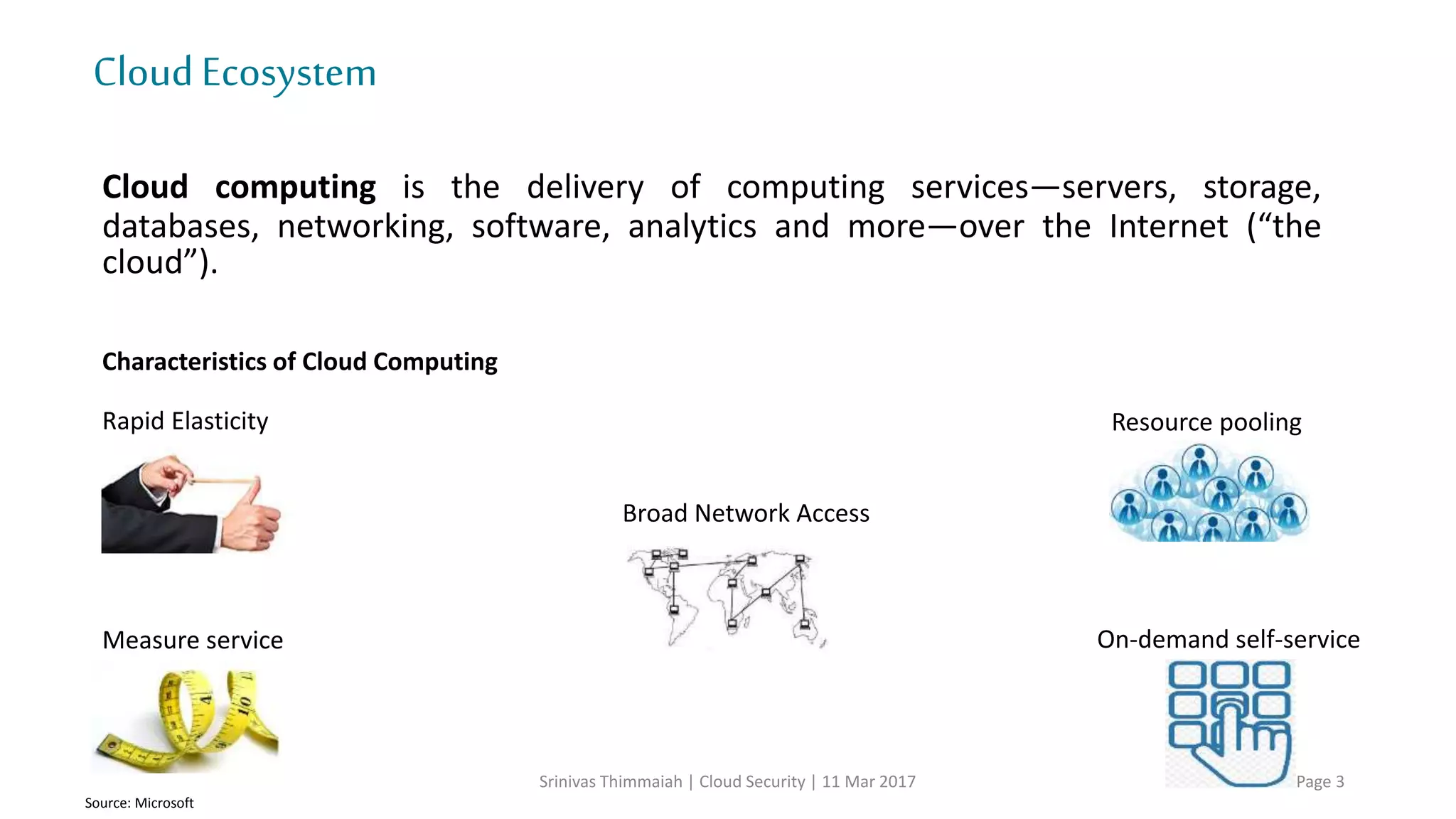
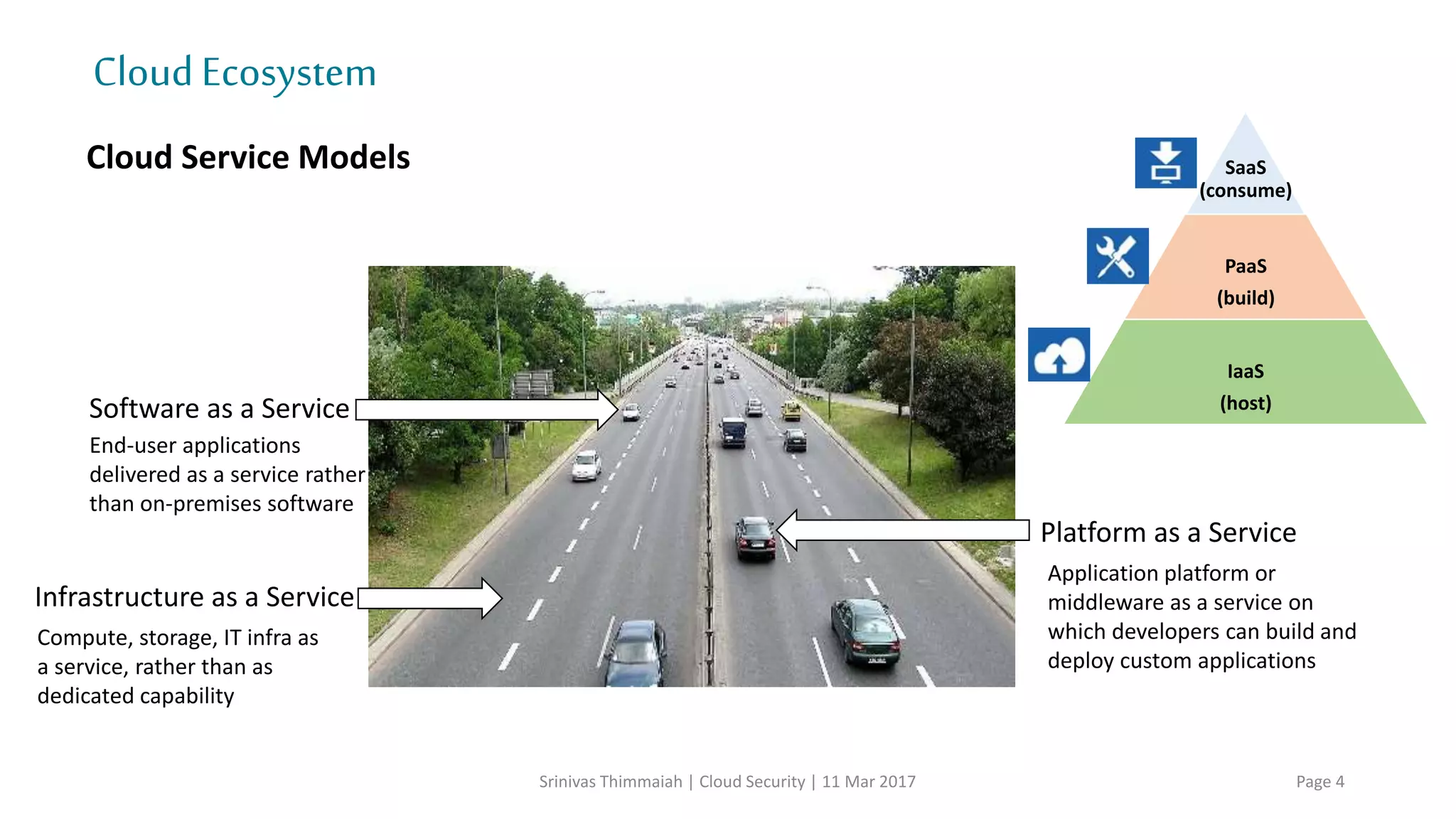
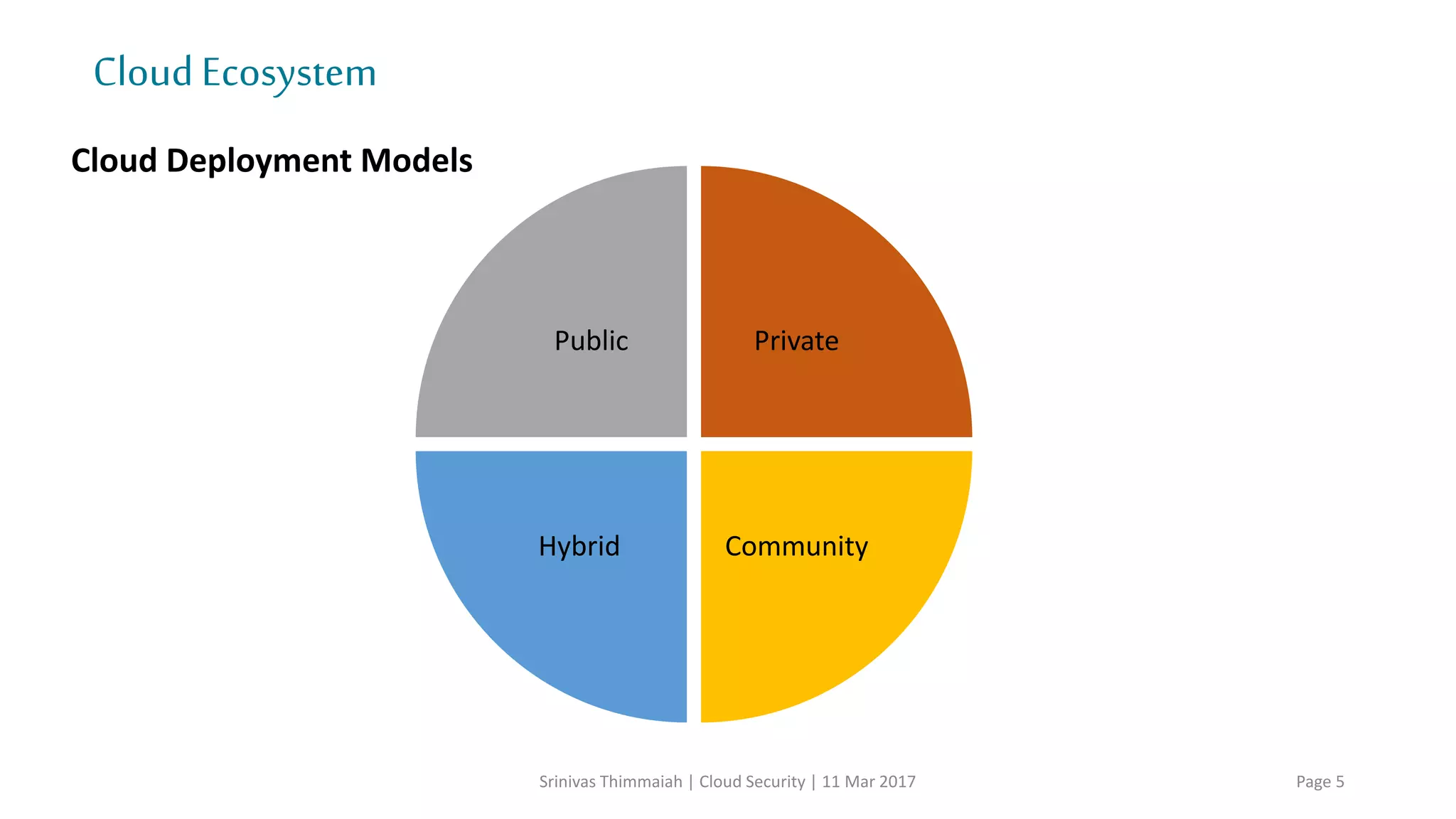
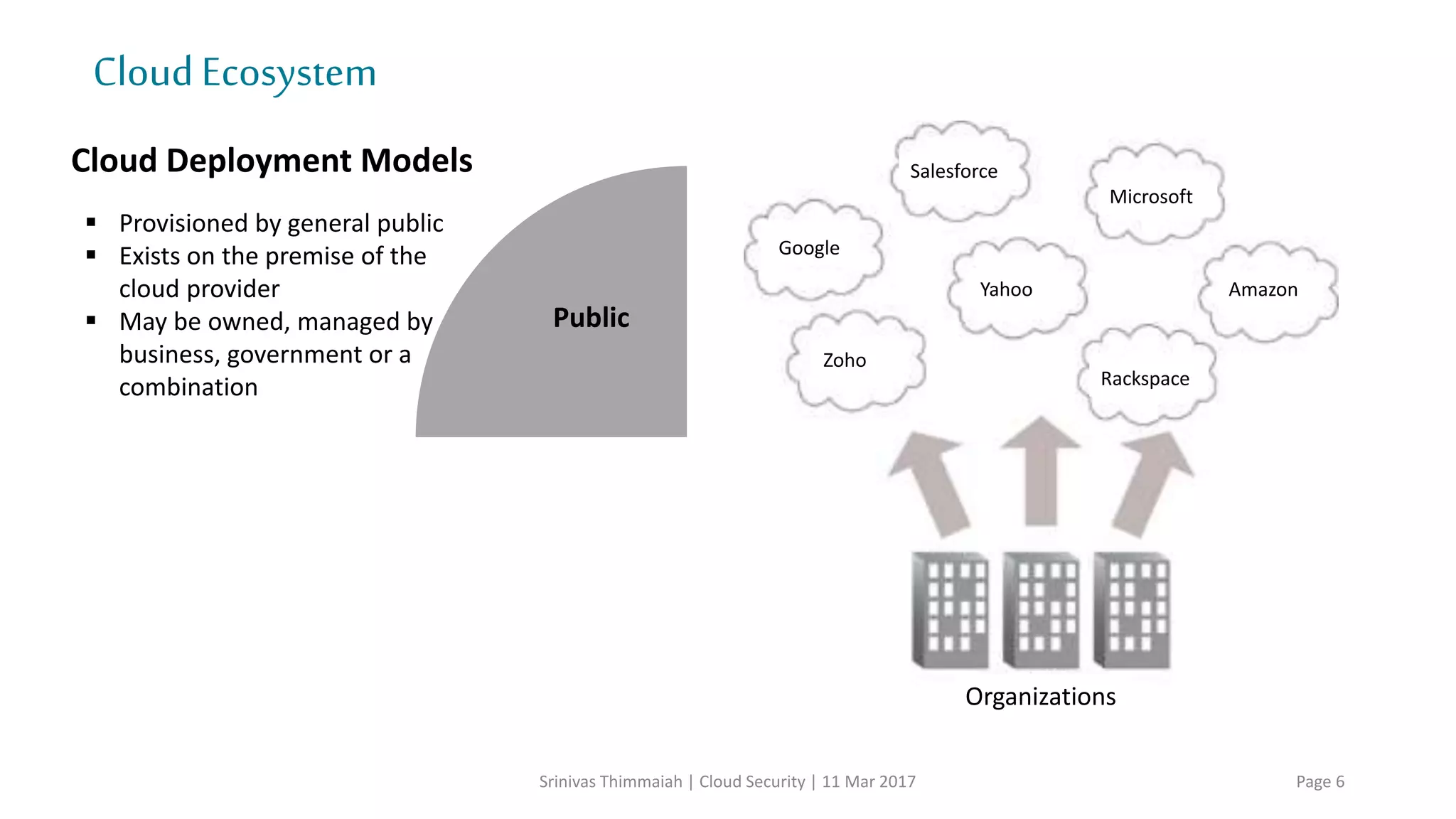
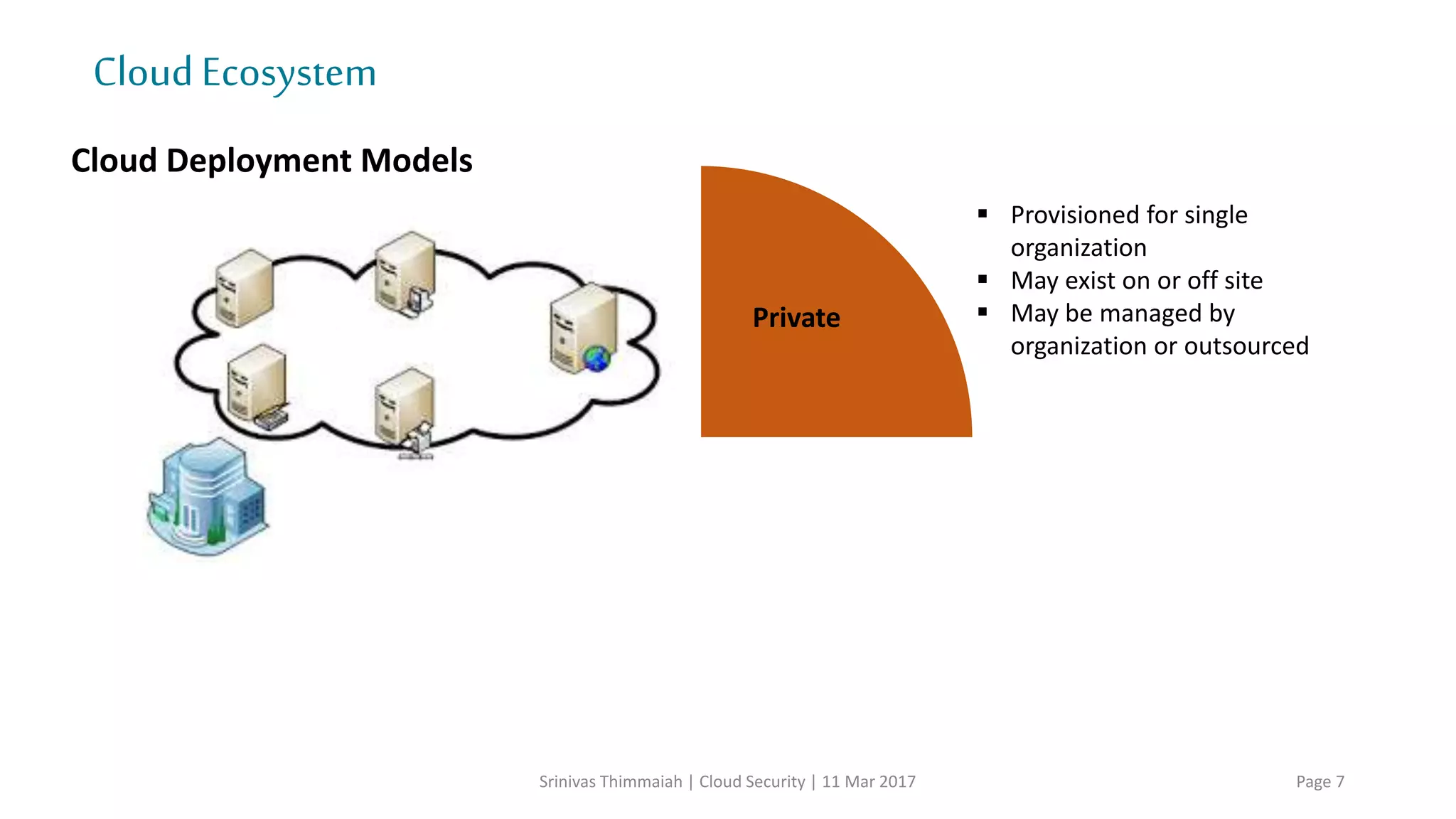
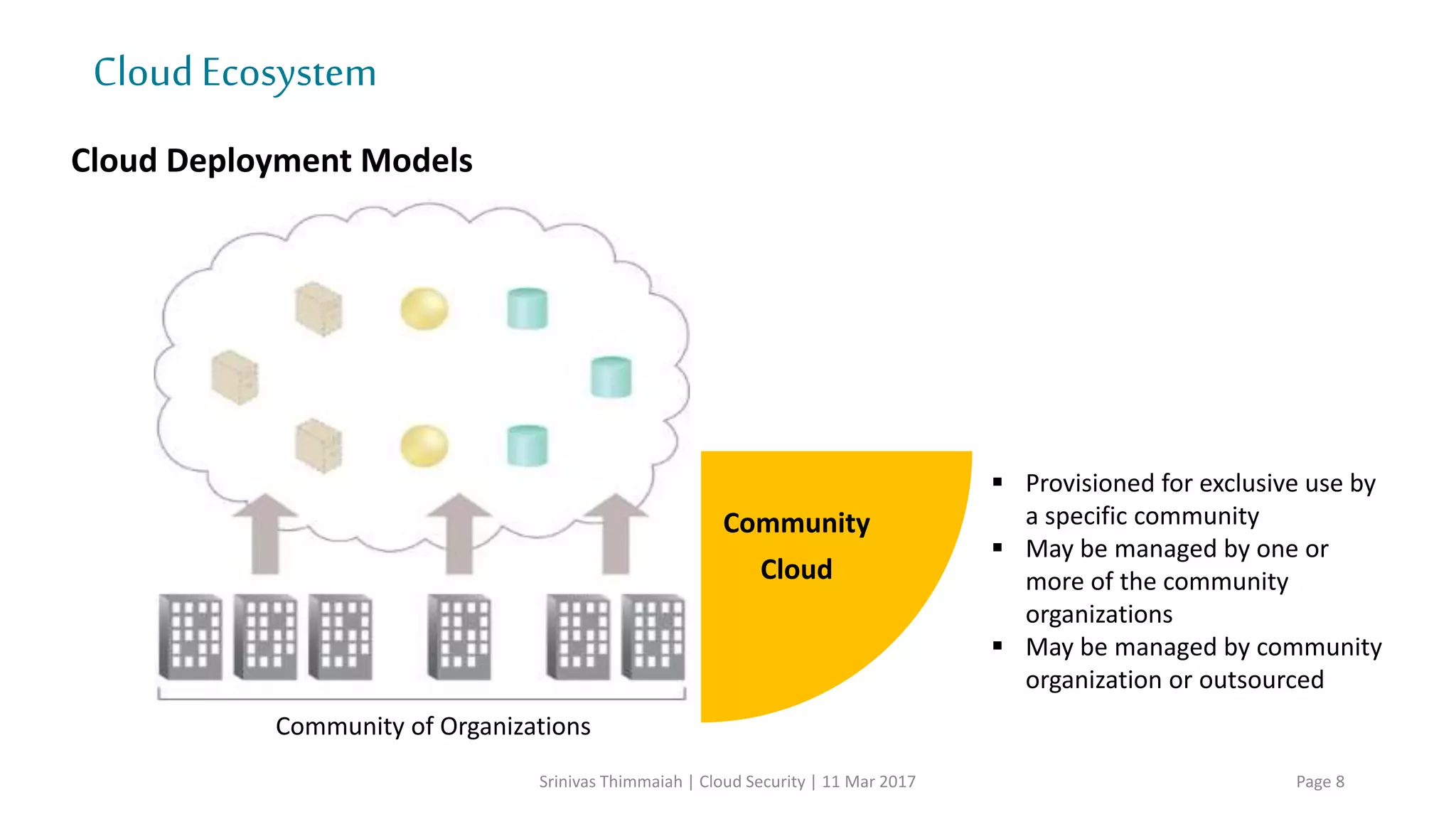
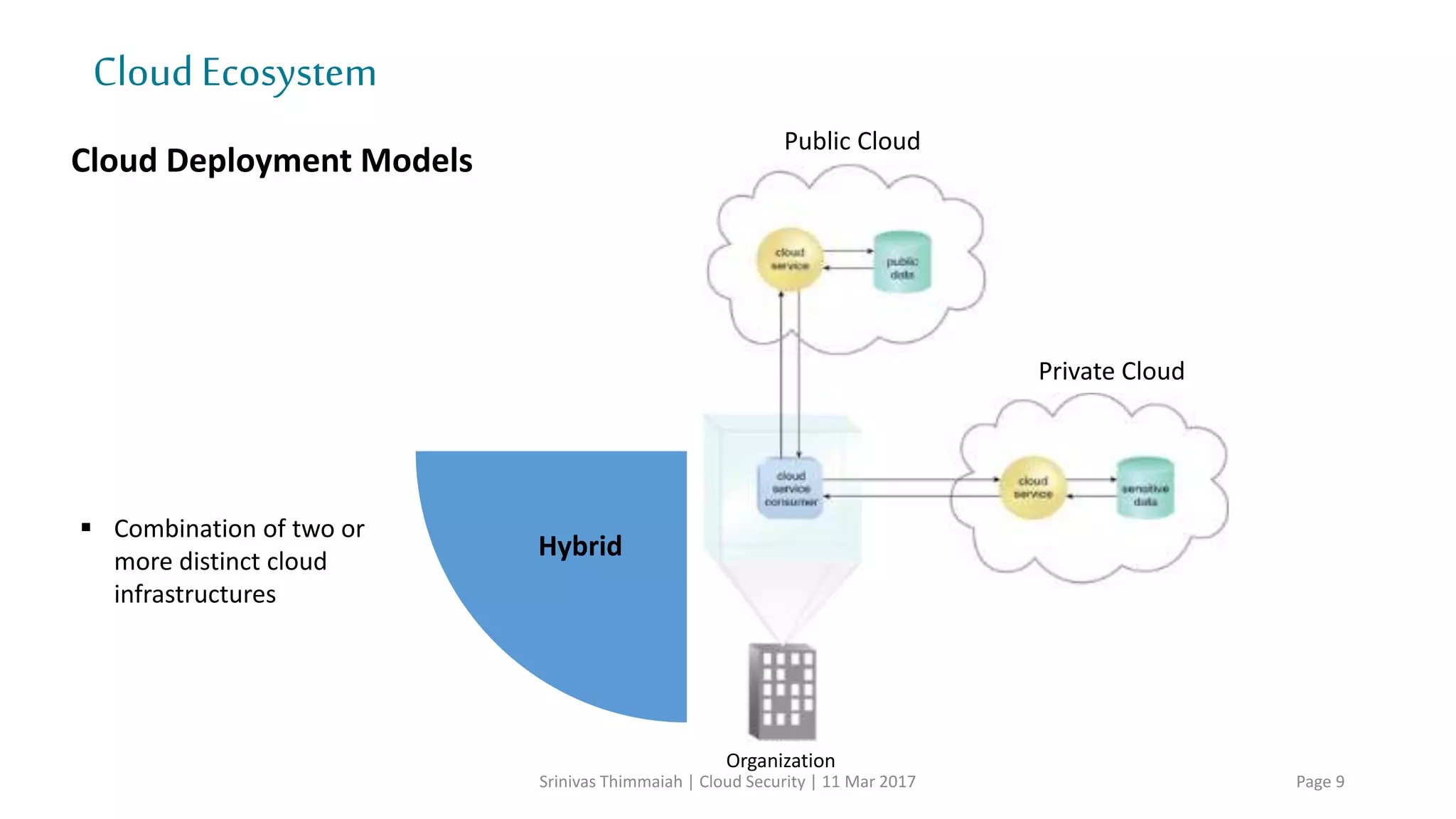
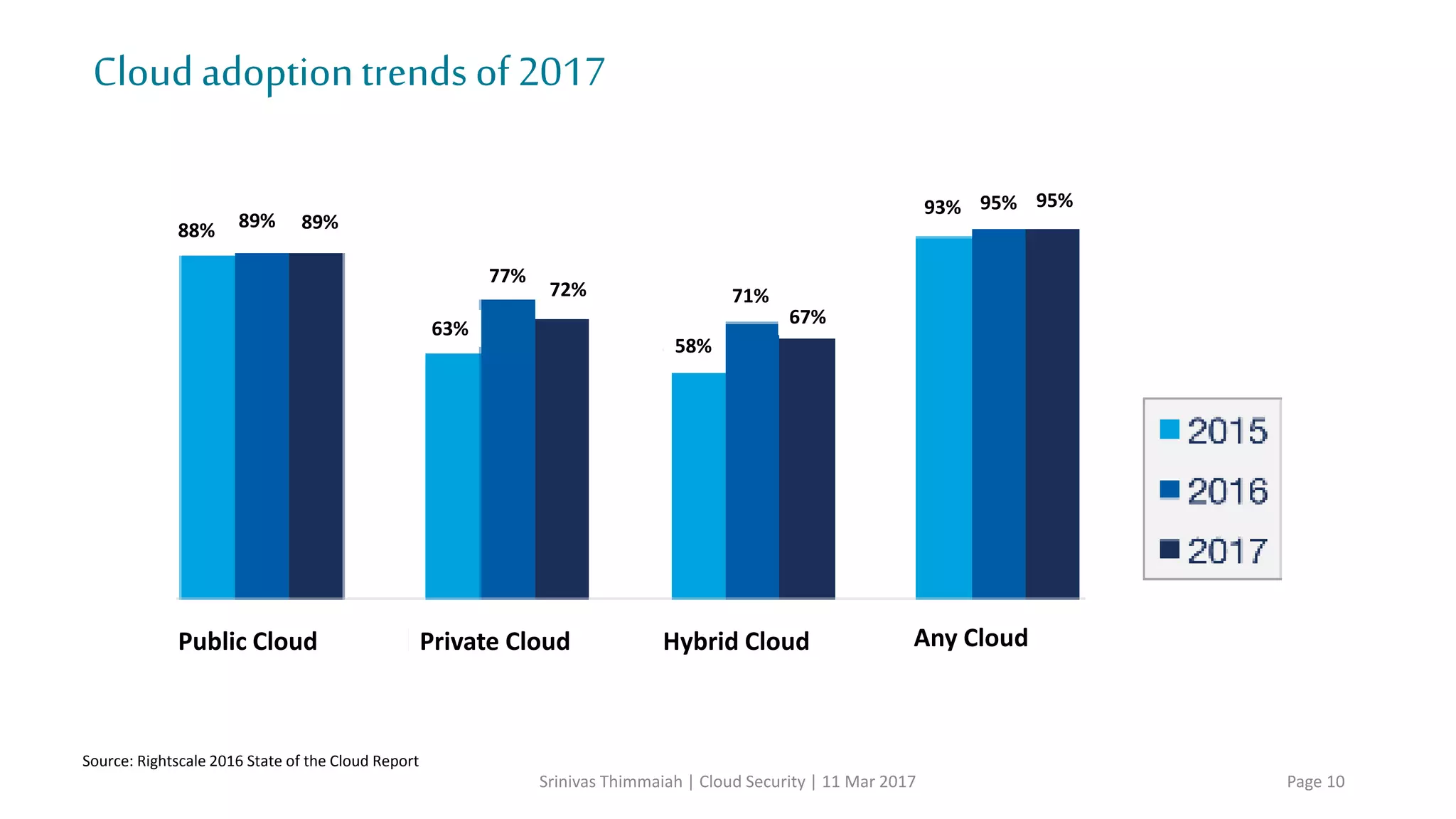
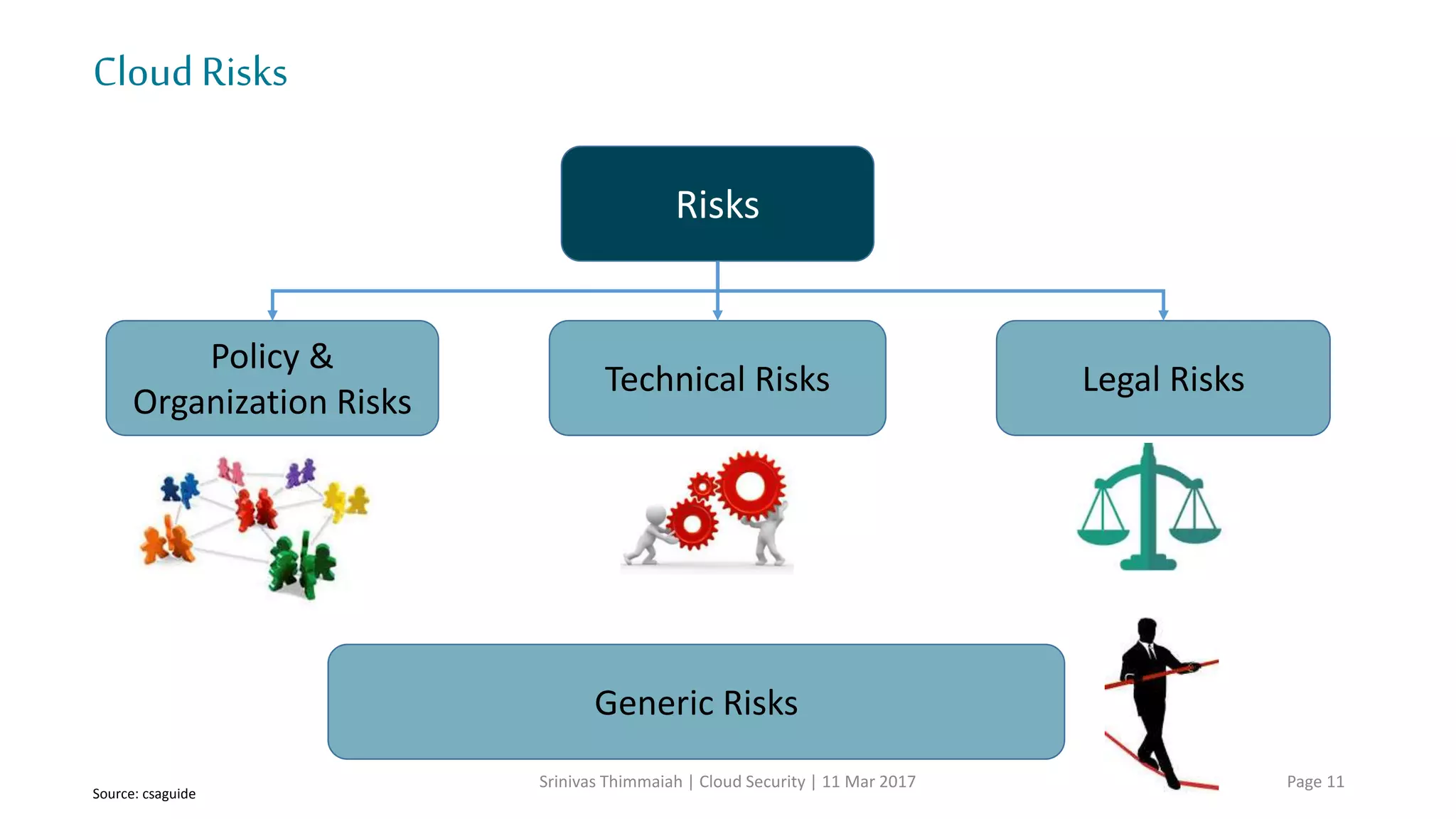
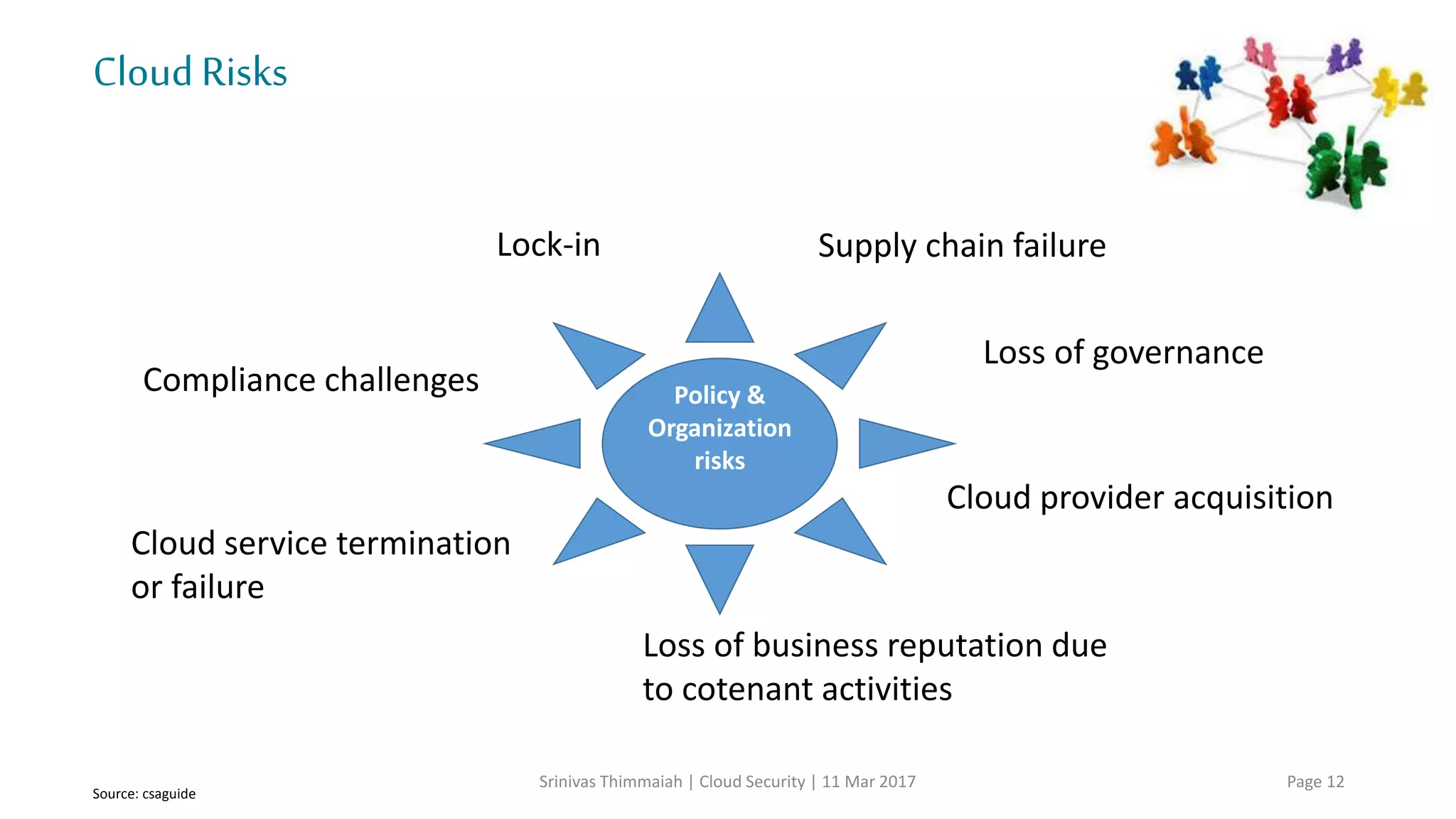
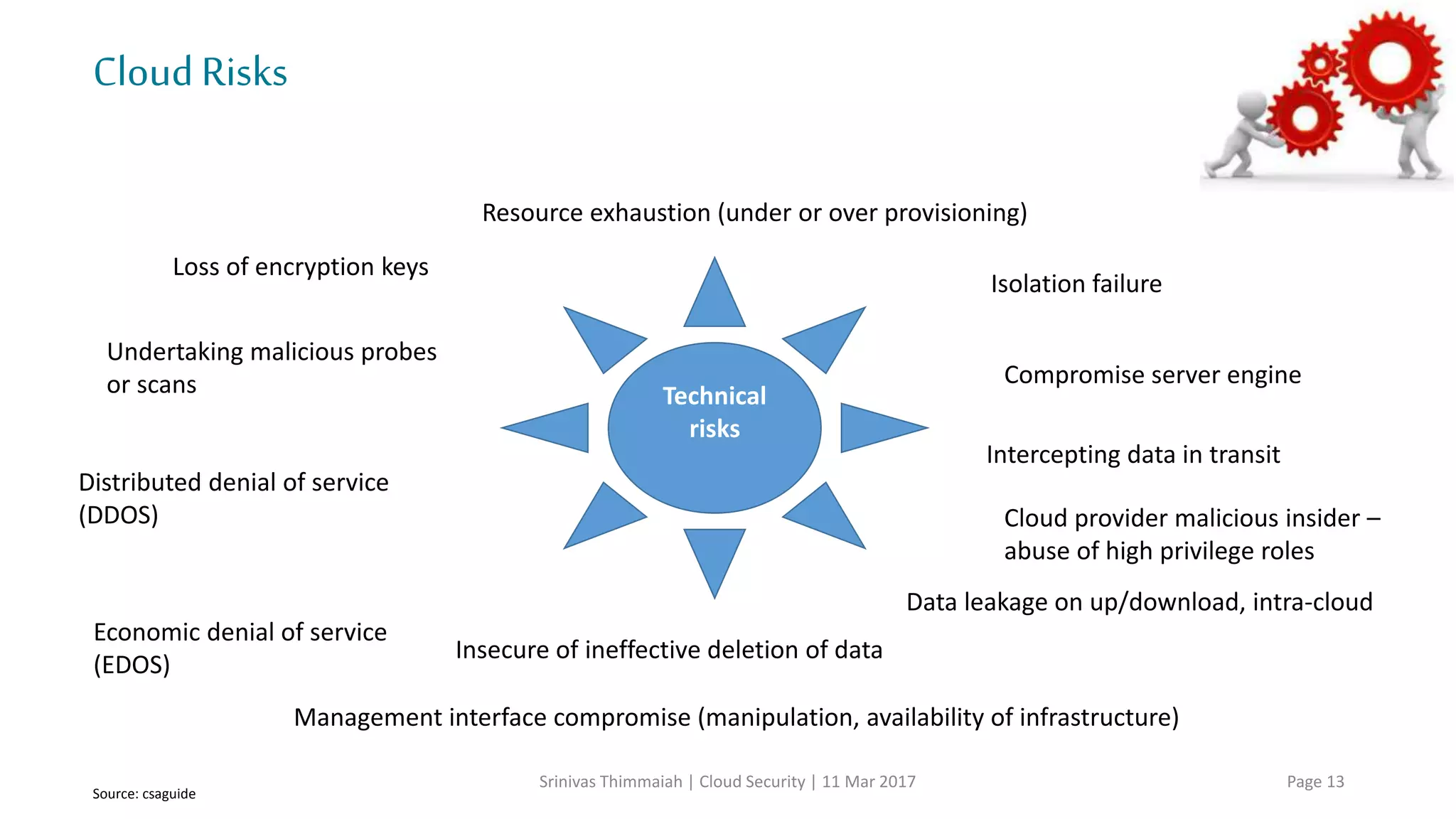
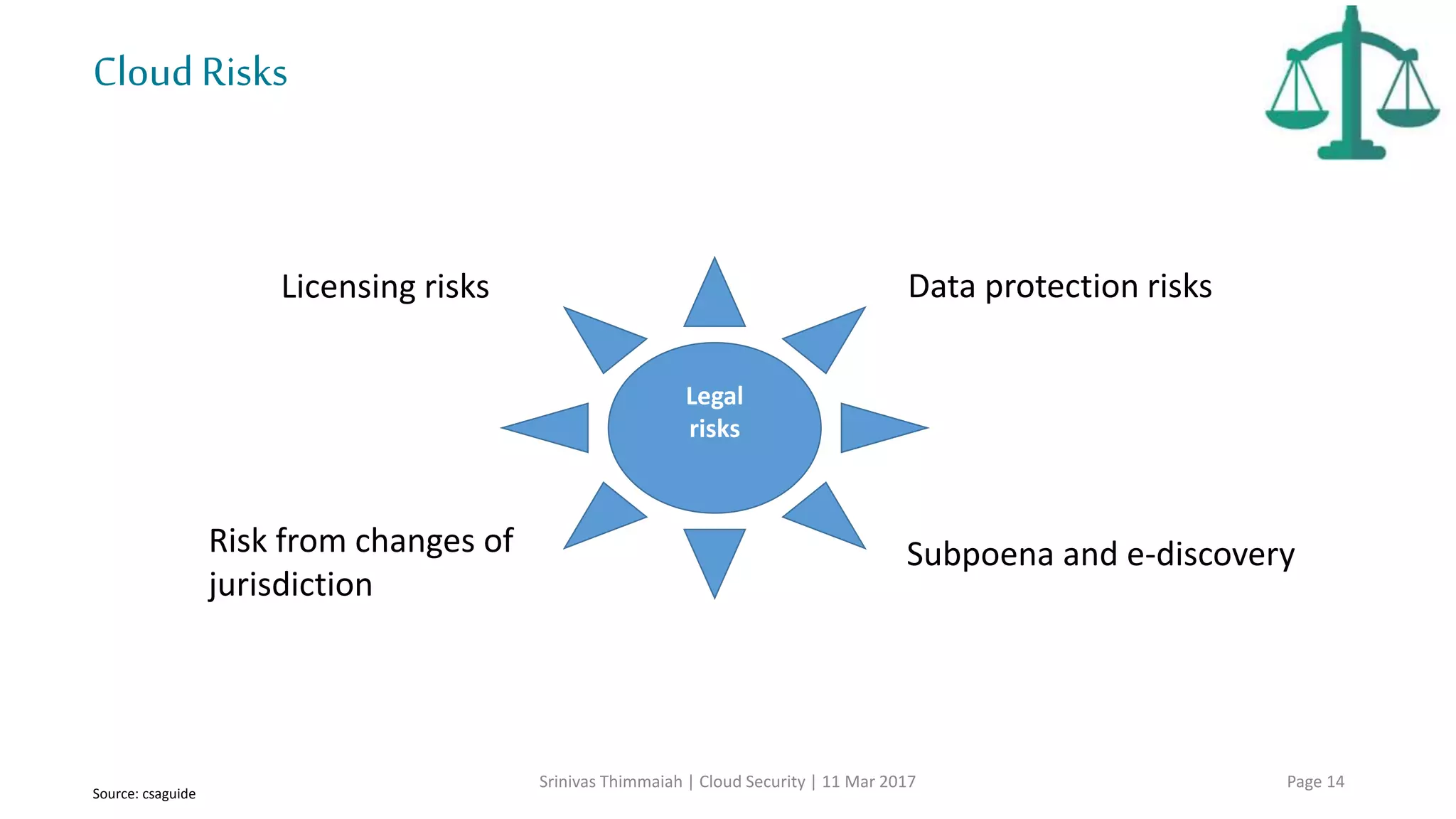
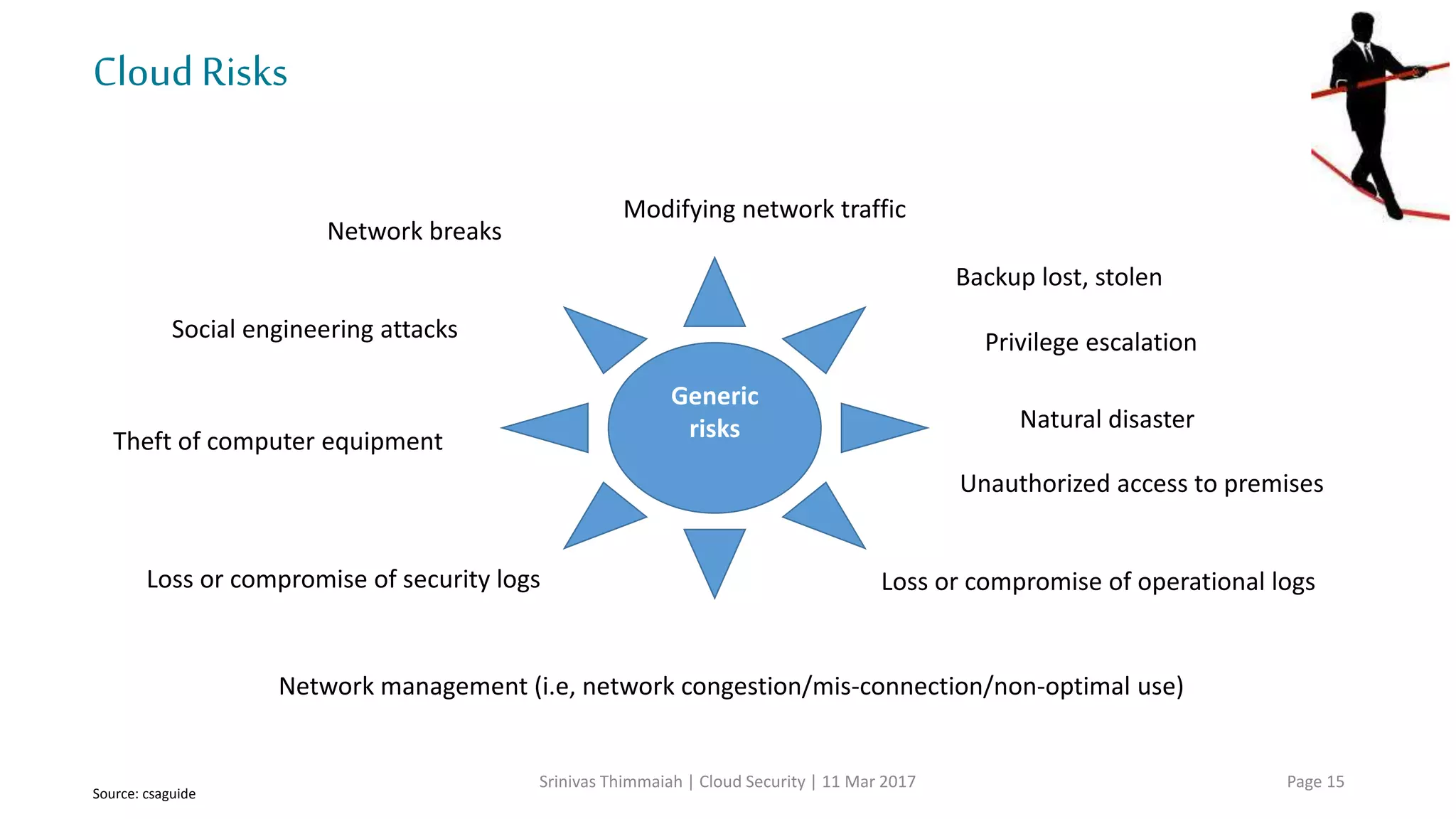
The document discusses cloud security and the risks associated with cloud adoption. It begins with an introduction to cloud computing models including infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS). The document then outlines public, private, community, and hybrid cloud deployment models and trends in cloud adoption for 2017. It identifies policy/organization, technical, legal, and generic risks of cloud computing and concludes with recommendations around effective onboarding, vendor analysis, risk management and contract management when adopting cloud services.