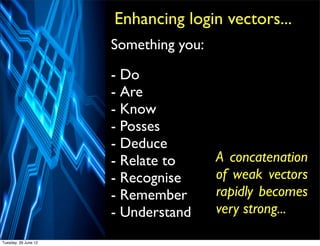
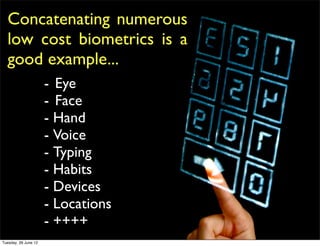
The document discusses the evolving landscape of security, emphasizing that threats are constant, often unexpected, and rely heavily on human behavior. It outlines key laws of security, the necessity for advanced and varied defenses in the cloud, and the increasing collaboration among criminals and governmental threats. To mitigate risks, organizations must adopt dynamic, multi-supplier approaches and rethink their security strategies extensively.