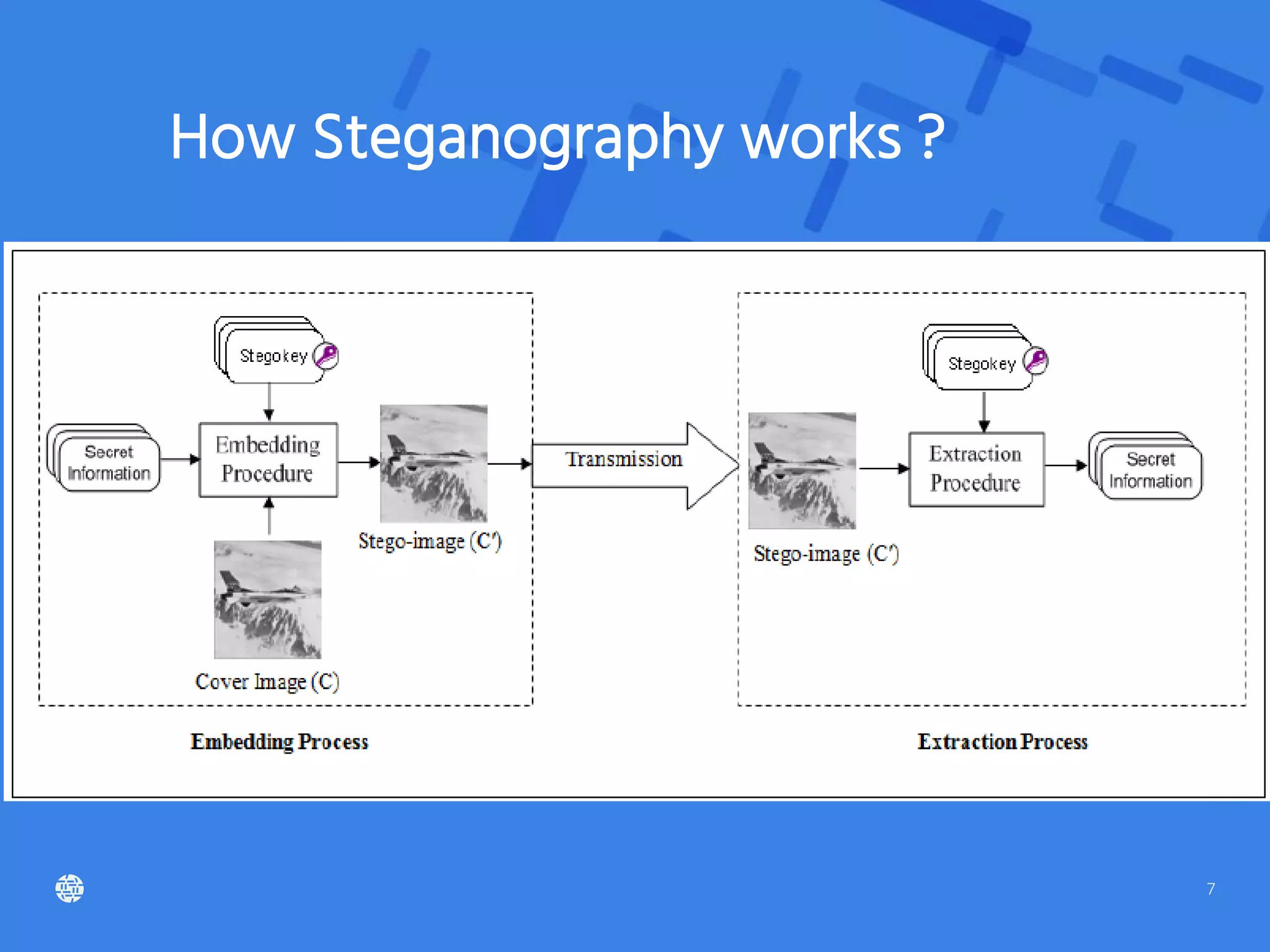
Steganography is the practice of hiding secret data within ordinary files like images, audio, or video. It works by embedding messages in parts of the digital files that are ignored or discarded by compression algorithms. Common uses include governments hiding sensitive data, digital watermarking for businesses, and individuals secretly communicating. Steganography tools hide messages in files while steganalysis tools try to detect and decode any hidden data. When combined with cryptography, steganography provides better protection of secret communications than either method alone.