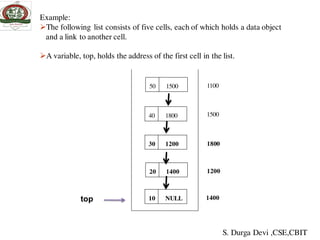
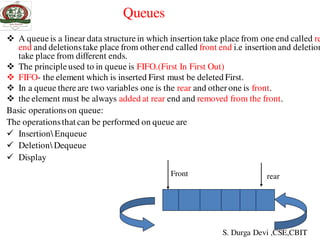
The document discusses stacks and queues. It begins by defining a stack as a collection of homogeneous data elements where insertion and deletion occurs at one end, known as the top. The stack follows the LIFO (last in, first out) principle. Common stack operations like push and pop are introduced. Implementing stacks using both arrays and linked lists is covered. Applications of stacks like balancing symbols, recursion, undo operations are mentioned. The document then moves to discussing queues, their applications and implementations. Priority queues and their applications are also briefly covered.




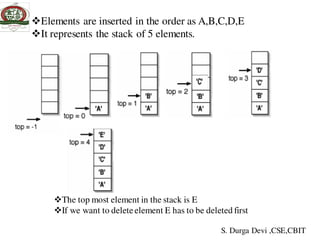
![ADT For Stack
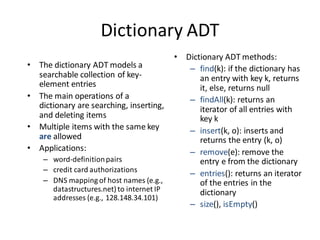
ADT for stack
int stack[5],top;
void push();
void pop();
void display();
int size();
void isEmpty();
void isFull();
S. Durga Devi ,CSE,CBIT](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-8-320.jpg)

![Implementing stack using arrays
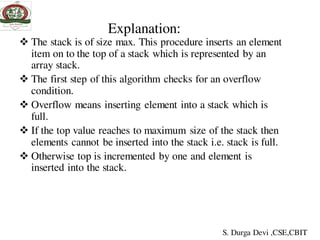
Algorithm for inserting element into the stack:
Algorithm push()
1. if top=(SIZE-1)
then write (‘stack overflow’)
else
2. read item or data
3. top←top+1
4. stack[top]← item
5. stop
S. Durga Devi ,CSE,CBIT](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-10-320.jpg)
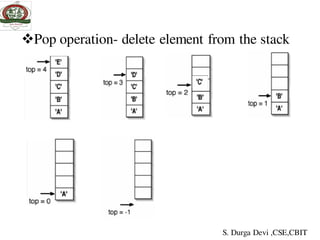
![Algorithm to delete elements from the stack:
Algorithm pop()
1. if top=-1
then write (‘stack underflow’)
else
2. item ← stack[top]
3. top ← top-1
S. Durga Devi ,CSE,CBIT](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-12-320.jpg)

![Display of stack:
Printing the contents of stack after push and pop
operations.
Algorithm print()
1. if top=-1
then write (‘stack empty’)
2. Repeat for i ← top to 0
print(stack[i])
3. stop
S. Durga Devi ,CSE,CBIT](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-14-320.jpg)








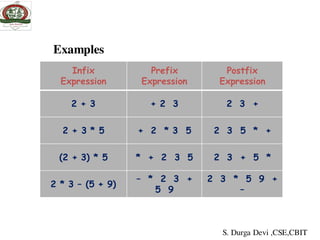





![#include<stdio.h>
#include<ctype.h>
#include<string.h>
int priority(char c);
int push(char c);
int pop();
static char str[30];
int top=-1;
void main()
{
char in[30],post[30],ch;
int i,j,l;
printf("enter the string");
gets(in);
l=strlen(in);
Write a C program to convert infix to postfix evaluation
S. Durga Devi ,CSE,CBIT](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-35-320.jpg)
![for(i=0,j=0;i<l;i++){
if((isalpha(in[i]))||(isdigit(in[i])))
post[j++]=in[i];
else
{
if(in[i]=='(')
push(in[i]);
else if(in[i]==')')
while((ch=pop())!='(')
post[j++]=ch;
else
{
while(priority(in[i])<=priority(str[top]))
post[j++]=pop();
push(in[i]);
}}}while(top!=-1)
post[j++]=pop();
post[j]='0';
printf("n equivalent infix to postfix
is:%s",post);
int priority (char c)
{
switch(c)
{
case'+':
case'-': return 1;
case'*':
case'/':
return 2;
case'$':return 3;
case '^':return 4;
}
return 0;
}
int push(char c)
{str[++top]=c;
}
pop()
{
return(str[top--]);
}
S. Durga Devi ,CSE,CBIT](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-36-320.jpg)





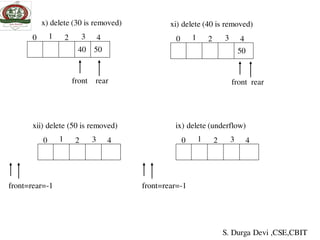
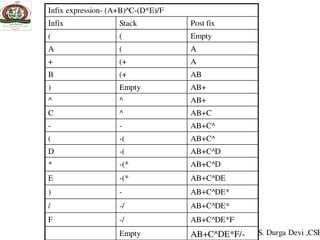
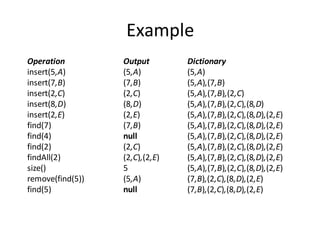
![Implementation of queue using array
Algorithm insert( )
1. If rear ≥ size-1
then write (‘overflow’)
2. Read item
3. rear← rear + 1
4. queue[rear]← item
5. If(front==-1)
6. front++;
7. stop
Explanation:
This procedureadds an element item to the
queue.
First it checks for an overflow condition.
If the rear value reaches or exceeds size of th
queue
then elements cannot be inserted into the queue
ie. Overflow.
Whenever element is inserted into the queue,
rear is increment by one
and place the element in the location
where rear is pointing.
S. Durga Devi ,CSE,CBIT](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-48-320.jpg)
![Algorithm to delete element from the queue
Algorithm delete()
1. If (front= = -1)or (front> rear)
then write (‘queueunderflow’)
item ← queue[front]
2. front ← front + 1
Explanation:
This procedure deletes an element from the queue.
The first step of this algorithm checks for underflow condition.
If the front value is -1or greater than rear then queue is empty.
Take out the element from the location where, the front is pointing and
store it in the variable, then increment front by one.
S. Durga Devi ,CSE,CBIT](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-49-320.jpg)
![Algorithm to display elements in a queue
1. if((front==-1)||(front>rear))
1.1 print statck is Underflow
2. Else
2.1 repeat for i->front to rear
2.2. print queue[i];
Drawback in queue
In a queue when the rear pointer reaches to the end of the queue,
insertion would be denied even if room is available at the front
one way to remove this is using the circular queue
S. Durga Devi ,CSE,CBIT](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-50-320.jpg)
![Program: implementation of queue using array
# include <stdio.h>
# define size 4
void insertion();
void deletion();
void display();
int front=-1,rear=-1,item,choice,queue[size];
void main()
{clrscr();
while(1)
{
printf("n*** MENU ***n 1. INSERTIONn 2. DELETIONn
3.TRAVERSEn 4. EXITn");
printf("enter your choice:");
scanf("%d",&choice);
switch(choice)
{
case 1:insertion();
break;
case 2:deletion();
break;
case 3:display();
break;
case 4:exit();
default:printf("*** wrong choice ***n");}}}
S. Durga Devi ,CSE,CBIT](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-51-320.jpg)
![void insertion()
{
if(rear>=size-1)
printf("*** queue is full ***n");
else
{
printf("enter item into queue:");
scanf("%d",&item);
rear++;
queue[rear]=item;
if(front==-1)
front++;
} }
void deletion()
{
if((front==-1)||(front>rear))
printf("*** queue is empty ***n");
else
{
item=queue[front];
front++;
printf("the deleted item from queue is
%dn",item);
}
}
void display(){
int i;
if((front==-1)||(front>rear))
printf("*** queue is empty ***n");
else
{
printf("n elements in queue:- ");
for(i=front;i<=rear;i++)
printf("%d ",queue[i]);
}} S. Durga Devi ,CSE,CBIT](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-52-320.jpg)
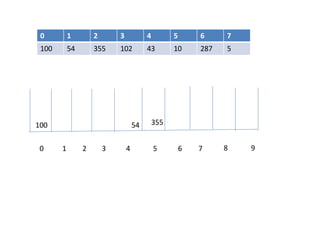
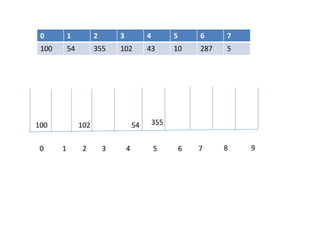
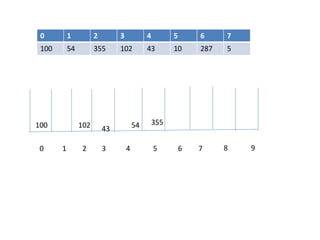
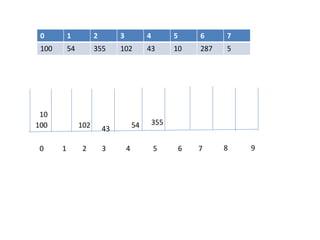
![EMPTY QUEUE
Circular queues
Q[0] Q[1] Q[2] Q[3] Q[N]
Delete element 5S. Durga Devi ,CSE,CBIT](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-53-320.jpg)
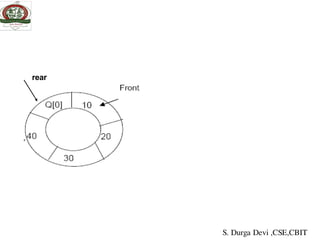

![Implementation of circular queue using array
• Algorithm for insertion
1.if((front == 0 && rear == SIZE-1) || (front == (rear+1)%size)
2.printf("Queue Overflow n");
return;
3.if (front == -1) /*If queue is empty */
3.1 front = 0;
3.2 rear = 0;
4.else
5.if(rear == SIZE-1)/*rear is at last position of queue */
6.rear = 0;
7. else
8.rear = rear+1;
9.Read item
10.cq[rear] = item ;
11.end
S. Durga Devi ,CSE,CBIT](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-56-320.jpg)

![int insert(){
int item;
if((front == 0 && rear == SIZE-1) || (front == rear+1))
{
printf("Queue Overflow n");
return;}
if (front == -1) /*If queue is empty */
{
front = 0;
rear = 0;
}
else
if(rear == SIZE-1)/*rear is at last position of queue */
rear = 0;
else
rear = rear+1;
printf("Input the element for insertion in queue : ");
scanf("%d", &item);
cq[rear] = item ;
printf("the element %d at %d position and
front=%d,rear=%dn",cq[rear],rear,front,rear);
return;
}/*End of insert()*/
S. Durga Devi ,CSE,CBIT](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-58-320.jpg)
![int del()
{
if (front == -1)
{
printf("Queue Underflown");
return ;
}
printf("Element deleted from queue is :
%dn",cq[front]);
if(front == rear) /* queue has only one
element */
{
front = -1;
rear=-1;
}
else
if(front == SIZE-1)
front = 0;
else
front = front+1;
printf("front=%d,rear=%dn",front,rear)
;
return;
}/*End of del() */
Deletion
S. Durga Devi ,CSE,CBIT](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-59-320.jpg)
![display()
int display(){
int front_pos = front,rear_pos = rear;
if(front == -1){
printf("Queue is emptyn");
Return;}
printf("Queue elements :n");
if( front_pos <= rear_pos )
while(front_pos <= rear_pos){
printf("%d ",cq[front_pos]);
front_pos++;}
else{
while(front_pos <= SIZE-1){
printf("%d ",cq[front_pos]);
front_pos++;}
front_pos = 0;
while(front_pos <= rear_pos){
printf("%d ",cq[front_pos]);
front_pos++;}}/*End of else */
printf("n");
return;
}/*End of display() */
S. Durga Devi ,CSE,CBIT](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-60-320.jpg)




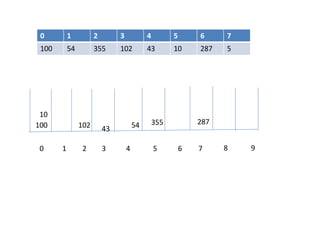
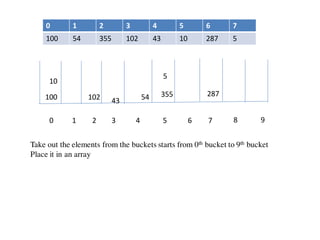
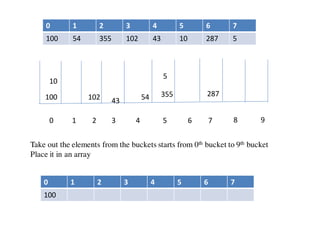
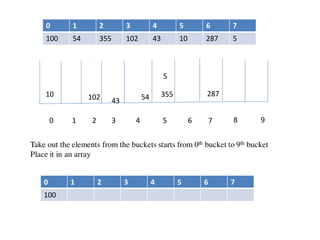
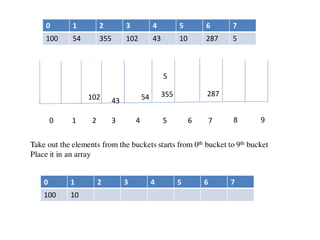
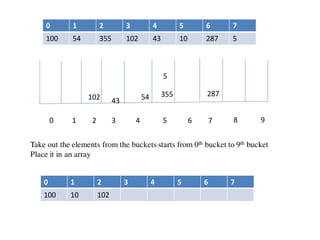
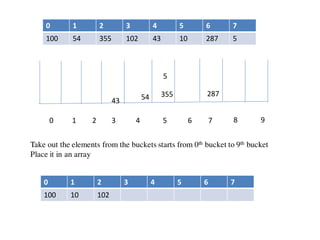
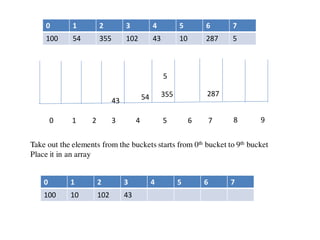
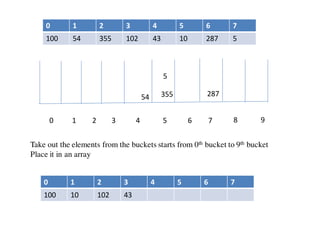
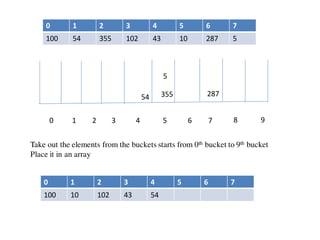
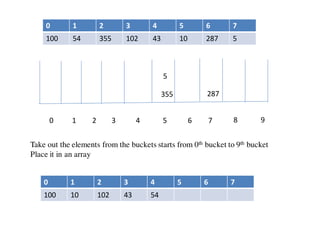
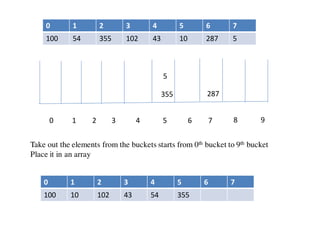
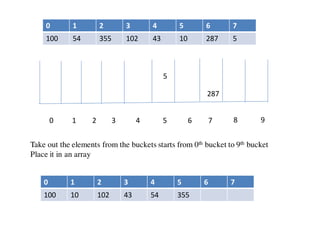
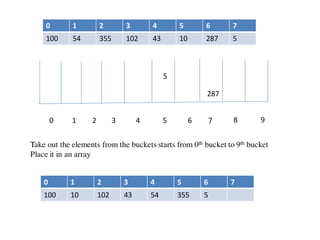
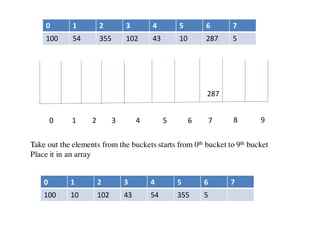
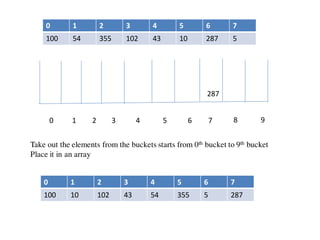

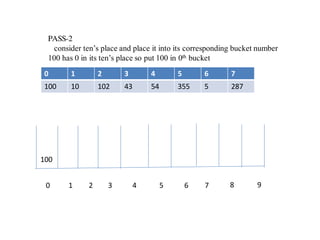
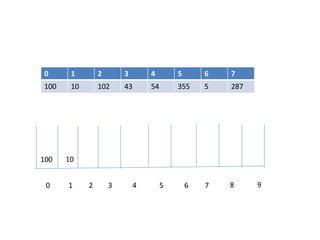
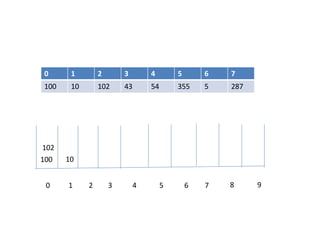
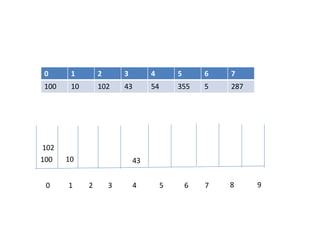
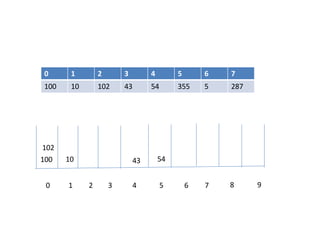
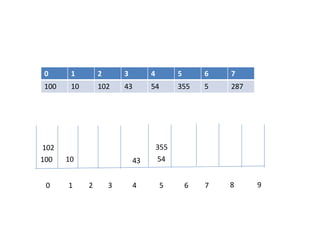
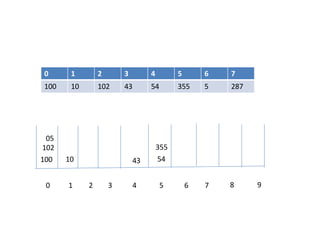
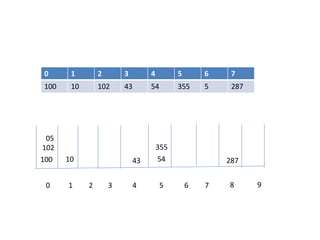
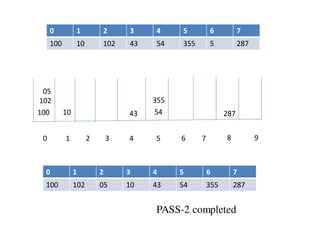
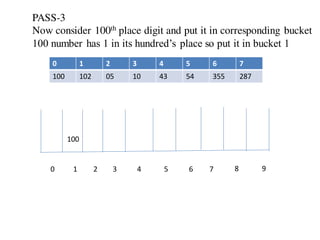
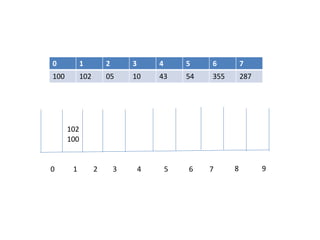
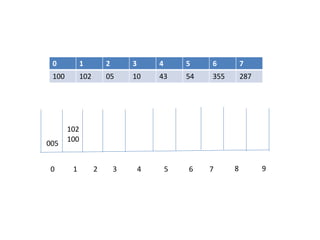
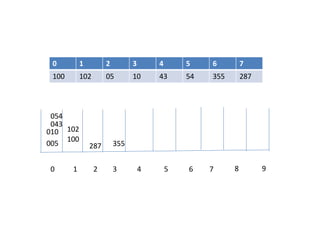
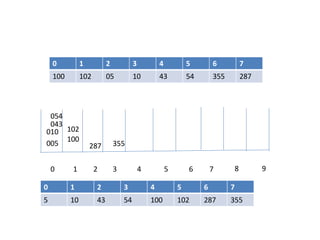
![Circular queue using array
# include<stdio.h>
#include<stdlib.h>
# define SIZE 4
int insert();
int del();
int display();
int cq[SIZE];
int front = -1;
int rear = -1;
main(){
while(1){
printf("1.Insertn");
printf("2.Deleten");
printf("3.Displayn");
printf("4.Quitn");
printf("Enter your choice : ");
scanf("%d",&choice);
switch(choice)
{
case 1 :
insert();
break;
case 2 :
del();
break;
case 3:
display();
break;
case 4:
exit(0);
default:
printf("Wrong choicen");
}/*End of switch*/
}/*End of while */
}/*End of main()*/](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-107-320.jpg)
![int insert(){
int item;
if((front == 0 && rear == SIZE-1) || (front == rear+1))
{
printf("Queue Overflow n");
return;}
if (front == -1) /*If queue is empty */
{
front = 0;
rear = 0;
}
else
if(rear == SIZE-1)/*rear is at last position of queue */
rear = 0;
else
rear = rear+1;
printf("Input the element for insertion in queue : ");
scanf("%d", &item);
cq[rear] = item ;
printf("the element %d at %d position and
front=%d,rear=%dn",cq[rear],rear,front,rear);
return;
}/*End of insert()*/](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-108-320.jpg)




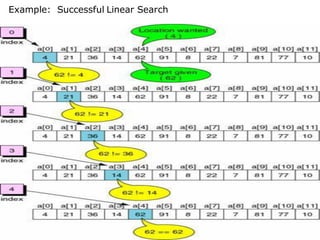
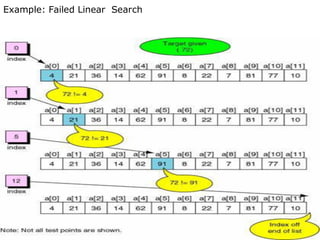
![Linear Search Implementation using non recursive method
#include<stdio.h>
#define SIZE 8
int linear_search(int a[], int target, int size);
void read_array(int a[], int size);
int main(void) {
int x[SIZE], target;
int index;
read_array(x, SIZE);
printf("EnterElement to search for: ");
scanf("%d", &target);
index = linear_search(x, target, SIZE);
if (index!= 0)
printf("Target was found at index %dn",index);
else
printf("Sorry, target item was not found");
return 0;
}
void read_array (int a[],int size) {
int i;
printf("Enter %d integer numbers separated by
blanksn> ", size);
for (i = 0; i < size; ++i)
scanf("%d", &a[i]);
}
/* Searches for an target in an array using
Linear search;
* Returns index of target or -1 if not found */
int linear_search(int a[], int target, int size)
{
int i,loc=0;
for(i=0;i<SIZE;i++)
{
if(target==a[i])
return ++loc;
else
loc++;
}
return 0;
}](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-120-320.jpg)
![/* C program that use recursivefunction to perform the Linear
Search for a Key value in a given listof integers*/
#include<stdio.h> #define SIZE 5
int linearSearch(intarray[], int index, int length, int value);
void main() {
int list[SIZE],element,i,target,index=0;
printf("nnEnter%d integer elements: ",SIZE);
for(i = 0; i < SIZE; i++) {
scanf("%d",&list[i]);
}
printf("nEntertarget element to be searched: ");
scanf("%d",&target);
element = linearSearch(list,index,SIZE,target);
if( element != -1 )
printf("nElement is found at %d location",element+1);
else
printf("Element is not found...");
}](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-121-320.jpg)
![int linearSearch(intarray[], int index,int length, int value)
{
if(index>length-1)
return -1;
else
if (array[index]==value)
return index;
else
return linearSearch(array,index+1,length,
value);
}](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-122-320.jpg)



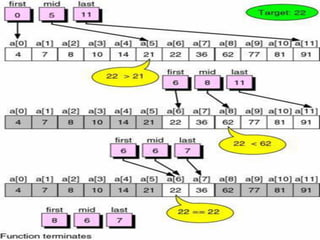
![/* C program that use recursivefunction to perform the Binary Search
for a Key valuein a given list of integers*/
#include<stdio.h> #define SIZE 8
int binary_search(int list[], int low, int high, int target);
void main() {
int list[SIZE], target, index,i;
printf("Enter%d elements in ascending or descendingorder: ",SIZE);
for(i=0;i<SIZE;i++)
scanf("%d",&list[i]);
printf("Enteran element that is to be searched: ");
scanf("%d", &target);
index = binary_search(list,0, SIZE-1, target);
if (index != -1)
printf("nTarget was found at index: %d ", index+1);
else
printf("Sorry, target item was not found");
}](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-127-320.jpg)
![int binary_search(int list[], int low, int high, int target)
{
int middle;
if (low > high)
return -1;
middle = (low + high)/2;
if (list[middle]== target)
return (middle);
else
if (list[middle]< target)
return binary_search(list,middle+1,high,target);
else
return binary_search(list,low,middle-1,target);
}](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-128-320.jpg)
![/* C program that use non recursivefunctionto perform the Binary
Search for a Key value in a given listof integers*/
#include<stdio.h>
#define SIZE 8
int binary_search(int list[], int low, int high, int target);
voidmain() {
int list[SIZE], target, index,i;
printf(“nenterthe array elements”);
for(i=0;i<SIZE;i++)
scanf("%d",&list[i]);
printf(“n enter the target element");
scanf("%d", &target);
index = binary_search(list,0, SIZE-1, target);
if (index != -1)
printf("nelement atlocation%d ", index+1);
else
printf("Sorry, target item was not found");
getch();
}](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-129-320.jpg)
![int binary_search(int a[],int low, int high, int target)
{
int middle;
while(low<=high)
{
middle=(low+high)/2;
if(target<a[middle])
high=middle-1;
else if(target>a[middle])
low=middle+1;
else
return middle;
}//while
return -1;
}//binary_search()](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-130-320.jpg)



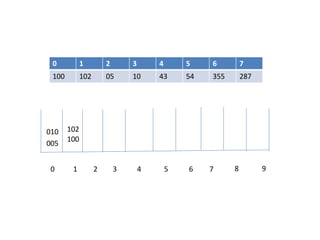
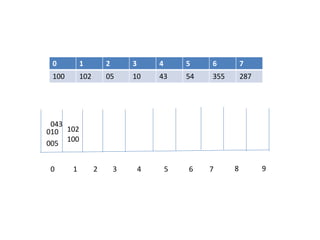
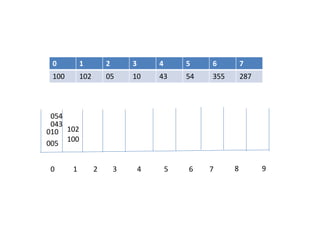
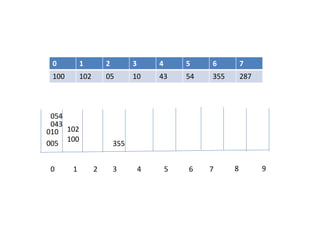
![Hash Function
- to map the key value into its corresponding index in hash table hash
function is used.
A hash function h transforms a key into an index in a hash table T[0…m-1]:
Where m is size of hash table.
-Use hash function to compute the index in the hash table for the given
key value.
-Hash function returns integer value which give the index value in the
hash table.](https://image.slidesharecdn.com/unit-iiids-190918102753/85/stacks-and-queues-134-320.jpg)