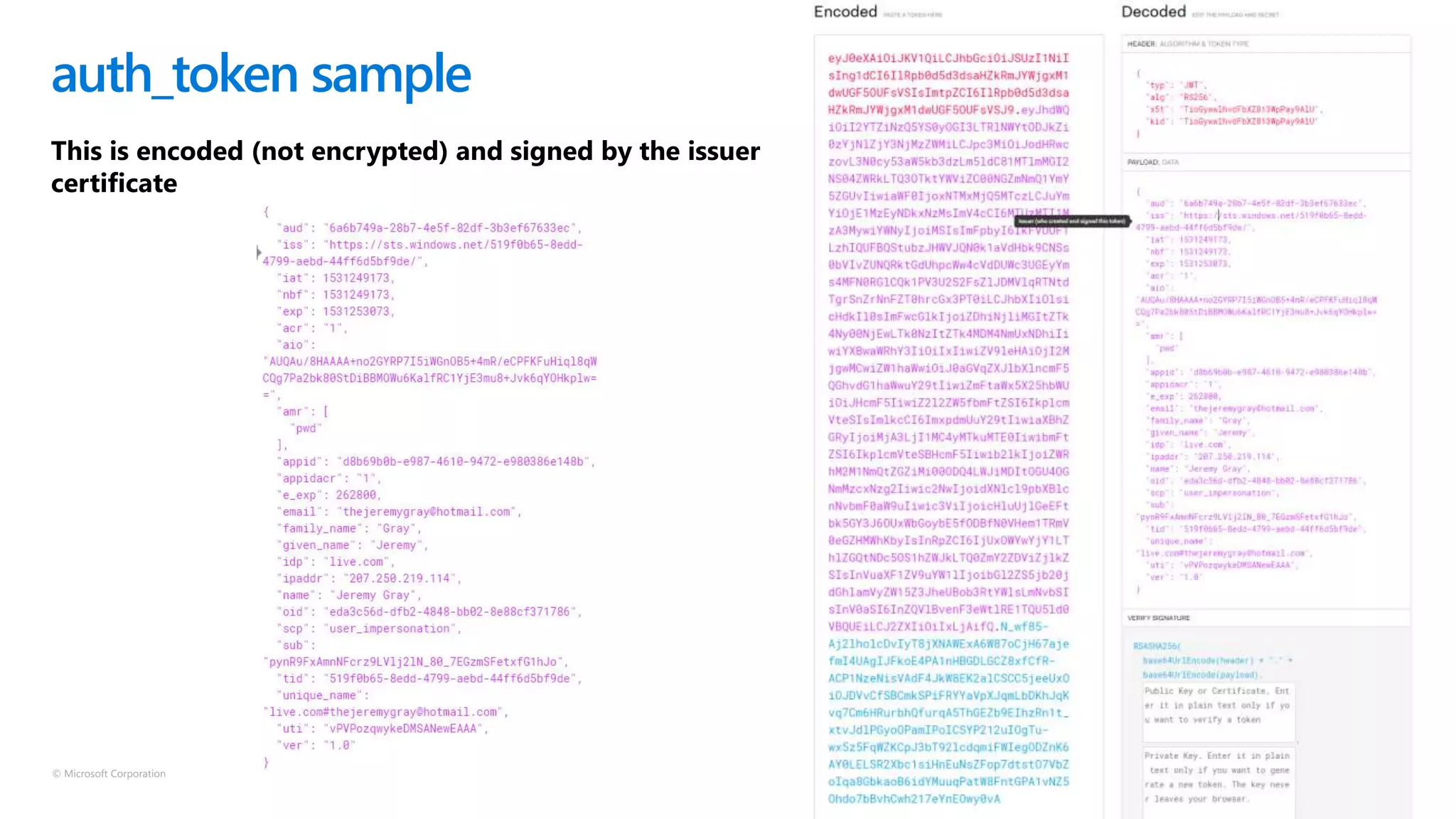
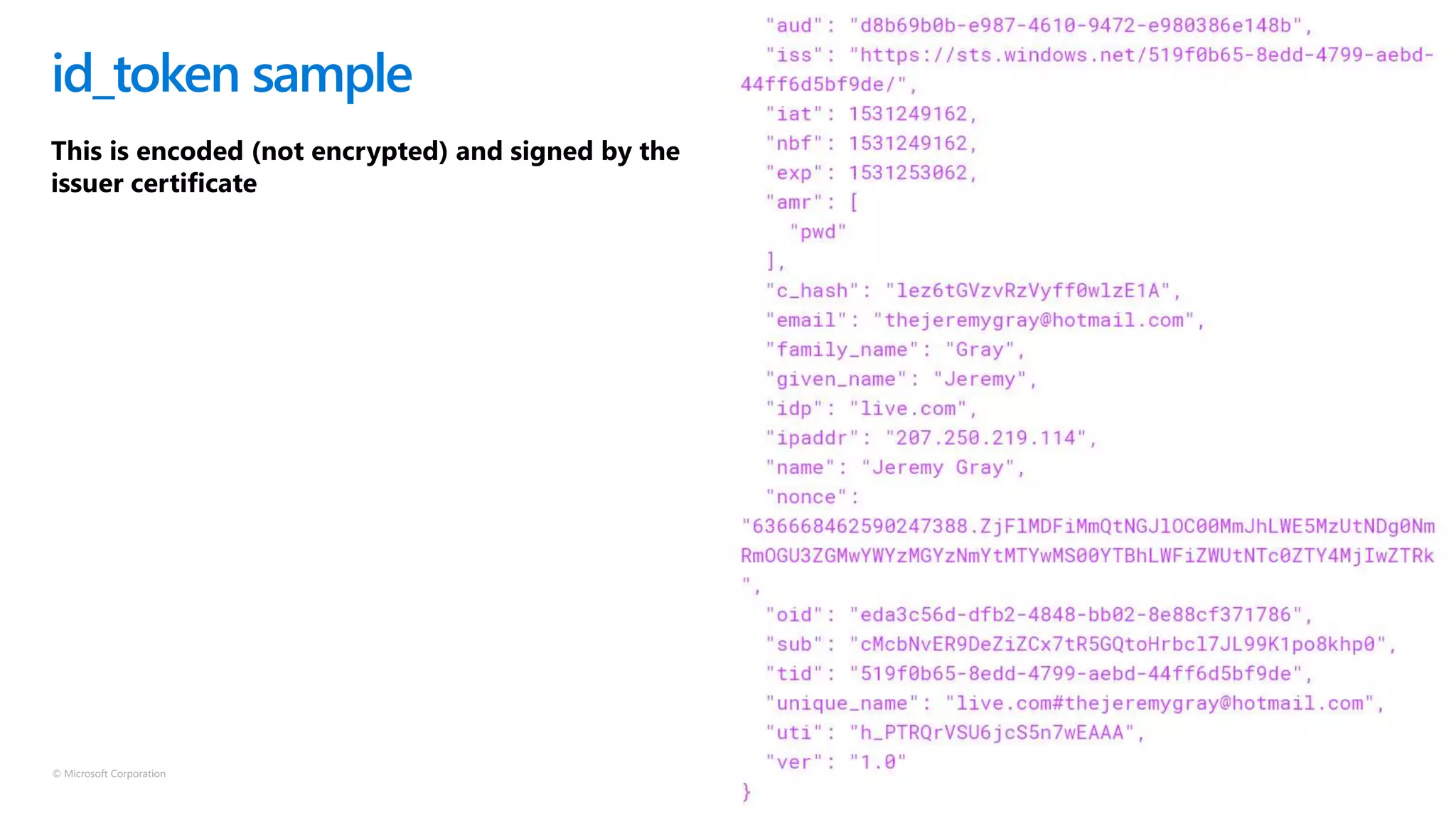
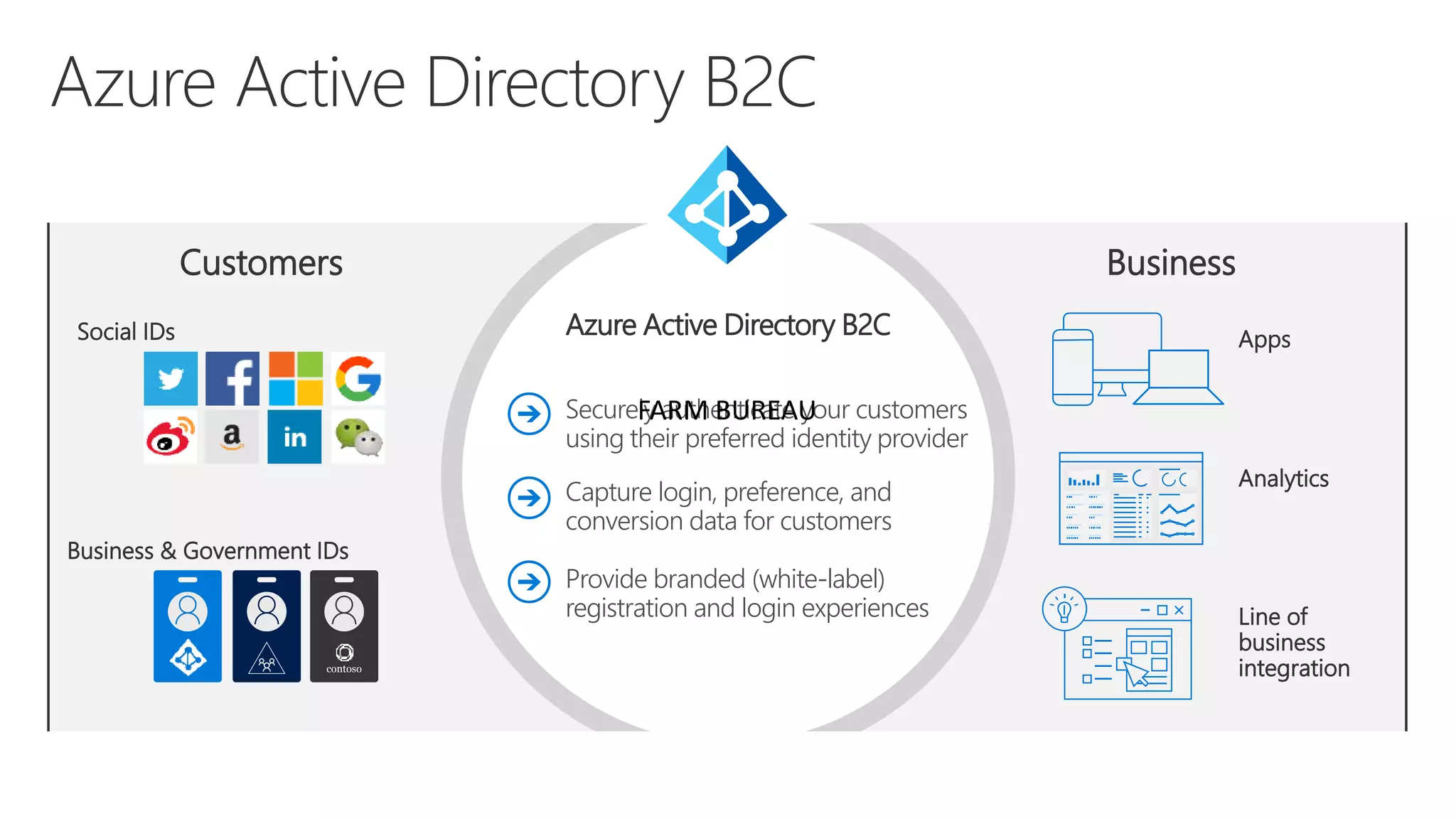
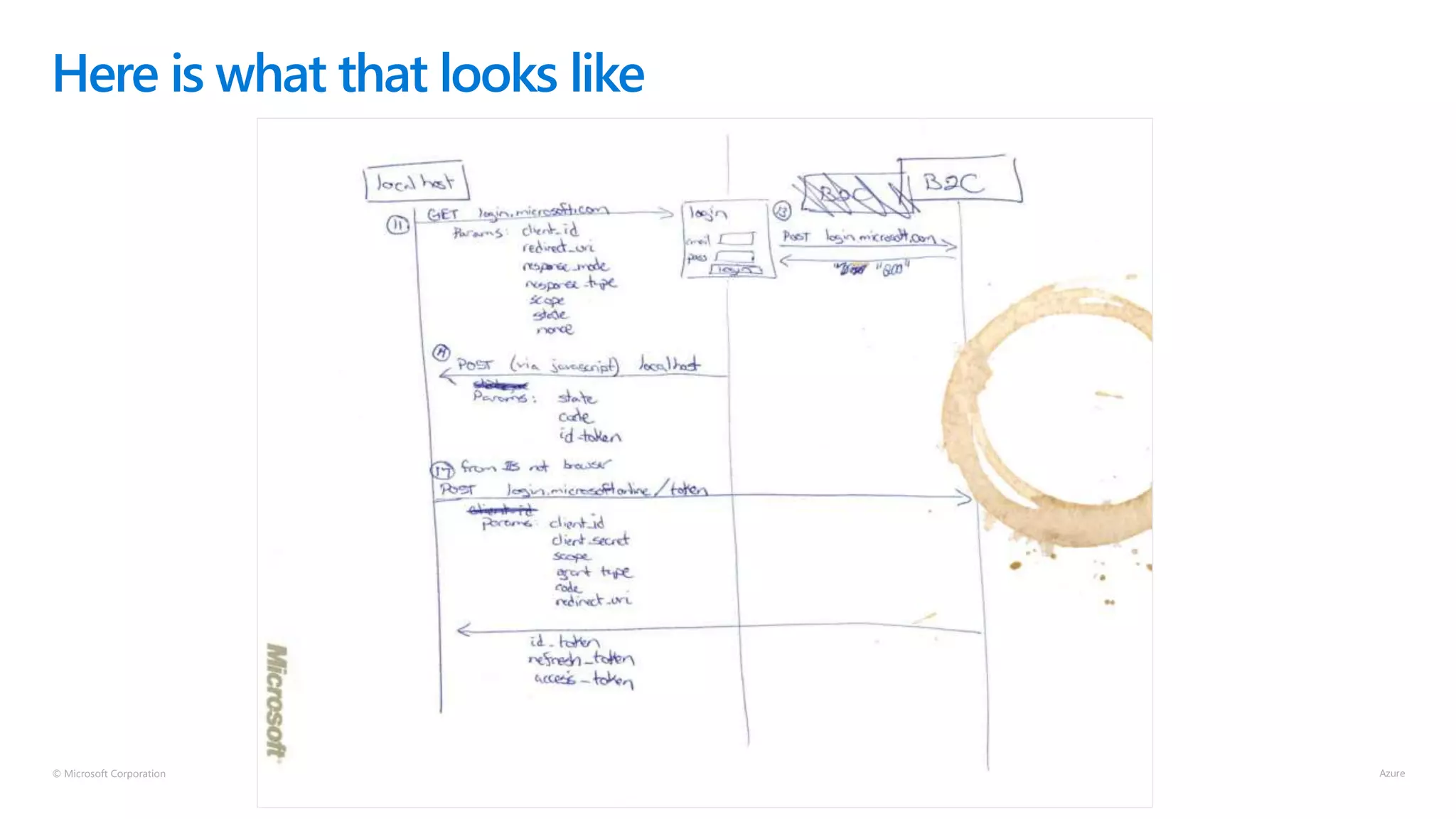
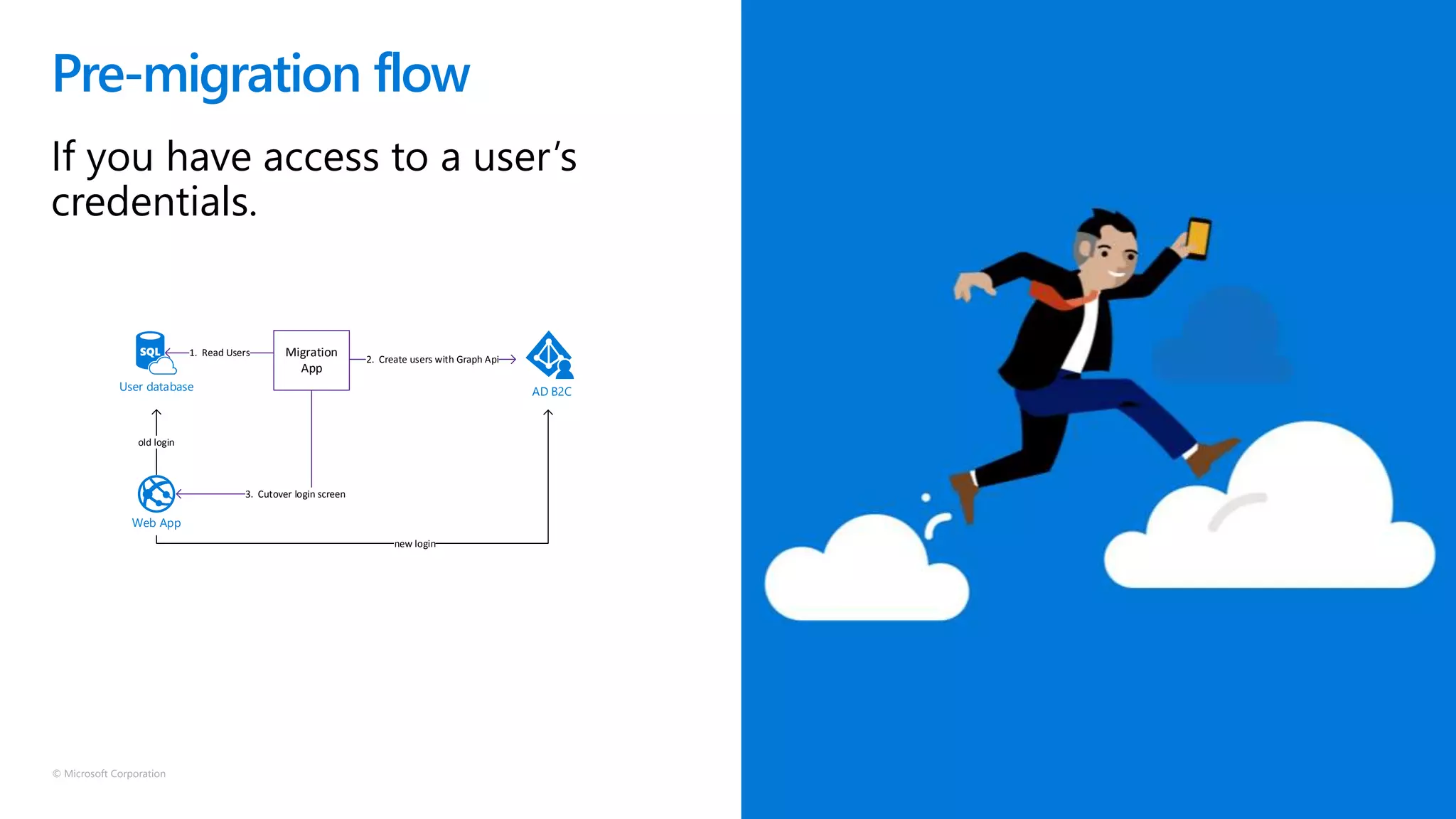
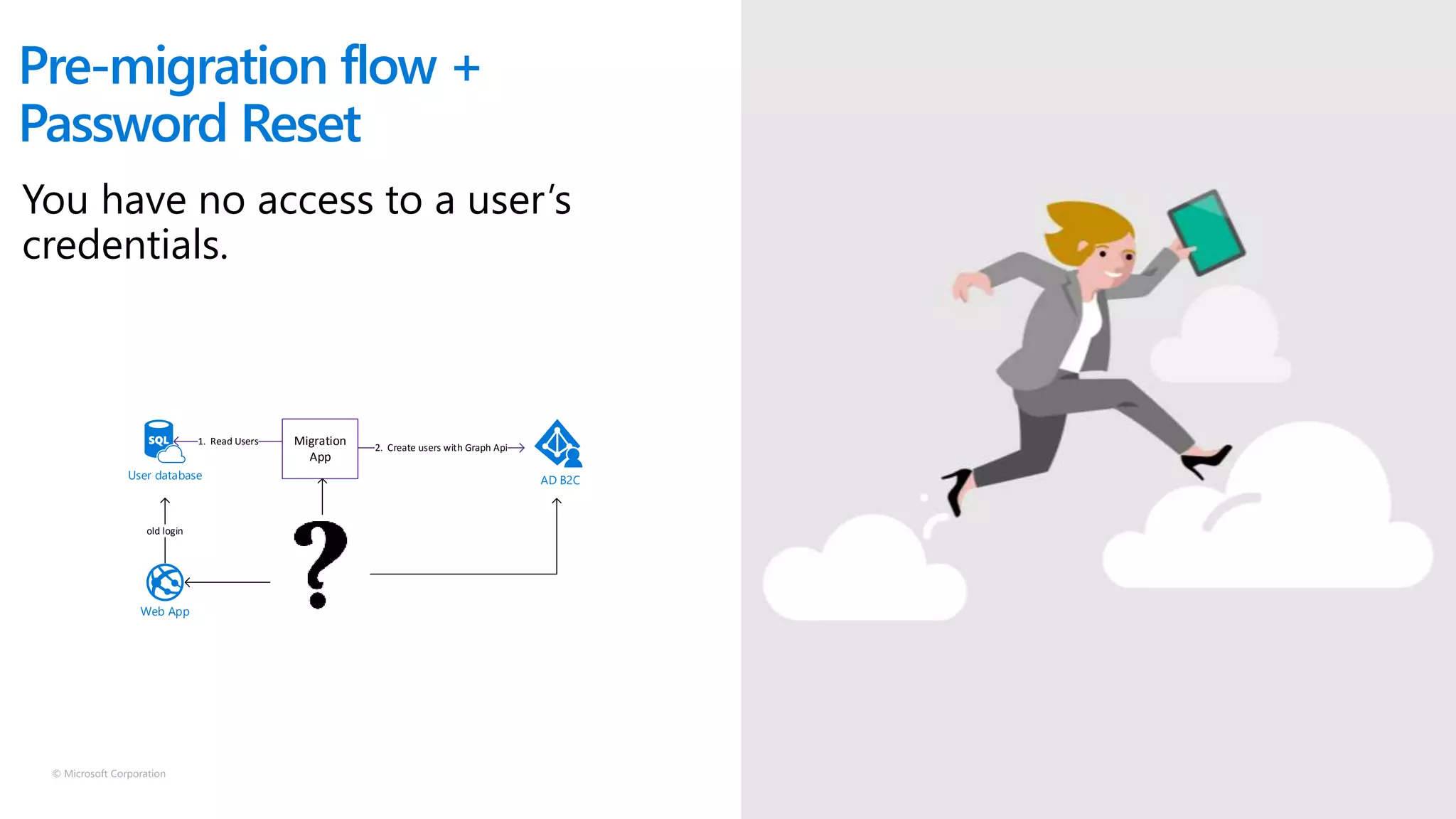
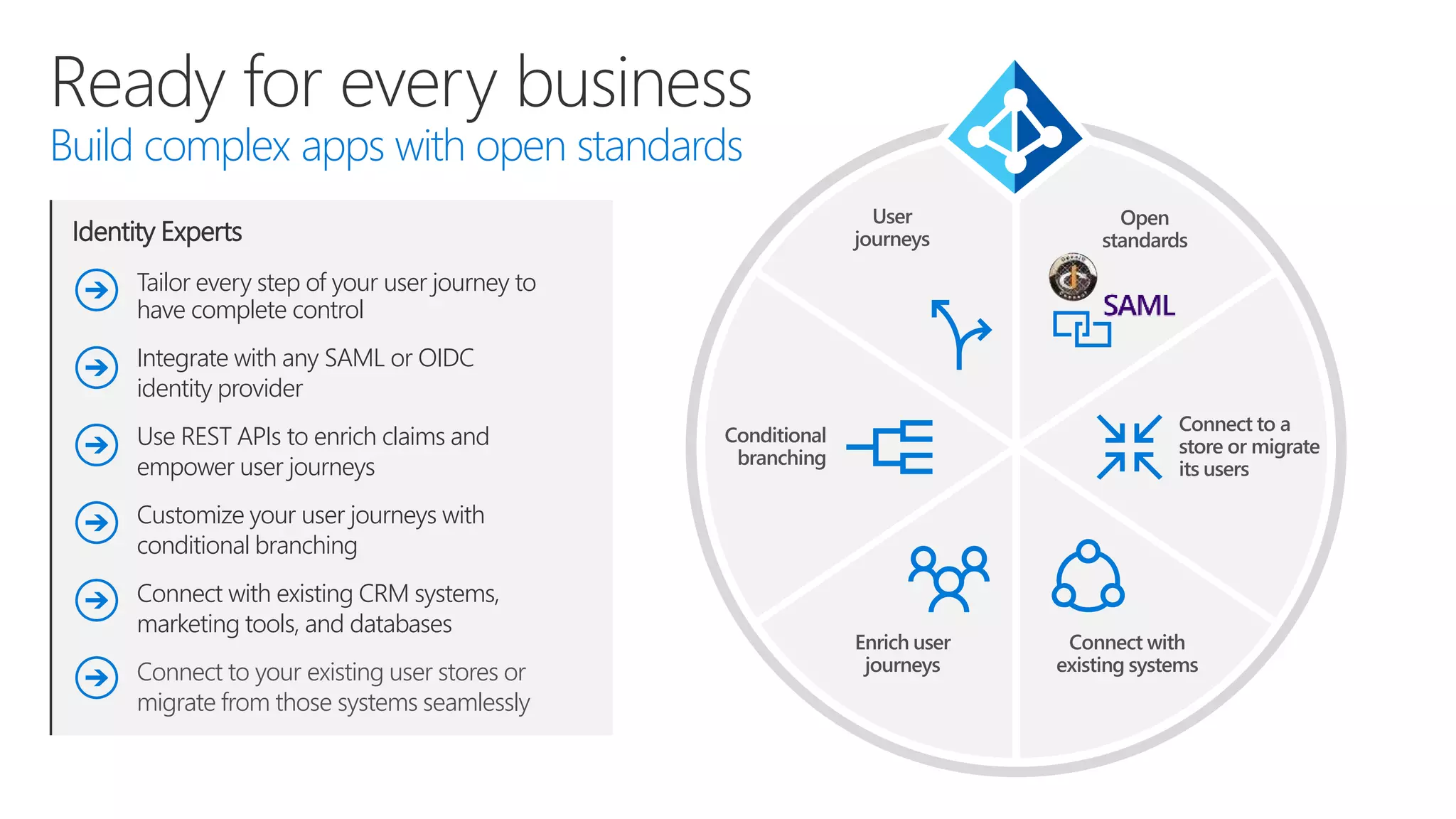
The document discusses Microsoft Azure Active Directory B2C, emphasizing its role in securely authenticating customers through various identity providers and customer experiences. It outlines the challenges of traditional authentication and the benefits of using OAuth 2.0 and OpenID Connect for authorization and authentication processes. Additionally, it provides insights into user migration and customization of user journeys using Graph API and integrations with other systems.