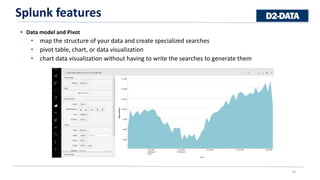
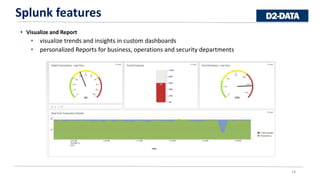
Splunk is a software that captures, indexes, and analyzes machine-generated data in real-time to generate operational intelligence across an organization. It transforms raw data into searchable events that can then be searched, visualized, and used to create reports, alerts, and dashboards. Splunk offers features like searching and investigating data, data modeling and pivoting, visualization and reporting, and monitoring and alerts. It is easy to deploy, load data into, and search and visualize data to gain insights. However, Splunk can be expensive for some organizations.


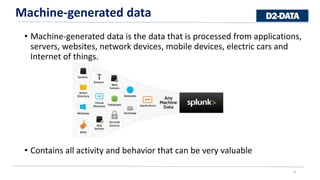



![Event: is a single piece of data, similar to a record in a log file or other data input.
172.26.34.223 - - [01/Jul/2005:12:05:27 -0700] "GET /trade/app?action=logout HTTP/1.1" 200 2953
When Splunk indexes data, it breaks up the data into individual pieces and gives each piece:
• Timestamp
• uses to correlate events by time, to create the timeline histogram and to set time ranges for searches
• Host
• hostname, IP address, or domain name of the network host on which the event originated
• Source
• source of an event - where the event originated
• Path of files and directories or network-based
• Source type
• tells Splunk what kind of data it is, so that Splunk can format the data intelligently during indexing (Ex.
access_combined,apache_error)
9
Events
9](https://image.slidesharecdn.com/splunk-151022002752-lva1-app6892/85/Splunk-9-320.jpg)