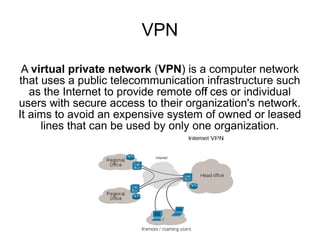
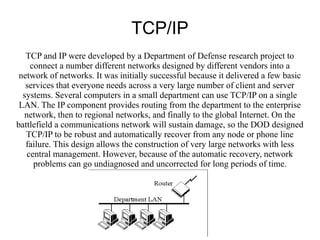
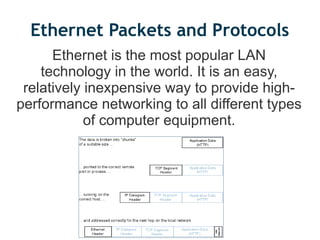
VPN uses public networks like the Internet to provide secure remote access to an organization's private network. TCP/IP was developed by the Department of Defense to connect different computer networks and provides basic routing and recovery from failures. WPA and WPA2 were developed to improve security over the previous WEP standard for wireless networks.