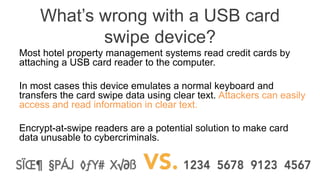
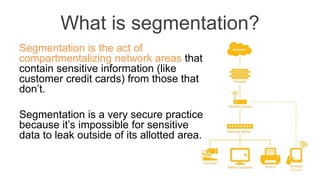
A popular vacation resort suffered a data breach when a front desk clerk clicked on a malicious link while assisting a customer, resulting in the download of keylogger malware that captured credit card information. The business made critical mistakes by using an unencrypted USB card reader and accepting credit card payments on the same machine used for internet browsing. Implementing network segmentation and proper employee training could have prevented the breach and secured sensitive information.