Embed presentation
Download to read offline
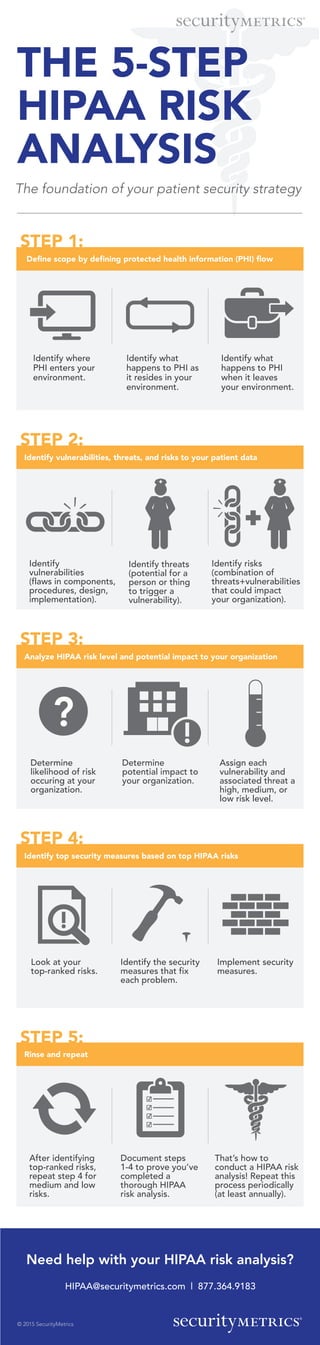

The document outlines a 5-step process for conducting a HIPAA risk analysis, focusing on identifying the flow of protected health information (PHI) and assessing top security measures against identified risks. It emphasizes the importance of regularly repeating the analysis and documenting each step to ensure ongoing compliance. Assistance for conducting the analysis is also offered through provided contact information.
