This document summarizes a CISSP mentor program session covering various topics:
1. The session reviewed chapters 1-3 of the curriculum and asked participants how many had read them and if they had any questions.
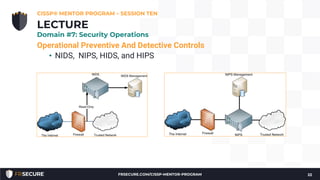
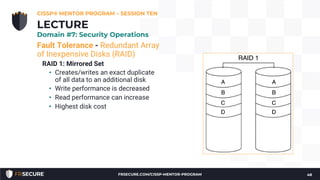
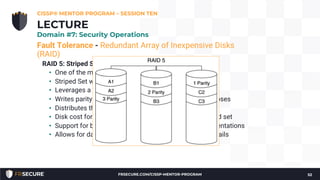
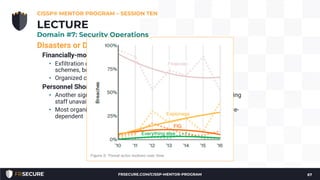
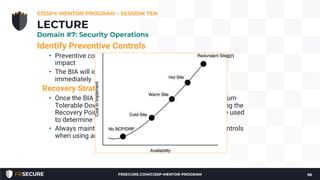
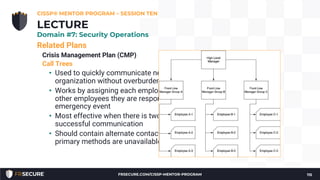
2. The presentation covered security models, incident response methodology, operational preventive and detective controls like IDS, honeypots, and asset/configuration management.
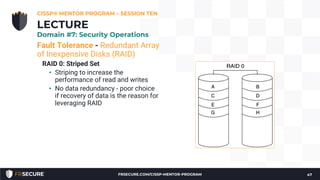
3. A quiz was given covering topics like appropriate responses during a penetration test and types of security tests. The session concluded with a discussion of vulnerability management and asset management principles.