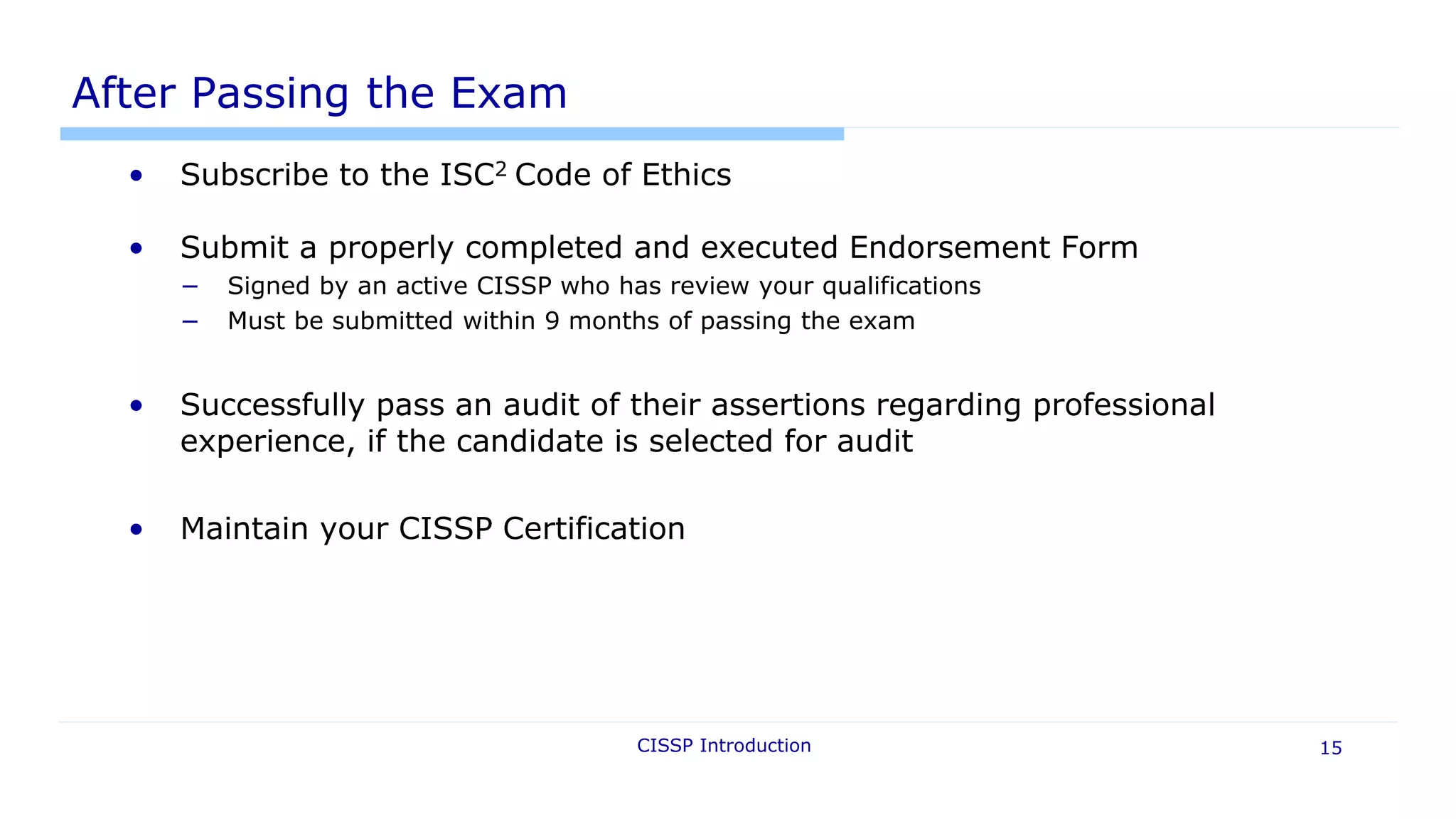
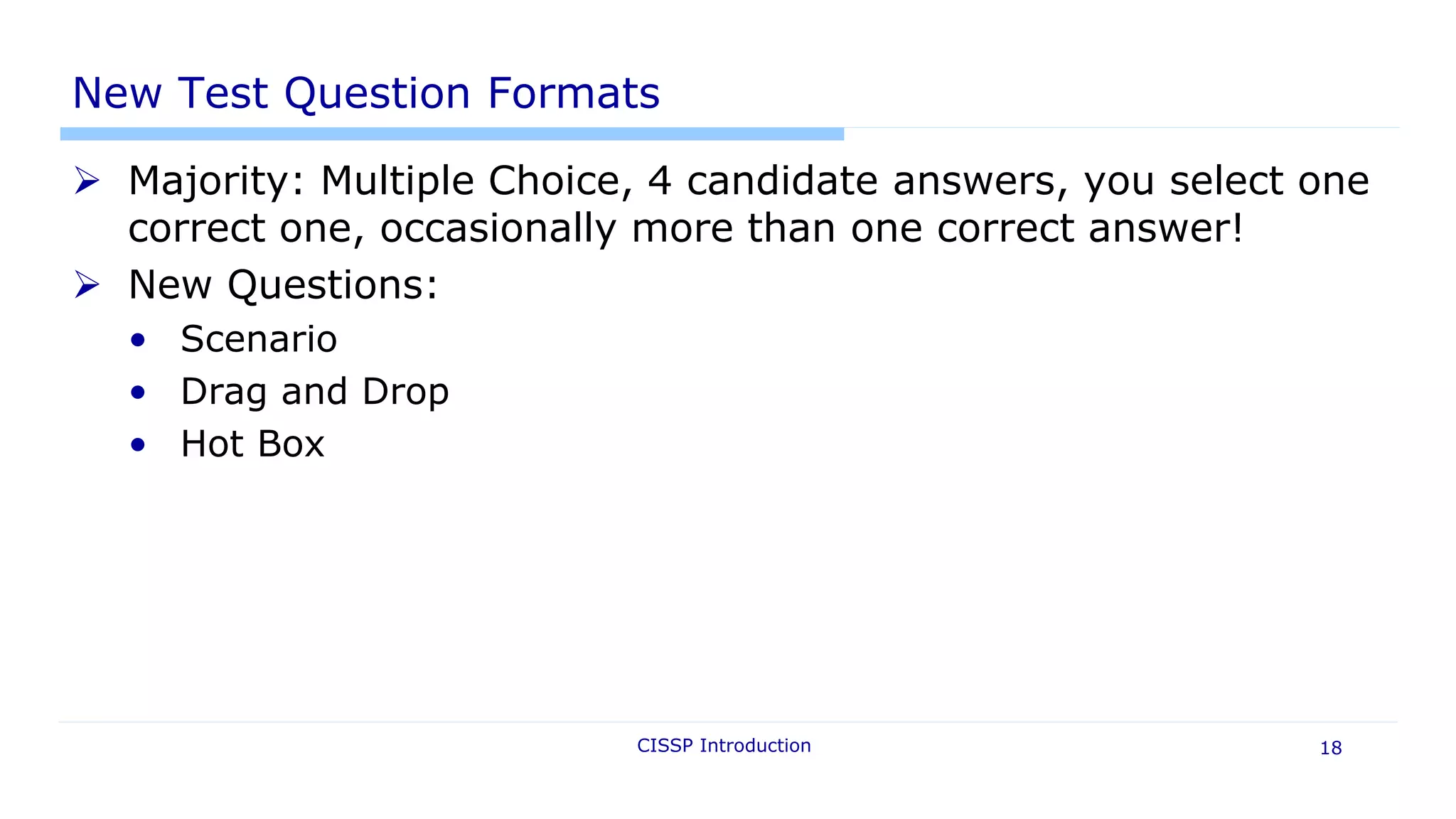
This document provides an introduction to the CISSP certification. It outlines the (ISC)2 organization that issues the CISSP, details the 8 domains covered on the exam, and explains the requirements to earn the CISSP certification, which include passing a 250 question exam and having 5 years of relevant work experience. It also provides an overview of the exam format and process, resources for study, and new topics covered on the updated 2015 exam.









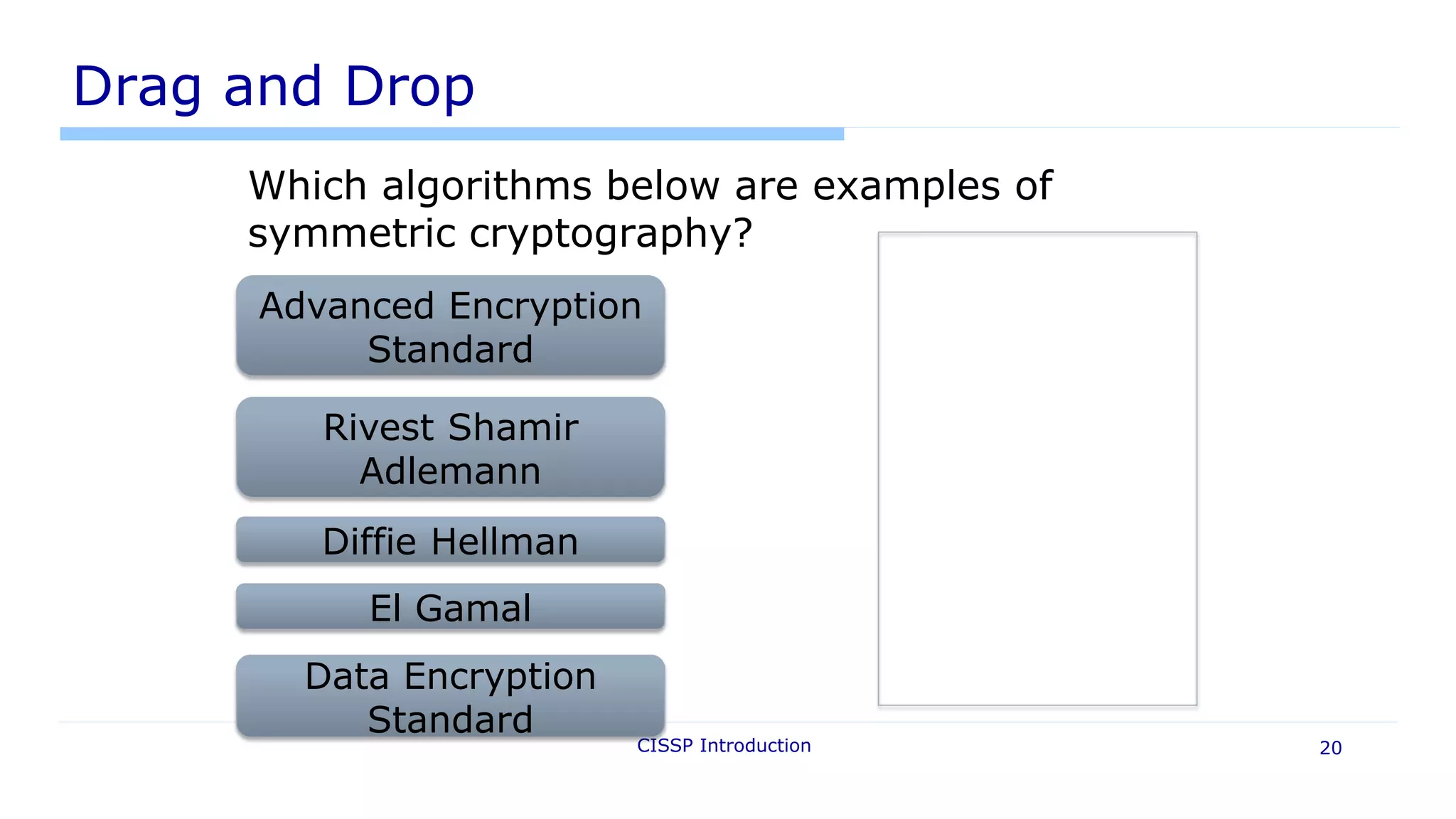
![Scenario Questions
Description:
• Situational: 1-2 paragraphs describing an environment, results of
an audit, etc.
• 3-5 questions on the scenario
Tactics:
• Read the question first [to understand!]
• Consider “operational” issues (tradeoffs)
CISSP Introduction 19](https://image.slidesharecdn.com/cisspintroduction2016udemyw-160324023229/75/CISSP-introduction-2016-Udemy-Course-19-2048.jpg)
![CISSP Introduction 22
Resources
ISC2: www.isc2.org
Online Resources & Practice Exams www.cccure.org
NIST Computer Security Resource Center http://csrc.nist.gov
http://learncissp.com/resources/
Shon Harris audio libraries & practice tests for EACH [old 10] Domains:
http://www.mhprofessional.com/sites/CISSPExams/](https://image.slidesharecdn.com/cisspintroduction2016udemyw-160324023229/75/CISSP-introduction-2016-Udemy-Course-22-2048.jpg)